In this guide, you will learn how to install Wazuh agent on pfSense. pfSense is the world’s most trusted opensource firewall which also doubles up as an opensource router. On the other hand, Wazuh is a free, open source and enterprise-ready security monitoring solution for threat detection, integrity monitoring, incident response and compliance. Wazuh agents are used to collect log and event data from the remote end points that are being monitored and ship to the Wazuh server which then analyzes the event data and triggers alerts when threats or anomalies are detected.
Installing Wazuh Agent on pfSense
Ensure that you have Wazuh manager up and running before you can proceed.
We have covered installation and setup of Wazuh manager server on various systems in our previous guides.
Install and Configure Wazuh Manager on Ubuntu 22.04
Install Wazuh Server on Rocky Linux 8
Install and Setup Wazuh Server in CentOS 8/Fedora 32
Once the server is up and running, you can proceed to install the agent on pfSense.
Well, it is good to note that pfSense software is based on FreeBSD OS.
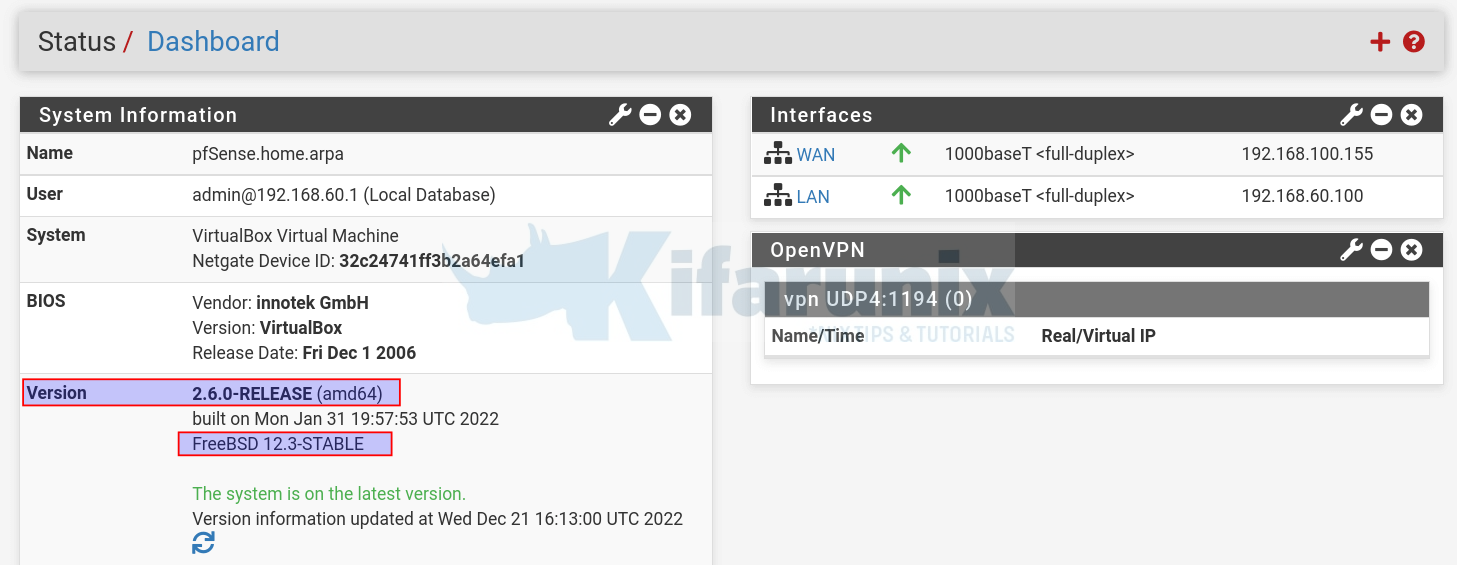
In my demo environment, we are running pfSense 2.6.0;
You can confirm from the command line;
cat /etc/versionSample output;
2.6.0-RELEASEOr from the pfSense dashboard;
As you can see, we have pfSense 2.6.0 based on FreeBSD 12.3.
Enable the use of FreeBSD Official Repositories on pfSense
Wazuh packages are not available on the official pfSense repositories. Thus the only way we can install Wazuh agent is via the use of official FreeBSD repos.
NOTE: Installing software/packages from FreeBSD repositories on pfSense can easily brick your system. This method is neither supported nor recommended by Netgate. Thus, if you have decided to proceed in this manner, then take utmost caution. We cannot be held responsible for whatever happens to your system.
