Follow through this tutorial to learn how to integrate sysPass with OpenLDAP for authentication and account management.
Install and Setup OpenLDAP server
In our previous tutorials, we covered how to install and setup OpenLDAP server. Follow the link below to check them.
Install and Setup OpenLDAP server
Install and Setup sysPass
Follow the link below to install and setup sysPass.
Install and setup sysPass on Linux
Integrate sysPass with OpenLDAP for Authentication
To begin, ensure sysPass is installed with PHP-LDAP modules.
php -m | grep ldapCreate OpenLDAP User Group for sysPass
Create an group of OpenLDAP that can be used to control access to sysPass. All members of the group to be created will allowed to access/login to sysPass.
Follow our guide below to learn how to setup OpenLDAP groups.
How to Create OpenLDAP Member Groups
In our OpenLDAP server, we have created a group called syspass.
Some members have been added to this group as evident in the command output below;
ldapsearch -H ldapi:/// -Y EXTERNAL -LLL -Q -b "dc=ldapmaster,dc=kifarunix-demo,dc=com" cn=syspassSample output;
dn: cn=syspass,ou=groups,dc=ldapmaster,dc=kifarunix-demo,dc=com
objectClass: groupOfNames
cn: syspass
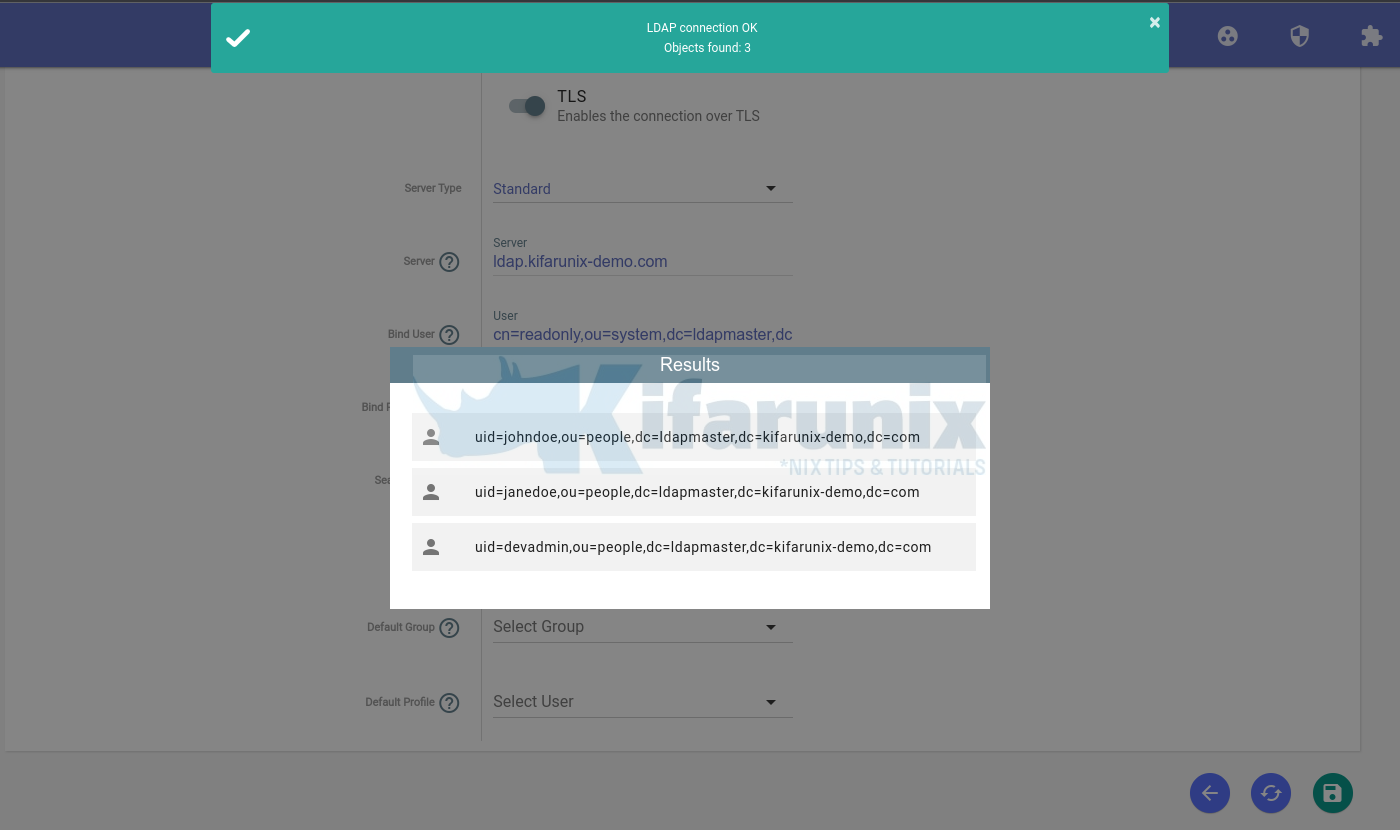
member: uid=johndoe,ou=people,dc=ldapmaster,dc=kifarunix-demo,dc=com
member: uid=janedoe,ou=people,dc=ldapmaster,dc=kifarunix-demo,dc=com
member: uid=devadmin,ou=people,dc=ldapmaster,dc=kifarunix-demo,dc=com
Once you have setup your OpenLDAP user/groups for sysPass authentication, login to sysPass web user interface as administrator.
