In this tutorial, you will learn how to install and configure Tripwire security monitoring tool on CentOS 8. Tripwire is available is as an open source and commercial version. In this setup, we will learning how to install and setup the open source version of Tripwire.
So, What is Tripwire? It is one of the leading Host-based Intrusion Detection tools. According to the their Github page, “Open Source Tripwire is a security and data integrity tool for monitoring and alerting on file & directory changes“
It works by “comparing the current filesystem state against a known baseline state, and alerts on any changes it detects. The baseline and check behavior are controlled by a policy file, which specifies which files or directories to monitor, and which attributes to monitor on them, such as hashes, file permissions, and ownership. When an expected change occurs, such as upgrading a package, the baseline database can be updated to the new known-good state. The policy can also be updated, for example to reduce noise or cover a newly installed package.“
Installing Tripwire Security Monitoring tool on CentOS 8
Tripwire should literally be installed on a clean OS in order to get the most out of it. If you are installing on already used system, then it will create a baseline right from when it is run for the first time.
Follow through this guide to learn how to install and configure Tripwire on CentOS 8.
Run system Update
Ensure that your system packages are up-to-date;
dnf updateInstall EPEL Repos on CentOS 8
Tripwire is not available on the default CentOS 8 repos. It is however provided by the EPEL repos which can be installed on CentOS 8 by executing the command below;
dnf install epel-releaseCheck whether Tripwire is actually provided by the EPEL repos;
yum provides tripwiretripwire-2.4.3.7-5.el8.x86_64 : IDS (Intrusion Detection System)
Repo : epel
Matched from:
Provide : tripwire = 2.4.3.7-5.el8So you all set to roll the installation.
Install Tripwire on CentOS 8
dnf install tripwireConfigure Tripwire Security Monitoring tool on CentOS 8
When Tripwire is initially set up, it creates a database that records certain file information. Then when it is run, it compares a designated set of files and directories to the information stored in the database. Any file that is added or deleted are flagged and reported. The same happens to any files that have changed from their previously recorded state in the database.
When Tripwire is run against system files on a regular basis, any file changes will be spotted when Tripwire is run. Tripwire will report the changes, which will give system administrators a clue that they need to enact damage control measures immediately if certain files have been altered.
Generate Tripwire Encryption Keys
To begin with, you need to generate Tripwire site and local encryption keys. While site keys are use to sign the configurations and policy, local keys are used to sign the database and reports. The local key is a like a private key and unique to each system while site key is a like a public key and can be shared across systems.
The keys can be generated using Tripwire administrative and utility tool called twadmin. This tool allows encoding, decoding, signing, and verification of Tripwire files, and provides a means to generate and change local and site keys.
While generating local key, it is recommended that you include the name of the system hostname on the name of the key.
On CentOS 8 and similar derivatives, you can create the hostname using using the hostnamectl command as shown below.
hostnamectl set-hostname centos8.kifarunix-demo.comNext, proceed to generate the keys.
Generate Tripwire local keys;
twadmin -m G -L /etc/tripwire/`hostname`-local.key(When selecting a passphrase, keep in mind that good passphrases typically
have upper and lower case letters, digits and punctuation marks, and are
at least 8 characters in length.)
Enter the local keyfile passphrase: ENTER_YOUR_PASSPHRASE
Verify the local keyfile passphrase: RE-ENTER_YOUR_PASSPHRASE
Generating key (this may take several minutes)...Key generation complete.Generate the Tripwire site keys;
twadmin -m G -S /etc/tripwire/site.keyThis generates and store the keys under the /etc/tripwire directory.
ls /etc/tripwire/centos8.kifarunix-demo.com-local.key site.key twcfg.txt twpol.txtCreate Tripwire Configuration file
The Tripwire configuration file stores system-specific information, including the location of Tripwire data files, and the settings used to send email notification. These settings are auto-generated during the installation but are subject to modification by the system admin. /etc/tripwire/twcfg.txt is a sample plain text version of the a signed Tripwire configuration file /etc/tripwire/tw.cfg.
You can edit the /etc/tripwire/twcfg.txt to update the defined parameters before generating the signed version of it.
To generate a signed version of the Tripwire configuration, you need the site key to sign it and to the edit the file later, you will need to provide the site key passphrase.