To enable the use of FreeBSD repositories on pfSense;
- Edit the file
/usr/local/etc/pkg/repos/FreeBSD.conf;
vi /usr/local/etc/pkg/repos/FreeBSD.confand change the line;
FreeBSD: { enabled: no }to;
FreeBSD: { enabled: yes }- Edit the file
/usr/local/etc/pkg/repos/pfSense.conf;
vi /usr/local/etc/pkg/repos/pfSense.confand change the line;
FreeBSD: { enabled: no }to;
FreeBSD: { enabled: yes }Run Package Repository Catalogues Update
Once you have enabled the FreeBSD repositories, run the command below to updates package repository catalogues;
pkg updateSample output;
Updating FreeBSD repository catalogue...
Fetching meta.conf: 100% 163 B 0.2kB/s 00:01
Fetching packagesite.pkg: 100% 6 MiB 1.7MB/s 00:04
Processing entries: 100%
FreeBSD repository update completed. 33014 packages processed.
Updating pfSense-core repository catalogue...
pfSense-core repository is up to date.
Updating pfSense repository catalogue...
pfSense repository is up to date.
All repositories are up to date.
Check Available Wazuh Agent from FreeBSD Repos
As of this writing, Wazuh 4.3.10 is the current stable release version. Thus run the command below to check what version is provided by the official FreeBSD repositories;
pkg search wazuh-agentSample output;
wazuh-agent-4.3.10_1 Security tool to monitor and check logs and intrusions (agent)So we go the latest stable release Wazuh package!
We are also running Wazuh Manager 4.3.10!
/var/ossec/bin/wazuh-control infoWAZUH_VERSION="v4.3.10"
WAZUH_REVISION="40323"
WAZUH_TYPE="server"Installing Wazuh Agent
You can now install Wazuh agent package as follows;
pkg install wazuh-agentSample installation command output;
Updating FreeBSD repository catalogue...
FreeBSD repository is up to date.
...
...
=====
Message from wazuh-agent-4.3.10_1:
--
Wazuh Agent was installed
1) Copy /etc/locatime to /var/ossec/etc directory
# cp /etc/localtime /var/ossec/etc
2) You must edit /var/ossec/etc/ossec.conf.sample for your setup and rename/copy
it to ossec.conf
Take a look wazuh configuration at the following url:
https://documentation.wazuh.com/current/user-manual/index.html
3) You can find additional useful files installed at
# /var/ossec/packages_files/agent_installation_scripts
4) Add Wazuh agent to /etc/rc.conf
# sysrc wazuh_agent_enable="YES"
5) Start Wazuh agent
# service wazuh_agent start
6) Enjoy it ;)
The installation summary gives how to finalize Wazuh agent setup on pfSense.
As suggested;
- Copy /etc/locatime to /var/ossec/etc directory
cp /etc/localtime /var/ossec/etc- Rename the sample Wazuh agent configuration file,
/var/ossec/etc/ossec.conf.sampleto/var/ossec/etc/ossec.conf.
cp /var/ossec/etc/ossec.conf{.sample,}- Edit the Wazuh agent config file and set the Wazuh manager IP;
vi /var/ossec/etc/ossec.confChange the section;
<server>
<address>IP</address>
</server>to;
<server>
<address>192.168.58.22</address>
</server>- Add extract pfSense logs to monitor;
In my demo setup, apart from the default log files monitored by Wazuh by default;
<!-- Log analysis -->
<localfile>
<log_format>syslog</log_format>
<location>/var/ossec/logs/active-responses.log</location>
</localfile>
<localfile>
<log_format>syslog</log_format>
<location>/var/log/messages</location>
</localfile>
<localfile>
<log_format>syslog</log_format>
<location>/var/log/auth.log</location>
</localfile>
<localfile>
<log_format>syslog</log_format>
<location>/var/log/syslog</location>
</localfile>
<localfile>
<log_format>command</log_format>
<command>df -P</command>
<frequency>360</frequency>
</localfile>
<localfile>
<log_format>full_command</log_format>
<command>netstat -tan |grep LISTEN |grep -v 127.0.0.1 | sort</command>
<frequency>360</frequency>
</localfile>
<localfile>
<log_format>full_command</log_format>
<command>last -n 5</command>
<frequency>360</frequency>
</localfile>
I will add some more;
/var/log/openvpn.log
/var/log/system.log
/var/log/gateways.log
/var/log/userlogAs shown below;
<localfile>
<log_format>syslog</log_format>
<location>/var/log/openvpn.log</location>
</localfile>
<localfile>
<log_format>syslog</log_format>
<location>/var/log/system.log</location>
</localfile>
<localfile>
<log_format>syslog</log_format>
<location>/var/log/gateways.log</location>
</localfile>
<localfile>
<log_format>syslog</log_format>
<location>/var/log/userlog</location>
</localfile>
- Enable and start Wazuh agent;
sysrc wazuh_agent_enable="YES"/var/ossec/bin/wazuh-control startSample output;
Starting Wazuh v4.3.10...
