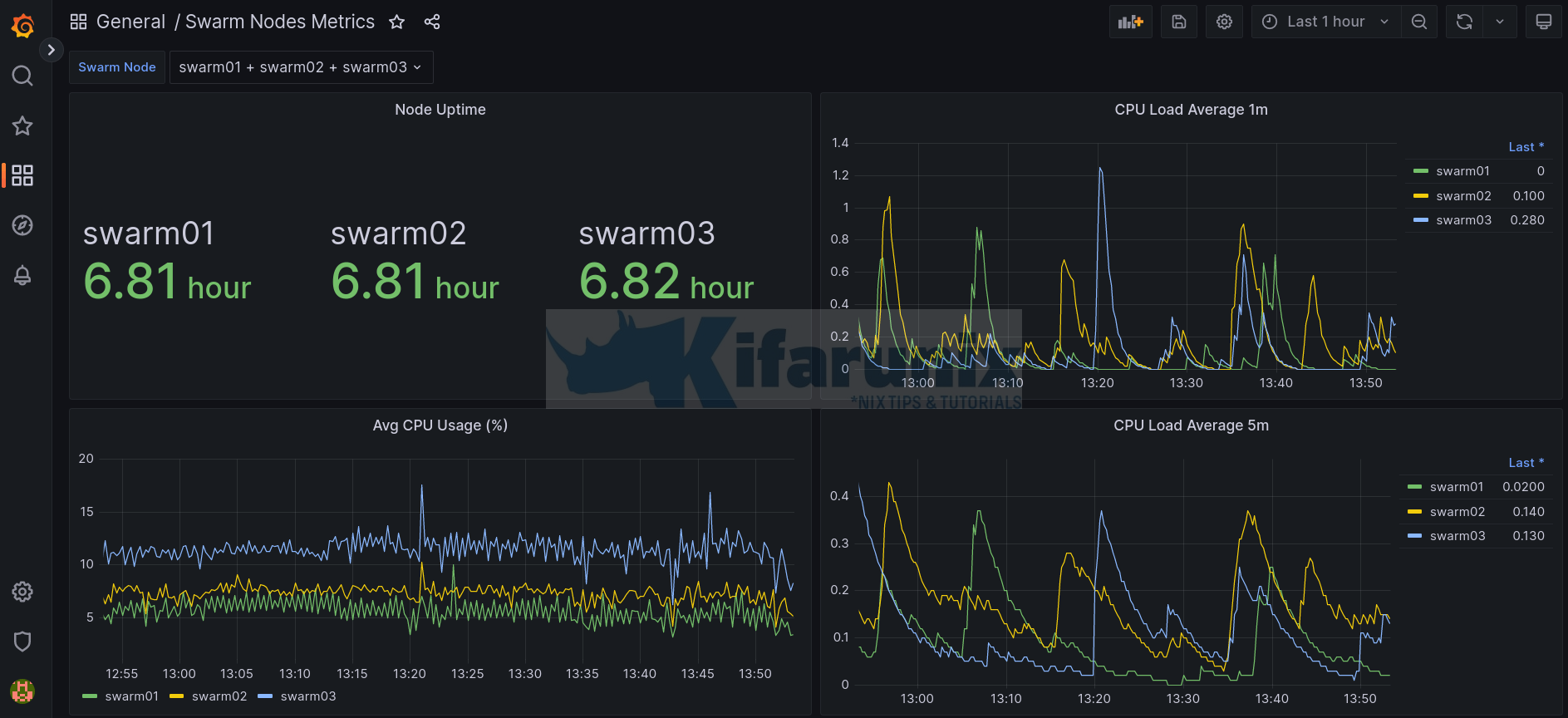
Monitor Docker Swarm Node Metrics using Grafana