Run the command below to generate the Tripwire configuration.
twadmin -m F -S /etc/tripwire/site.key /etc/tripwire/twcfg.txtYou are prompted to enter the site key passphrase.
This command generates a encrypted binary version of the twcfg.txt, /etc/tripwire/tw.cfg.
To read more about Tripwire configuration, refer to man twconfig.
Create Tripwire Policy file
The Tripwire policy file describes system objects to be monitored what properties for each object should be collected and stored in the database file. Each object in the policy file is associated with a property mask, which describes what changes to the file or directory Trip‐ wire should monitor, and which ones can safely be ignored.
A plain text version of Tripwire policy,/etc/tripwire/twpol.txt, is generated during installation.
Within the Tripwire policy configuration file, are a number of policy rules that are appliced against various parts of the system.
See the sample section of the twpol.txt, comment lines removed.
less /etc/tripwire/twpol.txt@@section GLOBAL
TWROOT=/usr/sbin;
TWBIN=/usr/sbin;
TWPOL="/etc/tripwire";
TWDB="/var/lib/tripwire";
TWSKEY="/etc/tripwire";
TWLKEY="/etc/tripwire";
TWREPORT="/var/lib/tripwire/report";
HOSTNAME=centos8.example.com;
@@section FS
SEC_CRIT = $(IgnoreNone)-SHa ; # Critical files that cannot change
SEC_SUID = $(IgnoreNone)-SHa ; # Binaries with the SUID or SGID flags set
SEC_BIN = $(ReadOnly) ; # Binaries that should not change
SEC_CONFIG = $(Dynamic) ; # Config files that are changed infrequently but accessed often
SEC_LOG = $(Growing) ; # Files that grow, but that should never change ownership
SEC_INVARIANT = +tpug ; # Directories that should never change permission or ownership
SIG_LOW = 33 ; # Non-critical files that are of minimal security impact
SIG_MED = 66 ; # Non-critical files that are of significant security impact
SIG_HI = 100 ; # Critical files that are significant points of vulnerability
...
...
(
rulename = "Invariant Directories",
severity = $(SIG_MED)
)
{
/ -> $(SEC_INVARIANT) (recurse = 0) ;
/home -> $(SEC_INVARIANT) (recurse = 0) ;
/etc -> $(SEC_INVARIANT) (recurse = 0) ;
}
(
rulename = "File System and Disk Administraton Programs",
severity = $(SIG_HI)
)
{
/sbin/accton -> $(SEC_CRIT) ;
/sbin/badblocks -> $(SEC_CRIT) ;
/sbin/busybox -> $(SEC_CRIT) ;
...
...The policy setup begins with setting up variables for various system binaries and directories, then the variables that defines the controls that will be applied to the specific systems files, directories and binaries, etc.
For example, the rule name, rulename = "Invariant Directories", is assigned a medium severity. Under this rule, we have /home and /etc and the controls applied to these directories are defined by the variable, SEC_INVARIANT.
You can further modify the policy file as you wish including removing the directories that don’t exist on the system as well adding that are not added yet and then sign it.
For example, for the purposes of demoing how this works, let us assume we have a critical file called classified under /etc/ directory that should not be changed and would like to report on any modification, just enter this directory under the Tripwire Data Files rule section.
vim /etc/tripwire/twpol.txt...
# Tripwire Data Files - Configuration Files, Policy Files, Keys, Reports, Databases
(
rulename = "Tripwire Data Files",
severity = $(SIG_HI)
)
{
...
...
$(TWSKEY)/site.key -> $(SEC_BIN) ;
/etc/classified -> $(SEC_CRIT) ; # Custom demo file
#don't scan the individual reports
$(TWREPORT) -> $(SEC_CONFIG) (recurse=0) ;
}
...Also note that I have update the file and removed all the files/directories that dont exist in my system as well as removing a number of those that exist to make it easy to demo.
Sign policy once you are done updating it.
twadmin -m P -S /etc/tripwire/site.key /etc/tripwire/twpol.txtEnter the passphrase to sign the policy. You should now have the signed policy file, /etc/tripwire/tw.pol.
Create a System Security Baseline
Once you have updated your policies, you need to set the starting point for Tripwire by creating the database of the current security posture of system files and directories. To initialize Tripwire database;
tripwire -m i...