Started wazuh-execd...
Started wazuh-agentd...
2022/12/21 20:47:01 wazuh-syscheckd: WARNING: The check_unixaudit option is deprecated in favor of the SCA module.
Started wazuh-syscheckd...
Started wazuh-logcollector...
Started wazuh-modulesd...
Completed.
You can check the logs file if any issue;
tail -f /var/ossec/logs/ossec.logDisable the use of FreeBSD Official Repositories on pfSense
You can now disable the use of FreeBSD official repositories on pfSense.
sed -iE '/FreeBSD: { enabled: yes }/s/yes/no/' /usr/local/etc/pkg/repos/FreeBSD.confvi /usr/local/etc/pkg/repos/pfSense.confand change the line;
FreeBSD: { enabled: yes }to;
FreeBSD: { enabled: no }Update package catalogue;
pkg clean allpkg updateConfirm pfSense Wazuh Agent Status on Wazuh Manager
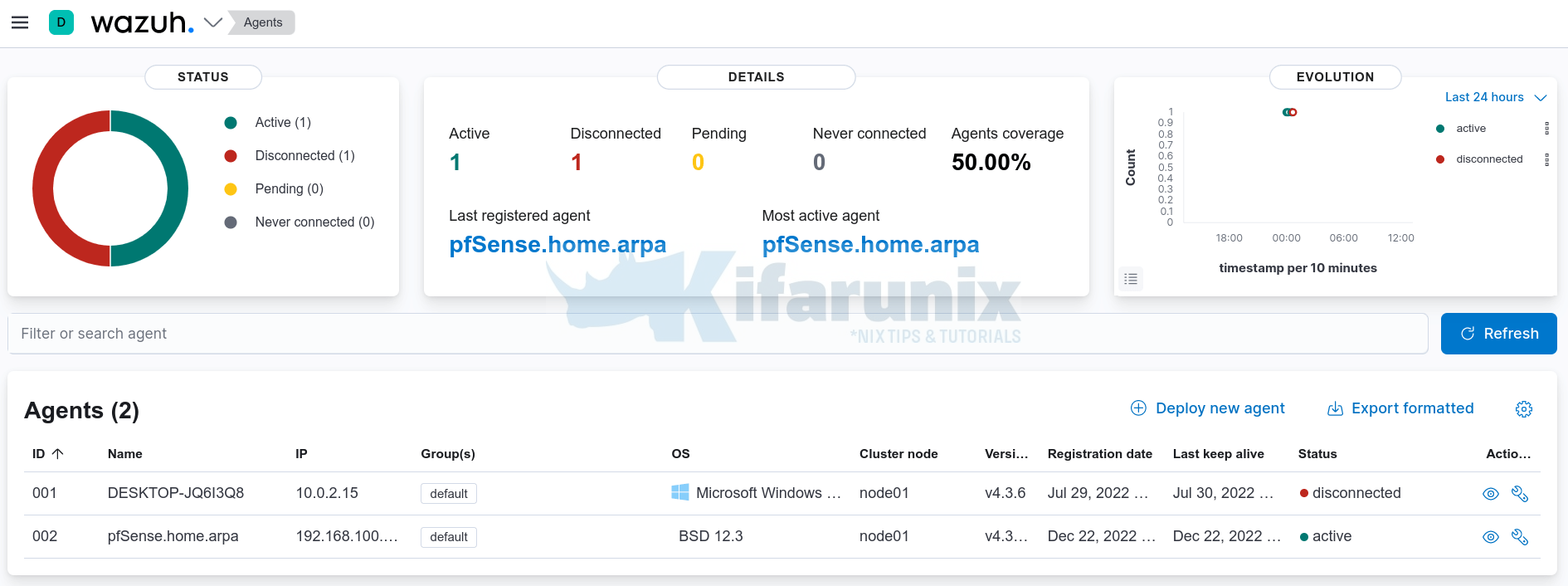
Login to Wazuh manager interface and confirm the pfSense agent status;
As you can see, the pfSense Wazuh agent (pfSense.home.arpa) is connected to the Wazuh server and is up and running.
You can simulate some activities such as;
- successful or failed logins to the server.
