In this tutorial, you will learn how to deploy NRPE agent as a Docker container. Docker containers have revolutionized how applications are deployed! They make it easy to develop, ship, and run applications. The beauty of this is it doesn’t matter your OS distro, as long as you are able to install Docker on it, the application build as Docker containers are portable and can be ran on any OS.
In our previous guide, we learnt how to deploy Nagios as a Docker container. You can have a look;
Deploy Nagios as a Docker Container
Deploying NRPE Agent as a Docker Container
Install Docker Engine
Begin by installing Docker on your Linux host system.
You can follow the links below to guide you on how to install Docker on various Linux distros;
Install Docker on Rocky Linux 8
Install Docker CE on Ubuntu 20.04
Install and Use Docker on Debian 10 Buster
Create and Build NRPE Docker Image
Once you have Docker packages installed, proceed to create and build your custom NRPE docker image.
You can create a directory, say under /opt for example, where you can store all necessary files that we will create for the purposes of creating NRPE Docker image. You can name the directory however you want!
mkdir /opt/nagios-nrpe-dockerNavigate to the directory above;
cd /opt/nagios-nrpe-dockerDownload latest NRPE release version;
wget https://github.com/NagiosEnterprises/nrpe/releases/download/nrpe-4.1.0/nrpe-4.1.0.tar.gzExtract the archive;
tar xzf nrpe-4.1.0.tar.gzDownload latest Nagios monitoring plugins;
wget https://github.com/nagios-plugins/nagios-plugins/releases/download/release-2.4.2/nagios-plugins-2.4.2.tar.gzExtract the plugins;
tar xzf nagios-plugins-2.4.2.tar.gzCreate NRPE Dockerfile. We will build our NRPE Docker image upon Rocky Linux 9 (see FROM line in the Dockerfile below);
vim Dockerfile
FROM rockylinux:9
RUN dnf install epel-release -y \
&& dnf update -y
# Install Required build tools
RUN dnf install -y gcc \
glibc \
glibc-common \
make \
gettext \
automake \
autoconf \
wget \
procps \
openssl-devel \
pkgconf-pkg-config \
diffutils \
net-snmp-perl \
supervisor
# Build and Install NRPE Agent
COPY nrpe-4.1.0 /nrpe-4.1.0
WORKDIR /nrpe-4.1.0
# Configure NRPE Agent to adapt it to the system
RUN ./configure \
--enable-command-args \
--with-nrpe-user=nagios \
--with-nrpe-group=nagios
# Compile, Install NRPE, install config and,
# create nagios user/group
RUN make all \
&& make install-groups-users \
&& make install \
&& make install-config
# Build and Install Nagios Plugins;
COPY nagios-plugins-2.4.2 /nagios-plugins-2.4.2
WORKDIR /nagios-plugins-2.4.2
RUN ./configure --with-nagios-user=nagios --with-nagios-group=nagios && \
make && \
make install
# Define NRPE Service, Port and Protocol
RUN echo "nrpe 5666/tcp # NRPE Service" >> /etc/services
#
WORKDIR /root
# Add NRPE Startup script
ADD start.sh /
RUN chmod +x /start.sh
CMD [ "/start.sh" ]
From the Dockerfile above, NRPE agent and plugins will be installed atop Rocky Linux 9 docker image.
We also have a startup script, start.sh that will be used to start NRPE agent;
The script is in our current directory;
cat /opt/nagios-nrpe-docker/start.sh#!/bin/sh
/usr/local/nagios/bin/nrpe -n -c /usr/local/nagios/etc/nrpe.cfg -d
/usr/bin/supervisord -nThe script will be copied into the NRPE Docker image we will create.