### Continuing...
Wrote database file: /var/lib/tripwire/centos8.kifarunix-demo.com.twd
The database was successfully generated.The baseline is now set.
You can always update your policy file and re-initialize the database.
To print the database, use the command, twprint -m d -d <path/to/*.twd>.
twprint -m d -d /var/lib/tripwire/centos8.kifarunix-demo.com.twdRun System Integrity Check
After building the Tripwire database, the next step is typically to run tripwire in Integrity Checking mode. This mode scans the system for violations, as specified in the policy file.
So before we can run an integrity check, let us edit the file we made above.
echo "test" > /etc/classifiedNext, run the integrity check.
tripwire -m cAn integrity checking report is printed to stdout and is saved in the location specified by the REPORTFILE setting in the Tripwire configuration file. In my setup, the report is saved as, /var/lib/tripwire/report/centos8.kifarunix-demo.com-20200811-233448.twr.
Open Source Tripwire(R) 2.4.3.7 Integrity Check Report
Report generated by: root
Report created on: Tue 11 Aug 2020 11:34:48 PM EAT
Database last updated on: Never
===============================================================================
Report Summary:
===============================================================================
Host name: centos8.kifarunix-demo.com
Host IP address: 10.0.2.15
Host ID: None
Policy file used: /etc/tripwire/tw.pol
Configuration file used: /etc/tripwire/tw.cfg
Database file used: /var/lib/tripwire/centos8.kifarunix-demo.com.twd
Command line used: tripwire -m c
===============================================================================
Rule Summary:
===============================================================================
-------------------------------------------------------------------------------
Section: Unix File System
-------------------------------------------------------------------------------
Rule Name Severity Level Added Removed Modified
--------- -------------- ----- ------- --------
Tripwire Binaries 100 0 0 0
Libraries 66 0 0 0
* Tripwire Data Files 100 0 0 1
System boot changes 100 0 0 0
OS executables and libraries 100 0 0 0
Security Control 100 0 0 0
Login Scripts 100 0 0 0
Critical configuration files 100 0 0 0
Critical system boot files 100 0 0 0
(/boot)
Invariant Directories 66 0 0 0
Total objects scanned: 37883
Total violations found: 1
===============================================================================
Object Summary:
===============================================================================
-------------------------------------------------------------------------------
# Section: Unix File System
-------------------------------------------------------------------------------
-------------------------------------------------------------------------------
Rule Name: Tripwire Data Files (/etc/classified)
Severity Level: 100
-------------------------------------------------------------------------------
Modified:
"/etc/classified"
===============================================================================
Error Report:
===============================================================================
No Errors
-------------------------------------------------------------------------------
*** End of report ***You can see the modified files from the report.
If you want to print the report later, use the twprint -m r -t {0|1|2|3|4} -r <path/to/*.twr> command.
Where {0|1|2|3|4} specifies the level of the report. For example, to print a detailed report to stdout;
twprint -m r -t 4 -r /var/lib/tripwire/report/centos8.kifarunix-demo.com-20200811-233448.twrBelow is a snippet of what attributes were changed on our file, /etc/classified.
...
Total objects scanned: 37883
Total violations found: 1
===============================================================================
Object Summary:
===============================================================================
-------------------------------------------------------------------------------
# Section: Unix File System
-------------------------------------------------------------------------------
-------------------------------------------------------------------------------
Rule Name: Tripwire Data Files (/etc/classified)
Severity Level: 100
-------------------------------------------------------------------------------
----------------------------------------
Modified Objects: 1
----------------------------------------
Modified object name: /etc/classified
Property: Expected Observed
------------- ----------- -----------
Object Type Regular File Regular File
Device Number 64768 64768
File Device Number 0 0
Inode Number 4320652 4320652
Mode -rw-r--r-- -rw-r--r--
Num Links 1 1
UID root (0) root (0)
GID root (0) root (0)
* Size 6 5
* Modify Time Tue 11 Aug 2020 11:19:35 PM EAT
Tue 11 Aug 2020 11:34:10 PM EAT
* Change Time Tue 11 Aug 2020 11:19:35 PM EAT
Tue 11 Aug 2020 11:34:10 PM EAT
Blocks 8 8
* CRC32 CzvquR A3v0iv
* MD5 CxlGrJJJLSNHxiNbTSYRGE DY6Pyi3A+Jb9fLTLADG6JJ
...Updating Tripwire Database
Once you have confirmed and validated the changes made on your system, you can then update the database using the report. This allows any differences between the database and the current system to be reconciled. This will prevent the violation from showing up in future reports. If the reported change is unexpected and potentially malicious, then the changed file should be replaced with the original version. If there is a valid reason for the change, the database must be changed to match the current files.