- e.t.c
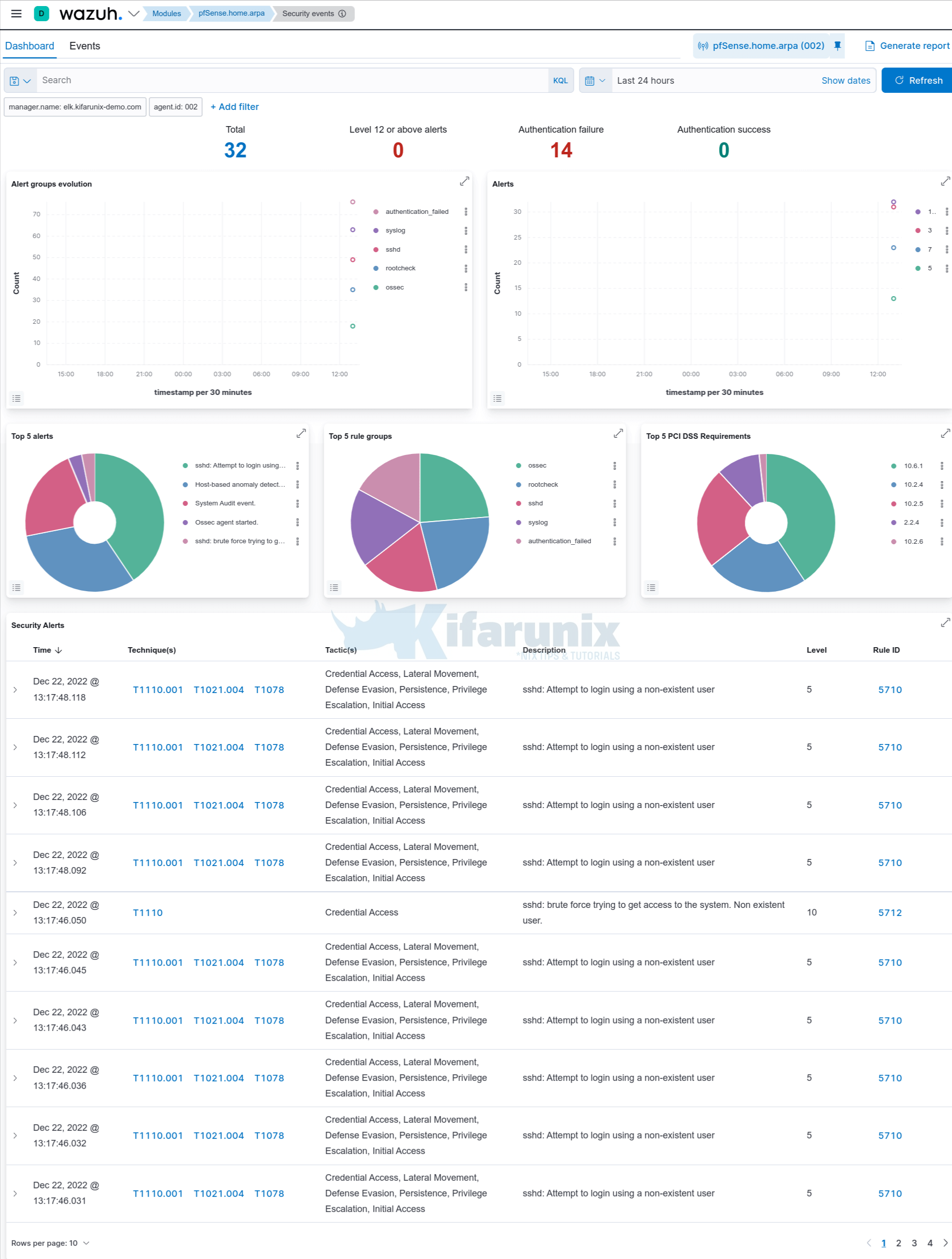
Now click on the agent to see more details related to events collected from it.