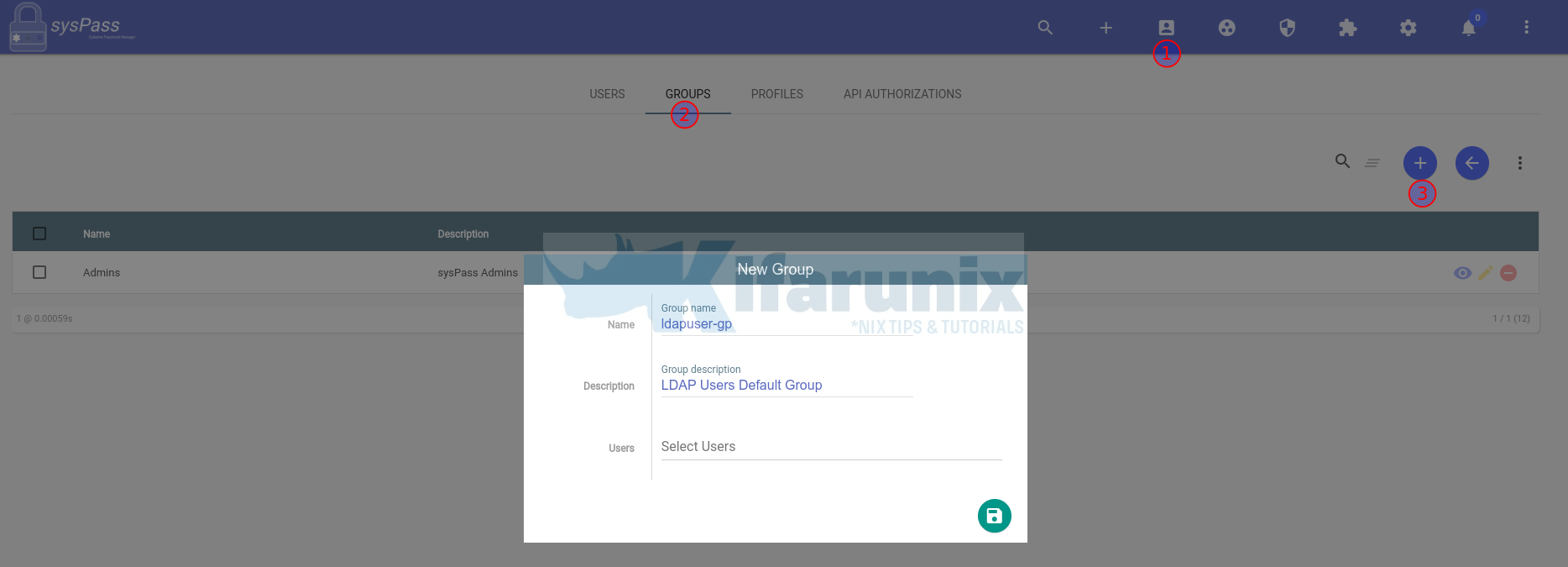
Create OpenLDAP users group.
This will be required to specify the default group under which OpenLDAP users belong to on sysPass.
To create group, click Users and accesses icon > GROUPS > New Group.
Save the group.
