In this tutorial, you will learn how to integrate Wazuh manager with ELK stack as a unified Security Information and Event management tool. Wazuh consists of an endpoint security agent, deployed to the monitored systems, and a management server, which collects and analyzes data gathered by the agents. Wazuh can be fully integrated with the Elastic Stack, which provides a search engine and data visualization tool that allows users to navigate through their security alerts.
Table of Contents
Integrating Wazuh Manager with ELK Stack
There are different deployment methods:
- All-in-one deployment where all the Wazuh and ELK components are installed on a single node. Suitable for testing or small working environements.
- Distributed deployment where each component is installed on a separate node. Provides high availability and scalability and hence suitable for large working environments.
This tutorial will use an all-in-one deployment method
Also NOTE that we are running our setup on an Debian system.
Install Wazuh Server on Debian 12/11/10
Install Wazuh Repository on Debian 12/11/10
To install the latest version of Wazuh server on Debian, you need to create the Wazuh repository as follows;
sudo su -apt install curl \
apt-transport-https \
unzip \
wget \
libcap2-bin \
software-properties-common \
lsb-release \
gnupg2
curl -s https://packages.wazuh.com/key/GPG-KEY-WAZUH | gpg --dearmor > /etc/apt/trusted.gpg.d/wazuh.gpgecho "deb https://packages.wazuh.com/4.x/apt stable main" | tee /etc/apt/sources.list.d/wazuh.list
Update the package information:
apt update
Install Wazuh Server on Debian 12/11/10
Next, install Wazuh manager on Debian 12/11/10.
apt install wazuh-manager
Once the installation is complete, you can start and enable Wazuh-manager to run on system boot;
systemctl enable --now wazuh-manager
Check the status;
systemctl status wazuh-manager● wazuh-manager.service - Wazuh manager
Loaded: loaded (/lib/systemd/system/wazuh-manager.service; enabled; preset: enabled)
Active: active (running) since Sat 2024-03-02 03:07:53 EST; 15s ago
Process: 1932 ExecStart=/usr/bin/env /var/ossec/bin/wazuh-control start (code=exited, status=0/SUCCESS)
Tasks: 139 (limit: 9475)
Memory: 642.1M
CPU: 21.665s
CGroup: /system.slice/wazuh-manager.service
├─1988 /var/ossec/framework/python/bin/python3 /var/ossec/api/scripts/wazuh-apid.py
├─2027 /var/ossec/bin/wazuh-authd
├─2044 /var/ossec/bin/wazuh-db
├─2067 /var/ossec/bin/wazuh-execd
├─2071 /var/ossec/framework/python/bin/python3 /var/ossec/api/scripts/wazuh-apid.py
├─2074 /var/ossec/framework/python/bin/python3 /var/ossec/api/scripts/wazuh-apid.py
├─2077 /var/ossec/framework/python/bin/python3 /var/ossec/api/scripts/wazuh-apid.py
├─2090 /var/ossec/bin/wazuh-analysisd
├─2151 /var/ossec/bin/wazuh-syscheckd
├─2166 /var/ossec/bin/wazuh-remoted
├─2198 /var/ossec/bin/wazuh-logcollector
├─2251 /var/ossec/bin/wazuh-monitord
└─2309 /var/ossec/bin/wazuh-modulesd
Mar 02 03:07:44 wazuh-elk env[1932]: Started wazuh-db...
Mar 02 03:07:45 wazuh-elk env[1932]: Started wazuh-execd...
Mar 02 03:07:46 wazuh-elk env[1932]: Started wazuh-analysisd...
Mar 02 03:07:47 wazuh-elk env[1932]: Started wazuh-syscheckd...
Mar 02 03:07:48 wazuh-elk env[1932]: Started wazuh-remoted...
Mar 02 03:07:49 wazuh-elk env[1932]: Started wazuh-logcollector...
Mar 02 03:07:50 wazuh-elk env[1932]: Started wazuh-monitord...
Mar 02 03:07:51 wazuh-elk env[1932]: Started wazuh-modulesd...
Mar 02 03:07:53 wazuh-elk env[1932]: Completed.
Mar 02 03:07:53 wazuh-elk systemd[1]: Started wazuh-manager.service - Wazuh manager.
Check that Wazuh ports are opened;
ss -altpn | grep -P '15\d+|55\d+'LISTEN 0 128 0.0.0.0:1514 0.0.0.0:* users:(("wazuh-remoted",pid=2166,fd=4))
LISTEN 0 128 0.0.0.0:1515 0.0.0.0:* users:(("wazuh-authd",pid=2027,fd=3))
LISTEN 0 128 0.0.0.0:55000 0.0.0.0:* users:(("python3",pid=1988,fd=40))
Install ELK/Elastic Stack on Debian 12/11/10
ELK Stack 8.12 is the current stable release of this guide update.
We have already provided a comprehensive tutorial on how to install and setup ELK stack 8 on Debian in our previous guide. So follow through to setup your ELK stack on Debian.
In the guide above, however, we didn’t cover installation of Logstash. So, once you are done installing Elasticsearch and Kibana, install Logstash. Ensure that all ELK stack components are of similar version number!
We already have ELK stack 8.x repos in place, so let us install Logstash 8;
apt install logstashIntegrating Wazuh Manager with ELK Stack
Install Logstash
As from Wazuh v4.6.0, Kibana plugins are not supported anymore. Thus, the only way to integrate Wazuh manager with ELK stack is to configure Wazuh manager to sent the security data to Logstash, which processes the data and sent to Elasticsearch indexing and search analytics engine, where you can visualize using Kibana.
We have already provided a command to install Logstash in the step above. So we are good to proceed.
As already mentioned before, this is a single node deployment. Hence, we have all the components, Wazuh manager, Kibana, Elasticsearch and Logstash on the same node. You can consider using a distributed deployment for production environments.
Install Logstash Elasticsearch output plugin
In in Logstash, output plugins are used to define where events processed by Logstash should be sent. These plugins determine the destination of the data after it has been filtered and processed. Logstash supports a variety of output plugins to facilitate sending data to different destinations. For example, the Elasticsearch output plugin in Logstash is used to send processed and transformed events to an Elasticsearch cluster.
You can install the plugin on the node running Logstash as follows;
/usr/share/logstash/bin/logstash-plugin install logstash-output-elasticsearchSample installation output;
Using bundled JDK: /usr/share/logstash/jdk
Validating logstash-output-elasticsearch
Resolving mixin dependencies
Updating mixin dependencies logstash-mixin-ecs_compatibility_support, logstash-mixin-deprecation_logger_support, logstash-mixin-ca_trusted_fingerprint_support, logstash-mixin-normalize_config_support
Bundler attempted to update logstash-mixin-ecs_compatibility_support but its version stayed the same
Bundler attempted to update logstash-mixin-deprecation_logger_support but its version stayed the same
Bundler attempted to update logstash-mixin-ca_trusted_fingerprint_support but its version stayed the same
Bundler attempted to update logstash-mixin-normalize_config_support but its version stayed the same
Installing logstash-output-elasticsearch
Installation successful
Install Elasticsearch Mapping Template
In this step, we will configure Elasticsearch to use a predefined Logstash/Wazuh mapping template. The mappings define how fields are interpreted by Elasticsearch. This ensures that Elasticsearch can index the Wazuh data collected by Logstash correctly.
To use a custom Elasticsearch mapping template, you define a valid path to the location of the custom template json file on the Logstash Elasticsearch output configuration using the template option.
