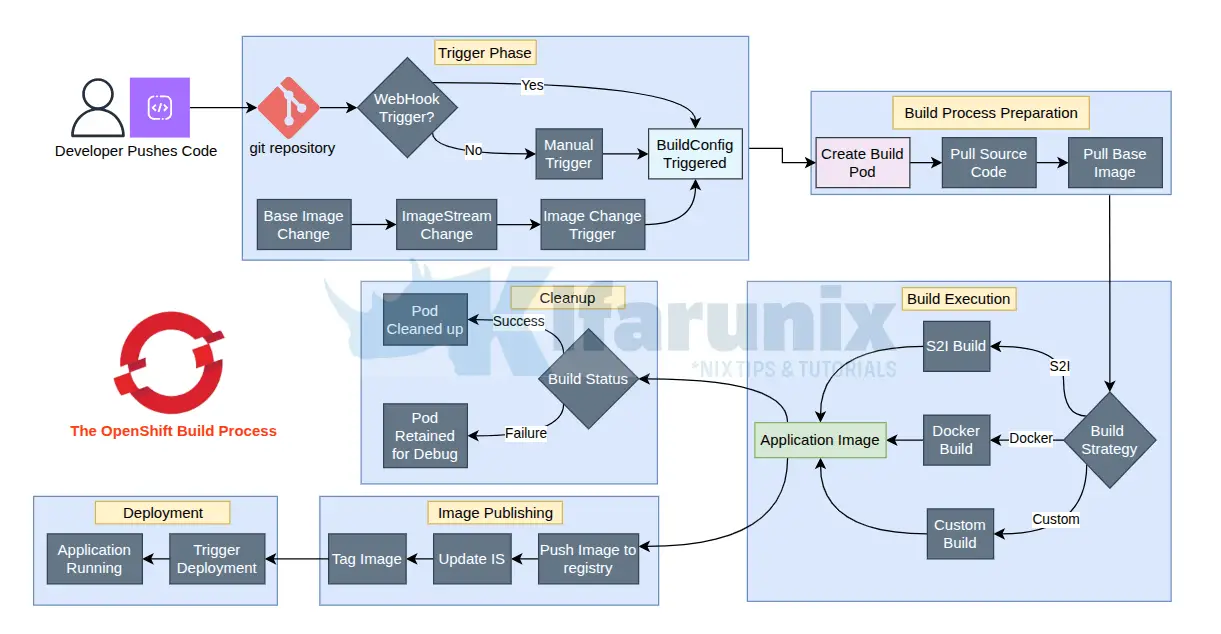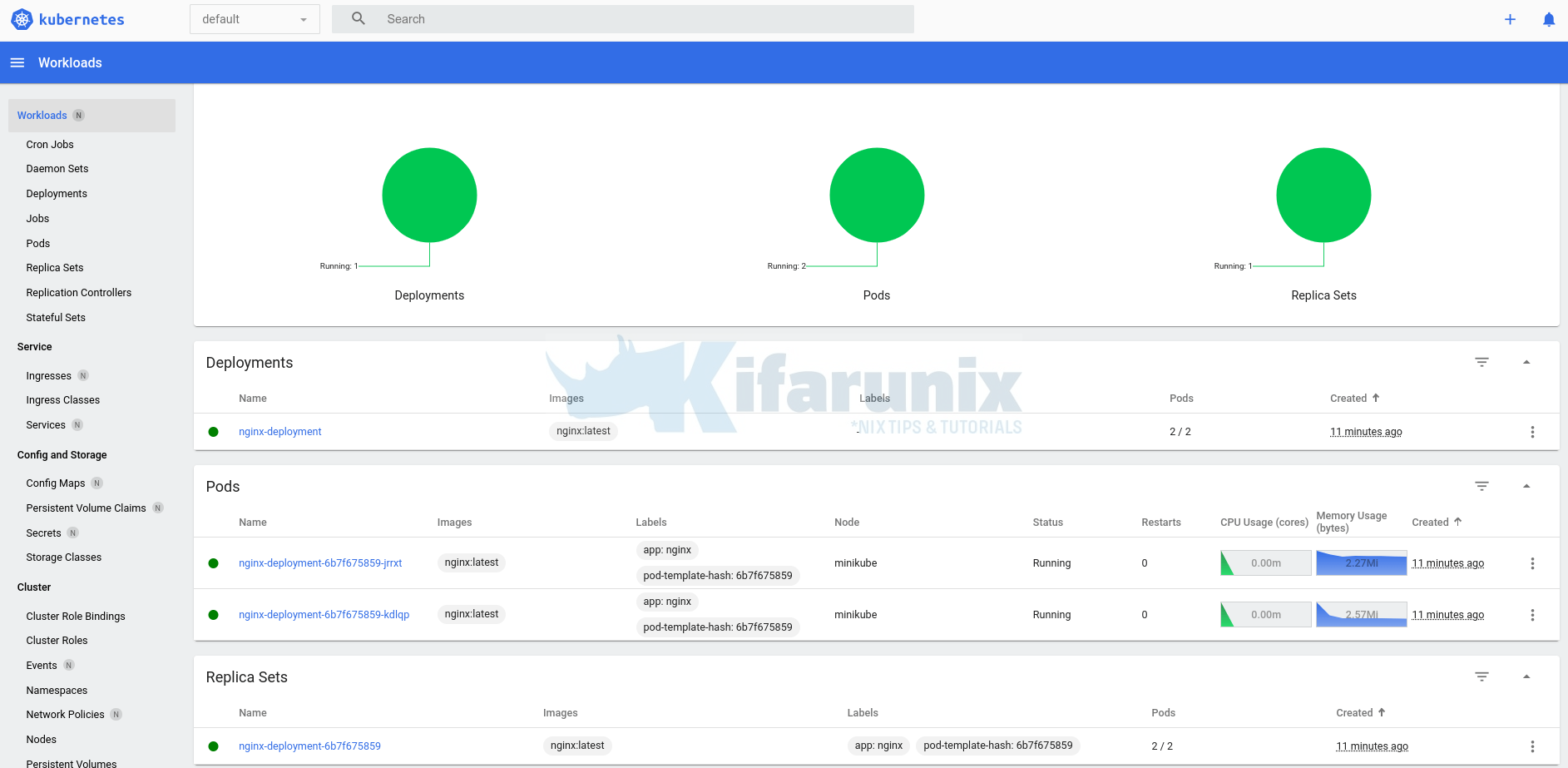