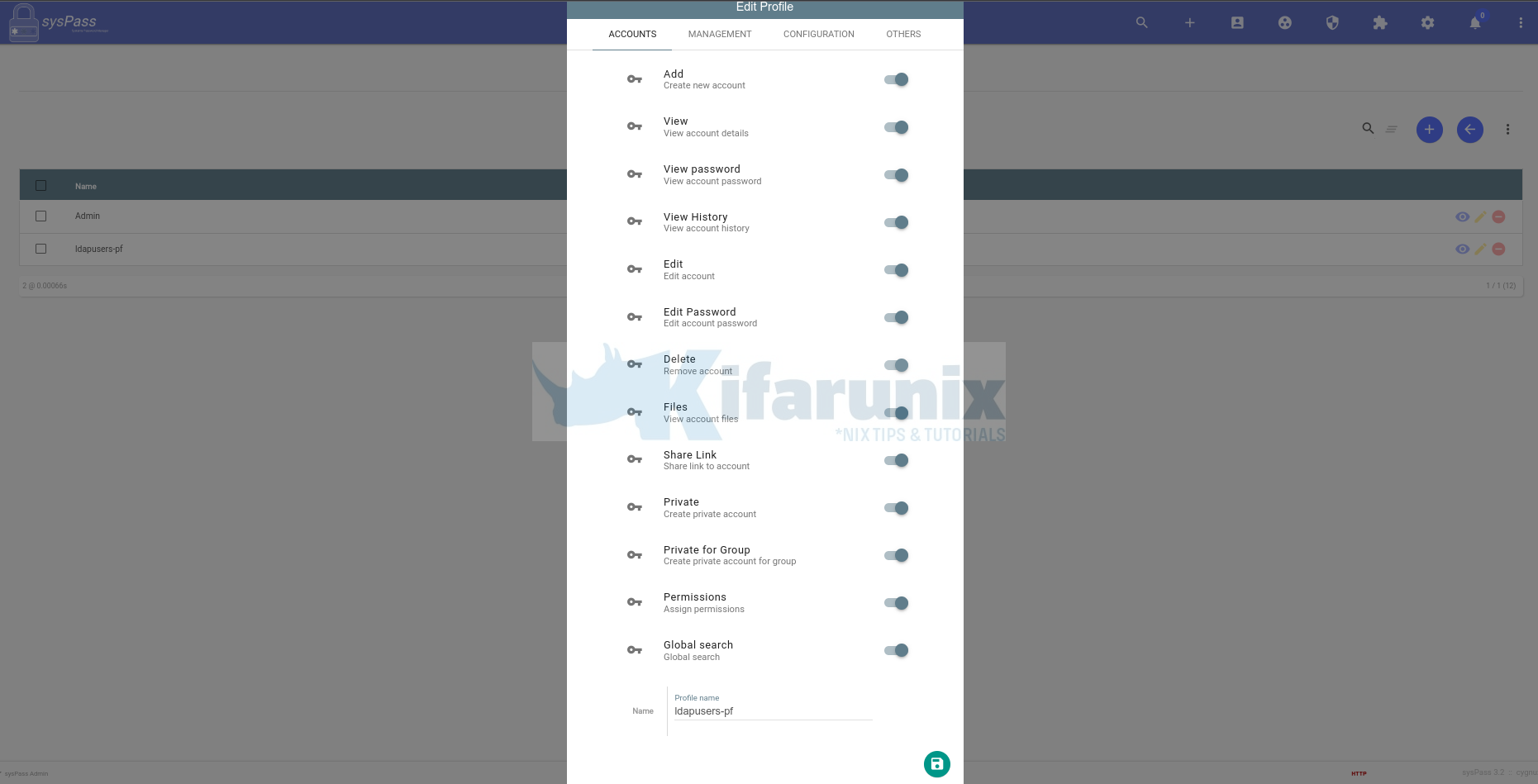
Next, create OpenLDAP Users default Profile
This is where you define the default permissions to be assigned to a specific user profile. To create a profile, click Users and accesses icon > PROFILE > New Profile.
Sample account permissioms.
For the rest of the accesses, we didn’t give any for this particular profile. Feel Free to set the accesses accordingly.