To update the database with the current report;
tripwire -m u -r /var/lib/tripwire/report/centos8.kifarunix-demo.com-20200811-233448.twrThe command will open the report in a text format using your defined EDITOR. For every change that is detected, there is a check box next to it, [X]. You can remove the “x” from the adjacent box to prevent updating the database with the new values for this object or simply leave it to make the updates.
...
Total objects scanned: 37883
Total violations found: 1
===============================================================================
Object Summary:
===============================================================================
-------------------------------------------------------------------------------
# Section: Unix File System
-------------------------------------------------------------------------------
-------------------------------------------------------------------------------
Rule Name: Tripwire Data Files (/etc/classified)
Severity Level: 100
-------------------------------------------------------------------------------
Remove the "x" from the adjacent box to prevent updating the database
with the new values for this object.
Modified:
[x] "/etc/classified"
===============================================================================
Object Detail:
===============================================================================
-------------------------------------------------------------------------------
Section: Unix File System
-------------------------------------------------------------------------------
...Once you have made the changes, save and exit the report.
You are then prompted to enter your local passphrase key to update the database.
Configure Tripwire to Send Report via Email
You can setup a cron job to run Tripwire checks at specific periods of time and deliver the reports to your mail inbox.
The email program and report level configuration settings are defined on the /etc/tripwire/twcfg.txt. Tripwire can use sendmail MTA to deliver your emails.
Deliver Mails via Postfix and Gmail SMTP Relay server
To be able to sent email, install and configure Postfix with SMTP server for mail relay. In our setup, we use Gmail SMTP server to relay our mails via Postfix.
yum install postfix cyrus-sasl-plain mailxNext, configure Postfix to use Gmail for mail relay on CentOS 8.
Insert the following lines to the end of Postfix main configuration file, /etc/postfix/main.cfg. Replace the value of the myhostname parameter.
myhostname = centos8.kifarunix-demo.com
relayhost = [smtp.gmail.com]:587
smtp_use_tls = yes
smtp_sasl_auth_enable = yes
smtp_sasl_password_maps = hash:/etc/postfix/sasl_passwd
smtp_sasl_security_options = noanonymous
smtp_sasl_tls_security_options = noanonymousYou can update the Postfix config by executing the command below, of course after replacing your hostname value.
cat << 'EOL' >> /etc/postfix/main.cf
myhostname = centos8.kifarunix-demo.com
relayhost = [smtp.gmail.com]:587
smtp_use_tls = yes
smtp_sasl_auth_enable = yes
smtp_sasl_password_maps = hash:/etc/postfix/sasl_passwd
smtp_sasl_security_options = noanonymous
smtp_sasl_tls_security_options = noanonymous
EOLUpdate Gmail relay account credentials on /etc/postfix/sasl_passwd. Replace the gmail account and its password accordingly.
echo "[smtp.gmail.com]:587 [email protected]:PASSWORD" > /etc/postfix/sasl_passwdHash the password file and set the proper ownership and permissions.
postmap /etc/postfix/sasl_passwdchown root:postfix /etc/postfix/sasl_passwd*
chmod 640 /etc/postfix/sasl_passwd*Start and enable postfix to run on system boot;
systemctl enable --now postfixTesting the email configuration using Tripwire;
tripwire --test --email [email protected]On maillog lines, you should see delivery status with status=sent (250 2.0.0 OK...
Also, check inbox, you should receive email with subject, Test email message from Tripwire. Otherwise, check your Postfix configs.
Now, you need to explicitly specify which report you want to receive email for. So edit the policy configuration file, /etc/tripwire/twpol.txt.
vim /etc/tripwire/twpol.txtOnce you identify the report that you need to receive email for, add the emailto= line to the rule directive section. Give your email address as the value to this parameter. See example below, in our demo above, we added a custom file to “Tripwire Data Files“ rule so we can be notified on any changes made to the /etc/classified file.
