Follow through this guide to learn how to configure Apache with SSL/TLS Certificates on CentOS 8.
Are you using Nginx instead? Check our guide on setting up Nginx with SSL/TLS certificates by following the link below;
Configure Nginx with SSL/TLS certificates on CentOS 8
Configuring Apache with SSL/TLS Certificates on CentOS 8
Run System Update
Update your system package by executing;
dnf updateInstall Apache and SSL/TLS module on CentOS 8
Apache HTTP server is provided by the httpd package while mod_ssl packages provides the Apache SSL/TLS module. Both packages can be installed by running;
dnf install httpd mod_sslRunning Apache
Start and enable Apache to run on system boot.
systemctl enable --now httpdAllow HTTPS on Firewall
To allow external access to Apache over HTTPS, open 443 (HTTPS) depending on the traffic to server.
In this guide, since we configuring Nginx to the TLS certificates, we are opening port 443/tcp.
firewall-cmd --add-port=443/tcp --permanentIf you are looking at redirecting the HTTP traffic to HTTPS, open port 80 too.
firewall-cmd --add-port=80/tcp --permanentfirewall-cmd --reloadGenerate SSL/TLS Certificates
There are multiple options to choose from when you want to secure Apache with SSL/TLS certificates.
- You can use self-signed certificates for test purposes.
- You can order for a commercially trusted server certificate from your preferred CA
- You can use the free, automated, and open CA, Let’s Encrypt.
Well, in this guide, we are using the first option of self-signed SSL/TLS certificates for demonstration purposes.
So how do you generate the self-signed SSL/TLS certificates on CentOS 8? Openssl command is used to generate the SSL/TLS certificates as shown below;
openssl req -newkey rsa:4096 -nodes -keyout /etc/pki/tls/private/kifarunix-demo.key -x509 -days 365 -out /etc/pki/tls/certs/kifarunix-demo.crtSo what are the openssl command line options used above?
req: It is used to create CSR as well as the self signed certificates.-newkey rsa:4096: This option creates a new certificate request and a 4096 bits RSA key at the same time.-nodes: When this option is specified then if a private key is created it will not be encrypted.-keyout/etc/pki/tls/private/kifarunix-demo.key: Writes the newly created private key to the specified filename. Replace the filename accordingly.-x509: This option outputs a self signed certificate instead of a certificate request.-days 365: Used to specify the validity period for the self signed certificate generated. This therefore is valid for 365 days.-out /etc/pki/tls/certs/kifarunix-demo.crt: Specifies the output filename to write the self signed certificate to.
When the command runs, you are prompted to provide certificate identification details such the Country Name of your organization, the State, the Locality, the name of Organization, the Organization Unit, the Common Name (This is the most important detail), optional email.
You can as well be able to provide these details on the command line using the -subj option of the openssl-req command as shown below;
-subj "/C=CN/ST=STATE/L=CITY/O=ORG NAME/OU=Department/CN=DOMAIN_NAME/emailAddress=name@domain"For example to generate a self-signed SSL/TLS certificate for the domain, kifarunix-demo.com and all its sub-domains (Common name will be written as *.kifarunix-demo.com), you can openssl-req command as;
(Replace the domain names accordingly)
openssl req -newkey rsa:4096 -nodes -keyout /etc/pki/tls/private/kifarunix-demo.key -x509 -days 365 -out /etc/pki/tls/certs/kifarunix-demo.crt \
-subj "/C=US/ST=Oregon/L=Springfield/O=kifarunix-demo/OU=IT/CN=*.kifarunix-demo.com/[email protected]"Well, there you go. Your private key has been written to /etc/pki/tls/private/kifarunix-demo.key while your certificate has been written to /etc/pki/tls/certs/kifarunix-demo.crt.
Well, want to use commercially signed certificates? Generate the CSR and submit it to your favourite CA to order for trusted certificates.
The command below can get you a CSR. Make due substitution.
openssl req -new -newkey rsa:4096 -nodes -keyout domain.key -out domain.csr \
-subj "/C=CN/ST=STATE/L=CITY/O=ORG NAME/OU=Department/CN=DOMAIN_NAME/emailAddress=name@domain"Be sure to keep the key safe as you will need when installing the certificates.
Configure Apache to Use SSL/TLS Certificates
Now that you have your SSL/TLS private key and certificate (sel-signed in this case), proceed to configure Apache to use them.