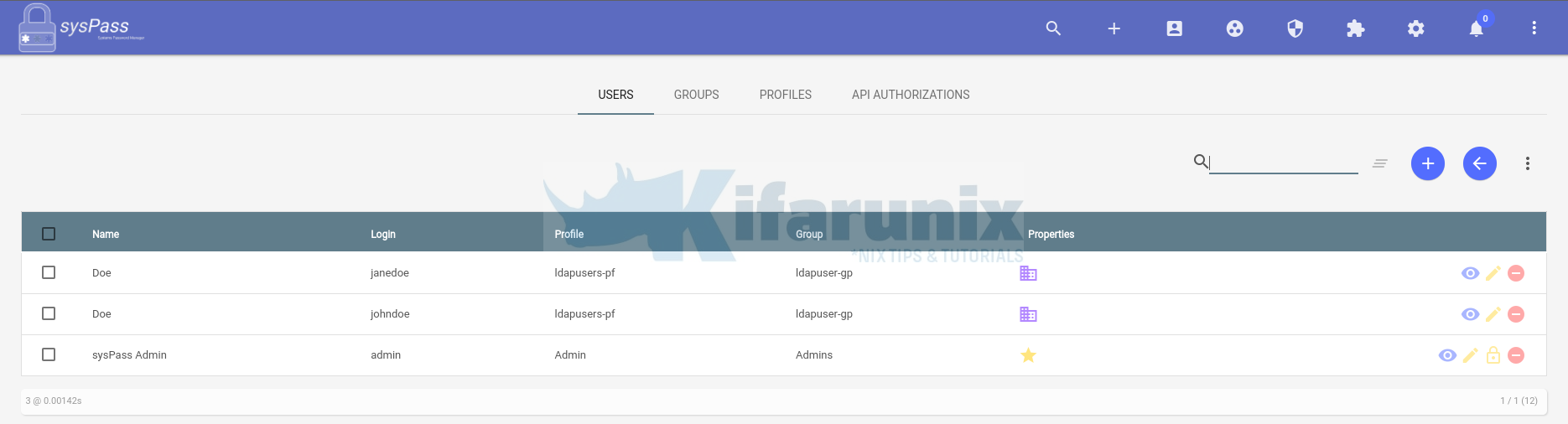
So we now have a group, ldapuser-gp, and profile, ldapusers-pf.
Note that you should be able to define the specific profile/groups once the LDAP users are in the sysPass system.
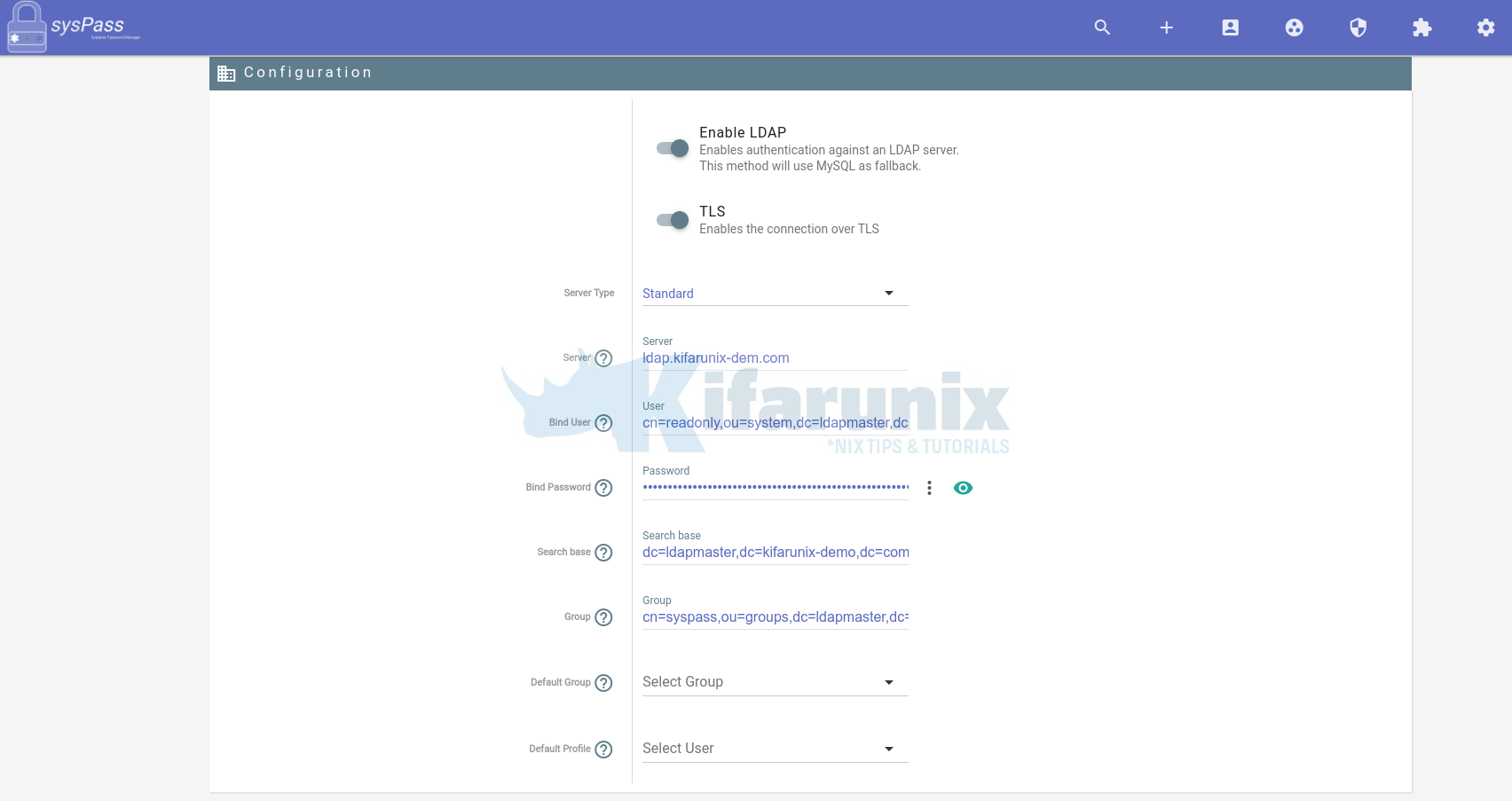
Next, click the gear icon to access the configuration menu and click LDAP.
- Define sysPass OpenLDAP Configuration options
- Toggle the button to enable LDAP based authentication.
- Also turn on TLS connection if your OpenLDAP server is configured with TLS.
- To be able to use TLS connection, you need to;
- Install LDAP CA cert on the sysPass server
- Define the LDAP CA Path on sysPass server as shown below.
- To be able to use TLS connection, you need to;
- Server type:
standard. - Server:
- This is the LDAP server url or IP address. In our setup, ldap.kifarunix-demo.com.
- Bind User:
- This is the DN of the user to authenticate. In our setup, it is
cn=readonly,ou=system,dc=ldapmaster,dc=kifarunix-demo,dc=com.
- This is the DN of the user to authenticate. In our setup, it is
- Bind Password:
- The credentials for the user to authenticate
- This is the password for the user specified by the bind DN above.
- Search Base:
- defines the location in the OpenLDAP directory where the search for a particular directory object begins.
- In our setup, the search base for users and groups is
dc=ldapmaster,dc=kifarunix-demo,dc=com.
- Group:
- This defines the group to which the user must belong to to be able to login to sysPass.
- As seen above, the group in our setup is
cn=syspass,ou=groups,dc=ldapmaster,dc=kifarunix-demo,dc=com.
- Default Group and Default Profile, leave empty.