Provision Block Storage for Kubernetes on Rook Ceph Cluster
VirtualBox, Virtualization
Install VirtualBox Extension Pack on VirtualBox 6.0
FIM, Security
Install and Configure AIDE on Ubuntu 18.04
HowTos, Security
Top 8 Security Skills To Prevent Cyber Threats
Database, HowTos, MySQL
Install MySQL 8 on Debian 10 Buster

Containers, HowTos, Kubernetes
Safely Upgrade Kubeadm Kubernetes Cluster: A Step-by-Step Guide
Installing Linux Dash with Nginx on Ubuntu 18.04 LTS
This guides presents a simple way installing Linux Dash with Nginx on Ubuntu 18.04 LTS. …
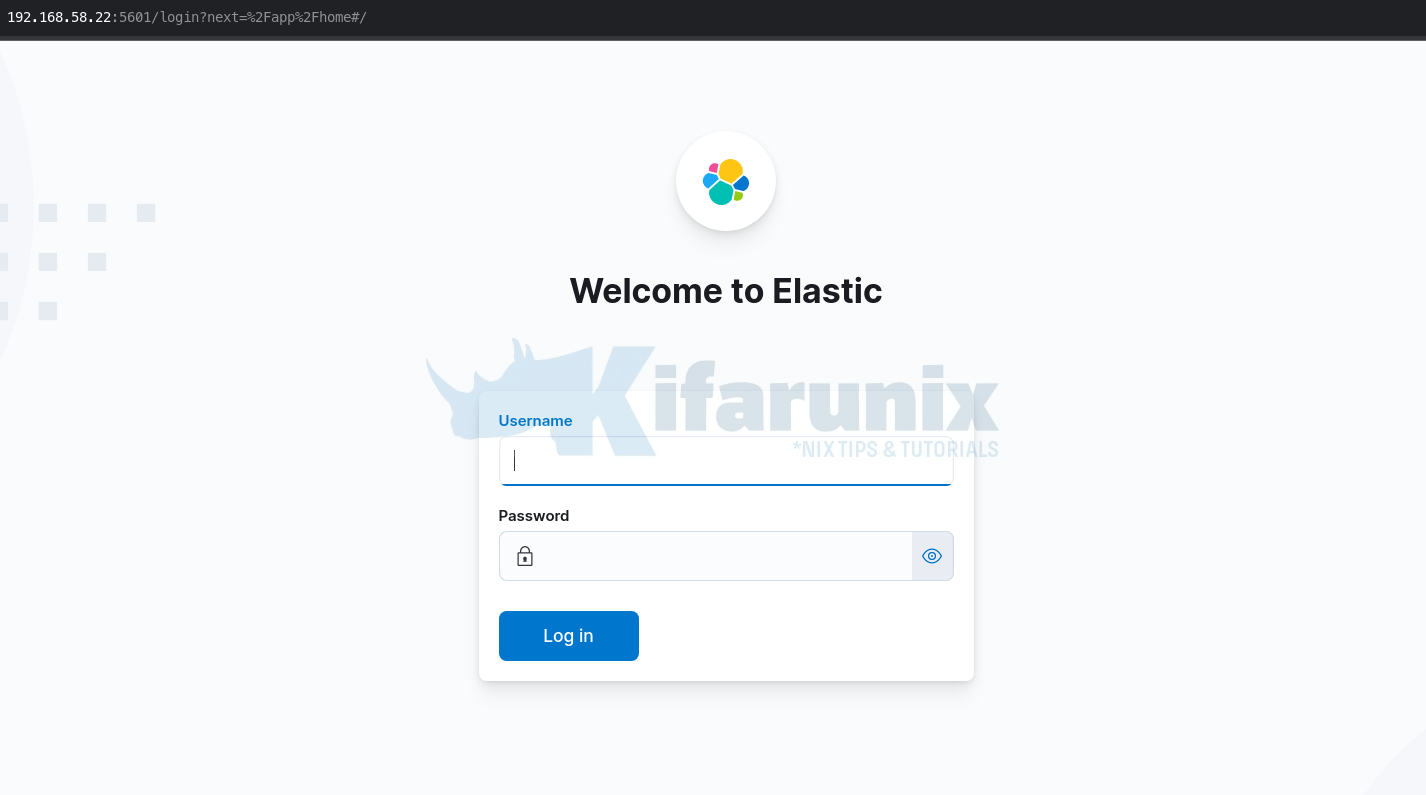
How to Enable Basic Authentication on ELK Stack
In this tutorial, you will learn how to enable basic authentication on ELK stack. Elastic/ELK …
Install GoAccess On Fedora 30/Fedora 29
Follow through this guide to learn how to install GoAccess on Fedora 30/Fedora 29. GoAccess …
Monitor SSL/TLS Certificates Expiry with Nagios
Well, assuming you understand the implications of the expired SSL/TLS certificates, let us go through …

