This guide will take you through how to process ModSecurity logs using Wazuh. ModSecurity WAF can be integrated with Wazuh in order to process the generated alert logs for better analysis and visualization.
Process ModSecurity Logs using Wazuh
Install and setup Wazuh server;
If not already configured, use the guides below to install and setup Wazuh;
Install and Configure Wazuh Manager on Ubuntu 22.04
Install Wazuh Server on Rocky Linux 8
Install and Configure ModSecurity WAF
On you web servers, you need to install and activate ModSecurity WAF to protect your web server against attacks. You can use the guides below on how to install and configure ModSecurity WAF;
Install ModSecurity with Apache on Ubuntu 22.04
Install ModSecurity 3 with Apache in a Docker Container
Modsecurity Logging
By default, ModSecurity logs attack related logs to HTTP server Error log file or to the ModSecurity audit logs file.
In order to be able to process the ModSecurity Logs using Wazuh, the logs that are written to the HTTP server needs to be collected using Wazuh agent and pushed to the Wazuh manager for processing.
In my current setup, my Modsecurity WAF is logging to Apache Error log file;
grep denied /var/log/apache2/error.logSample log;
[Sat Apr 30 23:42:36.559613 2022] [:error] [pid 4504:tid 140114027435584] [client 127.0.0.1:57026] [client 127.0.0.1] ModSecurity: Access denied with code 403 (phase 2). Matched phrase "bin/ls" at ARGS:doc. [file "/etc/modsecurity/crs/rules/REQUEST-932-APPLICATION-ATTACK-RCE.conf"] [line "518"] [id "932160"] [msg "Remote Command Execution: Unix Shell Code Found"] [data "Matched Data: bin/ls found within ARGS:doc: /bin/ls"] [severity "CRITICAL"] [ver "OWASP_CRS/3.2.0"] [tag "application-multi"] [tag "language-shell"] [tag "platform-unix"] [tag "attack-rce"] [tag "paranoia-level/1"] [tag "OWASP_CRS"] [tag "OWASP_CRS/WEB_ATTACK/COMMAND_INJECTION"] [tag "WASCTC/WASC-31"] [tag "OWASP_TOP_10/A1"] [tag "PCI/6.5.2"] [hostname "localhost"] [uri "/"] [unique_id "Ym2fPFtd6Nody7X50nHgUwAAAAA"]Configure Wazuh Agent to Read ModSecurity Logs
Thus, you can now configure Wazuh agents to read the Apache error log and push the ModSecurity events to the Wazuh manager for processing.
vim /var/ossec/etc/ossec.confWithin the <ossec_config> and </ossec_config>, paste the configuration lines below;
<localfile>
<log_format>apache</log_format>
<location>/var/log/apache2/access.log</location>
</localfile>
<localfile>
<log_format>apache</log_format>
<location>/var/log/apache2/error.log</location>
</localfile>
Save and exit the file;
Check for any syntax error;
/var/ossec/bin/wazuh-syscheckdExit status is 0 if no error.
Restart Wazuh agent;
systemctl restart wazuh-agentVerify Wazuh ModSecurity Log Processing
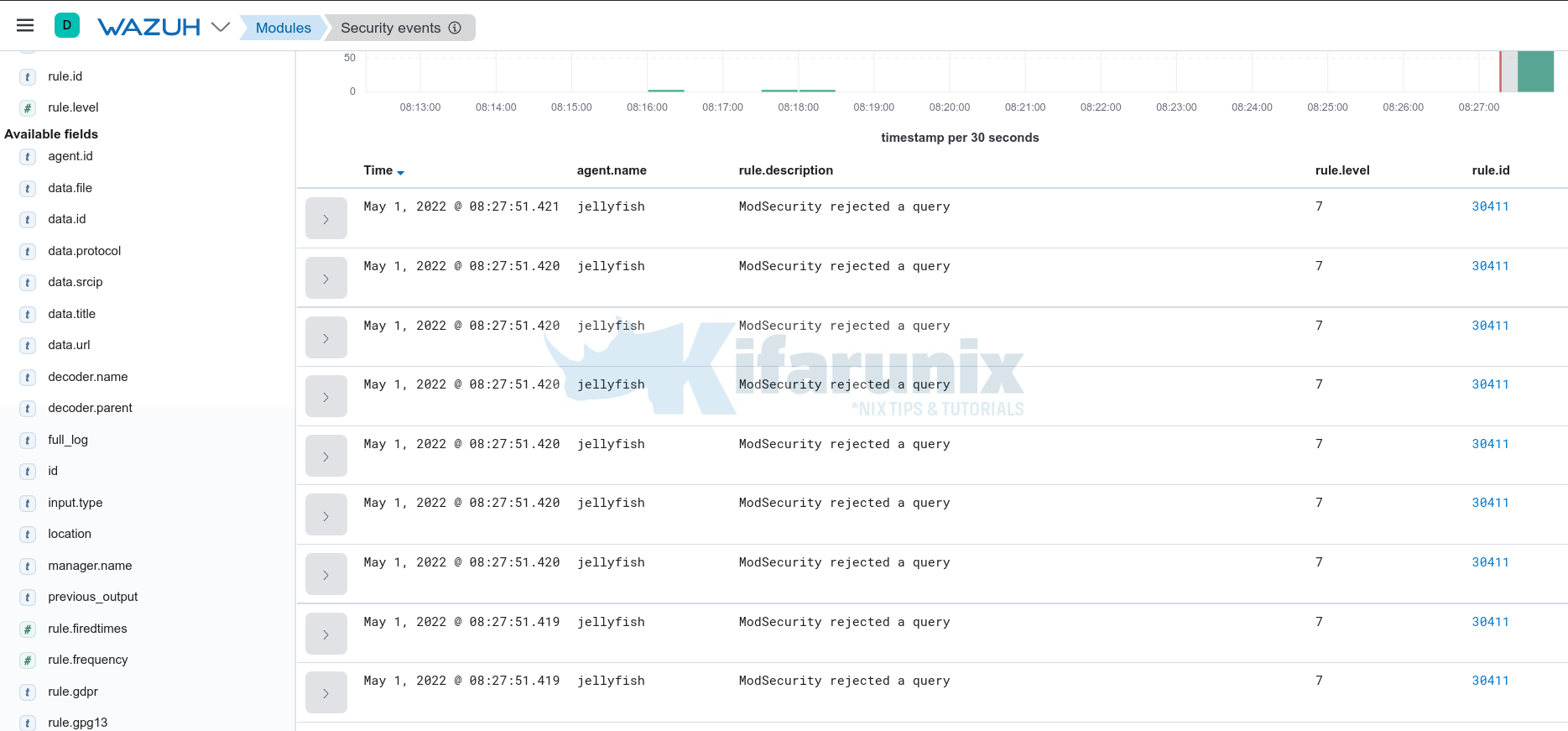
By default, Wazuh manager ships with ruleset that can process ModSecurity events for better visualization and analysis.
