Follow through this guide to learn how to integrate Portainer with OpenLDAP for authentication. By default, Portainer ships with its own internal authentication mechanism. But if you are using OpenLDAP in your environment, you can easily integrate Portainer with it to make the management of user accounts and access to various container environments easy.
When using LDAP authentication, Portainer will delegate user authentication to a LDAP server and fallback to internal authentication if LDAP authentication fails.
With Portainer community edition, some features are not available.
Integrate Portainer with OpenLDAP for Authentication
To begin with, ensure you have a Portainer and OpenLDAP already installed and setup.
You can use some of our tutorials below;
Install Portainer on Linux
Install and Setup Portainer in Linux
Install OpenLDAP Server on Linux
Install and Configure OpenLDAP for Authentication
Create OpenLDAP Portainer Access Groups
To make the account and access management easy, you can create specific groups on OpenLDAP.
Each user that needs to access and manage various container environments via the Portainer web interface can belong to a specific OpenLDAP group.
As per the guide below, we have created two groups, devops and admins on OpenLDAP;
How to Create OpenLDAP Member Groups
Confirming the groups and members;
Devops Group
ldapsearch -H ldapi:/// -Y EXTERNAL -LLL -QQQ \
-b "dc=ldapmaster,dc=kifarunix-demo,dc=com" cn=devopsSample output;
dn: cn=devops,ou=groups,dc=ldapmaster,dc=kifarunix-demo,dc=com
objectClass: groupOfNames
cn: devops
member: uid=janedoe,ou=people,dc=ldapmaster,dc=kifarunix-demo,dc=com
member: uid=johndoe,ou=people,dc=ldapmaster,dc=kifarunix-demo,dc=com
The individual users have the memberOf attributes defined;
memberOf: cn=devops,ou=groups,dc=ldapmaster,dc=kifarunix-demo,dc=comAdmins Group;
ldapsearch -H ldapi:/// -Y EXTERNAL -LLL -QQQ \
-b "dc=ldapmaster,dc=kifarunix-demo,dc=com" cn=adminsSample output;
dn: cn=admins,ou=groups,dc=ldapmaster,dc=kifarunix-demo,dc=com
objectClass: groupOfNames
cn: admins
member: uid=koromicha,ou=people,dc=ldapmaster,dc=kifarunix-demo,dc=com
member: uid=linus,ou=people,dc=ldapmaster,dc=kifarunix-demo,dc=com
The individual users have the memberOf attributes defined;
memberOf: cn=admins,ou=groups,dc=ldapmaster,dc=kifarunix-demo,dc=comldapsearch -Y EXTERNAL -H ldapi:/// -b "dc=ldapmaster,dc=kifarunix-demo,dc=com" uid=* memberOf -QQQ -LLLdn: uid=johndoe,ou=people,dc=ldapmaster,dc=kifarunix-demo,dc=com
memberOf: cn=devops,ou=groups,dc=ldapmaster,dc=kifarunix-demo,dc=com
dn: uid=janedoe,ou=people,dc=ldapmaster,dc=kifarunix-demo,dc=com
memberOf: cn=devops,ou=groups,dc=ldapmaster,dc=kifarunix-demo,dc=com
dn: uid=koromicha,ou=people,dc=ldapmaster,dc=kifarunix-demo,dc=com
memberOf: cn=admins,ou=groups,dc=ldapmaster,dc=kifarunix-demo,dc=com
dn: uid=linus,ou=people,dc=ldapmaster,dc=kifarunix-demo,dc=com
memberOf: cn=admins,ou=groups,dc=ldapmaster,dc=kifarunix-demo,dc=com
Create OpenLDAP Teams Groups on Portainer
To make access to various Portainer environments easy, you need to create the exact teams names as the OpenLDAP groups on Portainer.
In our OpenLDAP, we have two groups, admins and devops.