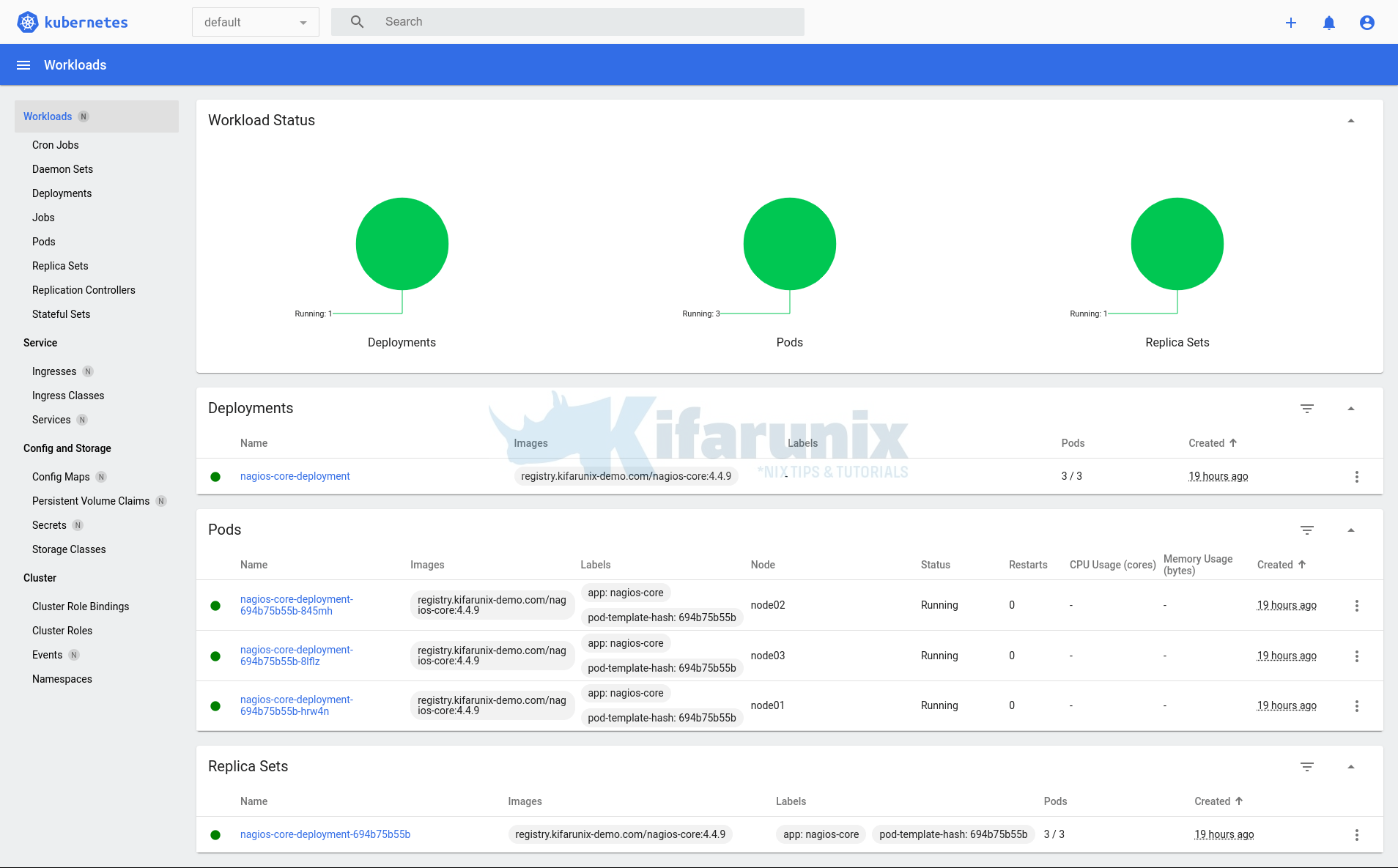