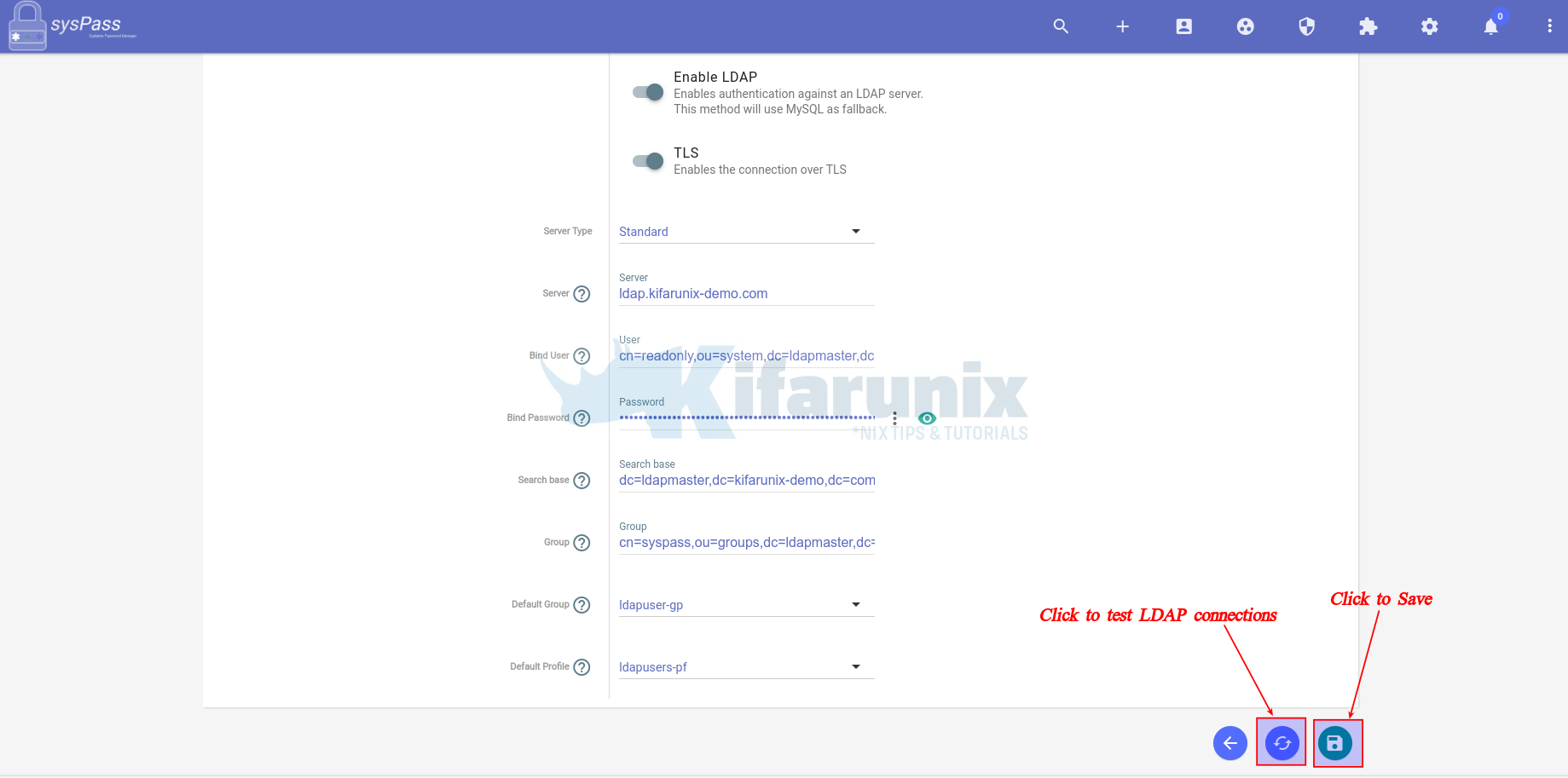
- Next, click the “exchange” icon to check connection to LDAP server. Ensure you have installed OpenLDAP CA certs if you enabled TLS before you can test the connection.
- If the connection is successful, you should see a list of all users in the OpenLDAP sysPass group.
Install OpenLDAP server CA cert and define the path on sysPass server.