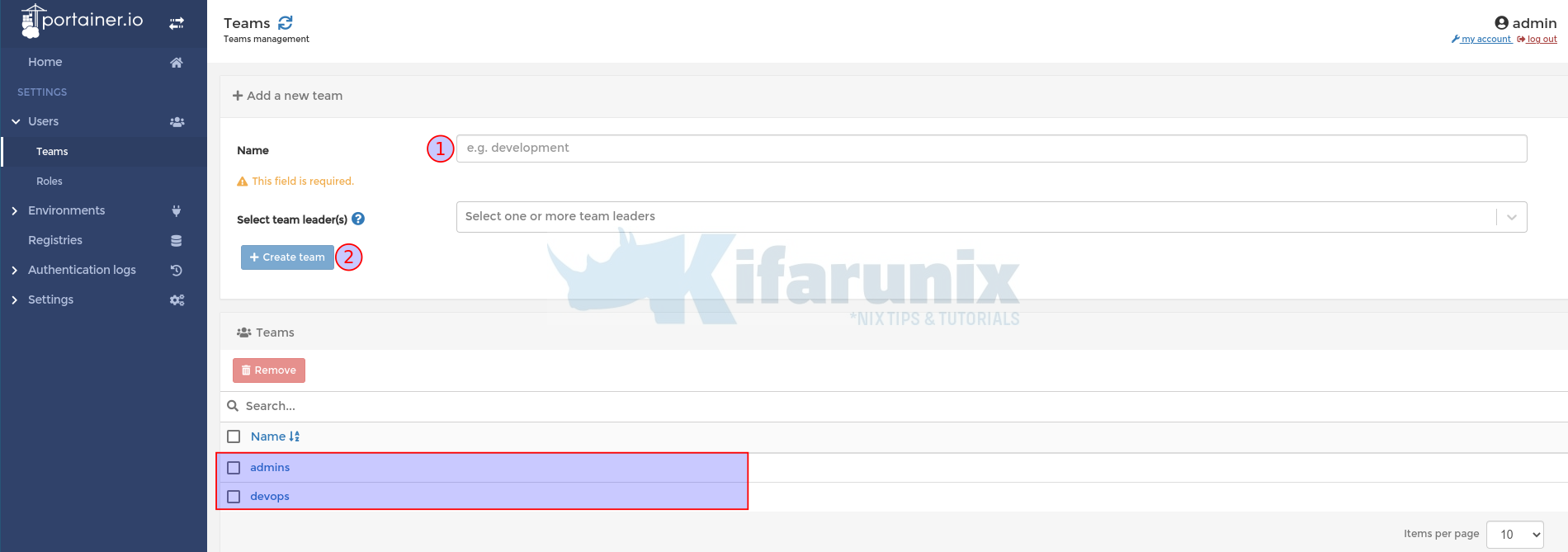
Thus, login to Portainer and navigate to Users > Teams and create teams whose names matches the OpenLDAP group names.
Connect Portainer to OpenLDAP Server
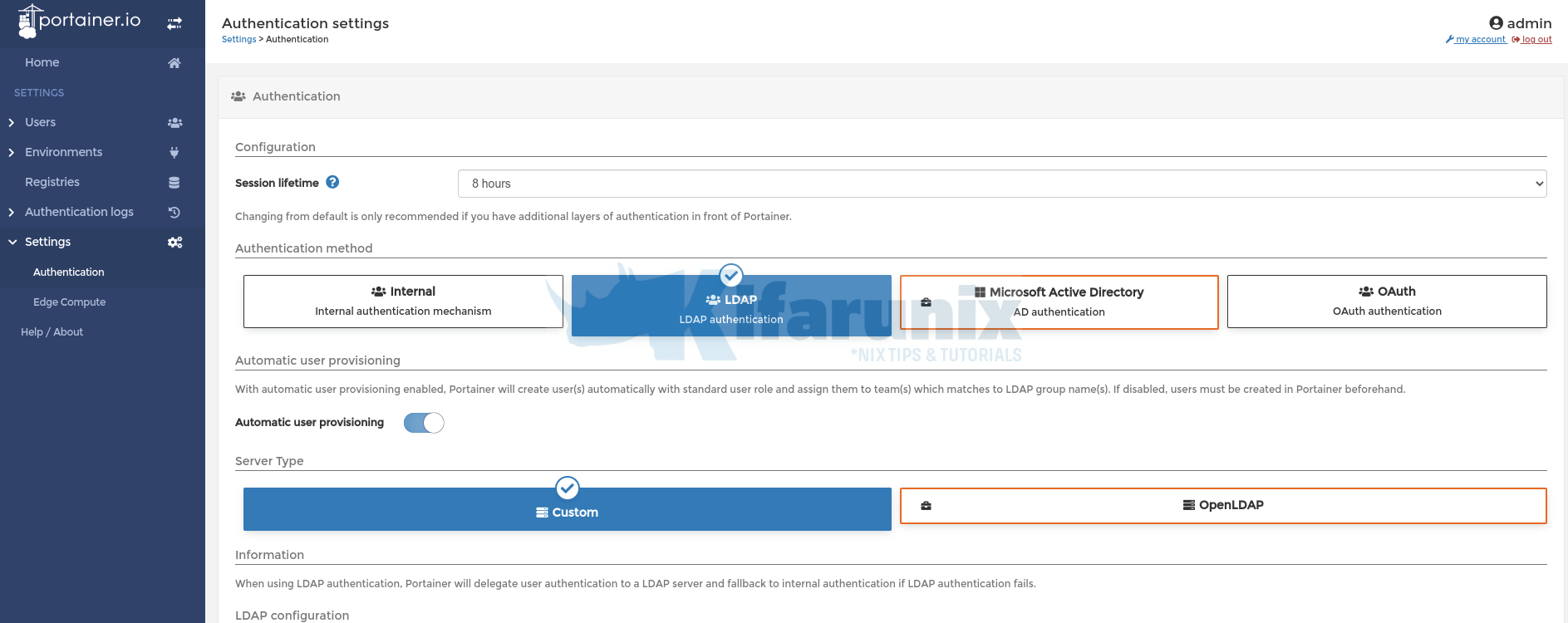
Head over to Portainer web interface and navigate to Settings > Authentications > Click LDAP (LDAP Authentication).
Server type, Custom, is selected by default on the community edition version.
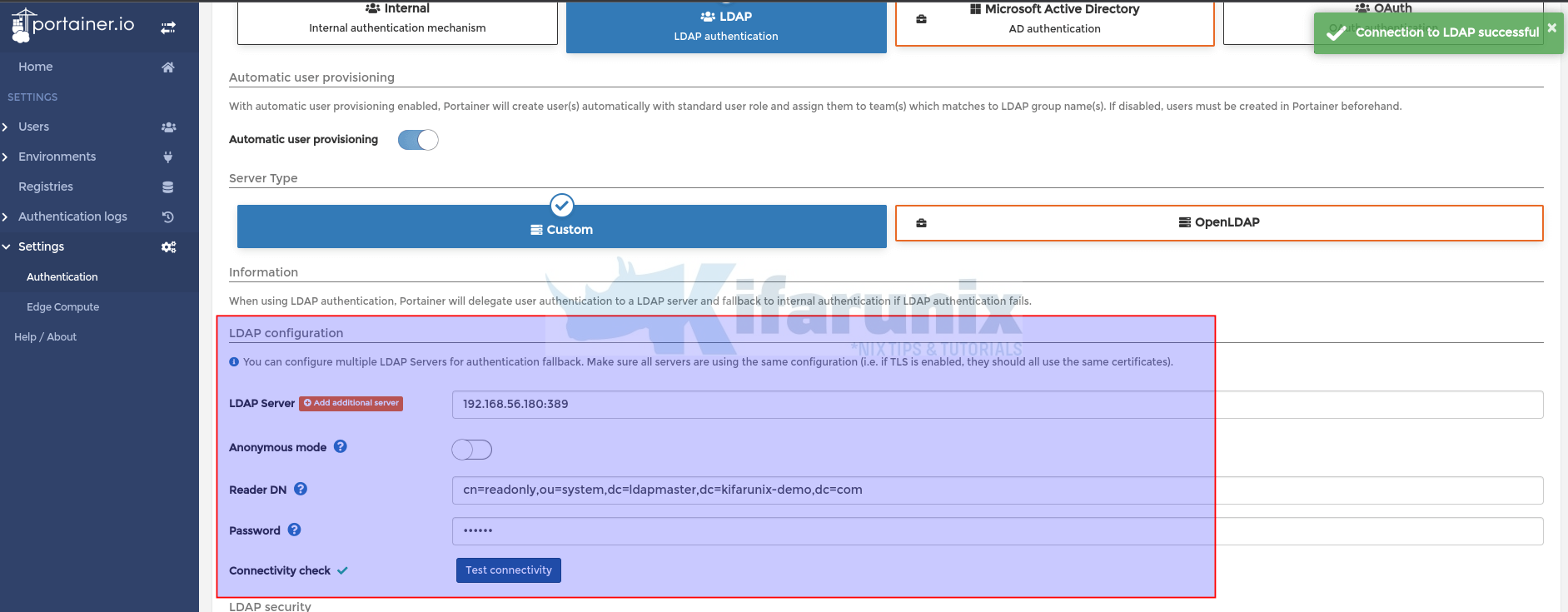
Next, configure OpenLDAP server connection details;
- LDAP server address. Can be IP address or container resolvable domain name.