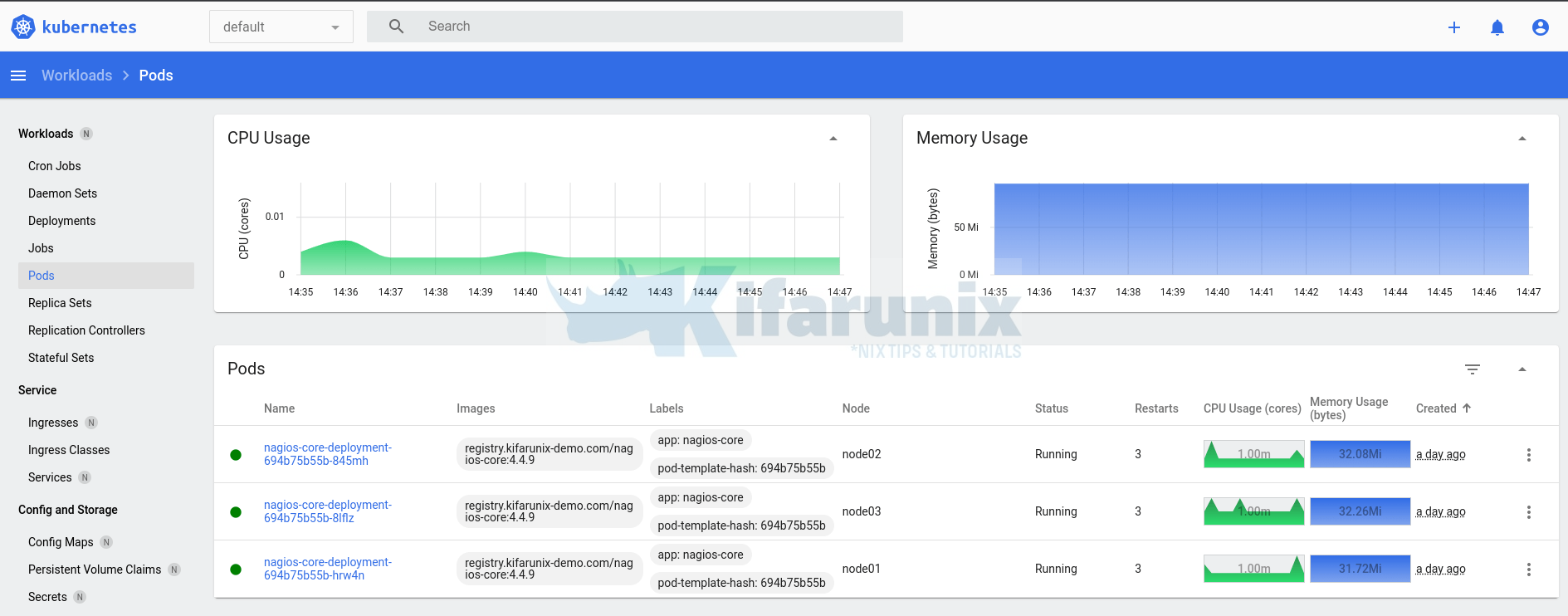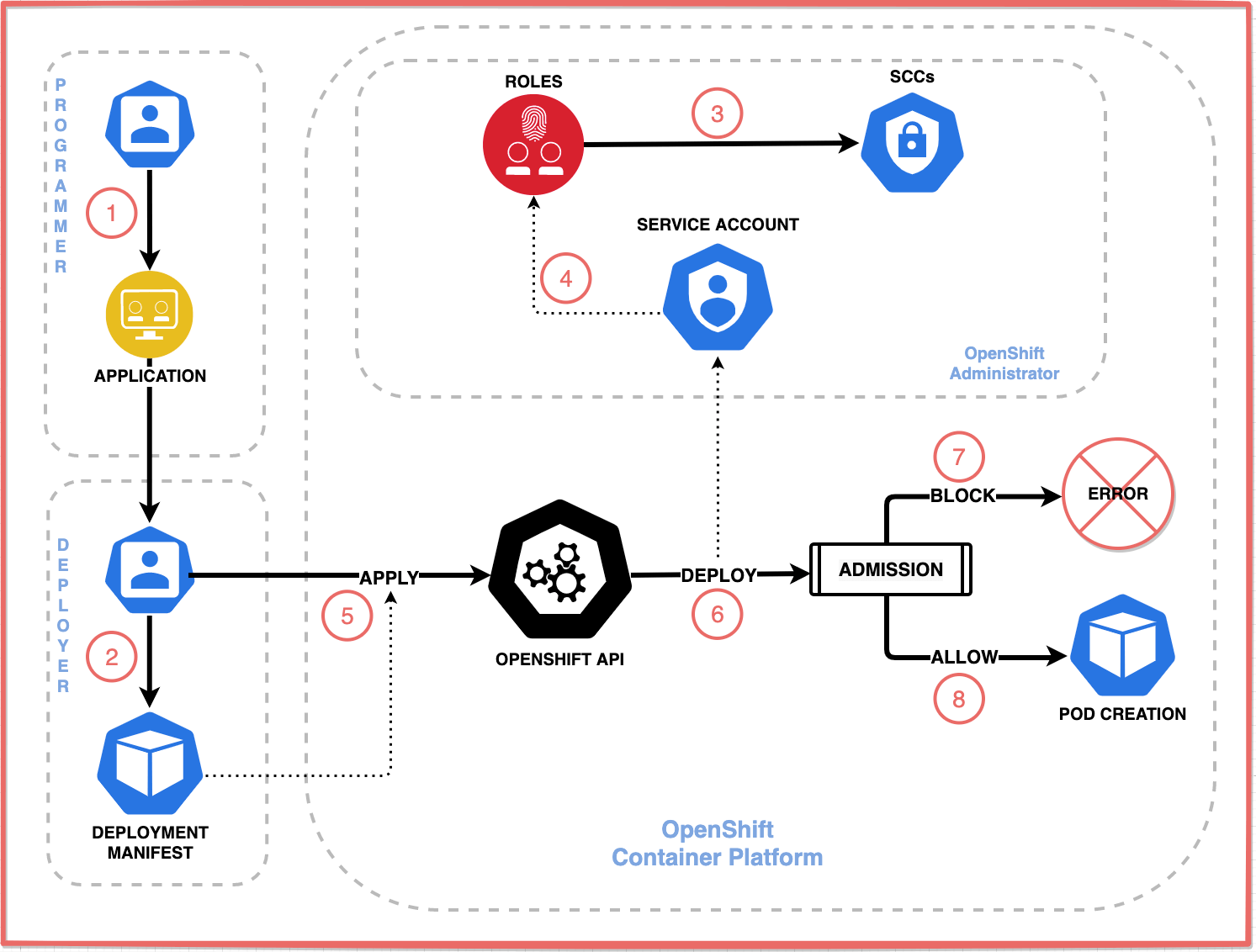
Control OpenShift Pod Permissions with SCCs and Service Accounts

