In this tutorial, you will learn how to install Wazuh Manager with ELK on Debian 12. According to the documentation, Wazuh is a free and open source platform for threat detection, security monitoring, incident response and regulatory compliance.
Table of Contents
Installing Wazuh Manager with ELK on Debian 12
Wazuh can be used to monitor endpoints, cloud services and containers, and to aggregate and analyze data from external sources. Wazuh provides the following capabilities:
- Security Analytics
- Intrusion Detection
- Log Data Analysis
- File Integrity Monitoring
- Vulnerability Detection
- Configuration Assessment
- Incident Response
- Regulatory Compliance
- Cloud Security Monitoring
- Containers Security
Install Elastic Stack on Debian 12
In order to fully utilize Wazuh manager capabilities and have a nice UI for visualization, Wazuh has to be integrated with Elastic Stack and to be precise, Kibana, for visualization, Elasticsearch, for data storage and search engine, Filebeat for collecting Wazuh manager event data and pushing them to Elasticsearch search engine.
Thus, in order to install Wazuh manager, you need to begin by setting up Elastic Stack; Kibana, Elasticsearch and Filebeat.
According to the Wazuh components compatibility matrix page, current stable release versions of Wazuh (v4.4.4) supports upto ELK 7.17.9 as of this writing.
This should therefore guide us on the version of Elastic stack to deploy.
To install Elastic Stack 7.17.9 components on Debian 12, proceed as follows.
Install Elastic Stack 7.x APT repositories on Debian 12;
apt updateapt install curl apt-transport-https unzip wget libcap2-bin software-properties-common lsb-release gnupg2wget -qO - https://artifacts.elastic.co/GPG-KEY-elasticsearch \
| sudo gpg --dearmor -o /etc/apt/trusted.gpg.d/elastic.gpgecho "deb https://artifacts.elastic.co/packages/7.x/apt stable main" \
> /etc/apt/sources.list.d/elastic-7.x.listapt updateInstall Elasticsearch 7.17.9 on Debian 12
apt install elasticsearch=7.17.9Configure Elasticsearch
By default, Elasticsearch should just work with the default settings by default. Feel free to check Important Elasticsearch settings.
If Elasticsearch will need to be accessed by other external Beats, then you need to set the IP address and define whether to run in a multi node or single node cluster.
Start and enable Elasticsearch to run on system boot;
systemctl enable --now elasticsearchConfirm the Elasticsearch port is opened;
ss -altnp | grep 9200You can check the status;
systemctl status elasticsearchYou can check the logs if need be. By default, the logs are written to /var/log/elasticsearch/CLUSTER_NAME.log, where CLUSTER_NAME is elasticsearch by default. Thus, the default log file is /var/log/elasticsearch/elasticsearch.log.
Install Kibana 7.17.9 on Debian 12
apt install kibana=7.17.9Configure Kibana
To begin with, set the Kibana server IP address to allow external access. Usually, it only listens on loopback interface.
For example, my server IP address is 192.168.57.102. Thus, to configure Kibana to listen on this host IP address, run the command below (Be sure to change the address as per your setup environment).
sed -i '/server.host:/s/^#//;s/localhost/192.168.57.102/' /etc/kibana/kibana.ymlIf you want to configure Kibana to listen on all interfaces, just use 0.0.0.0 instead of the IP above. For example;
sed -i '/server.host:/s/^#//;s/localhost/0.0.0.0/' /etc/kibana/kibana.ymlWe will use the other settings with the default values.
Start and enable Kibana to run on system boot;
systemctl enable --now kibanaConfirm the Kibana port is opened after a short while.
ss -altnp | grep 5601If need be, check syslog and /var/log/kibana/kibana.log log files.
Open Kibana port on firewall;
If using UFW, run;
ufw allow 5601/tcpIf using iptables;
iptables -I INPUT -p tcp --dport 5601 -j ACCEPTiptables-save > /etc/iptables/rules.v4Install Filebeat on Debian 12
Filebeat is required to forward Wazuh manager alerts and archived events to Elasticsearch. You can install version 7.17.9, currently supported by Wazuh as of this writing, using the command below;
apt install filebeat=7.17.9 -yEnable it to run on boot;
systemctl enable filebeatInstall Wazuh Manager on Debian 12
Next, proceed to install Wazuh server/manager on Debian 12
Install Wazuh APT Repository on Debian 12
Install Wazuh repos using the commands below;
curl -s https://packages.wazuh.com/key/GPG-KEY-WAZUH | \
gpg --dearmor > /etc/apt/trusted.gpg.d/wazuh.gpgecho "deb https://packages.wazuh.com/4.x/apt stable main" > /etc/apt/sources.list.d/wazuh.listUpdate the package information:
apt updateNext, install Wazuh manager on Debian 12.
apt install wazuh-managerOnce the installation is complete, you can start and enable Wazuh-manager to run on system boot;
systemctl enable --now wazuh-managerOpen Wazuh Manager Port on Firewall. Usually, the Wazuh agents is set to communicate with Wazuh manager via TCP port 1514 by default. Thus, open port 1514/tcp on Wazuh manager.
iptables -A INPUT -p tcp --dport 1514 -j ACCEPTOr
ufw allow 1514/tcpAlso, allow port 1515/tcp for agent registration;
iptables -A INPUT -p tcp --dport 1515 -j ACCEPTOr
ufw allow 1515/tcpRead more on required ports.