Forward Apache Logs to Central Log Server with Rsyslog
In this tutorial, you will learn how to forward Apache logs to central log server …
Send Alert When ClamAV Finds Infected Files on Linux Systems
In this tutorial, you will learn how to send alert when ClamAV finds infected files …
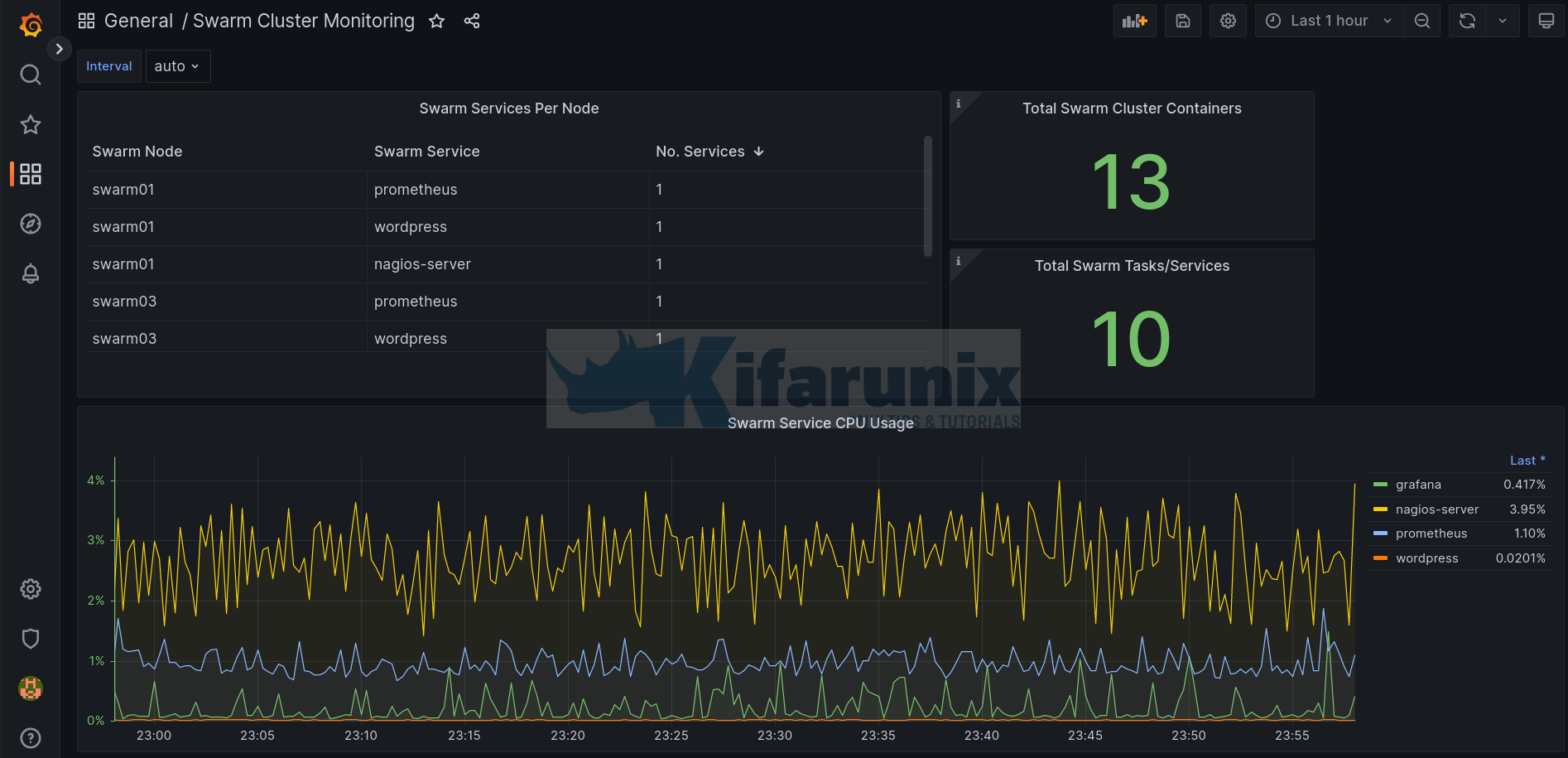
Monitor Docker Swarm Service Metrics using Grafana
How can I monitor Docker swarm service metrics? In this tutorial, you will learn how …