Install OpenLDAP utilities on the sysPass server;
apt install ldap-utils -yDownload LDAP CA cert;
openssl s_client -connect ldap:389 -starttls ldap -showcerts </dev/null 2>/dev/null | openssl x509
-----BEGIN CERTIFICATE-----
MIIDozCCAougAwIBAgIUDd/aVBaJgUpWFNUbXOHYZTIb5KYwDQYJKoZIhvcNAQEL
BQAwYTELMAkGA1UEBhMCWFgxFTATBgNVBAcMDERlZmF1bHQgQ2l0eTEcMBoGA1UE
CgwTRGVmYXVsdCBDb21wYW55IEx0ZDEdMBsGA1UEAwwUKi5raWZhcnVuaXgtZGVt
by5jb20wHhcNMjIwMTIyMjAwOTUwWhcNMjMwMTIyMjAwOTUwWjBhMQswCQYDVQQG
EwJYWDEVMBMGA1UEBwwMRGVmYXVsdCBDaXR5MRwwGgYDVQQKDBNEZWZhdWx0IENv
bXBhbnkgTHRkMR0wGwYDVQQDDBQqLmtpZmFydW5peC1kZW1vLmNvbTCCASIwDQYJ
KoZIhvcNAQEBBQADggEPADCCAQoCggEBANVwVxFtjvHrgTHADFmE/NfsBjnnsorD
d6Hww+RDKTTdwpSQtAi5e9roP4umjLelQmIs2iPijBwFzTwh1ok7e40K0WFUCXwW
O2R2FomvwXe5D5VmlXLc4jY8/z6QuSv/j27q3DT44ywV8WmtWQ732cLo6YT1e441
LeXcCn258zvH8QE4UJOErJqDijFzuSxTj0gAsHe7ef+B2rhhD9Jzh6g4RYzDWmI3
oAZT/oArfWJFf+yP9eCunn/Q+b2RVWB9/Do9MYGdqOJJcDJ1w3pAyuEUWnDqTrhR
wjpIFub8lRlqrlNv7raw++aIIIUzCkl74/ReLgMRYlHAHC2pfMgLYjkCAwEAAaNT
MFEwHQYDVR0OBBYEFMN/TE6ZSw95erqDLAXa/LOfRFtqMB8GA1UdIwQYMBaAFMN/
TE6ZSw95erqDLAXa/LOfRFtqMA8GA1UdEwEB/wQFMAMBAf8wDQYJKoZIhvcNAQEL
BQADggEBAL+PuCNgR0MnOzl6IrxVZA9dDH0/DnMm2WjxkS3w5sfIPpUlVgSHmVeT
+a9raqFrve7RXHRBwouWlO/3n0218WSns6nyl9hTWbYIlIjCTFVCEFe68Q0ulcPy
AUEQBoKc6fUZCtenJDo2SVKt7dnX1EAi4Ohnig+f9zMrYFxYajdFAxJJV6wxJnnF
duLYpRexUxdzOvPUP4vkP2haZmRRWBDfmj2bSQF/r3DE4Yg8nVxHndsmxcVls4wF
7ddAL/Gx5Lv3QZPpxi8ZcHV8SRCP8N5VZP+hINr/M4gw3YO/S5F0TXnq5LQP0ePD
bkc1+yvlgKUPaXH20/C1COiGI+r8UGA=
-----END CERTIFICATE-----
Install the OpenLDAP CA cert on specific path;
cat > /etc/ssl/certs/openldap-ca.pem << 'EOL'
-----BEGIN CERTIFICATE-----
MIIDozCCAougAwIBAgIUDd/aVBaJgUpWFNUbXOHYZTIb5KYwDQYJKoZIhvcNAQEL
BQAwYTELMAkGA1UEBhMCWFgxFTATBgNVBAcMDERlZmF1bHQgQ2l0eTEcMBoGA1UE
CgwTRGVmYXVsdCBDb21wYW55IEx0ZDEdMBsGA1UEAwwUKi5raWZhcnVuaXgtZGVt
by5jb20wHhcNMjIwMTIyMjAwOTUwWhcNMjMwMTIyMjAwOTUwWjBhMQswCQYDVQQG
EwJYWDEVMBMGA1UEBwwMRGVmYXVsdCBDaXR5MRwwGgYDVQQKDBNEZWZhdWx0IENv
bXBhbnkgTHRkMR0wGwYDVQQDDBQqLmtpZmFydW5peC1kZW1vLmNvbTCCASIwDQYJ
