Follow through this tutorial to learn how to integrate TheHive with MISP. TheHive, a Security Incident Response Platform (SIRP) can be integrated with MISP, (Malware Information Sharing Platform) to make the investigation of any security incidents easy for SOC analysts, CSIRTs or CERTs.
Integrating TheHive with MISP
To integrate TheHive with MISP, you can deploy each of these components on separate nodes or all on a single node. We will be using a single node for demonstration purposes in this guide.
Install and Configure TheHive
In order to integrate TheHive with MISP, you first need to have TheHive running.
Follow through this guide to learn how to install and configure TheHive;
Install TheHive on Ubuntu 22.04/Ubuntu 20.04
Install MISP
Follow through the guide below to learn how to install MISP on Ubuntu 22.04/Ubuntu 20.04.
Install MISP on Ubuntu 22.04/Ubuntu 20.04
You can simply download and execute the installation script on any supported system.
Integrating TheHive with MISP
The integration of TheHive and MISP will both tools work hand in hand in incident analysis. MISP can be configured to sent event alerts into TheHive while TheHive can be configured as well to sent event observables into MISP for analysis.
To integrate TheHive with MISP;
- Generate MISP Auth key
Login to MISP web interface as administrative user and navigate to Administration > List Auth Keys > Add authentication Key;
Select the User to create an API key for, comment, defined IPs allowed to query MISP using the API key, set expiration date or leave blank to set to not expire, choose whether to set the key as read only key.