Thus, navigate to Wazuh web interface and check the events related to the Wazuh agent shipping the ModSecurity logs.
Sample events;
Expanding the event;
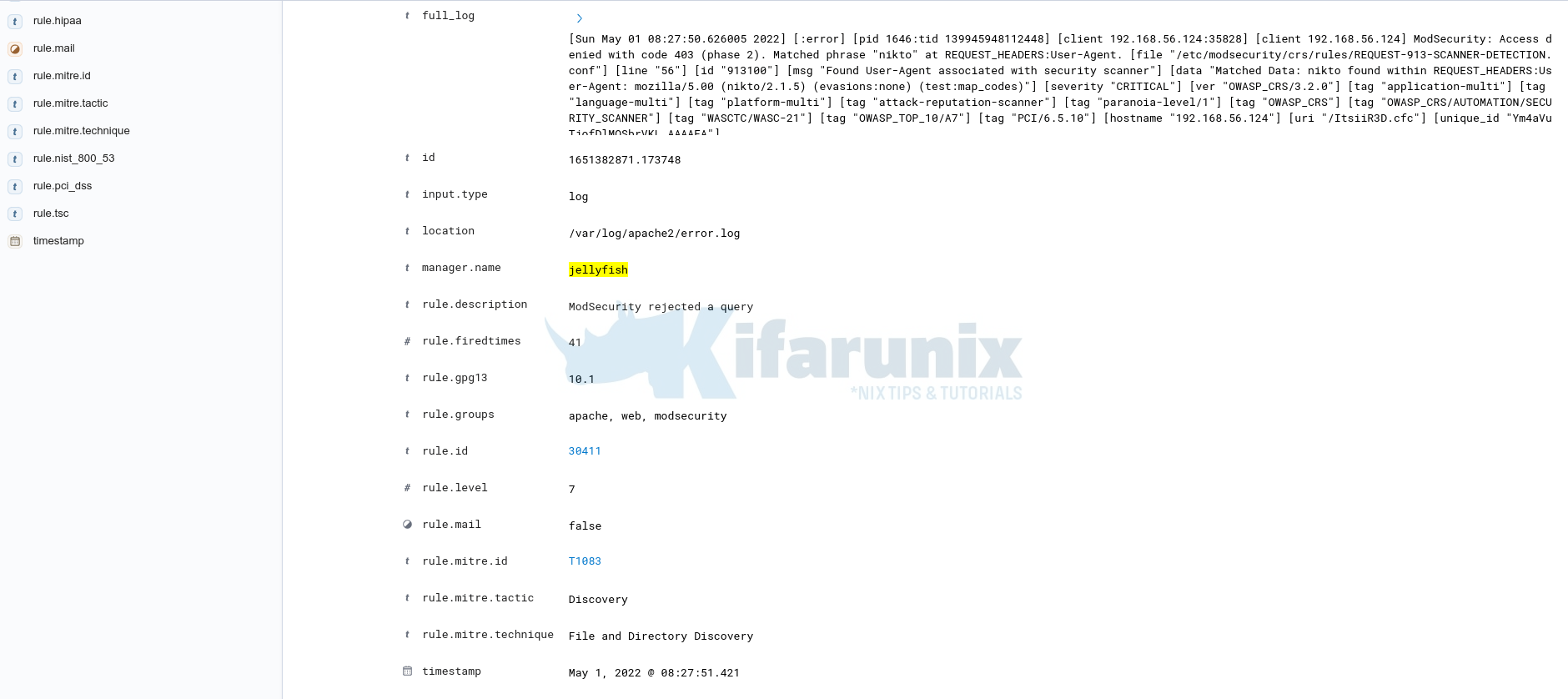
And that is how you can use Wazuh to process ModSecurity Logs.
Want to apply further processing to ModSecurity logs? Check the guide below;
Process and Visualize ModSecurity Logs on ELK Stack
Other Tutorials
Create Kibana Visualization Dashboards for ModSecurity Logs
Restrict Access to WordPress Login Page to Specific IPs with libModSecurity