KoZIhvcNAQEBBQADggEPADCCAQoCggEBANVwVxFtjvHrgTHADFmE/NfsBjnnsorD
d6Hww+RDKTTdwpSQtAi5e9roP4umjLelQmIs2iPijBwFzTwh1ok7e40K0WFUCXwW
O2R2FomvwXe5D5VmlXLc4jY8/z6QuSv/j27q3DT44ywV8WmtWQ732cLo6YT1e441
LeXcCn258zvH8QE4UJOErJqDijFzuSxTj0gAsHe7ef+B2rhhD9Jzh6g4RYzDWmI3
oAZT/oArfWJFf+yP9eCunn/Q+b2RVWB9/Do9MYGdqOJJcDJ1w3pAyuEUWnDqTrhR
wjpIFub8lRlqrlNv7raw++aIIIUzCkl74/ReLgMRYlHAHC2pfMgLYjkCAwEAAaNT
MFEwHQYDVR0OBBYEFMN/TE6ZSw95erqDLAXa/LOfRFtqMB8GA1UdIwQYMBaAFMN/
TE6ZSw95erqDLAXa/LOfRFtqMA8GA1UdEwEB/wQFMAMBAf8wDQYJKoZIhvcNAQEL
BQADggEBAL+PuCNgR0MnOzl6IrxVZA9dDH0/DnMm2WjxkS3w5sfIPpUlVgSHmVeT
+a9raqFrve7RXHRBwouWlO/3n0218WSns6nyl9hTWbYIlIjCTFVCEFe68Q0ulcPy
AUEQBoKc6fUZCtenJDo2SVKt7dnX1EAi4Ohnig+f9zMrYFxYajdFAxJJV6wxJnnF
duLYpRexUxdzOvPUP4vkP2haZmRRWBDfmj2bSQF/r3DE4Yg8nVxHndsmxcVls4wF
7ddAL/Gx5Lv3QZPpxi8ZcHV8SRCP8N5VZP+hINr/M4gw3YO/S5F0TXnq5LQP0ePD
bkc1+yvlgKUPaXH20/C1COiGI+r8UGA=
-----END CERTIFICATE-----
EOL
You can use one command though;
openssl s_client -connect ldap:389 -starttls ldap \
-showcerts </dev/null 2>/dev/null |\
openssl x509 > /etc/ssl/certs/openldap-ca.pemsysPass OpenLDAP User Login
Once you have configured sysPass for OpenLDAP authentication, you need to generate a temporary master password as it is required for every first login. Temporary master password is used so as not to reveal the original admin password.
To generate temporary master password, login to sysPass as admin and navigate to Configuration > Encryption > Temporary Password. Note the lifetime of the password.
For every new user logging in, share with them the temporary master password generated.
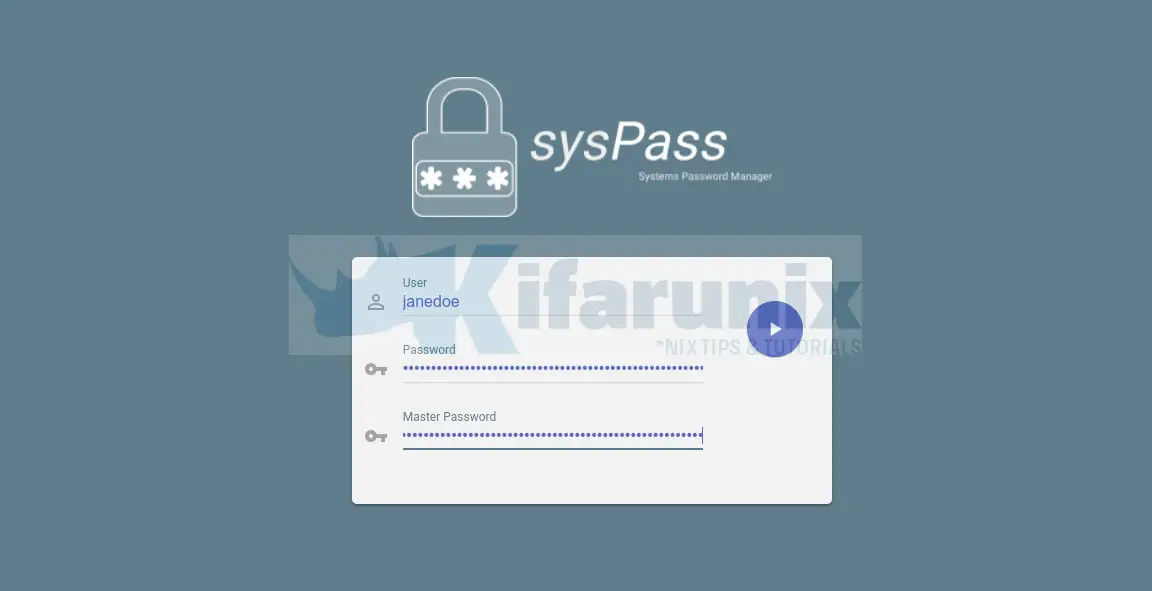
For example, logging in as our LDAP user janedoe;
When you first enter your credentials and press Enter, authentication will fail with Master password is not saved or wrong.
The enter the username/password and temporary master password provided.
From Administrator site, you should be able to see LDAP accounts added to the sysPass system.
And that is how easily you can sysPass can be integrated with OpenLDAP for authentication.
Other Tutorials