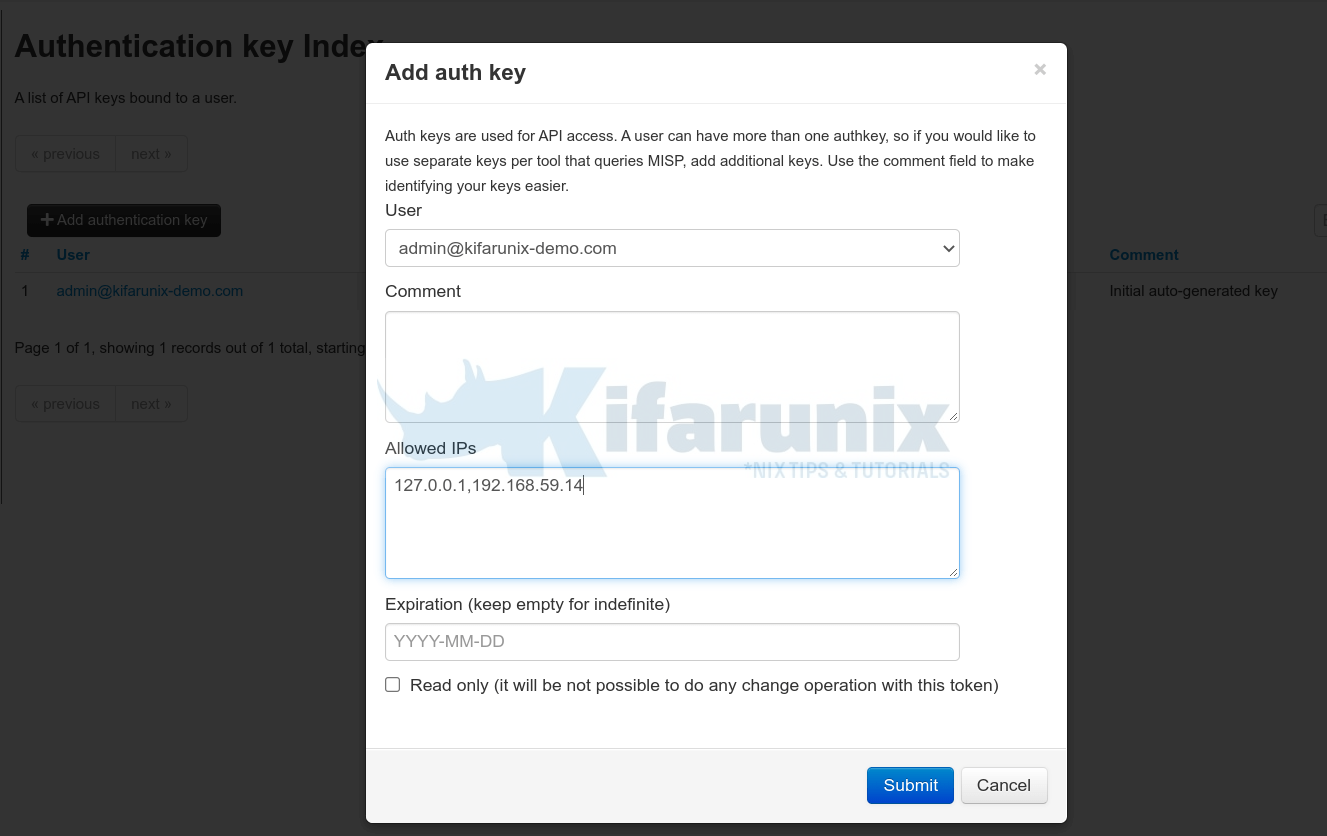
Click Submit to create MISP auth key;
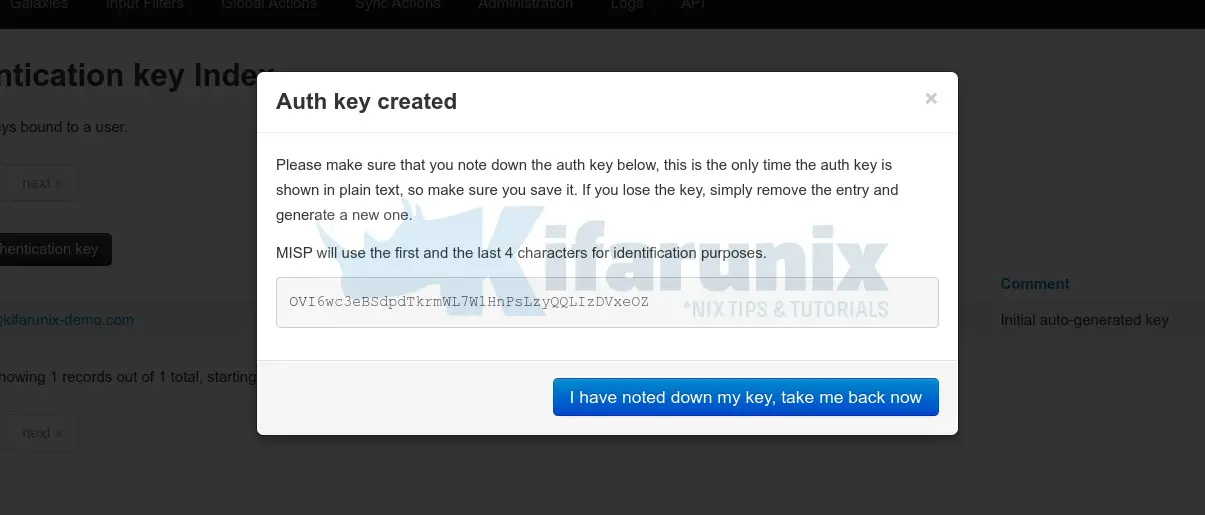
Next, copy and save the key somewhere you would be able to retrieve when needed. Once you click take me back now, you wont be able to see other parts of the key.
Next, open TheHive application configuration file, /etc/thehive/application.conf and uncomment the MISP configuration settings.
Note that we are using TheHive 5 in this guide. Hence the path to configuration files may vary.
Open the application.conf file;
sudo vim /etc/thehive/application.confAnd append the following configs or update if already exists;
# Integrate TheHive with MISP
## MISP configuration
misp {
interval: 2m
servers: [
{
name = "Kifarunix-demo MISP"
url = "https://misp.kifarunix-demo.com"
auth {
type = key
key = "OVI6wc3eBSdpdTkrmWL7W1HnPsLzyQQLIzDVxeOZ"
}
# wsConfig {}
wsConfig.ssl.loose.acceptAnyCertificate: true
# caseTemplate = "<Template_Name_goes_here>"
# tags = ["misp-server-id"]
# max-age = 7 days
# exclusion {
# organisations = ["bad organisation", "other orga"]
# tags = ["tag1", "tag2"]
# }
# whitelist {
# tags = ["tag1", "tag2"]
# }
# includedTheHiveOrganisations = ["*"]
# excludedTheHiveOrganisations = []
}
]
}
Also, ensure TheHive MISP module is enabled;
scalligraph.modules += org.thp.thehive.connector.misp.MispModuleNote, the line
wsConfig.ssl.loose.acceptAnyCertificate: trueAllows us to use either commercially signed or private self-signed certificates. We are using the private self-signed certs generated by MISP installer in this guide.
