This blog post serves as an introduction to Role-Based Access Control (RBAC) in Kubernetes. It is no doubt that currently, Kubernetes is the de facto standard for container orchestration. With its growing popularity, it is imperative to ensure access to its resources is restricted and controlled. This is where Role-Based Access Control (RBAC) comes in.
Table of Contents
Introduction to Role-Based Access Control (RBAC) in Kubernetes
What is Role-Based Access Control (RBAC)?
Role-Based Access Control (RBAC) is a security framework that controls access to resources based on pre-defined policies/roles assigned to users, groups or service accounts in a system. In the context of Kubernetes, RBAC allows admins to define a granular permissions for users, groups and processes that ensure that they ONLY have access to the resources they need to perform their tasks.
Why RBAC in Kubernetes?
Considering Kubernetes forms part of your critical infrastructure, you wouldn’t grant unrestricted access to it, would you? Hence, in a Kubernetes cluster, RBAC is used to:
- Implement the Principle of Least Privilege: This ensures that users, groups, or service accounts in a Kubernetes cluster have necessary permissions to access a set of Kubernetes resources, thus reducing the risk of unauthorized access. For example, limiting access to specific resources per namespace…
- Improve auditability: RBAC ensures that there is a clear audit trail, allowing you to track who did what, when, and on which resource. This facilitates troubleshooting and helps identify security breaches.
- Enhance Security: RBAC makes it hard for an attacker or malicious user to gain access or escalate privileges within a Kubernetes cluster and therefore this reduces attack surface.
- Isolate Namespaces: Kubernetes utilizes namespaces to logically group resources. RBAC strengthens this isolation by ensuring users and services within a namespace can’t see or modify resources in other namespaces unless explicitly granted permission. This helps prevent accidental cross-contamination or unauthorized access across projects.
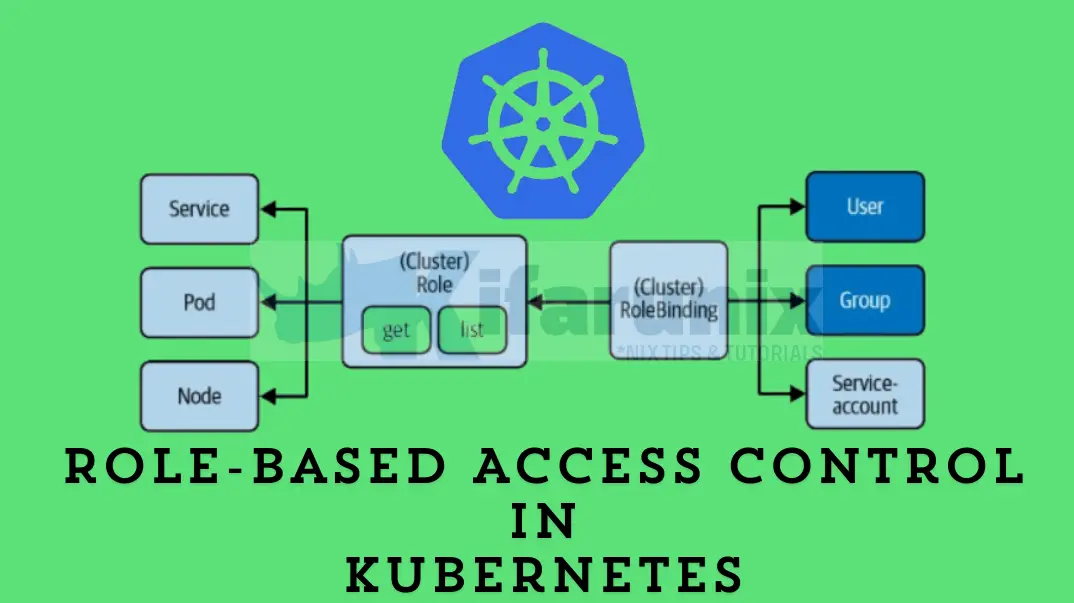
Building Blocks of RBAC in Kubernetes
Kubernetes RBAC uses three components to define permissions and access controls. These components include:
- Subject
- Resource
- Verb
These components form the basis of RBAC policies and enable administrators to granularly control access to Kubernetes resources.
So, what does these components represent exactly in a Kubernetes cluster?
Subjects: Who’s Requesting Access?
Subjects represent the entities asking for permission to interact with Kubernetes resources. They can be:
- Users: Individual human users authenticated to access the cluster.
- Groups: Collections of users with similar roles or responsibilities.
- Service Accounts: Identities used by pods or applications running within the cluster to access other resources.
Subjects are linked to roles or cluster roles through RoleBindings and ClusterRoleBindings respectively, defining their permitted actions.
Resources: What Data is Being Accessed?
Resources are the objects managed by the Kubernetes API, like pods, services, deployments, etc. Some examples include:
- Pods: Individual instances of running containers.
- Services: Provide network access to sets of pods.
- Deployments: Manage replicated sets of pods for high availability and scalability.
- ConfigMaps: Store configuration data (key-value pairs) used by pods or other resources.