- Disable anonymous option if your LDAP requires authentication to get records.
- Reader DN/Bind DN and Password. This is the DN used to authenticate to OpenLDAP server to enable you query the directory server for user records.
- Click Test Connectivity to confirm that you can connect to OpenLDAP server with provided credentials;
Configure OpenLDAP SSL/TLS connection
- If your OpenLDAP server is configured with SSL/TLS, you can enable TLS/SSL connnection.
- Thus;
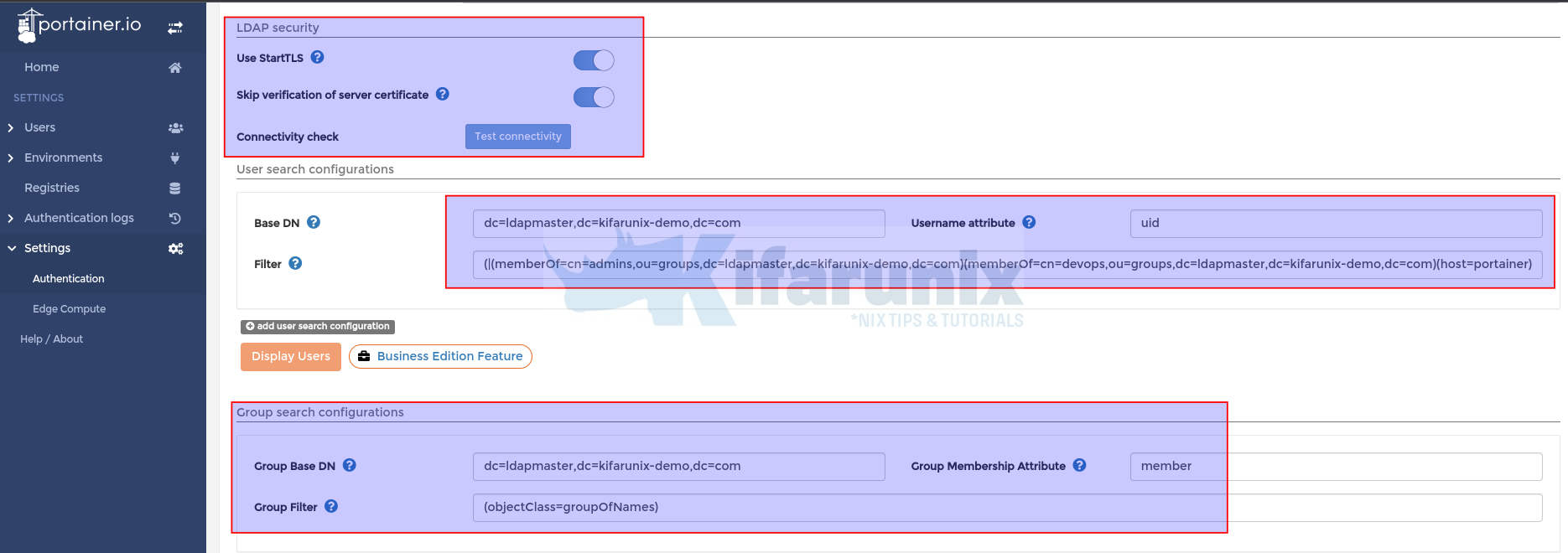
- Enable the use of StartTLS (as you can see we use port 389, if using LDAPS/TLS, change port on the server address above to 636)
- We chose to Skip certificate verification in this setup.
- Test connectivity
- Define User search configurations.
- Base DN (where to start when searching for users) e.g:
dc=ldapmaster,dc=kifarunix-demo,dc=com - Username attribute: We use
uidin our LDAP setup. - User entry filter: We only allow users whose LDAP entry have host=portainer entry OR they belong to devops OR admins groups.
(|(memberOf=cn=admins,ou=groups,dc=ldapmaster,dc=kifarunix-demo,dc=com)(memberOf=cn=devops,ou=groups,dc=ldapmaster,dc=kifarunix-demo,dc=com)(host=portainer))
- We have a user called Alex (uid is alex) with host attribute entry defined as portainer. The rest of users belong to either groups as shown above.