With the Dockerfile setup, you can now build your NRPE agent Docker image;
docker build -t nrpe:4.1.0 .This will create an NRPE Docker image and tag it with the version number, 4.1.0.
docker imagesREPOSITORY TAG IMAGE ID CREATED SIZE
nrpe 4.1.0 01bbdb86b63f 3 minutes ago 548MB
rockylinux 9 ce99dcf19c24 2 weeks ago 176MBList installed plugins;
docker run --rm -ti nrpe:4.1.0 ls /usr/local/nagios/libexec/check_apt check_ifstatus check_ntp_peer check_ssl_validity
check_breeze check_imap check_ntp_time check_ssmtp
check_clamd check_ircd check_nwstat check_swap
check_cluster check_jabber check_oracle check_tcp
check_dhcp check_load check_overcr check_time
check_disk check_log check_ping check_udp
check_disk_smb check_mailq check_pop check_ups
check_dummy check_mrtg check_procs check_uptime
check_file_age check_mrtgtraf check_real check_users
check_flexlm check_nagios check_rpc check_wave
check_ftp check_nntp check_sensors negate
check_http check_nntps check_simap remove_perfdata
check_icmp check_nrpe check_smtp urlize
check_ide_smart check_nt check_spop utils.pm
check_ifoperstatus check_ntp check_ssh utils.sh
Now, to easily configure NRPE agent for host monitoring, create a configuration directory on the Docker host current directory where to place a custom nrpe.cfg file.
mkdir /opt/nagios-nrpe-docker/etcInside this directory, we will create nrpe.cfg file which you can then mount it into the NRPE Docker container NRPE configuration file.
By default, NRPE configuration file looks like;