Integrate Wazuh Manager with ELK Stack
Install Wazuh Manager Kibana App plugin
To install Wazuh manager/server Kibana App, proceed as follows;
chown -R kibana: /usr/share/kibana/pluginsEnsure the plugin version to install is compatible with currently installed version of ELK stack as well as the Wazuh manager installed.
sudo -u kibana /usr/share/kibana/bin/kibana-plugin install \
https://packages.wazuh.com/4.x/ui/kibana/wazuh_kibana-4.4.4_7.17.9-1.zipSample output of the installation;
https://packages.wazuh.com/4.x/ui/kibana/wazuh_kibana-4.4.4_7.17.9-1.zip
Attempting to transfer from https://packages.wazuh.com/4.x/ui/kibana/wazuh_kibana-4.4.4_7.17.9-1.zip
Transferring 38528170 bytes....................
Transfer complete
Retrieving metadata from plugin archive
Extracting plugin archive
Extraction complete
Plugin installation complete
Create Wazuh Kibana data directory and set the ownership to kibana user.
mkdir /usr/share/kibana/datachown -R kibana: /usr/share/kibana/dataRestart Kibana;
systemctl restart kibanaConfigure Filebeat for Wazuh Manager
Make a backup of the default configuration file and replace it with the following configs.
mv /etc/filebeat/filebeat.{yml,stock}cat > /etc/filebeat/filebeat.yml << 'EOL'
output.elasticsearch:
hosts: ["localhost:9200"]
setup.template.json.enabled: true
setup.template.json.path: '/etc/filebeat/wazuh-template.json'
setup.template.json.name: 'wazuh'
setup.ilm.overwrite: true
setup.ilm.enabled: false
filebeat.modules:
- module: wazuh
alerts:
enabled: true
archives:
enabled: false
logging.level: info
logging.to_files: true
logging.files:
path: /var/log/filebeat
name: filebeat
keepfiles: 7
permissions: 0644
logging.metrics.enabled: false
seccomp:
default_action: allow
syscalls:
- action: allow
names:
- rseq
EOL
Install Filebeat Wazuh Module:
wget -qO- https://packages.wazuh.com/4.x/filebeat/wazuh-filebeat-0.2.tar.gz \
| tar -xz -C /usr/share/filebeat/module/Download and install Wazuh alerts Elasticsearch template:
wget -O /etc/filebeat/wazuh-template.json \
https://raw.githubusercontent.com/wazuh/wazuh/4.4/extensions/elasticsearch/7.x/wazuh-template.jsonchmod go+r /etc/filebeat/wazuh-template.jsonTest Filebeat config;
filebeat test configConfig OKTest Filebeat Elasticsearch output;
filebeat test outputelasticsearch: http://localhost:9200...
parse url... OK
connection...
parse host... OK
dns lookup... OK
addresses: 127.0.0.1
dial up... OK
TLS... WARN secure connection disabled
talk to server... OK
version: 7.17.9
Enable Syslog Logging on Debian 12
Note that in the recent base Debian systems, Systemd Journald is now the default logging system. Rsyslog has been made optional and thus, not installed by default.
As a result, you might want to use other mechanisms to read and collect Journald logs using Wazuh.
To make life “easier”, let’s just enable Rsyslog!
Install Rsyslog;
apt install rsyslogStart and enable rsyslog to run on system boot;
systemctl enable --now rsyslogYou now have your usual logs under /var/log/.
To avoid double log storage on the system, just remove Journald log directory;
rm -rf /var/log/journalsystemctl restart systemd-journaldNext, configure Wazuh-manager to include your Syslog logs in its configuration;
vim /var/ossec/etc/ossec.confYou can add these lines in between the <ossec_config> and </ossec_config>;
<localfile>
<log_format>syslog</log_format>
<location>/var/log/syslog</location>
</localfile>
<localfile>
<log_format>syslog</log_format>
<location>/var/log/auth.log</location>
</localfile>
Save and exit the file.