- Confirming on LDAP server;
- Base DN (where to start when searching for users) e.g:
ldapsearch -Y EXTERNAL -H ldapi:/// -b "dc=ldapmaster,dc=kifarunix-demo,dc=com" uid=alex host -QQQ -LLLdn: uid=alex,ou=people,dc=ldapmaster,dc=kifarunix-demo,dc=com
host: portainer- Define Group Search Configuration
- Group Base DN: dc=ldapmaster,dc=kifarunix-demo,dc=com
- Group Membership Attribute: member
- Filter (we filter for only member of the devops or admins group created above): (objectClass=groupOfNames)
- Save the changes by hitting Save settings at the bottom;
Test Login to Portainer using OpenLDAP Account
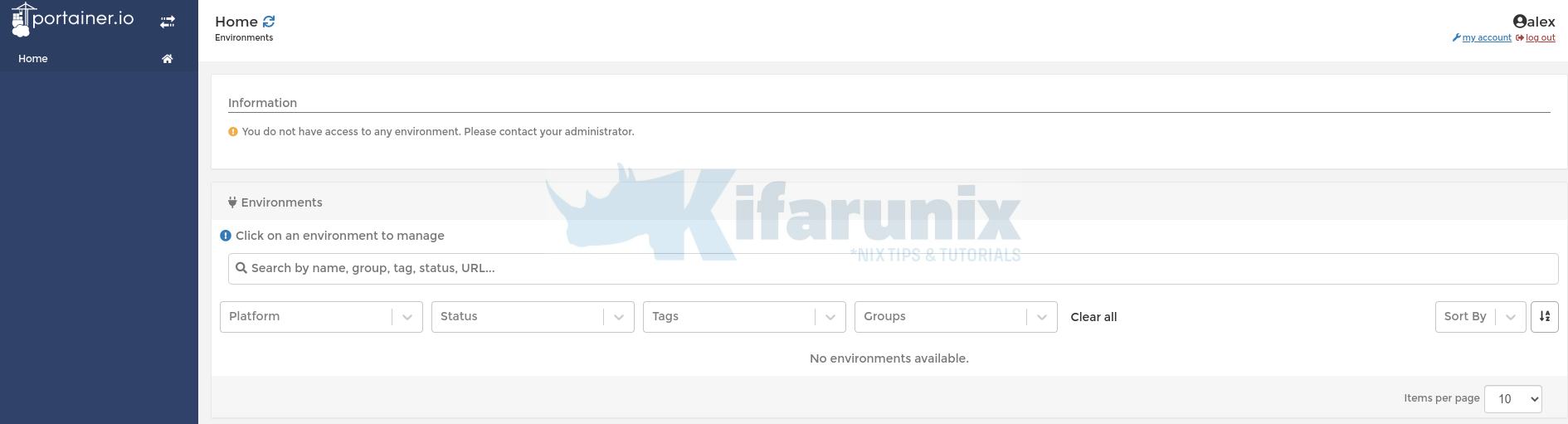
Now, logout and test login using OpenLDAP accounts. We will login as LDAP user alex, with host=portainer attribute entry.
And there you go! No permissions given yet!
Log out and re-login as admin to continue with access management setup.
Grant Portainer Environment/Endpoints Access to LDAP Users
You can now grant access to various Portainer environments to various OpenLDAP user groups/users depending on your setup.