Thus, run the command below to install Wazuh Elasticsearch mapping template.
curl -sL https://packages.wazuh.com/integrations/elastic/4.x-8.x/dashboards/wz-es-4.x-8.x-template.json -o /etc/logstash/wazuh.json
This is how the template look like by default;
cat /etc/logstash/wazuh.json{
"index_patterns": "wazuh-*",
"template": {
"settings": {
"index": {
"routing": {
"allocation": {
"include": {
"_tier_preference": "data_content"
}
}
},
"mapping": {
"total_fields": {
"limit": "10000"
}
},
"refresh_interval": "5s",
"number_of_shards": "3",
"auto_expand_replicas": "0-1",
"query": {
"default_field": [
"GeoLocation.city_name",
"GeoLocation.continent_code",
"GeoLocation.country_code2",
"GeoLocation.country_code3",
"GeoLocation.country_name",
"GeoLocation.ip",
"GeoLocation.postal_code",
"GeoLocation.real_region_name",
"GeoLocation.region_name",
"GeoLocation.timezone",
"agent.id",
"agent.ip",
"agent.name",
"cluster.name",
"cluster.node",
"command",
"data",
"data.action",
"data.audit",
"data.audit.acct",
"data.audit.arch",
"data.audit.auid",
"data.audit.command",
"data.audit.cwd",
"data.audit.dev",
"data.audit.directory.inode",
"data.audit.directory.mode",
"data.audit.directory.name",
"data.audit.egid",
"data.audit.enforcing",
"data.audit.euid",
"data.audit.exe",
"data.audit.execve.a0",
"data.audit.execve.a1",
"data.audit.execve.a2",
"data.audit.execve.a3",
"data.audit.exit",
"data.audit.file.inode",
"data.audit.file.mode",
"data.audit.file.name",
"data.audit.fsgid",
"data.audit.fsuid",
"data.audit.gid",
"data.audit.id",
"data.audit.key",
"data.audit.list",
"data.audit.old-auid",
"data.audit.old-ses",
"data.audit.old_enforcing",
"data.audit.old_prom",
"data.audit.op",
"data.audit.pid",
"data.audit.ppid",
"data.audit.prom",
"data.audit.res",
"data.audit.session",
"data.audit.sgid",
"data.audit.srcip",
"data.audit.subj",
"data.audit.success",
"data.audit.suid",
"data.audit.syscall",
"data.audit.tty",
"data.audit.uid",
"data.aws.accountId",
"data.aws.account_id",
"data.aws.action",
"data.aws.actor",
"data.aws.aws_account_id",
"data.aws.description",
"data.aws.dstport",
"data.aws.errorCode",
"data.aws.errorMessage",
"data.aws.eventID",
"data.aws.eventName",
"data.aws.eventSource",
"data.aws.eventType",
"data.aws.id",
"data.aws.name",
"data.aws.requestParameters.accessKeyId",
"data.aws.requestParameters.bucketName",
"data.aws.requestParameters.gatewayId",
"data.aws.requestParameters.groupDescription",
"data.aws.requestParameters.groupId",
"data.aws.requestParameters.groupName",
"data.aws.requestParameters.host",
"data.aws.requestParameters.hostedZoneId",
"data.aws.requestParameters.instanceId",
"data.aws.requestParameters.instanceProfileName",
"data.aws.requestParameters.loadBalancerName",
"data.aws.requestParameters.loadBalancerPorts",
"data.aws.requestParameters.masterUserPassword",
"data.aws.requestParameters.masterUsername",
"data.aws.requestParameters.name",
"data.aws.requestParameters.natGatewayId",
"data.aws.requestParameters.networkAclId",
"data.aws.requestParameters.path",
"data.aws.requestParameters.policyName",
"data.aws.requestParameters.port",
"data.aws.requestParameters.stackId",
"data.aws.requestParameters.stackName",
"data.aws.requestParameters.subnetId",
"data.aws.requestParameters.subnetIds",
"data.aws.requestParameters.volumeId",
"data.aws.requestParameters.vpcId",
"data.aws.resource.accessKeyDetails.accessKeyId",
"data.aws.resource.accessKeyDetails.principalId",
"data.aws.resource.accessKeyDetails.userName",
"data.aws.resource.instanceDetails.instanceId",
"data.aws.resource.instanceDetails.instanceState",
"data.aws.resource.instanceDetails.networkInterfaces.privateDnsName",
"data.aws.resource.instanceDetails.networkInterfaces.publicDnsName",
"data.aws.resource.instanceDetails.networkInterfaces.subnetId",
"data.aws.resource.instanceDetails.networkInterfaces.vpcId",
"data.aws.resource.instanceDetails.tags.value",
"data.aws.responseElements.AssociateVpcCidrBlockResponse.vpcId",
"data.aws.responseElements.description",
"data.aws.responseElements.instanceId",
"data.aws.responseElements.instances.instanceId",
"data.aws.responseElements.instancesSet.items.instanceId",
"data.aws.responseElements.listeners.port",
"data.aws.responseElements.loadBalancerName",
"data.aws.responseElements.loadBalancers.vpcId",
"data.aws.responseElements.loginProfile.userName",
"data.aws.responseElements.networkAcl.vpcId",
"data.aws.responseElements.ownerId",
"data.aws.responseElements.publicIp",
"data.aws.responseElements.user.userId",
"data.aws.responseElements.user.userName",
"data.aws.responseElements.volumeId",
"data.aws.service.serviceName",
"data.aws.severity",
"data.aws.source",
"data.aws.sourceIPAddress",
"data.aws.srcport",
"data.aws.userIdentity.accessKeyId",
"data.aws.userIdentity.accountId",
"data.aws.userIdentity.userName",
"data.aws.vpcEndpointId",
"data.command",
"data.data",
"data.docker.Actor.Attributes.container",
"data.docker.Actor.Attributes.image",
"data.docker.Actor.Attributes.name",
"data.docker.Actor.ID",
"data.docker.id",
"data.docker.message",
"data.docker.status",
"data.dstip",
"data.dstport",
"data.dstuser",
"data.extra_data",
"data.hardware.serial",
"data.id",
"data.integration",
"data.netinfo.iface.adapter",
"data.netinfo.iface.ipv4.address",
"data.netinfo.iface.ipv6.address",
"data.netinfo.iface.mac",
"data.netinfo.iface.name",
"data.os.architecture",
"data.os.build",
"data.os.codename",
"data.os.hostname",
"data.os.major",
"data.os.minor",
"data.os.name",
"data.os.platform",
"data.os.release",
"data.os.release_version",
"data.os.sysname",
"data.os.version",
"data.oscap.check.description",
"data.oscap.check.id",
"data.oscap.check.identifiers",
"data.oscap.check.oval.id",
"data.oscap.check.rationale",
"data.oscap.check.references",
"data.oscap.check.result",
"data.oscap.check.severity",
"data.oscap.check.title",
"data.oscap.scan.benchmark.id",
"data.oscap.scan.content",
"data.oscap.scan.id",
"data.oscap.scan.profile.id",
"data.oscap.scan.profile.title",
"data.osquery.columns.address",
"data.osquery.columns.command",
"data.osquery.columns.description",
"data.osquery.columns.dst_ip",
"data.osquery.columns.gid",
"data.osquery.columns.hostname",
"data.osquery.columns.md5",
"data.osquery.columns.path",
"data.osquery.columns.sha1",
"data.osquery.columns.sha256",
"data.osquery.columns.src_ip",
"data.osquery.columns.user",
"data.osquery.columns.username",
"data.osquery.name",
"data.osquery.pack",
"data.port.process",
"data.port.protocol",
"data.port.state",
"data.process.args",
"data.process.cmd",
"data.process.egroup",
"data.process.euser",
"data.process.fgroup",
"data.process.name",
"data.process.rgroup",