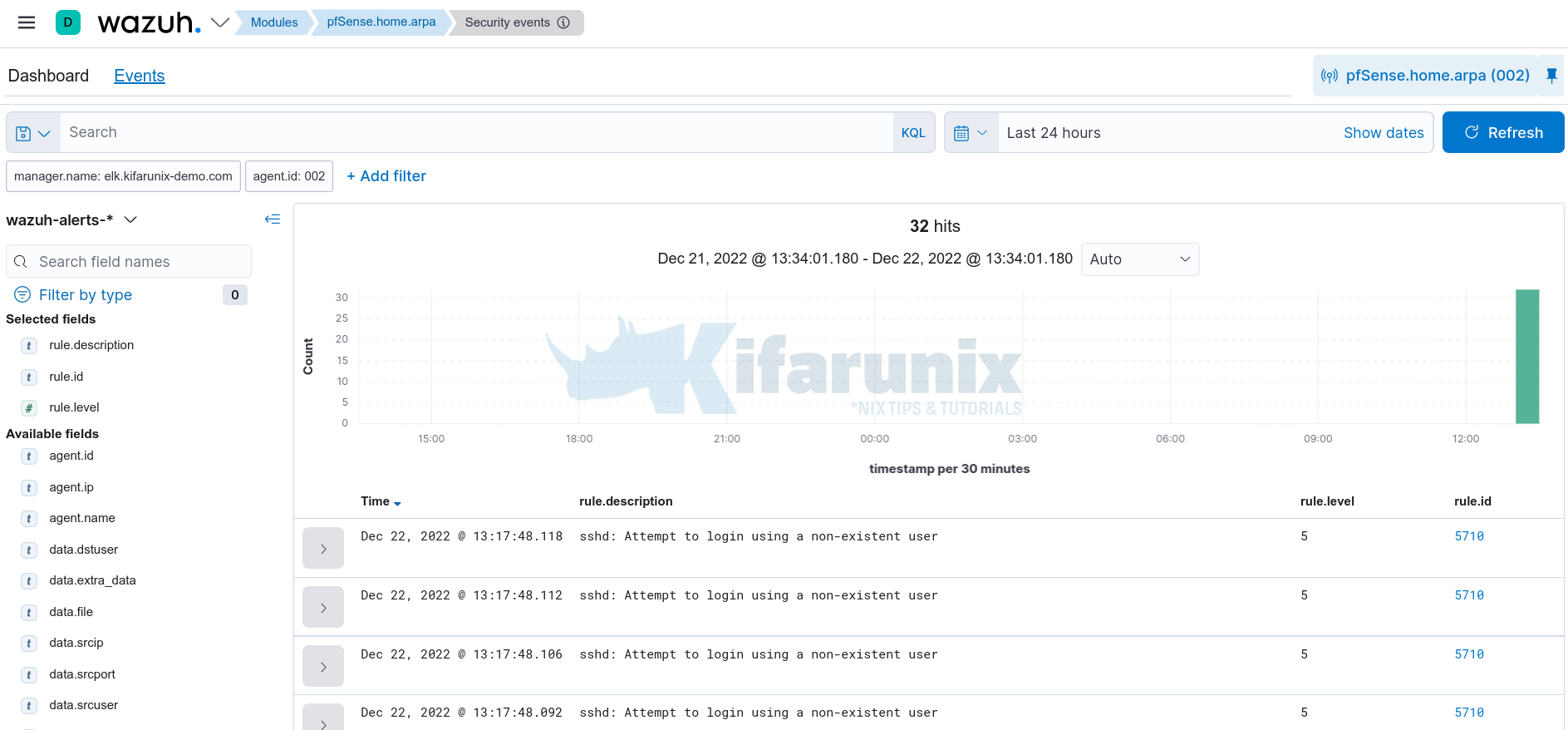
Click on Security Events to see more event details;
Dashboard
Events;
And that is it on how to install Wazuh agent on pfSense.



Hello I am Inri for 3 days I try to reproduce your tutorial but it does not work
what is the challenge?
Hello, for me, it does not work. Can you help me with your configuration?
Hello, it’s good it works. After doing it again, I saw my mistake. Thank you so much
Great. Glad to hear that
pardon quelle est ta solution? mon agent ne communique pas avec le serveur
Good morning. Please how to configure Wazuh server so that it can perform vulnerability scan of my pfsense router?
Good morning. Please how to configure Wazuh server so that it can perform vulnerability scan of my pfsense router
Hello, my pfsense is unable to update the pkg repository, gives the following error:
pkg: Error extracting the archive: ‘Write error’
pkg: No signature found
I have been googling for a week or so on it and haven’t found any answers up to this point. the FreeBSD.conf file is
FreeBSD: { enabled: yes }
the pfSense.conf file will revert automatically to FreeBSD: {enabled: no } after a few minutes from when i change it. I feel like 2.7.2 may have extra guards against adding BSD packages or my config is messed up for some reason.
To find updates and packages and the catalog you must execute the following commands on the pfSense :
certctl rehash
pkg-static update -f
pkg-static install -fy pkg pfSense-repo pfSense-upgrade
Hello, excellent tutorial! I tried it, but at the last step, the agent pfSense.home.arpa appears on my Wazuh server, but it always shows as ‘never connected’. Every time I try to redo the tutorial, I get the same issue. What could be the problem?”