#############################################################################
#
# Sample NRPE Config File
#
# Notes:
#
# This is a sample configuration file for the NRPE daemon. It needs to be
# located on the remote host that is running the NRPE daemon, not the host
# from which the check_nrpe client is being executed.
#
#############################################################################
# LOG FACILITY
# The syslog facility that should be used for logging purposes.
log_facility=daemon
# LOG FILE
# If a log file is specified in this option, nrpe will write to
# that file instead of using syslog.
#log_file=/usr/local/nagios/var/nrpe.log
# DEBUGGING OPTION
# This option determines whether or not debugging messages are logged to the
# syslog facility.
# Values: 0=debugging off, 1=debugging on
debug=0
# PID FILE
# The name of the file in which the NRPE daemon should write it's process ID
# number. The file is only written if the NRPE daemon is started by the root
# user and is running in standalone mode.
pid_file=/usr/local/nagios/var/nrpe.pid
# PORT NUMBER
# Port number we should wait for connections on.
# NOTE: This must be a non-privileged port (i.e. > 1024).
# NOTE: This option is ignored if NRPE is running under either inetd or xinetd
server_port=5666
# SERVER ADDRESS
# Address that nrpe should bind to in case there are more than one interface
# and you do not want nrpe to bind on all interfaces.
# NOTE: This option is ignored if NRPE is running under either inetd or xinetd
#server_address=127.0.0.1
# LISTEN QUEUE SIZE
# Listen queue size (backlog) for serving incoming connections.
# You may want to increase this value under high load.
#listen_queue_size=5
# NRPE USER
# This determines the effective user that the NRPE daemon should run as.
# You can either supply a username or a UID.
#
# NOTE: This option is ignored if NRPE is running under either inetd or xinetd
nrpe_user=nagios
# NRPE GROUP
# This determines the effective group that the NRPE daemon should run as.
# You can either supply a group name or a GID.
#
# NOTE: This option is ignored if NRPE is running under either inetd or xinetd
nrpe_group=nagios
# ALLOWED HOST ADDRESSES
# This is an optional comma-delimited list of IP address or hostnames
# that are allowed to talk to the NRPE daemon. Network addresses with a bit mask
# (i.e. 192.168.1.0/24) are also supported. Hostname wildcards are not currently
# supported.
#
# Note: The daemon only does rudimentary checking of the client's IP
# address. I would highly recommend adding entries in your /etc/hosts.allow
# file to allow only the specified host to connect to the port
# you are running this daemon on.
#
# NOTE: This option is ignored if NRPE is running under either inetd or xinetd
allowed_hosts=127.0.0.1,::1
# COMMAND ARGUMENT PROCESSING
# This option determines whether or not the NRPE daemon will allow clients
# to specify arguments to commands that are executed. This option only works
# if the daemon was configured with the --enable-command-args configure script
# option.
#
# *** ENABLING THIS OPTION IS A SECURITY RISK! ***
# Read the SECURITY file for information on some of the security implications
# of enabling this variable.
#
# Values: 0=do not allow arguments, 1=allow command arguments
dont_blame_nrpe=0
# BASH COMMAND SUBSTITUTION
# This option determines whether or not the NRPE daemon will allow clients
# to specify arguments that contain bash command substitutions of the form
# $(...). This option only works if the daemon was configured with both
# the --enable-command-args and --enable-bash-command-substitution configure
# script options.
#
# *** ENABLING THIS OPTION IS A HIGH SECURITY RISK! ***
# Read the SECURITY file for information on some of the security implications
# of enabling this variable.
#
# Values: 0=do not allow bash command substitutions,
# 1=allow bash command substitutions
allow_bash_command_substitution=0
# COMMAND PREFIX
# This option allows you to prefix all commands with a user-defined string.
# A space is automatically added between the specified prefix string and the
# command line from the command definition.
#
# *** THIS EXAMPLE MAY POSE A POTENTIAL SECURITY RISK, SO USE WITH CAUTION! ***
# Usage scenario:
# Execute restricted commmands using sudo. For this to work, you need to add
# the nagios user to your /etc/sudoers. An example entry for allowing
# execution of the plugins from might be:
#
# nagios ALL=(ALL) NOPASSWD: /usr/lib/nagios/plugins/
#
# This lets the nagios user run all commands in that directory (and only them)
# without asking for a password. If you do this, make sure you don't give
# random users write access to that directory or its contents!
# command_prefix=/usr/bin/sudo
# MAX COMMANDS
# This specifies how many children processes may be spawned at any one
# time, essentially limiting the fork()s that occur.
# Default (0) is set to unlimited
# max_commands=0
# COMMAND TIMEOUT
# This specifies the maximum number of seconds that the NRPE daemon will
# allow plugins to finish executing before killing them off.
command_timeout=60
# CONNECTION TIMEOUT
# This specifies the maximum number of seconds that the NRPE daemon will
# wait for a connection to be established before exiting. This is sometimes
# seen where a network problem stops the SSL being established even though
# all network sessions are connected. This causes the nrpe daemons to
# accumulate, eating system resources. Do not set this too low.
connection_timeout=300
# WEAK RANDOM SEED OPTION
# This directive allows you to use SSL even if your system does not have
# a /dev/random or /dev/urandom (on purpose or because the necessary patches
# were not applied). The random number generator will be seeded from a file
# which is either a file pointed to by the environment valiable $RANDFILE
# or $HOME/.rnd. If neither exists, the pseudo random number generator will
# be initialized and a warning will be issued.
# Values: 0=only seed from /dev/[u]random, 1=also seed from weak randomness
#allow_weak_random_seed=1