"data.process.ruser",
"data.process.sgroup",
"data.process.state",
"data.process.suser",
"data.program.architecture",
"data.program.description",
"data.program.format",
"data.program.location",
"data.program.multiarch",
"data.program.name",
"data.program.priority",
"data.program.section",
"data.program.source",
"data.program.vendor",
"data.program.version",
"data.protocol",
"data.pwd",
"data.sca",
"data.sca.check.compliance.cis",
"data.sca.check.compliance.cis_csc",
"data.sca.check.compliance.pci_dss",
"data.sca.check.compliance.hipaa",
"data.sca.check.compliance.nist_800_53",
"data.sca.check.description",
"data.sca.check.directory",
"data.sca.check.file",
"data.sca.check.id",
"data.sca.check.previous_result",
"data.sca.check.process",
"data.sca.check.rationale",
"data.sca.check.reason",
"data.sca.check.references",
"data.sca.check.registry",
"data.sca.check.remediation",
"data.sca.check.result",
"data.sca.check.status",
"data.sca.check.title",
"data.sca.description",
"data.sca.file",
"data.sca.invalid",
"data.sca.name",
"data.sca.policy",
"data.sca.policy_id",
"data.sca.scan_id",
"data.sca.total_checks",
"data.script",
"data.src_ip",
"data.src_port",
"data.srcip",
"data.srcport",
"data.srcuser",
"data.status",
"data.system_name",
"data.title",
"data.tty",
"data.uid",
"data.url",
"data.virustotal.description",
"data.virustotal.error",
"data.virustotal.found",
"data.virustotal.permalink",
"data.virustotal.scan_date",
"data.virustotal.sha1",
"data.virustotal.source.alert_id",
"data.virustotal.source.file",
"data.virustotal.source.md5",
"data.virustotal.source.sha1",
"data.vulnerability.cve",
"data.vulnerability.cvss.cvss2.base_score",
"data.vulnerability.cvss.cvss2.exploitability_score",
"data.vulnerability.cvss.cvss2.impact_score",
"data.vulnerability.cvss.cvss2.vector.access_complexity",
"data.vulnerability.cvss.cvss2.vector.attack_vector",
"data.vulnerability.cvss.cvss2.vector.authentication",
"data.vulnerability.cvss.cvss2.vector.availability",
"data.vulnerability.cvss.cvss2.vector.confidentiality_impact",
"data.vulnerability.cvss.cvss2.vector.integrity_impact",
"data.vulnerability.cvss.cvss2.vector.privileges_required",
"data.vulnerability.cvss.cvss2.vector.scope",
"data.vulnerability.cvss.cvss2.vector.user_interaction",
"data.vulnerability.cvss.cvss3.base_score",
"data.vulnerability.cvss.cvss3.exploitability_score",
"data.vulnerability.cvss.cvss3.impact_score",
"data.vulnerability.cvss.cvss3.vector.access_complexity",
"data.vulnerability.cvss.cvss3.vector.attack_vector",
"data.vulnerability.cvss.cvss3.vector.authentication",
"data.vulnerability.cvss.cvss3.vector.availability",
"data.vulnerability.cvss.cvss3.vector.confidentiality_impact",
"data.vulnerability.cvss.cvss3.vector.integrity_impact",
"data.vulnerability.cvss.cvss3.vector.privileges_required",
"data.vulnerability.cvss.cvss3.vector.scope",
"data.vulnerability.cvss.cvss3.vector.user_interaction",
"data.vulnerability.cwe_reference",
"data.vulnerability.package.source",
"data.vulnerability.package.architecture",
"data.vulnerability.package.condition",
"data.vulnerability.package.generated_cpe",
"data.vulnerability.package.name",
"data.vulnerability.package.version",
"data.vulnerability.rationale",
"data.vulnerability.severity",
"data.vulnerability.title",
"data.vulnerability.assigner",
"data.vulnerability.cve_version",
"data.win.eventdata.auditPolicyChanges",
"data.win.eventdata.auditPolicyChangesId",
"data.win.eventdata.binary",
"data.win.eventdata.category",
"data.win.eventdata.categoryId",
"data.win.eventdata.data",
"data.win.eventdata.image",
"data.win.eventdata.ipAddress",
"data.win.eventdata.ipPort",
"data.win.eventdata.keyName",
"data.win.eventdata.logonGuid",
"data.win.eventdata.logonProcessName",
"data.win.eventdata.operation",
"data.win.eventdata.parentImage",
"data.win.eventdata.processId",
"data.win.eventdata.processName",
"data.win.eventdata.providerName",
"data.win.eventdata.returnCode",
"data.win.eventdata.service",
"data.win.eventdata.status",
"data.win.eventdata.subcategory",
"data.win.eventdata.subcategoryGuid",
"data.win.eventdata.subcategoryId",
"data.win.eventdata.subjectDomainName",
"data.win.eventdata.subjectLogonId",
"data.win.eventdata.subjectUserName",
"data.win.eventdata.subjectUserSid",
"data.win.eventdata.targetDomainName",
"data.win.eventdata.targetLinkedLogonId",
"data.win.eventdata.targetLogonId",
"data.win.eventdata.targetUserName",
"data.win.eventdata.targetUserSid",
"data.win.eventdata.workstationName",
"data.win.system.channel",
"data.win.system.computer",
"data.win.system.eventID",
"data.win.system.eventRecordID",
"data.win.system.eventSourceName",
"data.win.system.keywords",
"data.win.system.level",
"data.win.system.message",
"data.win.system.opcode",
"data.win.system.processID",
"data.win.system.providerGuid",
"data.win.system.providerName",
"data.win.system.securityUserID",
"data.win.system.severityValue",
"data.win.system.userID",
"decoder.ftscomment",
"decoder.name",
"decoder.parent",
"full_log",
"host",
"id",
"input",
"location",
"manager.name",
"message",
"offset",
"predecoder.hostname",
"predecoder.program_name",
"previous_log",
"previous_output",
"program_name",
"rule.cis",
"rule.cve",
"rule.description",
"rule.gdpr",
"rule.gpg13",
"rule.groups",
"rule.id",
"rule.info",
"rule.mitre.id",
"rule.mitre.tactic",
"rule.mitre.technique",
"rule.pci_dss",
"rule.hipaa",
"rule.nist_800_53",
"syscheck.audit.effective_user.id",
"syscheck.audit.effective_user.name",
"syscheck.audit.group.id",
"syscheck.audit.group.name",
"syscheck.audit.login_user.id",
"syscheck.audit.login_user.name",
"syscheck.audit.process.id",
"syscheck.audit.process.name",
"syscheck.audit.process.ppid",
"syscheck.audit.user.id",
"syscheck.audit.user.name",
"syscheck.diff",
"syscheck.event",
"syscheck.gid_after",
"syscheck.gid_before",
"syscheck.gname_after",
"syscheck.gname_before",
"syscheck.inode_after",
"syscheck.inode_before",
"syscheck.md5_after",
"syscheck.md5_before",
"syscheck.path",
"syscheck.mode",
"syscheck.perm_after",
"syscheck.perm_before",
"syscheck.sha1_after",
"syscheck.sha1_before",
"syscheck.sha256_after",
"syscheck.sha256_before",
"syscheck.tags",
"syscheck.uid_after",
"syscheck.uid_before",
"syscheck.uname_after",
"syscheck.uname_before",
"title",
"type"
]
},
"number_of_replicas": "0"
}
},
"mappings": {
"dynamic_templates": [
{
"string_as_keyword": {
"match_mapping_type": "string",
"mapping": {
"type": "keyword"
}
}
}
],
"date_detection": false,
"properties": {
"@timestamp": {
"type": "date"
},
"@version": {
"type": "text"
},
"GeoLocation": {
"properties": {
"area_code": {
"type": "long"
},
"city_name": {
"type": "keyword"
},