Open Apache SSL configuration file for editing.
vim /etc/httpd/conf.d/ssl.confApart from installing the SSL/TLS certificates, there are some ciphers provided by Cipherli.st that aims to provide Strong SSL Security for all modern browsers. We will also add these ciphers to Apache SSL configuration.
In this guide, we are making changes to the default SSL virtual host configuration.
## Redirect HTTP Traffic to HTTPS
<VirtualHost *:80>
DocumentRoot /var/www/html
ServerName centos8.kifarunix-demo.com
RewriteEngine On
RewriteCond %{HTTPS} off
RewriteRule ^(.*)$ https://%{HTTP_HOST}%{REQUEST_URI} [R=301,L]
</VirtualHost>
## Begin SSL configuration
Listen 443 https
SSLPassPhraseDialog exec:/usr/libexec/httpd-ssl-pass-dialog
SSLSessionCache shmcb:/run/httpd/sslcache(512000)
SSLSessionCacheTimeout 300
SSLCryptoDevice builtin
<VirtualHost _default_:443>
ErrorLog logs/ssl_error_log
TransferLog logs/ssl_access_log
LogLevel warn
SSLEngine on
SSLProtocol -all +TLSv1.3 +TLSv1.2
SSLOpenSSLConfCmd Curves X25519:secp521r1:secp384r1:prime256v1
SSLHonorCipherOrder on
SSLCipherSuite EECDH+AESGCM:EDH+AESGCM
SSLCertificateFile /etc/pki/tls/certs/kifarunix-demo.crt
SSLCertificateKeyFile /etc/pki/tls/private/kifarunix-demo.key
<FilesMatch "\.(cgi|shtml|phtml|php)$">
SSLOptions +StdEnvVars
</FilesMatch>
<Directory "/var/www/cgi-bin">
SSLOptions +StdEnvVars
</Directory>
BrowserMatch "MSIE [2-5]" \
nokeepalive ssl-unclean-shutdown \
downgrade-1.0 force-response-1.0
CustomLog logs/ssl_request_log \
"%t %h %{SSL_PROTOCOL}x %{SSL_CIPHER}x \"%r\" %b"
Header always set Strict-Transport-Security "max-age=63072000; includeSubDomains; preload"
Header always set X-Frame-Options DENY
Header always set X-Content-Type-Options nosniff
SSLCompression off
#SSLUseStapling on
#SSLStaplingCache "shmcb:logs/stapling-cache(150000)"
SSLSessionTickets Off
</VirtualHost>The Online Certificate Status Protocol (OCSP) stapling is disabled since we are using self-signed certificates.
Save the configuration file and check for any configuration syntax.
apachectl configtestor
httpd -tSyntax OKCreate sample Apache test page on the default root directory;
vim /var/www/html/index.html<!DOCTYPE html>
<html>
<body>
<h1>centos8.kifarunix-demo.com</h1>
<p>Configuring Apache to use SSL/TLS certificates on CentOS 8</p>
</body>
</html>Running Apache with SSL/TLS enabled
You can now restart Apache to effect the changes.
systemctl restart httpdTesting Apache SSL/TLS configuration
It is now time to test whether Apache is able to server HTTPS requests as well as redirect HTTP traffic to HTTPS traffic. Access it using the server’s IP address of hostname, https://server-IP-or-Hostname.
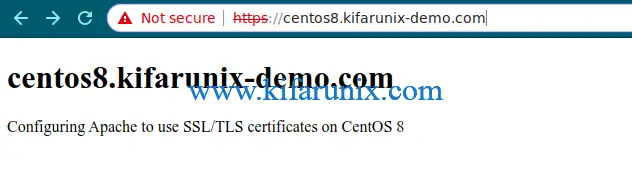
Even if you try with http://server-IP-or-Hostname, it will be redirected to HTTPS.
Related Tutorials
Install Redmine with Apache and MariaDB on CentOS 8
Install Apache with Self-signed Certificate on FreeBSD 12


apachectl configtest
AH00526: Syntax error on line 41 of /etc/httpd/conf.d/ssl.conf:
Invalid command ‘%t %h %{SSL_PROTOCOL}x %{SSL_CIPHER}x “%r” %b’, perhaps misspelled or defined by a module not included in the server configuration
Please how to resolve this error