# SSL/TLS OPTIONS
# These directives allow you to specify how to use SSL/TLS.
# SSL VERSION
# This can be any of: SSLv2 (only use SSLv2), SSLv2+ (use any version),
# SSLv3 (only use SSLv3), SSLv3+ (use SSLv3 or above), TLSv1 (only use
# TLSv1), TLSv1+ (use TLSv1 or above), TLSv1.1 (only use TLSv1.1),
# TLSv1.1+ (use TLSv1.1 or above), TLSv1.2 (only use TLSv1.2),
# TLSv1.2+ (use TLSv1.2 or above)
# If an "or above" version is used, the best will be negotiated. So if both
# ends are able to do TLSv1.2 and use specify SSLv2, you will get TLSv1.2.
# If you are using openssl 1.1.0 or above, the SSLv2 options are not available.
#ssl_version=SSLv2+
# SSL USE ADH
# This is for backward compatibility and is DEPRECATED. Set to 1 to enable
# ADH or 2 to require ADH. 1 is currently the default but will be changed
# in a later version.
#ssl_use_adh=1
# SSL CIPHER LIST
# This lists which ciphers can be used. For backward compatibility, this
# defaults to 'ssl_cipher_list=ALL:!MD5:@STRENGTH' for < OpenSSL 1.1.0,
# and 'ssl_cipher_list=ALL:!MD5:@STRENGTH:@SECLEVEL=0' for OpenSSL 1.1.0 and
# greater.
#ssl_cipher_list=ALL:!MD5:@STRENGTH
#ssl_cipher_list=ALL:!MD5:@STRENGTH:@SECLEVEL=0
#ssl_cipher_list=ALL:!aNULL:!eNULL:!SSLv2:!LOW:!EXP:!RC4:!MD5:@STRENGTH
# SSL Certificate and Private Key Files
#ssl_cacert_file=/etc/ssl/servercerts/ca-cert.pem
#ssl_cert_file=/etc/ssl/servercerts/nagios-cert.pem
#ssl_privatekey_file=/etc/ssl/servercerts/nagios-key.pem
# SSL USE CLIENT CERTS
# This options determines client certificate usage.
# Values: 0 = Don't ask for or require client certificates (default)
# 1 = Ask for client certificates
# 2 = Require client certificates
#ssl_client_certs=0
# SSL LOGGING
# This option determines which SSL messages are send to syslog. OR values
# together to specify multiple options.
# Values: 0x00 (0) = No additional logging (default)
# 0x01 (1) = Log startup SSL/TLS parameters
# 0x02 (2) = Log remote IP address
# 0x04 (4) = Log SSL/TLS version of connections
# 0x08 (8) = Log which cipher is being used for the connection
# 0x10 (16) = Log if client has a certificate
# 0x20 (32) = Log details of client's certificate if it has one
# -1 or 0xff or 0x2f = All of the above
#ssl_logging=0x00
# NASTY METACHARACTERS
# This option allows you to override the list of characters that cannot
# be passed to the NRPE daemon.
# nasty_metachars=|`&><'\\[]{};\r\n
# This option allows you to enable or disable logging error messages to the syslog facilities.
# If this option is not set, the error messages will be logged.
disable_syslog=0
# COMMAND DEFINITIONS
# Command definitions that this daemon will run. Definitions
# are in the following format:
#
# command[]=
#
# When the daemon receives a request to return the results of
# it will execute the command specified by the argument.
#
# Unlike Nagios, the command line cannot contain macros - it must be
# typed exactly as it should be executed.
#
# Note: Any plugins that are used in the command lines must reside
# on the machine that this daemon is running on! The examples below
# assume that you have plugins installed in a /usr/local/nagios/libexec
# directory. Also note that you will have to modify the definitions below
# to match the argument format the plugins expect. Remember, these are
# examples only!
# The following examples use hardcoded command arguments...
# This is by far the most secure method of using NRPE
command[check_users]=/usr/local/nagios/libexec/check_users -w 5 -c 10
command[check_load]=/usr/local/nagios/libexec/check_load -r -w .15,.10,.05 -c .30,.25,.20
command[check_hda1]=/usr/local/nagios/libexec/check_disk -w 20% -c 10% -p /dev/hda1
command[check_zombie_procs]=/usr/local/nagios/libexec/check_procs -w 5 -c 10 -s Z
command[check_total_procs]=/usr/local/nagios/libexec/check_procs -w 150 -c 200
# The following examples allow user-supplied arguments and can
# only be used if the NRPE daemon was compiled with support for
# command arguments *AND* the dont_blame_nrpe directive in this
# config file is set to '1'. This poses a potential security risk, so
# make sure you read the SECURITY file before doing this.
### MISC SYSTEM METRICS ###
#command[check_users]=/usr/local/nagios/libexec/check_users $ARG1$
#command[check_load]=/usr/local/nagios/libexec/check_load $ARG1$
#command[check_disk]=/usr/local/nagios/libexec/check_disk $ARG1$
#command[check_swap]=/usr/local/nagios/libexec/check_swap $ARG1$
#command[check_cpu_stats]=/usr/local/nagios/libexec/check_cpu_stats.sh $ARG1$
#command[check_mem]=/usr/local/nagios/libexec/custom_check_mem -n $ARG1$
### GENERIC SERVICES ###
#command[check_init_service]=sudo /usr/local/nagios/libexec/check_init_service $ARG1$
#command[check_services]=/usr/local/nagios/libexec/check_services -p $ARG1$
### SYSTEM UPDATES ###
#command[check_yum]=/usr/local/nagios/libexec/check_yum
#command[check_apt]=/usr/local/nagios/libexec/check_apt
### PROCESSES ###
#command[check_all_procs]=/usr/local/nagios/libexec/custom_check_procs
#command[check_procs]=/usr/local/nagios/libexec/check_procs $ARG1$
### OPEN FILES ###
#command[check_open_files]=/usr/local/nagios/libexec/check_open_files.pl $ARG1$
### NETWORK CONNECTIONS ###
#command[check_netstat]=/usr/local/nagios/libexec/check_netstat.pl -p $ARG1$ $ARG2$
### ASTERISK ###
#command[check_asterisk]=/usr/local/nagios/libexec/check_asterisk.pl $ARG1$
#command[check_sip]=/usr/local/nagios/libexec/check_sip $ARG1$
#command[check_asterisk_sip_peers]=sudo /usr/local/nagios/libexec/check_asterisk_sip_peers.sh $ARG1$
#command[check_asterisk_version]=/usr/local/nagios/libexec/nagisk.pl -c version
#command[check_asterisk_peers]=/usr/local/nagios/libexec/nagisk.pl -c peers
#command[check_asterisk_channels]=/usr/local/nagios/libexec/nagisk.pl -c channels