"continent_code": {
"type": "text"
},
"coordinates": {
"type": "double"
},
"country_code2": {
"type": "text"
},
"country_code3": {
"type": "text"
},
"country_name": {
"type": "keyword"
},
"dma_code": {
"type": "long"
},
"ip": {
"type": "keyword"
},
"latitude": {
"type": "double"
},
"location": {
"type": "geo_point"
},
"longitude": {
"type": "double"
},
"postal_code": {
"type": "keyword"
},
"real_region_name": {
"type": "keyword"
},
"region_name": {
"type": "keyword"
},
"timezone": {
"type": "text"
}
}
},
"agent": {
"properties": {
"id": {
"type": "keyword"
},
"ip": {
"type": "keyword"
},
"name": {
"type": "keyword"
}
}
},
"cluster": {
"properties": {
"name": {
"type": "keyword"
},
"node": {
"type": "keyword"
}
}
},
"command": {
"type": "keyword"
},
"data": {
"properties": {
"action": {
"type": "keyword"
},
"audit": {
"properties": {
"acct": {
"type": "keyword"
},
"arch": {
"type": "keyword"
},
"auid": {
"type": "keyword"
},
"command": {
"type": "keyword"
},
"cwd": {
"type": "keyword"
},
"dev": {
"type": "keyword"
},
"directory": {
"properties": {
"inode": {
"type": "keyword"
},
"mode": {
"type": "keyword"
},
"name": {
"type": "keyword"
}
}
},
"egid": {
"type": "keyword"
},
"enforcing": {
"type": "keyword"
},
"euid": {
"type": "keyword"
},
"exe": {
"type": "keyword"
},
"execve": {
"properties": {
"a0": {
"type": "keyword"
},
"a1": {
"type": "keyword"
},
"a2": {
"type": "keyword"
},
"a3": {
"type": "keyword"
}
}
},
"exit": {
"type": "keyword"
},
"file": {
"properties": {
"inode": {
"type": "keyword"
},
"mode": {
"type": "keyword"
},
"name": {
"type": "keyword"
}
}
},
"fsgid": {
"type": "keyword"
},
"fsuid": {
"type": "keyword"
},
"gid": {
"type": "keyword"
},
"id": {
"type": "keyword"
},
"key": {
"type": "keyword"
},
"list": {
"type": "keyword"
},
"old-auid": {
"type": "keyword"
},
"old-ses": {
"type": "keyword"
},
"old_enforcing": {
"type": "keyword"
},
"old_prom": {
"type": "keyword"
},
"op": {
"type": "keyword"
},
"pid": {
"type": "keyword"
},
"ppid": {
"type": "keyword"
},
"prom": {
"type": "keyword"
},
"res": {
"type": "keyword"
},
"session": {
"type": "keyword"
},
"sgid": {
"type": "keyword"
},
"srcip": {
"type": "keyword"
},
"subj": {
"type": "keyword"
},
"success": {
"type": "keyword"
},
"suid": {
"type": "keyword"
},
"syscall": {
"type": "keyword"
},
"tty": {
"type": "keyword"
},
"type": {
"type": "keyword"
},
"uid": {
"type": "keyword"
}
}
},
"aws": {
"properties": {
"accountId": {
"type": "keyword"
},
"bytes": {
"type": "long"
},
"createdAt": {
"type": "date"
},
"dstaddr": {
"type": "ip"
},
"end": {
"type": "date"
},
"log_info": {
"properties": {
"s3bucket": {
"type": "keyword"
}
}
},
"region": {
"type": "keyword"
},
"resource": {
"properties": {
"instanceDetails": {
"properties": {
"launchTime": {
"type": "date"
},
"networkInterfaces": {
"properties": {
"privateIpAddress": {
"type": "ip"
},
"publicIp": {
"type": "ip"
}
}
}
}
}
}
},
"service": {
"properties": {
"action": {
"properties": {
"networkConnectionAction": {
"properties": {
"remoteIpDetails": {
"properties": {
"geoLocation": {
"type": "geo_point"
},
"ipAddressV4": {
"type": "ip"
}
}
}
}
}
}
},
"count": {
"type": "long"
},
"eventFirstSeen": {
"type": "date"
},
"eventLastSeen": {
"type": "date"
}
}
},
"source": {
"type": "keyword"
},
"source_ip_address": {
"type": "ip"
},
"srcaddr": {
"type": "ip"
},
"start": {
"type": "date"
},
"updatedAt": {
"type": "date"
}
}
},
"cis": {
"properties": {
"benchmark": {
"type": "keyword"
},
"error": {
"type": "long"
},
"fail": {
"type": "long"
},
"group": {
"type": "keyword"
},
"notchecked": {
"type": "long"
},
"pass": {
"type": "long"
},
"result": {
"type": "keyword"
},
"rule_title": {
"type": "keyword"
},
"score": {
"type": "long"
},
"timestamp": {
"type": "keyword"
},
"unknown": {
"type": "long"
}
}
},
"command": {
"type": "keyword"
},
"data": {
"type": "keyword"
},
"docker": {
"properties": {
"Action": {
"type": "keyword"
},
"Actor": {
"properties": {
"Attributes": {
"properties": {
"image": {
"type": "keyword"
},
"name": {
"type": "keyword"
}
}
}
}
},
"Type": {
"type": "keyword"
}
}
},
"dstip": {
"type": "keyword"
},
"dstport": {
"type": "keyword"
},
"dstuser": {
"type": "keyword"
},
"extra_data": {
"type": "keyword"
},
"gcp": {
"properties": {
"jsonPayload": {
"properties": {
"authAnswer": {
"type": "keyword"
},
"queryName": {
"type": "keyword"
},
"responseCode": {
"type": "keyword"
},
"vmInstanceId": {
"type": "keyword"
},
"vmInstanceName": {
"type": "keyword"
}
}
},
"resource": {
"properties": {
"labels": {
"properties": {
"location": {
"type": "keyword"
},
"project_id": {
"type": "keyword"
},
"source_type": {
"type": "keyword"
}
}
},
"type": {
"type": "keyword"
}
}
},
"severity": {
"type": "keyword"
}
}
},
"github": {
"properties": {
"action": {
"type": "keyword"
},
"actor": {
"type": "keyword"
},
"actor_location": {
"properties": {
"country_code": {
"type": "keyword"
}
}
},
"org": {
"type": "keyword"
},
"repo": {
"type": "keyword"
}
}
},
"hardware": {
"properties": {
"cpu_cores": {
"type": "long"
},
"cpu_mhz": {
"type": "double"
},
"cpu_name": {
"type": "keyword"
},
"ram_free": {
"type": "long"
},
"ram_total": {
"type": "long"
},
"ram_usage": {
"type": "long"
},
"serial": {
"type": "keyword"
}
}
},
"id": {
"type": "keyword"
},
"integration": {
"type": "keyword"
},
"netinfo": {
"properties": {
"iface": {
"properties": {
"adapter": {
"type": "keyword"
},
"ipv4": {
"properties": {
"address": {
"type": "keyword"
},
"broadcast": {
"type": "keyword"
},
"dhcp": {
"type": "keyword"
},
"gateway": {
"type": "keyword"
},
"metric": {
"type": "long"
},
"netmask": {
"type": "keyword"
}
}
},
"ipv6": {
"properties": {
"address": {
"type": "keyword"
},
"broadcast": {
"type": "keyword"
},
"dhcp": {
"type": "keyword"
},
"gateway": {
"type": "keyword"
},
"metric": {
"type": "long"
},
"netmask": {
"type": "keyword"
}
}
},
"mac": {
"type": "keyword"
},
"mtu": {
"type": "long"
},
"name": {
"type": "keyword"
},
"rx_bytes": {
"type": "long"
},
"rx_dropped": {
"type": "long"
},
"rx_errors": {
"type": "long"
},
"rx_packets": {
"type": "long"
},
"state": {
"type": "keyword"
},
"tx_bytes": {
"type": "long"
},
"tx_dropped": {
"type": "long"
},
"tx_errors": {
"type": "long"
},
"tx_packets": {
"type": "long"
},
"type": {
"type": "keyword"
}
}
}
}
},
"office365": {
"properties": {
"Actor": {
"properties": {
"ID": {
"type": "keyword"
}
}
},
"ClientIP": {
"type": "keyword"
},
"Operation": {
"type": "keyword"
},
"ResultStatus": {
"type": "keyword"
},
"Subscription": {
"type": "keyword"
},
"UserId": {
"type": "keyword"
}
}
},
"os": {
"properties": {
"architecture": {
"type": "keyword"
},
"build": {
"type": "keyword"
},
"codename": {
"type": "keyword"