Install OpenStack on Ubuntu 24.04 using Kolla Ansible

Provision Block Storage for Kubernetes on Rook Ceph Cluster

Security, HowTos, Monitoring
How to Integrate TheHive with MISP
Monitoring, Telegraf, TIG stack
Install and Configure Telegraf on FreeBSD 12

HowTos, Apache, Nginx, PHP
How to Install PHP 7.3.3 on Ubuntu 18.04
Monitoring, Elastic Stack, HowTos
Deploy ELK Stack 8 on Docker Containers
HowTos, Ubuntu 18.04
How to Setup APT-Caching Server Using Apt-Cacher NG on Ubuntu 18.04
Install Icinga 2 on Debian 10 Buster
In this guide, we are going to learn how to install Icinga 2 on Debian …

Monitor Linux Hosts using Nagios check_by_ssh Plugin
Welcome to our tutorial on how to monitor Linux Hosts using Nagios check_by_ssh plugin. This …
Visualize ClamAV Scan Logs on ELK Stack Kibana
In this tutorial, you will learn how to visualize ClamAV scan logs on ELK stack …

Install ntopng on Rocky Linux 8
This guide will take you through how to install ntopng on Rocky Linux 8. ntopng …

Install Filebeat on Fedora 30/Fedora 29/CentOS 7
In this guide, we are going to learn how to install Filebeat on Fedora 30/Fedora …

Install OSSEC Agent on Rocky Linux 8
This guide presents a step-by-step tutorial on how to install OSSEC Agent on Rocky Linux …
How to Enable Basic Authentication on ELK Stack
In this tutorial, you will learn how to enable basic authentication on ELK stack. Elastic/ELK …

Install Sensu Go on Debian 11
Follow through this tutorial to learn how to install Sensu Go on Debian 11. Sensu …

How to Monitor Linux System Metrics using Sensu
In this tutorial, you will learn how to monitor Linux system metrics using Sensu. Sensu is …
How to Upgrade ELK Stack 7.x to ELK Stack 8.x
How to upgrade Elasticsearch 7 to 8? In this guide, you will learn how to …