Verbs: What Actions are Allowed?
Verbs specify the actions/operations a subject can perform on a Kubernetes resource. Common verbs include:
- get: Retrieve information about a resource. ( like “read”)
- list: Retrieve a list of resources matching certain criteria. (like “browse”)
- create: Create new resources. (like “add”)
- update: Modify existing resources. (like “edit”)
- delete: Delete resources. (like “remove”)
By defining specific verbs, administrators can precisely control what a subject can do within the cluster.
RBAC Implementation in Kubernetes
As stated above, Kubernetes subjects are linked to roles or cluster roles through RoleBindings and ClusterRoleBindings respectively, which defines their permitted actions. This is what is called, Kubernetes RBAC API primitives/Kubernetes objects and they are the foundational elements used to implement RBAC in Kubernetes.
So, what are these objects?
Role
A role is a Kubernetes object that defines a set of permissions for specific tasks within a namespace. They outline the “what” (actions) a user, a group or service can do within the cluster. For example, you could create a role that allows users to create, delete, or modify Pods within a specific namespace.
ClusterRole
ClusterRole object defines a set of permissions for running specific tasks cluster-wide. They define permissions that apply across all namespaces. ClusterRoles are useful when you want to grant permissions that span multiple namespaces or affect cluster-level resources like Nodes or PersistentVolumes.
Some of the default user-facing Kubernetes roles include;
- cluster-admin: Grants complete control over all resources in the entire cluster, including all namespaces. Use with extreme caution!
- admin: Intended for use within a specific namespace using a RoleBinding. It allows read/write access to most resources within that namespace, but excludes modifying the namespace itself or resource quotas.
- edit: Offers read/write access to most objects within a namespace, but it cannot view or modify RBAC configurations (roles and role bindings). It can access Secrets and run Pods as any ServiceAccount, potentially enabling privilege escalation.
- view: Provides read-only access to most objects within a namespace. It cannot view RBAC configurations or Secrets to prevent unauthorized access to ServiceAccount credentials.
RoleBinding
A RoleBinding is used to bind a Role to one or more users, groups, or service accounts within a namespace. It associates the permissions defined in the Role with specific entities, allowing those entities to perform the actions specified by the Role. For example, you could create a RoleBinding that grants a particular group of users read-only access to Pods within a namespace.
ClusterRoleBinding
Similar to a RoleBinding, a ClusterRoleBinding binds a ClusterRole to one or more users, groups, or service accounts. However, ClusterRoleBindings apply cluster-wide, allowing you to grant permissions defined in a ClusterRole to entities across all namespaces in the cluster.
While Roles and Role Bindings operate at the namespace level, ClusterRoles and ClusterRole Bindings function at the cluster-wide level.
Kubernetes RBAC Best Practices
Implementing Role-Based Access Control (RBAC) in a Kubernetes environment requires adherence to several best practices to ensure effective access management, security, and governance. Here are some good practices to consider:
- Utilize Least Privilege Principle: Grant users and services only the bare minimum permissions they need to perform their specific tasks within a namespace. This minimizes the risk of damage from accidental or malicious actions.
- Clear Role Definitions: Define roles with well-defined and documented permissions. This ensures everyone understands the actions each role can perform. Use descriptive names for roles and avoid overly broad permissions.
- Separate Responsibilities: Consider separating duties by assigning users different roles for different tasks. This reduces the risk of a compromised account granting complete access.
- Leverage Built-in Roles: Kubernetes offers pre-defined roles like “admin,” “edit,” and “view.” Use these roles whenever possible instead of creating custom roles with excessive permissions.
- Minimize Cluster-Wide Access: ClusterRoleBindings grant access across all namespaces. Use them sparingly as they bypass namespace isolation. Prefer RoleBindings for granting access within specific namespaces.
- Regular Reviews and Updates: Regularly review and update RBAC configurations to ensure they reflect current needs. Revoke unused permissions and adjust roles as user responsibilities evolve.
- Automation for Efficiency: Consider using automation tools to manage RBAC configurations. This can streamline the process and reduce human error.
- Detailed Audit Logging: Enable audit logging for RBAC actions to track who did what, when, and on which resource. This facilitates troubleshooting and helps identify suspicious activity.
- Limited Service Account Permissions: Service accounts represent applications or pods. Ensure service accounts have the minimum necessary permissions to function effectively.
- Educate Your Users: Educate users about RBAC principles and best practices. This helps them understand their access levels and promotes responsible behavior within the cluster.
- Stay Current with Security: Keep your cluster and RBAC configurations up-to-date with the latest security best practices.
Conclusion
In conclusion, Role-Based Access Control (RBAC) is a fundamental aspect of Kubernetes security, enabling organizations to effectively manage access to cluster resources. By understanding RBAC concepts and implementing best practices, administrators can strengthen security, maintain compliance, and ensure the integrity of their Kubernetes deployments. As Kubernetes continues to evolve, RBAC will remain a critical tool for safeguarding containerized workloads and enabling secure, scalable application delivery.