},
"display_version": {
"type": "keyword"
},
"hostname": {
"type": "keyword"
},
"major": {
"type": "keyword"
},
"minor": {
"type": "keyword"
},
"name": {
"type": "keyword"
},
"patch": {
"type": "keyword"
},
"platform": {
"type": "keyword"
},
"release": {
"type": "keyword"
},
"release_version": {
"type": "keyword"
},
"sysname": {
"type": "keyword"
},
"version": {
"type": "keyword"
}
}
},
"oscap": {
"properties": {
"check": {
"properties": {
"description": {
"type": "text"
},
"id": {
"type": "keyword"
},
"identifiers": {
"type": "text"
},
"oval": {
"properties": {
"id": {
"type": "keyword"
}
}
},
"rationale": {
"type": "text"
},
"references": {
"type": "text"
},
"result": {
"type": "keyword"
},
"severity": {
"type": "keyword"
},
"title": {
"type": "keyword"
}
}
},
"scan": {
"properties": {
"benchmark": {
"properties": {
"id": {
"type": "keyword"
}
}
},
"content": {
"type": "keyword"
},
"id": {
"type": "keyword"
},
"profile": {
"properties": {
"id": {
"type": "keyword"
},
"title": {
"type": "keyword"
}
}
},
"return_code": {
"type": "long"
},
"score": {
"type": "double"
}
}
}
}
},
"osquery": {
"properties": {
"action": {
"type": "keyword"
},
"calendarTime": {
"type": "keyword"
},
"name": {
"type": "keyword"
},
"pack": {
"type": "keyword"
}
}
},
"port": {
"properties": {
"inode": {
"type": "long"
},
"local_ip": {
"type": "ip"
},
"local_port": {
"type": "long"
},
"pid": {
"type": "long"
},
"process": {
"type": "keyword"
},
"protocol": {
"type": "keyword"
},
"remote_ip": {
"type": "ip"
},
"remote_port": {
"type": "long"
},
"rx_queue": {
"type": "long"
},
"state": {
"type": "keyword"
},
"tx_queue": {
"type": "long"
}
}
},
"process": {
"properties": {
"args": {
"type": "keyword"
},
"cmd": {
"type": "keyword"
},
"egroup": {
"type": "keyword"
},
"euser": {
"type": "keyword"
},
"fgroup": {
"type": "keyword"
},
"name": {
"type": "keyword"
},
"nice": {
"type": "long"
},
"nlwp": {
"type": "long"
},
"pgrp": {
"type": "long"
},
"pid": {
"type": "long"
},
"ppid": {
"type": "long"
},
"priority": {
"type": "long"
},
"processor": {
"type": "long"
},
"resident": {
"type": "long"
},
"rgroup": {
"type": "keyword"
},
"ruser": {
"type": "keyword"
},
"session": {
"type": "long"
},
"sgroup": {
"type": "keyword"
},
"share": {
"type": "long"
},
"size": {
"type": "long"
},
"start_time": {
"type": "long"
},
"state": {
"type": "keyword"
},
"stime": {
"type": "long"
},
"suser": {
"type": "keyword"
},
"tgid": {
"type": "long"
},
"tty": {
"type": "long"
},
"utime": {
"type": "long"
},
"vm_size": {
"type": "long"
}
}
},
"program": {
"properties": {
"architecture": {
"type": "keyword"
},
"description": {
"type": "keyword"
},
"format": {
"type": "keyword"
},
"install_time": {
"type": "keyword"
},
"location": {
"type": "keyword"
},
"multiarch": {
"type": "keyword"
},
"name": {
"type": "keyword"
},
"priority": {
"type": "keyword"
},
"section": {
"type": "keyword"
},
"size": {
"type": "long"
},
"source": {
"type": "keyword"
},
"vendor": {
"type": "keyword"
},
"version": {
"type": "keyword"
}
}
},
"protocol": {
"type": "keyword"
},
"sca": {
"properties": {
"check": {
"properties": {
"compliance": {
"properties": {
"cis": {
"type": "keyword"
},
"cis_csc": {
"type": "keyword"
},
"hipaa": {
"type": "keyword"
},
"nist_800_53": {
"type": "keyword"
},
"pci_dss": {
"type": "keyword"
}
}
},
"description": {
"type": "keyword"
},
"directory": {
"type": "keyword"
},
"file": {
"type": "keyword"
},
"id": {
"type": "keyword"
},
"previous_result": {
"type": "keyword"
},
"process": {
"type": "keyword"
},
"rationale": {
"type": "keyword"
},
"reason": {
"type": "keyword"
},
"references": {
"type": "keyword"
},
"registry": {
"type": "keyword"
},
"remediation": {
"type": "keyword"
},
"result": {
"type": "keyword"
},
"title": {
"type": "keyword"
}
}
},
"description": {
"type": "keyword"
},
"failed": {
"type": "integer"
},
"file": {
"type": "keyword"
},
"invalid": {
"type": "keyword"
},
"name": {
"type": "keyword"
},
"passed": {
"type": "integer"
},
"policy": {
"type": "keyword"
},
"policy_id": {
"type": "keyword"
},
"scan_id": {
"type": "keyword"
},
"score": {
"type": "long"
},
"total_checks": {
"type": "keyword"
},
"type": {
"type": "keyword"
}
}
},
"srcip": {
"type": "keyword"
},
"srcport": {
"type": "keyword"
},
"srcuser": {
"type": "keyword"
},
"status": {
"type": "keyword"
},
"system_name": {
"type": "keyword"
},
"timestamp": {
"type": "date"
},
"title": {
"type": "keyword"
},
"type": {
"type": "keyword"
},
"uid": {
"type": "keyword"
},
"url": {
"type": "keyword"
},
"virustotal": {
"properties": {
"description": {
"type": "keyword"
},
"error": {
"type": "keyword"
},
"found": {
"type": "keyword"
},
"malicious": {
"type": "keyword"
},
"permalink": {
"type": "keyword"
},
"positives": {
"type": "keyword"
},
"scan_date": {
"type": "keyword"
},
"sha1": {
"type": "keyword"
},
"source": {
"properties": {
"alert_id": {
"type": "keyword"
},
"file": {
"type": "keyword"
},
"md5": {
"type": "keyword"
},
"sha1": {
"type": "keyword"
}
}
},
"total": {
"type": "keyword"
}
}
},
"vulnerability": {
"properties": {
"assigner": {
"type": "keyword"
},
"cve": {
"type": "keyword"
},
"cve_version": {
"type": "keyword"
},
"cvss": {
"properties": {
"cvss2": {
"properties": {
"base_score": {
"type": "keyword"
},
"exploitability_score": {
"type": "keyword"
},
"impact_score": {
"type": "keyword"
},
"vector": {
"properties": {
"access_complexity": {
"type": "keyword"
},
"attack_vector": {
"type": "keyword"
},
"authentication": {
"type": "keyword"
},
"availability": {
"type": "keyword"
},
"confidentiality_impact": {
"type": "keyword"
},
"integrity_impact": {
"type": "keyword"
},
"privileges_required": {
"type": "keyword"
},
"scope": {
"type": "keyword"
},
"user_interaction": {
"type": "keyword"
}
}
}
}
},
"cvss3": {
"properties": {
"base_score": {
"type": "keyword"
},
"exploitability_score": {
"type": "keyword"
},
"impact_score": {
"type": "keyword"
},
"vector": {
"properties": {
"access_complexity": {
"type": "keyword"
},
"attack_vector": {
"type": "keyword"
},
"authentication": {
"type": "keyword"
},
"availability": {
"type": "keyword"
},
"confidentiality_impact": {
"type": "keyword"
},
"integrity_impact": {
"type": "keyword"
},
"privileges_required": {
"type": "keyword"
},
"scope": {
"type": "keyword"
},
"user_interaction": {
"type": "keyword"
}
}
}
}
}
}
},
"cwe_reference": {
"type": "keyword"
},
"package": {
"properties": {
"architecture": {
"type": "keyword"
},
"condition": {
"type": "keyword"
},
"generated_cpe": {
"type": "keyword"
},
"name": {
"type": "keyword"
},
"source": {
"type": "keyword"
},
"version": {
"type": "keyword"
}
}
},
"published": {
"type": "date"
},
"rationale": {