Install Nagios Plugins From Source RHEL/CentOS/Oracle Linux
This guide describes how to install Nagios Plugins from Source RHEL/CentOS/Oracle Linux. In our previous tutorial, …

Install and Setup OSSEC agent on Ubuntu 18.04/CentOS 7
In this guide, we are going to learn how to install and configure OSSEC agent …
Install Nagios Server on CentOS 9 Stream
In this guide, you will learn how to install Nagios Server on CentOS 9 Stream. …
Install Zabbix Server from Source on Debian 11

Install Grafana on Rocky Linux 8
Install Latest Grafana on CentOS 8
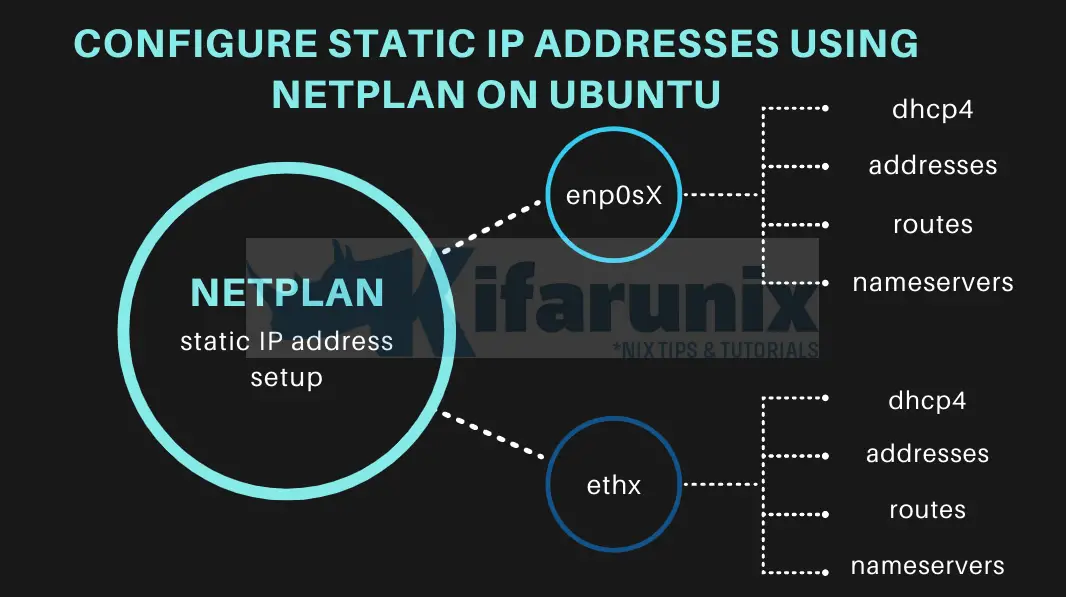
Configure Static IP Addresses using Netplan on Ubuntu
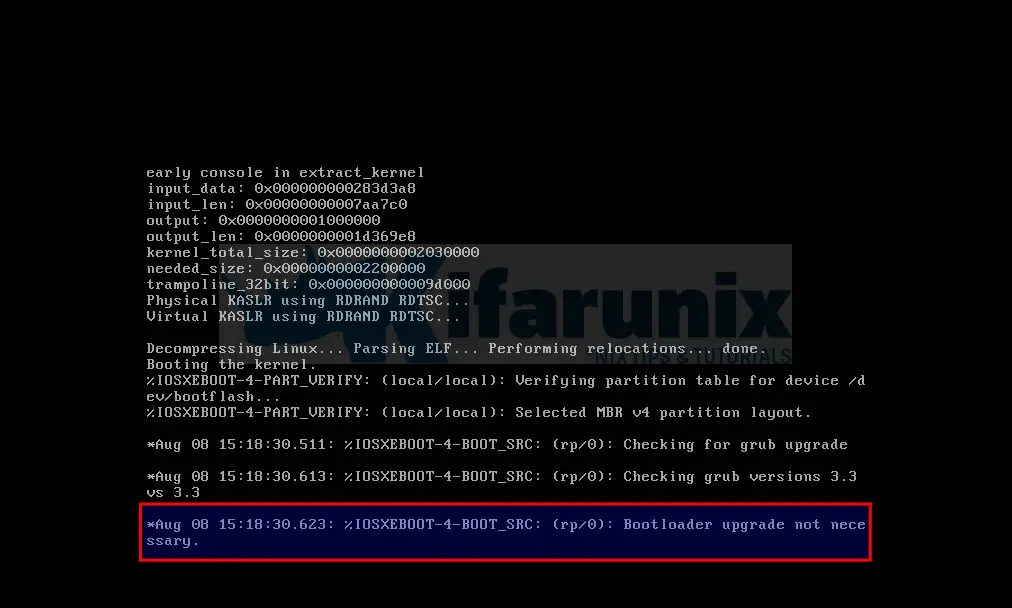
Cisco Catalyst 8000v Edge Stuck on Bootloader upgrade not Necessary
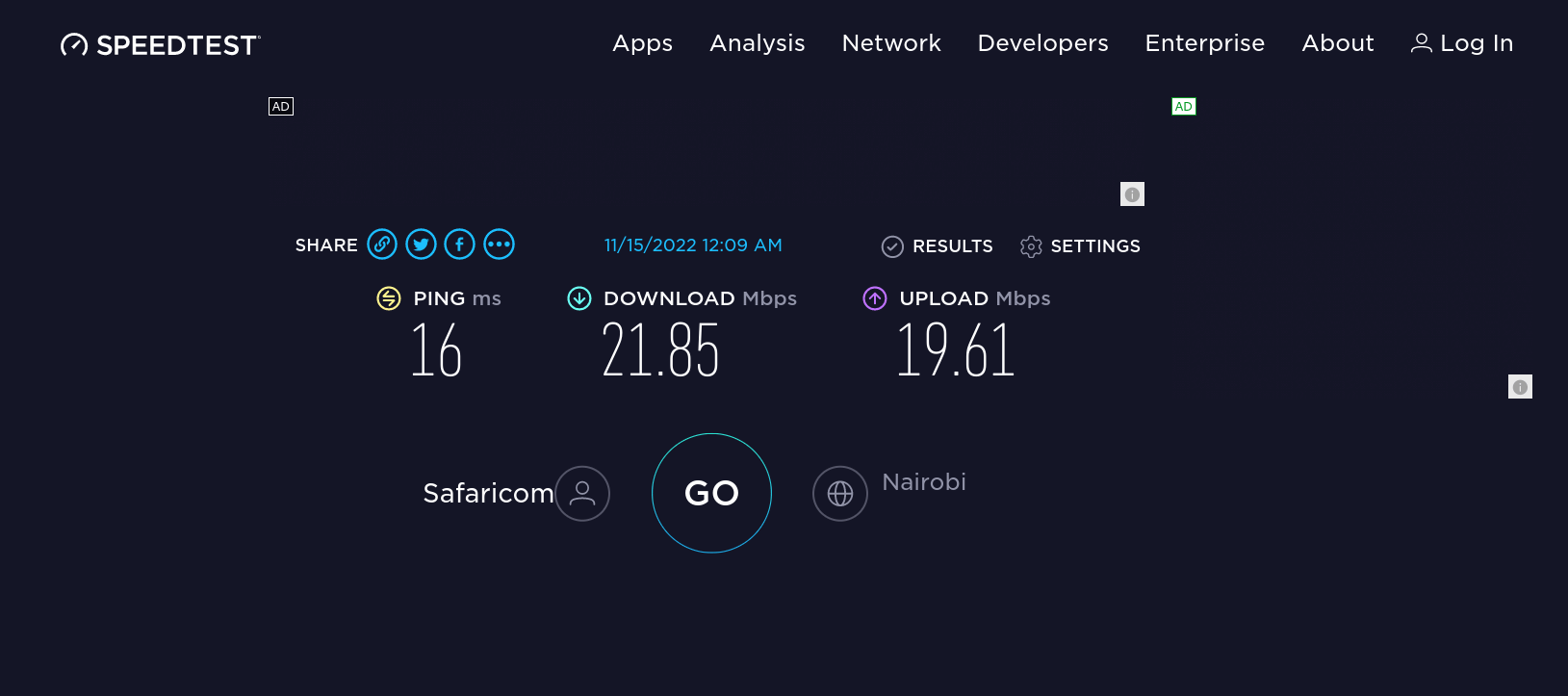
Easy way to Test Internet Speed on Linux Terminal