Restart Kibana, Elasticsearch, Filebeat ans Wazuh-manager
The configuration is done!
systemctl restart elasticsearch kibana filebeat wazuh-managerChecking the status of each service;
systemctl status elasticsearch kibana filebeat wazuh-manager
● elasticsearch.service - Elasticsearch
Loaded: loaded (/lib/systemd/system/elasticsearch.service; enabled; preset: enabled)
Active: active (running) since Tue 2023-07-04 15:01:42 EDT; 4min 53s ago
Docs: https://www.elastic.co
Main PID: 49870 (java)
Tasks: 67 (limit: 4642)
Memory: 2.2G
CPU: 1min 2.324s
CGroup: /system.slice/elasticsearch.service
├─49870 /usr/share/elasticsearch/jdk/bin/java -Xshare:auto -Des.networkaddress.cache.ttl=60 -Des.networkaddress.cache.negati>
└─50181 /usr/share/elasticsearch/modules/x-pack-ml/platform/linux-x86_64/bin/controller
Jul 04 15:01:11 wazuh-elk systemd[1]: Starting elasticsearch.service - Elasticsearch...
Jul 04 15:01:42 wazuh-elk systemd[1]: Started elasticsearch.service - Elasticsearch.
● kibana.service - Kibana
Loaded: loaded (/etc/systemd/system/kibana.service; enabled; preset: enabled)
Active: active (running) since Tue 2023-07-04 15:01:10 EDT; 5min ago
Docs: https://www.elastic.co
Main PID: 49805 (node)
Tasks: 11 (limit: 4642)
Memory: 423.9M
CPU: 22.012s
CGroup: /system.slice/kibana.service
└─49805 /usr/share/kibana/bin/../node/bin/node /usr/share/kibana/bin/../src/cli/dist --logging.dest=/var/log/kibana/kibana.l>
Jul 04 15:01:10 wazuh-elk systemd[1]: Started kibana.service - Kibana.
● filebeat.service - Filebeat sends log files to Logstash or directly to Elasticsearch.
Loaded: loaded (/lib/systemd/system/filebeat.service; enabled; preset: enabled)
Active: active (running) since Tue 2023-07-04 15:01:10 EDT; 5min ago
Docs: https://www.elastic.co/beats/filebeat
Main PID: 49789 (filebeat)
Tasks: 7 (limit: 4642)
Memory: 33.2M
CPU: 198ms
CGroup: /system.slice/filebeat.service
└─49789 /usr/share/filebeat/bin/filebeat --environment systemd -c /etc/filebeat/filebeat.yml --path.home /usr/share/filebeat>
Jul 04 15:01:10 wazuh-elk systemd[1]: Started filebeat.service - Filebeat sends log files to Logstash or directly to Elasticsearch..
● wazuh-manager.service - Wazuh manager
Loaded: loaded (/lib/systemd/system/wazuh-manager.service; enabled; preset: enabled)
Active: active (running) since Tue 2023-07-04 15:01:37 EDT; 6min ago
Process: 50102 ExecStart=/usr/bin/env /var/ossec/bin/wazuh-control start (code=exited, status=0/SUCCESS)
Tasks: 112 (limit: 4642)
Memory: 315.9M
CPU: 30.736s
CGroup: /system.slice/wazuh-manager.service
├─50204 /var/ossec/framework/python/bin/python3 /var/ossec/api/scripts/wazuh-apid.py
├─50244 /var/ossec/bin/wazuh-authd
├─50261 /var/ossec/bin/wazuh-db
├─50285 /var/ossec/bin/wazuh-execd
├─50299 /var/ossec/bin/wazuh-analysisd
├─50311 /var/ossec/bin/wazuh-syscheckd
├─50357 /var/ossec/bin/wazuh-remoted
├─50405 /var/ossec/bin/wazuh-logcollector
├─50413 /var/ossec/framework/python/bin/python3 /var/ossec/api/scripts/wazuh-apid.py
├─50416 /var/ossec/framework/python/bin/python3 /var/ossec/api/scripts/wazuh-apid.py
├─50430 /var/ossec/bin/wazuh-monitord
└─50452 /var/ossec/bin/wazuh-modulesd
Jul 04 15:01:27 wazuh-elk env[50102]: Started wazuh-db...
Jul 04 15:01:28 wazuh-elk env[50102]: Started wazuh-execd...
Jul 04 15:01:30 wazuh-elk env[50102]: Started wazuh-analysisd...
Jul 04 15:01:31 wazuh-elk env[50102]: Started wazuh-syscheckd...
Jul 04 15:01:32 wazuh-elk env[50102]: Started wazuh-remoted...
Jul 04 15:01:33 wazuh-elk env[50102]: Started wazuh-logcollector...
Jul 04 15:01:34 wazuh-elk env[50102]: Started wazuh-monitord...
Jul 04 15:01:35 wazuh-elk env[50102]: Started wazuh-modulesd...
Jul 04 15:01:37 wazuh-elk env[50102]: Completed.