"type": "keyword"
},
"severity": {
"type": "keyword"
},
"title": {
"type": "keyword"
},
"updated": {
"type": "date"
}
}
}
}
},
"decoder": {
"properties": {
"accumulate": {
"type": "long"
},
"fts": {
"type": "long"
},
"ftscomment": {
"type": "keyword"
},
"name": {
"type": "keyword"
},
"parent": {
"type": "keyword"
}
}
},
"full_log": {
"type": "text"
},
"host": {
"type": "keyword"
},
"id": {
"type": "keyword"
},
"input": {
"properties": {
"type": {
"type": "keyword"
}
}
},
"location": {
"type": "keyword"
},
"manager": {
"properties": {
"name": {
"type": "keyword"
}
}
},
"message": {
"type": "text"
},
"offset": {
"type": "keyword"
},
"predecoder": {
"properties": {
"hostname": {
"type": "keyword"
},
"program_name": {
"type": "keyword"
},
"timestamp": {
"type": "keyword"
}
}
},
"previous_log": {
"type": "text"
},
"previous_output": {
"type": "keyword"
},
"program_name": {
"type": "keyword"
},
"rule": {
"properties": {
"cis": {
"type": "keyword"
},
"cve": {
"type": "keyword"
},
"description": {
"type": "keyword"
},
"firedtimes": {
"type": "long"
},
"frequency": {
"type": "long"
},
"gdpr": {
"type": "keyword"
},
"gpg13": {
"type": "keyword"
},
"groups": {
"type": "keyword"
},
"hipaa": {
"type": "keyword"
},
"id": {
"type": "keyword"
},
"info": {
"type": "keyword"
},
"level": {
"type": "long"
},
"mail": {
"type": "boolean"
},
"mitre": {
"properties": {
"id": {
"type": "keyword"
},
"tactic": {
"type": "keyword"
},
"technique": {
"type": "keyword"
}
}
},
"nist_800_53": {
"type": "keyword"
},
"pci_dss": {
"type": "keyword"
},
"tsc": {
"type": "keyword"
}
}
},
"syscheck": {
"properties": {
"audit": {
"properties": {
"effective_user": {
"properties": {
"id": {
"type": "keyword"
},
"name": {
"type": "keyword"
}
}
},
"group": {
"properties": {
"id": {
"type": "keyword"
},
"name": {
"type": "keyword"
}
}
},
"login_user": {
"properties": {
"id": {
"type": "keyword"
},
"name": {
"type": "keyword"
}
}
},
"process": {
"properties": {
"id": {
"type": "keyword"
},
"name": {
"type": "keyword"
},
"ppid": {
"type": "keyword"
}
}
},
"user": {
"properties": {
"id": {
"type": "keyword"
},
"name": {
"type": "keyword"
}
}
}
}
},
"diff": {
"type": "keyword"
},
"event": {
"type": "keyword"
},
"gid_after": {
"type": "keyword"
},
"gid_before": {
"type": "keyword"
},
"gname_after": {
"type": "keyword"
},
"gname_before": {
"type": "keyword"
},
"hard_links": {
"type": "keyword"
},
"inode_after": {
"type": "keyword"
},
"inode_before": {
"type": "keyword"
},
"md5_after": {
"type": "keyword"
},
"md5_before": {
"type": "keyword"
},
"mode": {
"type": "keyword"
},
"mtime_after": {
"type": "date",
"format": "date_optional_time"
},
"mtime_before": {
"type": "date",
"format": "date_optional_time"
},
"path": {
"type": "keyword"
},
"perm_after": {
"type": "keyword"
},
"perm_before": {
"type": "keyword"
},
"sha1_after": {
"type": "keyword"
},
"sha1_before": {
"type": "keyword"
},
"sha256_after": {
"type": "keyword"
},
"sha256_before": {
"type": "keyword"
},
"size_after": {
"type": "long"
},
"size_before": {
"type": "long"
},
"tags": {
"type": "keyword"
},
"uid_after": {
"type": "keyword"
},
"uid_before": {
"type": "keyword"
},
"uname_after": {
"type": "keyword"
},
"uname_before": {
"type": "keyword"
}
}
},
"timestamp": {
"type": "date",
"format": "date_optional_time||epoch_millis"
},
"title": {
"type": "keyword"
},
"type": {
"type": "text"
}
}
},
"aliases": {}
},
"version": 1
}
Configure Logstash to Read Wazuh Data and Sent to Elasticsearch
Next, you need to configure Logstash to read Wazuh event data. Alert data or information about security alerts that Wazuh has detected/generated is stored in JSON-formatted file, /var/ossec/logs/alerts/alerts.json. You need to therefore configure Logstash to read this Wazuh alert data using the input plugin and forward them to Elasticsearch for indexing using the output plugin.
Therefore, create a Logstash configuration as follows.
vim /etc/logstash/conf.d/wazuh.confinput {
file {
id => "wazuh_alerts"
codec => "json"
start_position => "beginning"
stat_interval => "1 second"
path => "/var/ossec/logs/alerts/alerts.json"
mode => "tail"
ecs_compatibility => "disabled"
}
}
output {
elasticsearch {
hosts => "https://wazuh-elk:9200"
index => "wazuh-alerts-4.x-%{+YYYY.MM.dd}"
user => 'elastic'
password => 'iXxATQ+do7fYRDKw1XBR'
ssl => true
cacert => "/etc/logstash/elastic.ca.pem"
template => "/etc/logstash/wazuh.json"
template_name => "wazuh"
template_overwrite => true
}
}
Where on the INPUT section;
- file: Specifies that Logstash should read data from a file. You need to add logstash user to wazuh group to be able to read this file.
- id: Unique identifier for this input.
- codec: Specifies the codec used for decoding the content of the file. In this case, it’s set to “json,” indicating that the content of the file is in JSON format.
- start_position: Sets the position from where Logstash should start reading the file. In this case, it starts from the beginning of the file.
- stat_interval: Defines the interval at which Logstash should check the file for updates (every 1 second in this example).
- path: Specifies the path to the file Logstash should read.
- mode: Sets the file reading mode to “tail,” meaning Logstash will read new lines that are appended to the file.
- ecs_compatibility: Disables the Elastic Common Schema (ECS) compatibility for the input.
On the OUTPUT section;
- elasticsearch: Specifies that Logstash should send the processed data to an Elasticsearch cluster.
- hosts: Specifies the Elasticsearch cluster’s address (in this case, “https://wazuh-elk:9200“).
- index: Defines the index name pattern in Elasticsearch, including a date pattern (
%{+YYYY.MM.dd}) for daily indices. - user and password: Provide Elasticsearch authentication credentials.
- ssl: Enables SSL communication.
- cacert: Specifies the path to the CA certificate used for SSL verification.
- template: Sets the path to an index template file in Elasticsearch. The template file likely defines the mapping and settings for the Elasticsearch index.
- template_name: Specifies the name of the template in Elasticsearch.
- template_overwrite: Indicates whether to overwrite an existing template with the same name.
As you can see, we have defined the Elastic super user to use in publishing events on the Elasticsearch. You can consider creating a user with specific roles to publish events on the specified index. See more on Create Required Publishing Roles for Logstash User.
You can also consider using variables to store the user credentials instead of storing them in plain text, especially if you are using a super user such as elastic user as per the guidance here.