#command[check_asterisk_zaptel]=/usr/local/nagios/libexec/nagisk.pl -c zaptel
#command[check_asterisk_span]=/usr/local/nagios/libexec/nagisk.pl -c span -s 1
# INCLUDE CONFIG FILE
# This directive allows you to include definitions from an external config file.
#include=
# INCLUDE CONFIG DIRECTORY
# This directive allows you to include definitions from config files (with a
# .cfg extension) in one or more directories (with recursion).
#include_dir=
#include_dir=
# KEEP ENVIRONMENT VARIABLES
# This directive allows you to retain specific variables from the environment
# when starting the NRPE daemon.
#keep_env_vars=NRPE_MULTILINESUPPORT,NRPE_PROGRAMVERSION
We will update this configuration to make it as simple as possible such that it look like;
cat /opt/nagios-nrpe-docker/etc/nrpe.cfg
log_facility=daemon
debug=0
server_port=5666
nrpe_user=nagios
nrpe_group=nagios
allowed_hosts=127.0.0.1,192.168.59.48
dont_blame_nrpe=1
command_timeout=60
connection_timeout=300
command[check_users]=/usr/local/nagios/libexec/check_users -w 5 -c 10
command[check_load]=/usr/local/nagios/libexec/check_load -r -w .15,.10,.05 -c .30,.25,.20
command[check_disk]=/usr/local/nagios/libexec/check_disk -w 20% -c 10% -p /
command[check_zombie_procs]=/usr/local/nagios/libexec/check_procs -w 5 -c 10 -s Z
command[check_total_procs]=/usr/local/nagios/libexec/check_procs -w 150 -c 200
Adjust your thresholds as you so wish!
Start and Test NRPE Docker Agent
You can now start and test if the NRPE Docker agent works as expected.
Note that NRPE listens on port 5666 by default and so you need to expose this port on the host;
docker run --name nagios-nrpe-4.1.0 \
-dp 5666:5666 \
-v "/opt/nagios-nrpe-docker/etc/nrpe.cfg:/usr/local/nagios/etc/nrpe.cfg" \
nrpe:4.1.0You can add the --restart unless-stopped option to start the NRPE agent container on system reboot.
Check the status of the NRPE agent Docker container;
docker ps -aSample output;
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
152eae72b9a2 nrpe:4.1.0 "/start.sh" 2 seconds ago Up 2 seconds 0.0.0.0:5666->5666/tcp, :::5666->5666/tcp nagios-nrpe-4.1.0Confirm that the port is exposed on your host;
ss -altnp | grep :5666LISTEN 0 4096 0.0.0.0:5666 0.0.0.0:* users:(("docker-proxy",pid=40626,fd=4))
LISTEN 0 4096 [::]:5666 [::]:* users:(("docker-proxy",pid=40632,fd=4))You should now be able to connect to your NRPE agent Docker container from the hosts defined by the line allowed_hosts in the configuration file.
For example, let’s test NRPE agent response from the Nagios server Docker container;
docker run --rm -ti nagios-core:4.4.9 /usr/local/nagios/libexec/check_nrpe -n -H 192.168.59.49Sample output;
NRPE v4.1.0Run a simple check e.g check load from your Nagios server;
docker run --rm -ti nagios-core:4.4.9 /usr/local/nagios/libexec/check_nrpe -n -H 192.168.59.49 -c check_loadSample output;
OK - load average per CPU: 0.06, 0.03, 0.03|load1=0.055;0.150;0.300;0; load5=0.025;0.100;0.250;0; load15=0.030;0.050;0.200;0;To do the monitoring from the Nagios, add the host and service checks to your Nagios.