How to Install Arkime with Elasticsearch 8 on Ubuntu 24.04

Install Zabbix Server on Rocky Linux

Install ELK Stack on Ubuntu 20.04
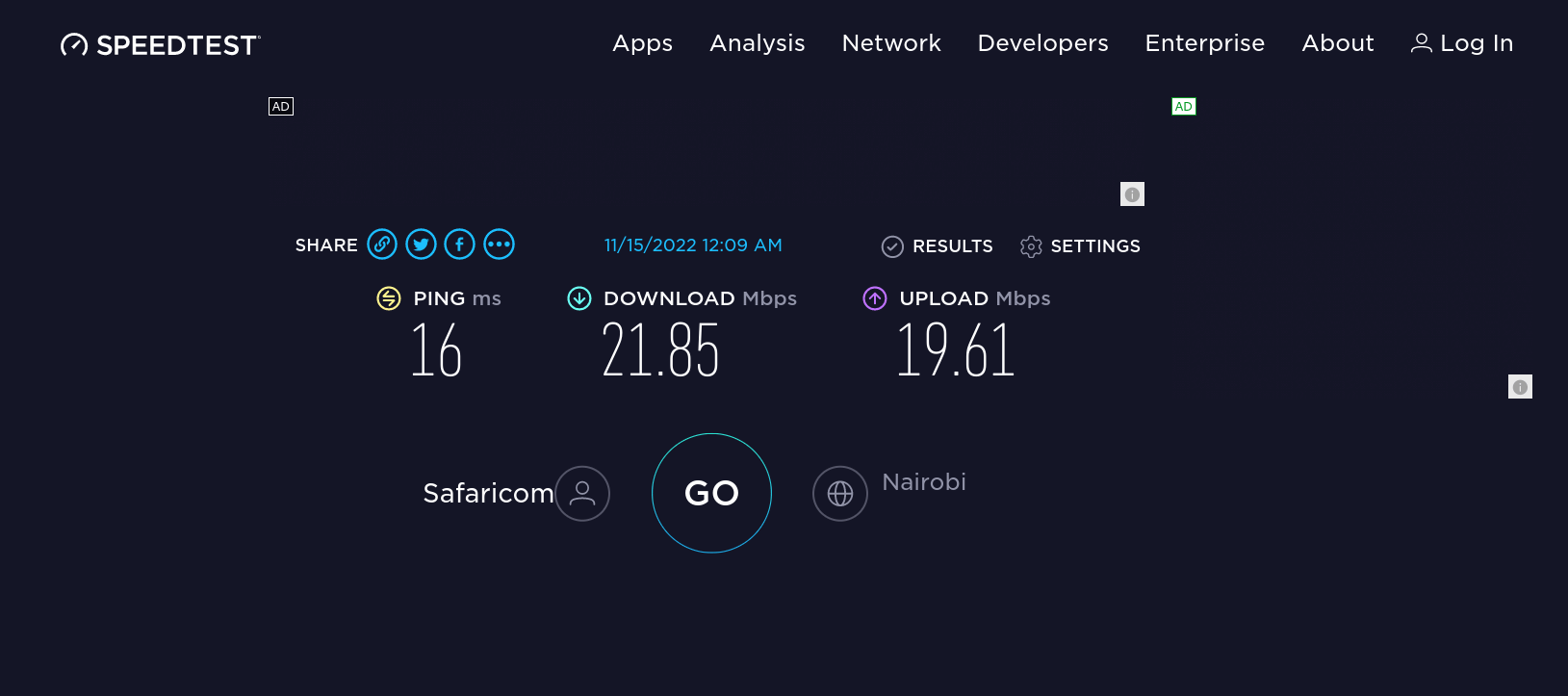
Easy way to Test Internet Speed on Linux Terminal