For example, let’s make Alex and Administrator for Portainer at large;
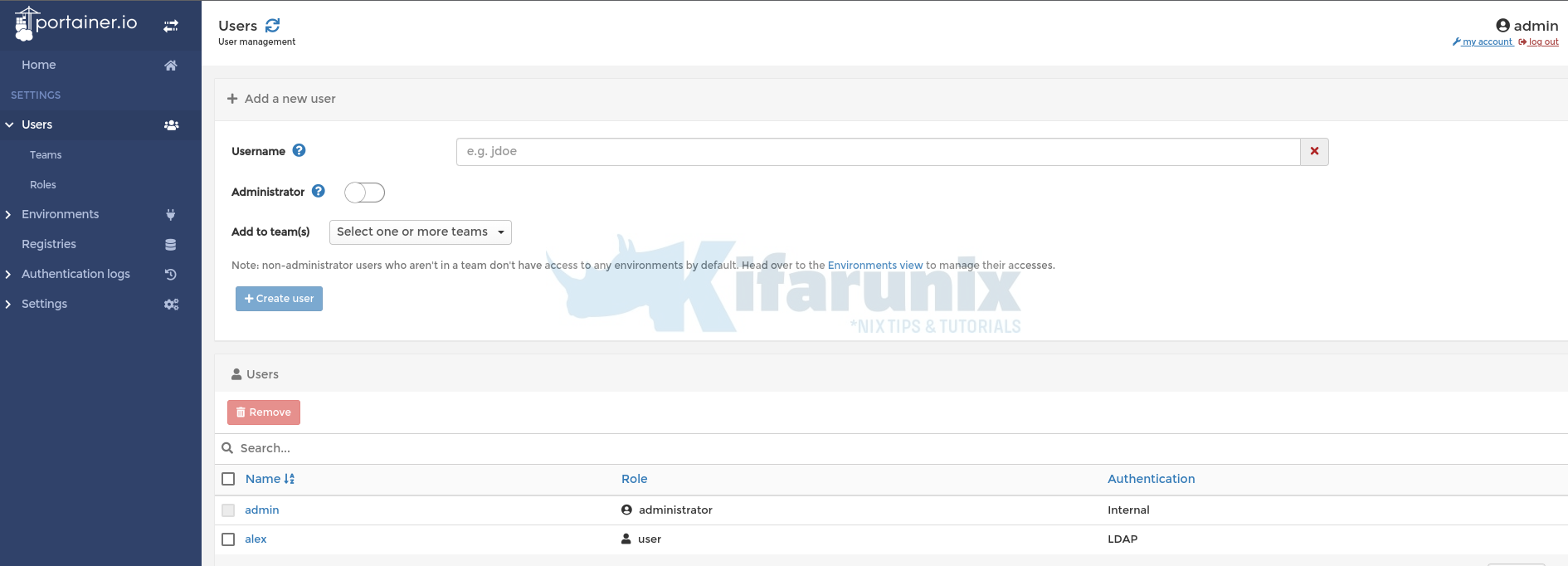
Under Users, you will see user alex or any other user who has logged in and authentication method is LDAP.
To grant Alex Portainer system wide admin access, click on the username alex and toggle the Administrator button on to make alex admin.
Save the changes by clicking Save button. Alex is now Portainer system wide administrator.
To avoid having to grant each individual user access to specific environments, you can utilize the groups created before. Remember we had two groups, admins and devops created both on LDAP and Portainer.
Thus, you can grant access to various endpoints to users based on their group names.
As you can see, at the moment, we only have the local Portainer docker environment connected;
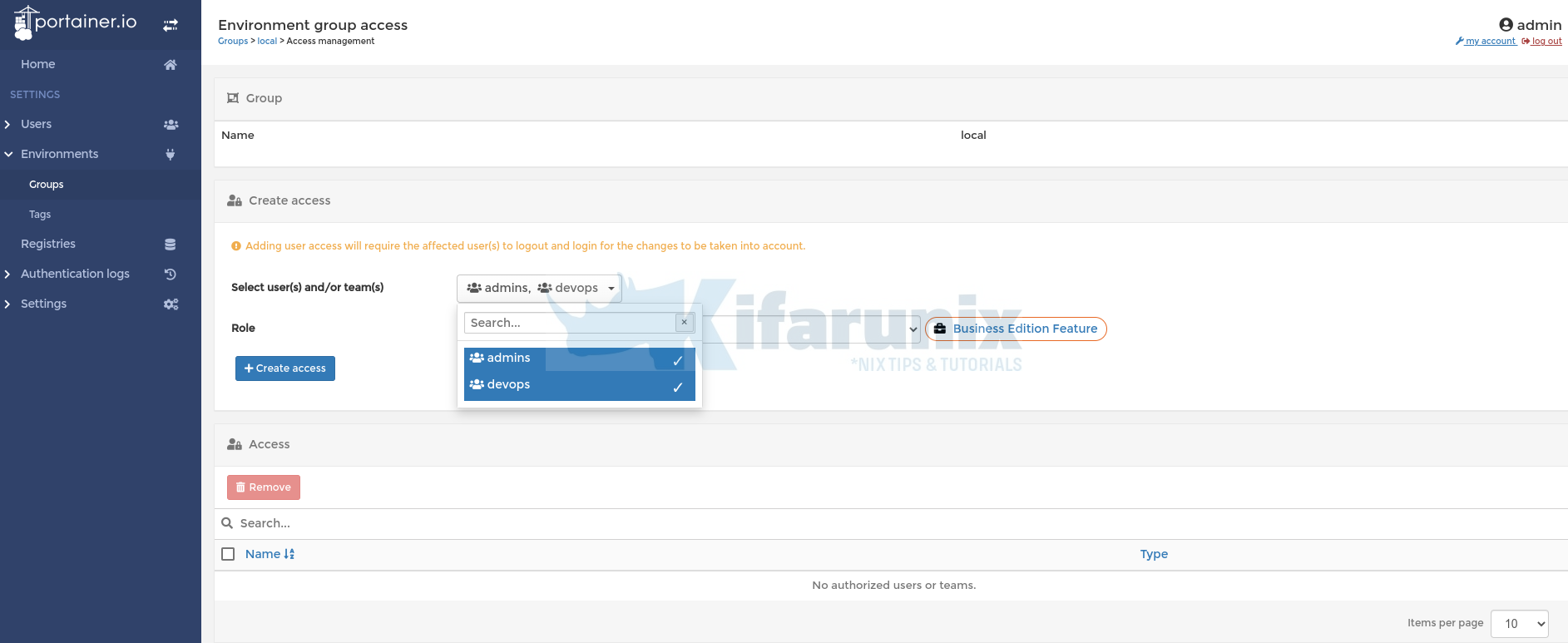