(
rulename = "Tripwire Data Files",
severity = $(SIG_HI),
emailto = [email protected]
)
{
$(TWDB) -> $(SEC_CONFIG) -i ;
$(TWPOL)/tw.pol -> $(SEC_BIN) -i ;
$(TWPOL)/tw.cfg -> $(SEC_BIN) -i ;
$(TWLKEY)/$(HOSTNAME)-local.key -> $(SEC_BIN) ;
$(TWSKEY)/site.key -> $(SEC_BIN) ;
/etc/classified -> $(SEC_CRIT) ; # Custom demo file
$(TWREPORT) -> $(SEC_CONFIG) (recurse=0) ;
}
...Resign the policy once you are done updating it.
twadmin -m P -S /etc/tripwire/site.key /etc/tripwire/twpol.txtFor any changes made to the file under the rule, Tripwire Data Files, you will be notified of the changes via email.
Let’s modify our file and run the checks;
echo "test" >> /etc/classifiedRun the checks and email the report;
tripwire -m c -MBelow is a snippet of the sample email report.
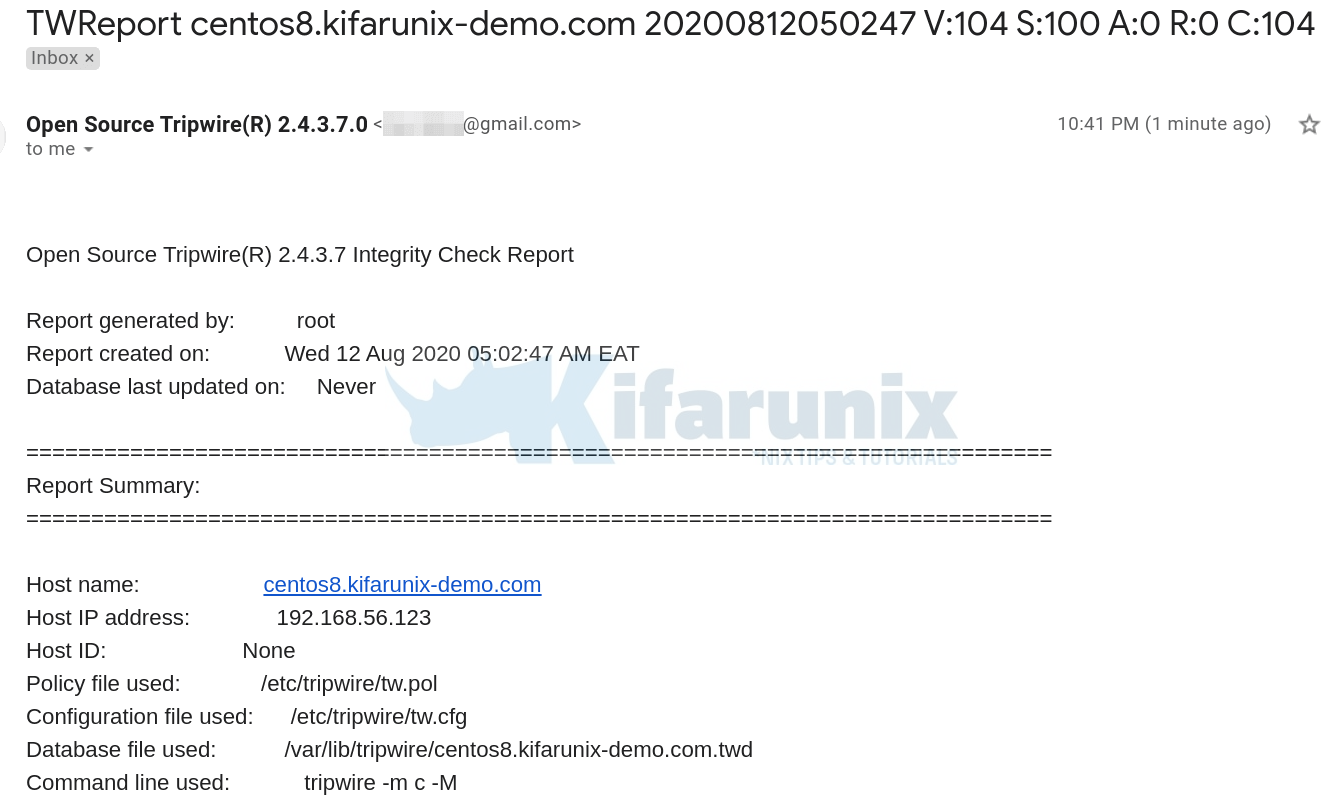
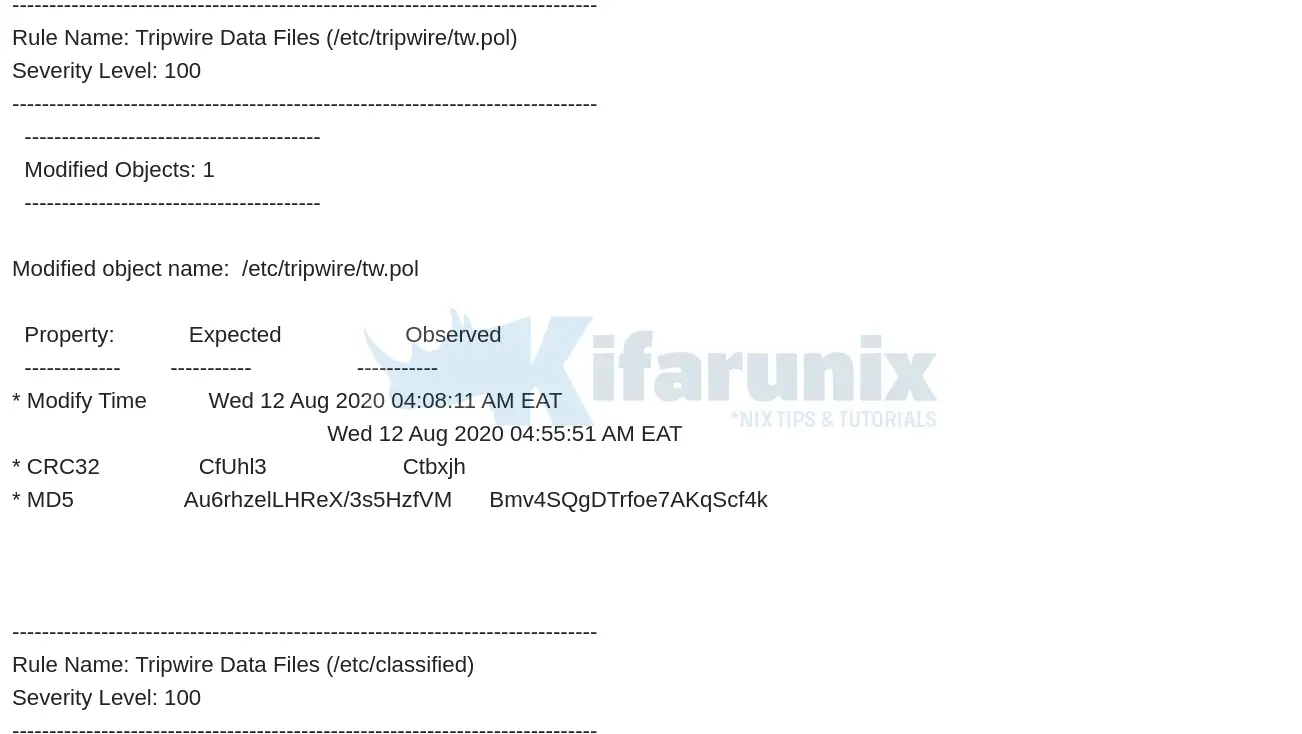
Install a cronjob to automate this task;
sudo crontab -e0 18 * * * /usr/sbin/tripwire -m c -MThe above cronjob will run everyday at 6 pm and sent the report to your inbox.
Reference
man tripwireman twadminman twaconfig- OpenSource Tripwire
Other Related Tutorials
Install and Setup Lynis Security Auditing tool on CentOS 8
Install and Setup Suricata on CentOS 8
Restrict Access to WordPress Login Page to Specific IPs with libModSecurity