Install and use NMCLI tool on Debian Linux
Create Virtual/Secondary IP addresses on an Interface in Linux

Useful Facts About Setting Up Mobile Rugged Servers

Install Wireshark on Ubuntu 22.04
Install and Setup OpenVPN Server on Fedora 29/CentOS 7

Connect to WiFi in Linux Using NMCLI command

Install Latest Wireshark on Ubuntu 18.04
Set Static Routes via an Interface/IP on CentOS/Ubuntu

Analyze PCAP Files using Malcolm Network Traffic Analysis tool
How to Upload ISO File to VMware ESXi Datastore using vSphere Client
Hello there, welcome to this tutorial on how to upload an ISO file to VMware …

Install Portainer on Rocky Linux
In this tutorial, you will learn how to install Portainer on Rocky Linux. Portainer is a …

Install Rocky Linux 8 on VirtualBox
Follow through this tutorial to learn how to install Rocky Linux 8 on VirtualBox. According …
Install VirtualBox Guest Additions on Ubuntu 18.04
In this guide, we are going to learn how to install VirtualBox Guest Additions on …

Create and Upload Custom Linux Image into OpenStack
In this tutorial, you will learn how to create and upload custom Linux image into …
Install Rocky Linux 9 on VirtualBox
In this tutorial, you will learn on how to easily install Rocky Linux 9 on …
Install Ubuntu 21.04 Desktop on VirtualBox
In this tutorial, you learn how to install Ubuntu 21.04 Desktop on VirtualBox. The latest …
How to Install FreeBSD 12 on VirtualBox
Hello there, welcome to our guide on how to install FreeBSD 12 on VirtualBox. FreeBSD …
Install Debian 10 Buster on VirtualBox
In this guide, we are going to learn how to install Debian 10 Buster on …

How to Install KVM on Ubuntu 24.04
In this tutorial, you will learn how to install KVM on Ubuntu 24.04. KVM (Kernel-based …
Install VirtualBox 7 on Ubuntu 24.04
How to Install FreeBSD 12 on VirtualBox