Now that we have two groups of users, lets grant users in admins/devops groups access to local environment.
Thus, under Environment > Groups > local environment > click Manage access. Under Create Access > Select user(s) and/or team(s) > Select teams. Ability to select roles other than standard user is not possible on community edition.
and click Create access.
You can also give access to specific components of the Portainer environment.
For example, click Home > Open specific environment e.g local > Stacks/Volumes/Networks/Containers > you can give access accordingly.
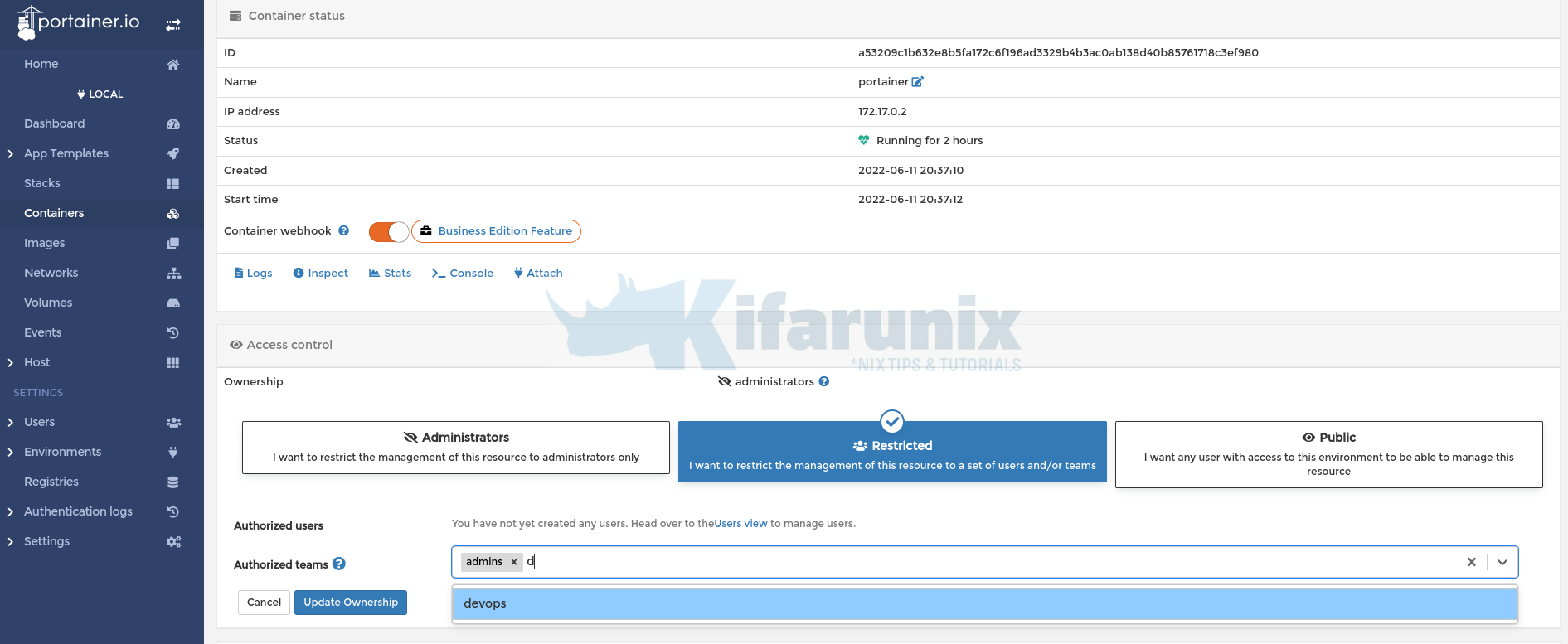
So take for example, to restrict access to Portainer containers, navigate to containers under local environment > click Portainer container name > Access Control > Change ownership > Restricted > Authorized teams > Select appropriate teams.