Similarly, copy the Elasticsearch CA cert to the specified path.
cp /etc/elasticsearch/certs/http_ca.crt /etc/logstash/elastic.ca.pemEnsure logstash owns the file;
chown logstash: /etc/logstash/elastic.ca.pemAs already mentioned, add logstash user to wazuh group to be able to read the Wazuh event data.
usermod -aG wazuh logstashTest Validity of Logstash Configuration
Next, check if the Logstash configuration is fine.
sudo -u logstash /usr/share/logstash/bin/logstash --path.settings /etc/logstash -tOr to test specific file;
sudo -u logstash /usr/share/logstash/bin/logstash --path.settings /etc/logstash -t -f /etc/logstash/conf.d/wazuh.confIf you get, Configuration OK, in the output, you are good to go.
Running Logstash
Start and enable Logstash to run on system boot;
systemctl enable --now logstashCheck status;
systemctl status logstash● logstash.service - logstash
Loaded: loaded (/lib/systemd/system/logstash.service; enabled; preset: enabled)
Active: active (running) since Sat 2024-03-02 03:11:36 EST; 4s ago
Main PID: 3784 (java)
Tasks: 26 (limit: 9475)
Memory: 405.2M
CPU: 12.185s
CGroup: /system.slice/logstash.service
└─3784 /usr/share/logstash/jdk/bin/java -XX:+HeapDumpOnOutOfMemoryError -Dlogstash.jackson.stream-read-constraints.max-number-length=10000 --add-opens=java.bas>
Mar 02 03:11:36 wazuh-elk systemd[1]: Started logstash.service - logstash.
Mar 02 03:11:36 wazuh-elk logstash[3784]: Using bundled JDK: /usr/share/logstash/jdk
Check the logs;
journalctl -f -u logstashSample logs;
Mar 02 03:19:43 wazuh-elk logstash[7949]: [2024-03-02T03:19:43,560][INFO ][logstash.outputs.elasticsearch][main] Not eligible for data streams because config contains one or more settings that are not compatible with data streams: {"template"=>"/etc/logstash/wazuh.json", "template_name"=>"wazuh", "template_overwrite"=>"true", "index"=>"wazuh-alerts-4.x-%{+YYYY.MM.dd}"}
Mar 02 03:19:43 wazuh-elk logstash[7949]: [2024-03-02T03:19:43,561][INFO ][logstash.outputs.elasticsearch][main] Data streams auto configuration (`data_stream => auto` or unset) resolved to `false`
Mar 02 03:19:43 wazuh-elk logstash[7949]: [2024-03-02T03:19:43,599][INFO ][logstash.outputs.elasticsearch][main] Using mapping template from {:path=>"/etc/logstash/wazuh.json"}
Mar 02 03:19:43 wazuh-elk logstash[7949]: [2024-03-02T03:19:43,613][INFO ][logstash.javapipeline ][main] Starting pipeline {:pipeline_id=>"main", "pipeline.workers"=>4, "pipeline.batch.size"=>125, "pipeline.batch.delay"=>50, "pipeline.max_inflight"=>500, "pipeline.sources"=>["/etc/logstash/conf.d/wazuh.conf"], :thread=>"#"}