In our Nagios server, these are sample checks against our NRPE agent server;
cat /opt/nagios-core-docker/etc/objects/kifarunix/services.cfg
#################################
# COMMAND DEFINITIONS
#################################
define command {
command_name check_nrpe
command_line /usr/local/nagios/libexec/check_nrpe -n -H $HOSTADDRESS$ -c $ARG1$
}
#################################
# SERVICE DEFINITIONS
#################################
define service {
use remote-service
host_name elk-stack
service_description Root Partition
check_command check_nrpe!check_disk
}
define service {
use remote-service
host_name elk-stack
service_description Current Users
check_command check_nrpe!check_users
}
define service {
use remote-service
host_name elk-stack
service_description Total Processes
check_command check_nrpe!check_total_procs
}
define service {
use remote-service
host_name elk-stack
service_description Current Load
check_command check_nrpe!check_load
}
These services will be checked on our server on which NRPE agent Docker container is running.
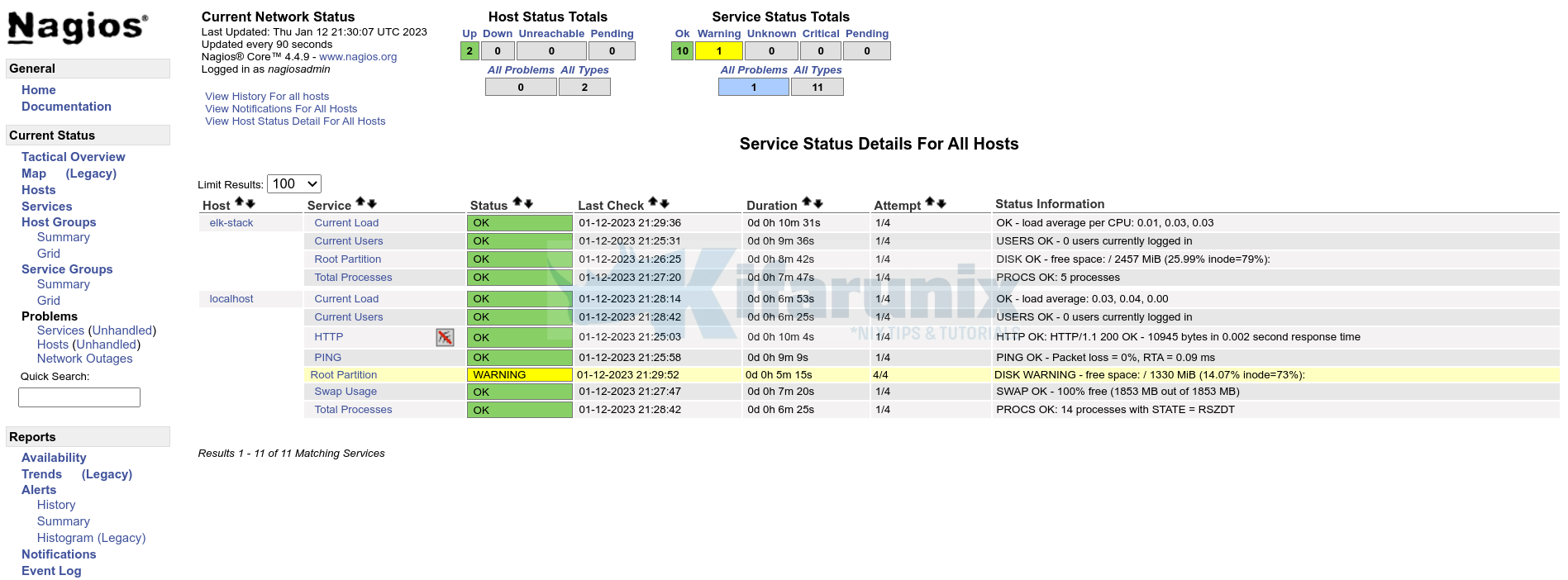
Sample checks status on Nagios server;
And that is it on how you can deploy NRPE agent as a Docker container.


Cool tutorial.
Do the ‘check_users’ and check_processes’ commands check information on the host or within the container? I’d assume the former; e.g. number of users logged into the container.