Restart TheHive service;
sudo systemctl restart thehiveNext, login to TheHive web UI and confirm the integration with MISP.
You should see the MISP icon at the bottom left corner turn to green.
Click on the ICON to view the MISP server details;

TheHive should now be able to pull any events that are published on the MISP.
You can check how to enable default opensource MISP feeds to download events related to known Malwares, APTS, ransomware and their attributes, metadata, IOCs…
If the events are already populated/published int the MISP, TheHive will immediately start to pull those published events as alerts;
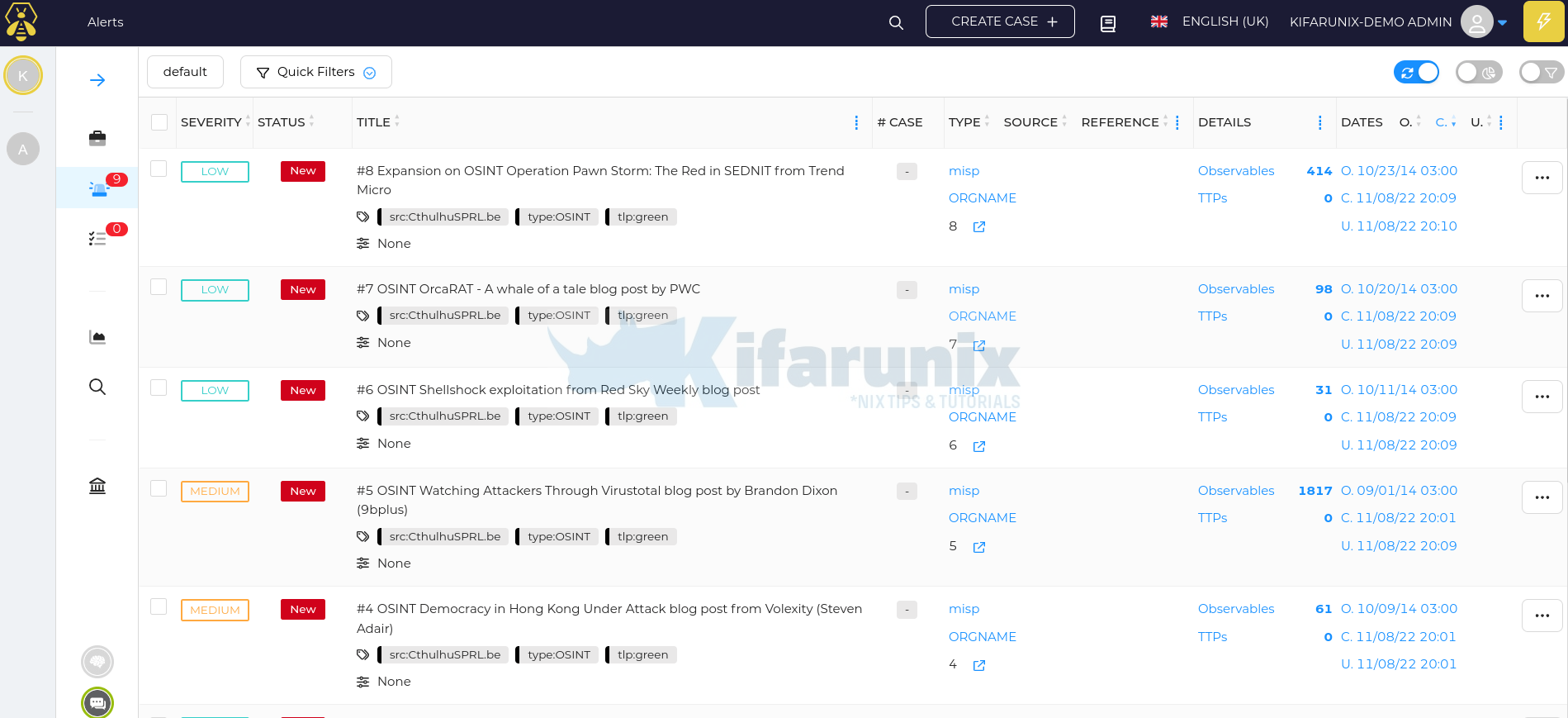
You can go into the preview details of an alert to see more details;
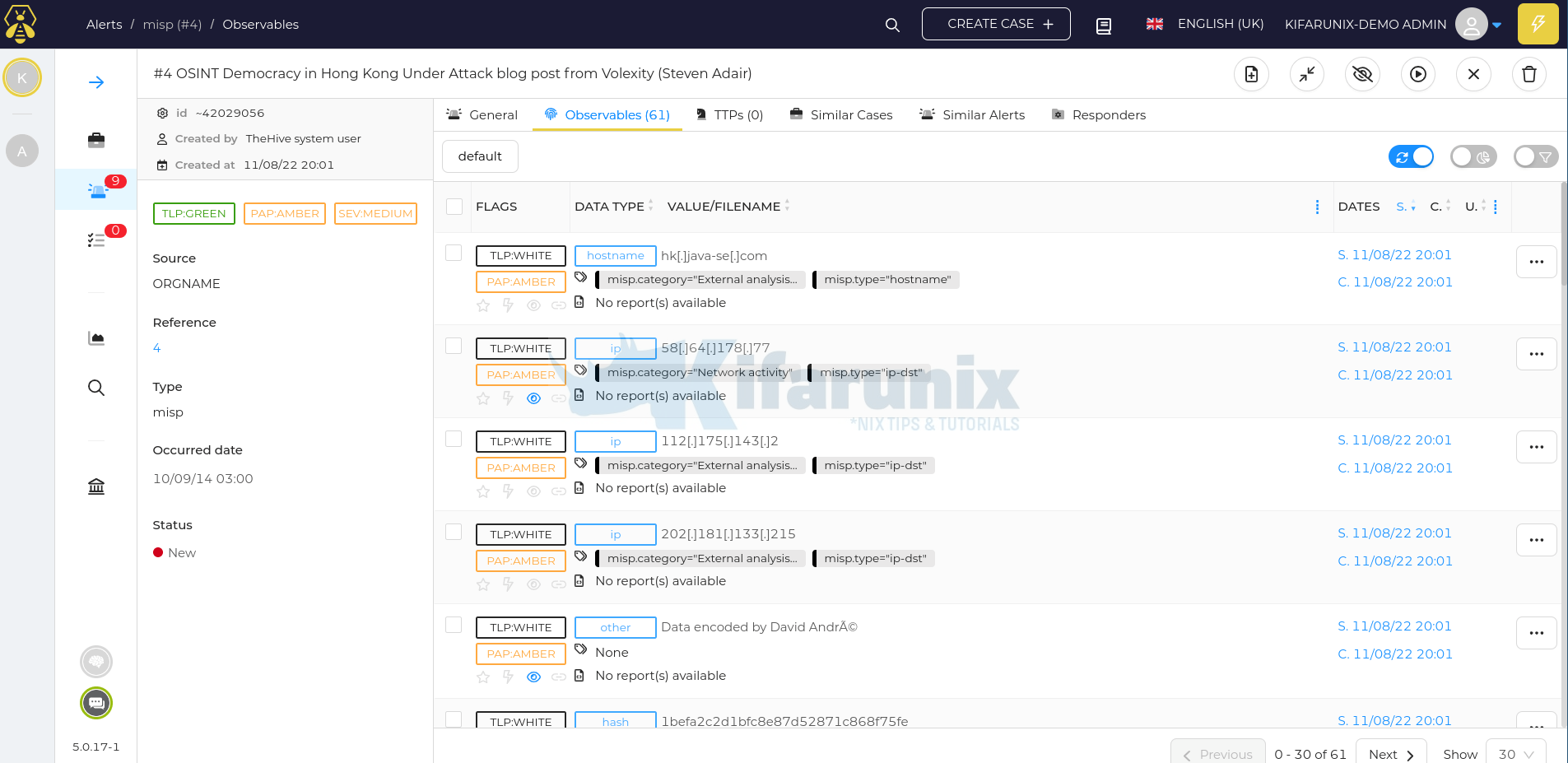
You can define the tags/list of organizations for the events that you want to pull from the MISP on the integration configuration file.
With that kind of integration, any event that is created on the MISP will automatically be pulled and created on TheHive.
And that is it on integrating TheHive with MISP.