Connect to WiFi in Linux Using NMCLI command
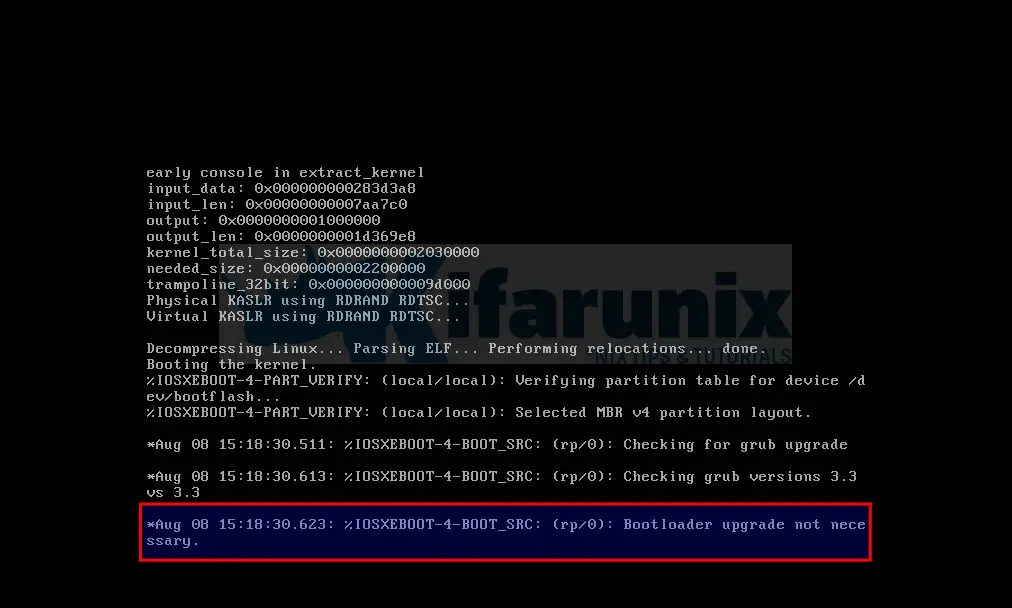
Cisco Catalyst 8000v Edge Stuck on Bootloader upgrade not Necessary

Install and use NMCLI tool on Debian Linux

Analyze PCAP Files using Malcolm Network Traffic Analysis tool

Install Latest Wireshark on Ubuntu 18.04
Configure Static IP Addresses using Netplan on Ubuntu

Install Wireshark on Ubuntu 22.04

Useful Facts About Setting Up Mobile Rugged Servers
Set Static Routes via an Interface/IP on CentOS/Ubuntu
Create Virtual/Secondary IP addresses on an Interface in Linux
Install and Setup OpenVPN Server on Fedora 29/CentOS 7

Upgrade VirtualBox 6.x to VirtualBox 7.x on Ubuntu/Debian
In this tutorial, you will learn how to upgrade VirtualBox 6.x to VirtualBox 7.x on …

How to Create And Delete OpenStack Project
In this blog post, we’ll provide a step by step tutorial on how to create …

Install VirtualBox Guest Additions on Oracle Linux 9
Follow through this tutorial to learn how to install VirtualBox guest additions on Oracle Linux …

Install VirtualBox Guest Additions on Ubuntu 21.04
If you have installed Ubuntu 21.04 on VirtualBox, you realize that it is not in …
Install Wubuntu Linux on VirtualBox
Follow through this guide to learn how to install Wubuntu Linux on VirtualBox. According to …

Install Portainer on Debian 11/Debian 10
In this tutorial, you will learn how to install Portainer on Debian 11/Debian 10. Portainer is …
Install Ubuntu 20.04 on VirtualBox
Follow through this guide to learn how to install Ubuntu 20.04 on VirtualBox. Well, Ubuntu …

Install and Setup Security Onion on VirtualBox
In this tutorial, you will learn how to install and setup Security Onion on VirtualBox. …

Easy Way to Decrease/Shrink KVM Virtual Machine Disk Size
In this tutorial, you will learn an easy way to decrease/shrink KVM virtual machine disk …

Upgrade Kali Linux 2021.3 to 2021.4
Learn how to upgrade Kali Linux 2021.3 to 2021.4. Kali Linux 2021.4 has just been …

Easy Way to Decrease/Shrink KVM Virtual Machine Disk Size

Easy way to Install Linux Mint 21 on VirtualBox