Update ownership.
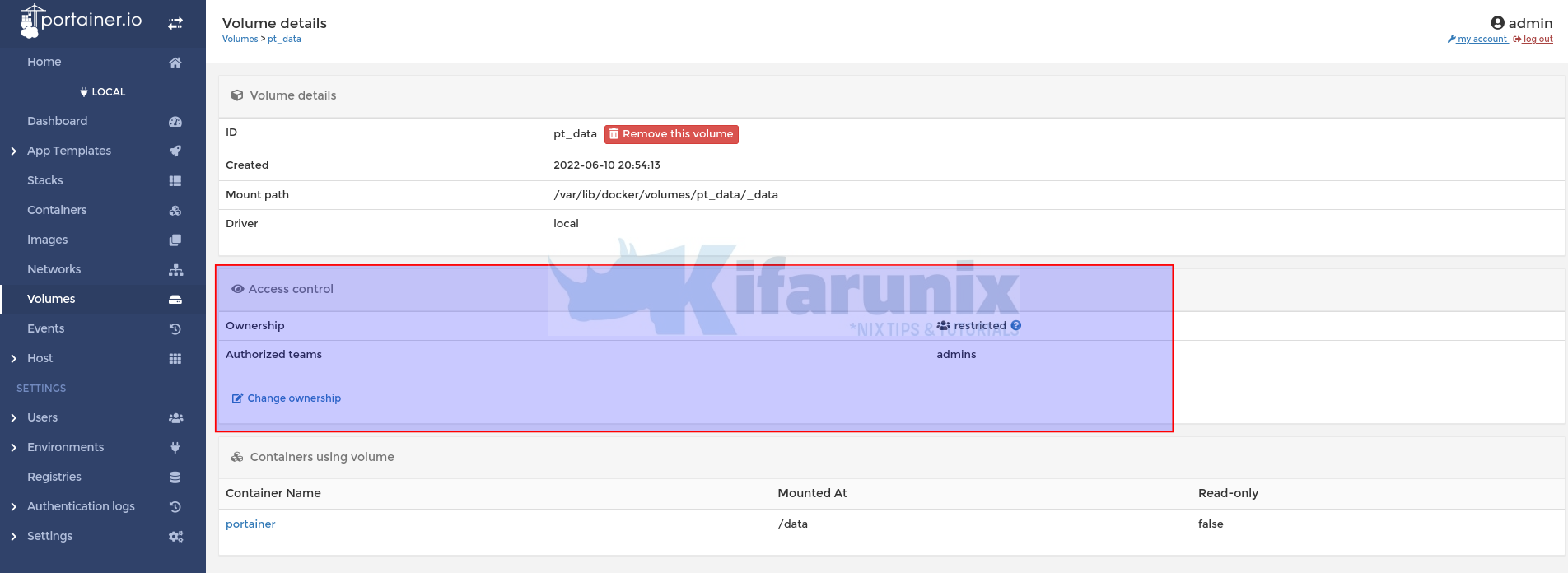
See screenshot below for restriction of the Volumes on the local environment to users in admins groups only;
If you login as a user in devops group, you wouldnt be able to access the restricted volume;
See johndoe from devops group cannot access volumes;
And that is how easy it is to control access to Portainer environment and specific resources using LDAP based authentication.