Jul 04 15:01:37 wazuh-elk systemd[1]: Started wazuh-manager.service - Wazuh manager.
Accessing Wazuh App on Kibana Web Interface
You can now access Kibana via the url http://<server-IP-or-hostname>:5601.
On the UI, click Explore on my own and under the Kibana menu section, you should be able to see Wazuh App.
When you click on the APP, you should see such dashboard.
No agents are connected by default. However, there should be some default events already collected from the Wazuh manager.
For example head over to Modules > Security Events >Dashboard or Events;
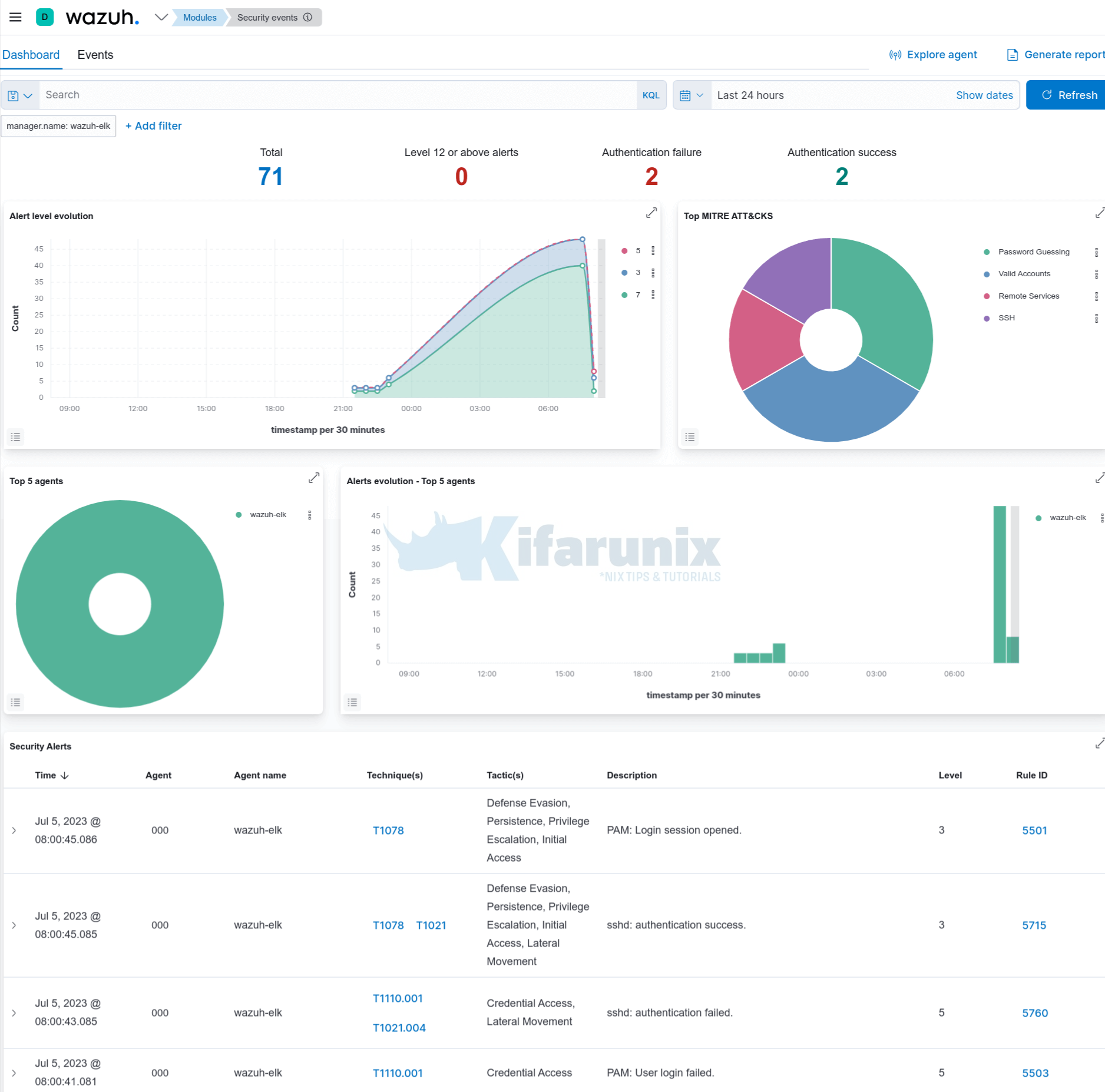
Install Wazuh Agents
You can now go ahead and install Wazuh agents and start log collection from your end points.
Easy Way to Install Wazuh Agents on Ubuntu/Debian
Install Wazuh Agent on Rocky Linux 8
That marks the end of our tutorial on installing Wazuh manager with ELK on Debian 12.
Other Tutorials
Monitor Process Creation Events on Windows Systems using Wazuh and ELK stack