Mar 02 03:19:43 wazuh-elk logstash[7949]: [2024-03-02T03:19:43,624][INFO ][logstash.outputs.elasticsearch][main] Installing Elasticsearch template {:name=>"wazuh"}
Mar 02 03:19:43 wazuh-elk logstash[7949]: [2024-03-02T03:19:43,954][INFO ][logstash.javapipeline ][main] Pipeline Java execution initialization time {"seconds"=>0.34}
Mar 02 03:19:43 wazuh-elk logstash[7949]: [2024-03-02T03:19:43,959][INFO ][logstash.inputs.file ][main] No sincedb_path set, generating one based on the "path" setting {:sincedb_path=>"/var/lib/logstash/plugins/inputs/file/.sincedb_b6991da130c0919d87fbe36c3e98e363", :path=>["/var/ossec/logs/alerts/alerts.json"]}
Mar 02 03:19:43 wazuh-elk logstash[7949]: [2024-03-02T03:19:43,962][INFO ][logstash.javapipeline ][main] Pipeline started {"pipeline.id"=>"main"}
Mar 02 03:19:43 wazuh-elk logstash[7949]: [2024-03-02T03:19:43,968][INFO ][filewatch.observingtail ][main][wazuh_alerts] START, creating Discoverer, Watch with file and sincedb collections
Mar 02 03:19:43 wazuh-elk logstash[7949]: [2024-03-02T03:19:43,981][INFO ][logstash.agent ] Pipelines running {:count=>1, :running_pipelines=>[:main], :non_running_pipelines=>[]}
Verify Wazuh Alerts Index Creation on Elasticsearch via Kibana
You can now access Kibana via the url https://<server-IP-or-hostname>:5601 and check status of the Wazuh alerts indices:
- Login to Kibana using your admin credentials
- Navigate to ☰ > Management > Stack Management > Data > Index Management.
You should be able to see Wazuh alerts index pattern created.
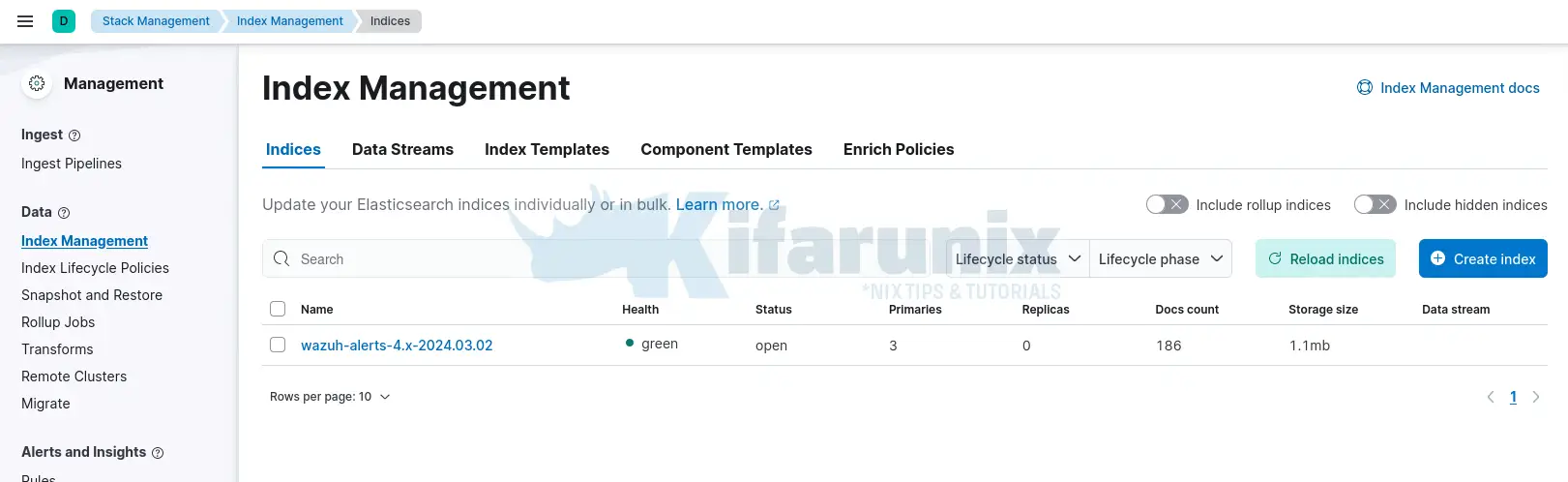
Create Wazuh Index patterns on Kibana
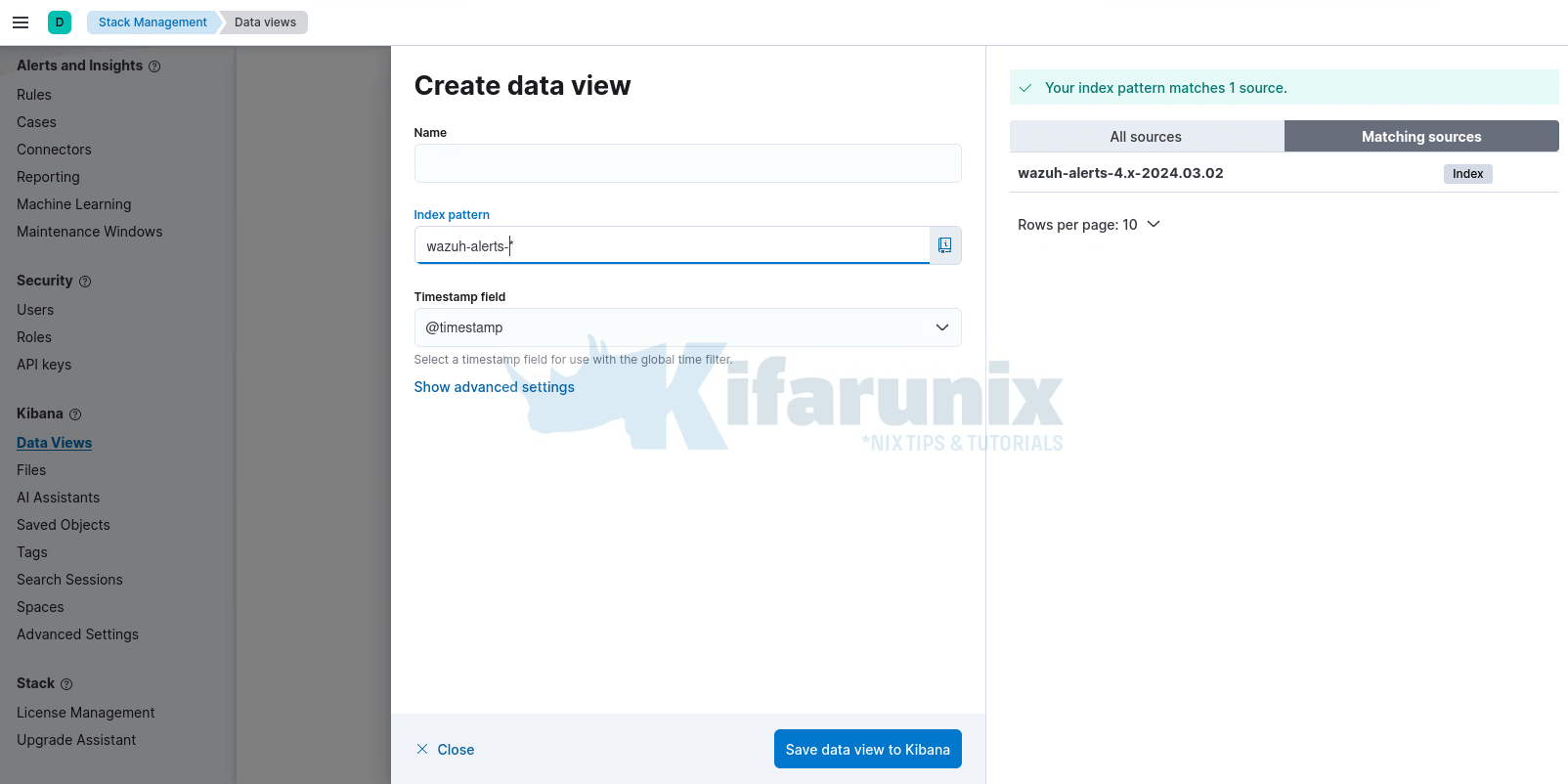
From the management interface above;
- Go to Kibana > Data Views and select Create data view.
- Enter a name [optional] for the data view and define
wazuh-alerts-*as the index pattern name. - Select timestamp in the Timestamp fields dropdown menu. Then Save data view to Kibana.
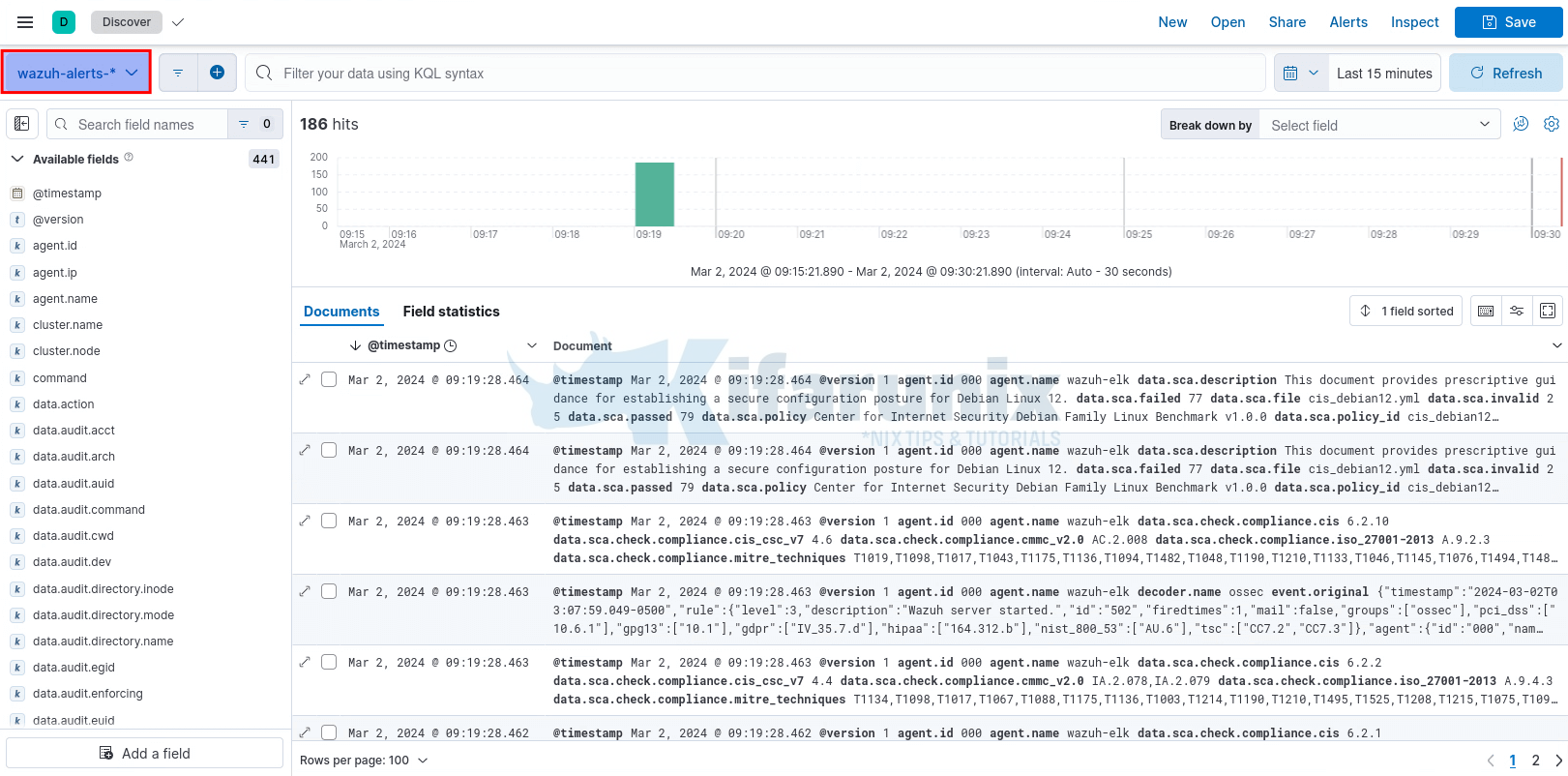
Next, verify data on the Kibana discover tab; Select ☰ > Analytics > Discover, select wazuh-alerts-* index pattern to view the data. Adjust the time range accordingly.
Import Wazuh Elastic Dashboards
Wazuh provides several dashboards for Elastic Stack for visualizing the data.
You can download the dashboards;
curl -Ls https://packages.wazuh.com/integrations/elastic/4.x-8.x/dashboards/wz-es-4.x-8.x-dashboards.ndjson -o wazuh-dashboards.ndjson
You can them import from command line;
curl -k -XPOST "http://wazuh-elk:5601/api/saved_objects/_import" \
-H "kbn-xsrf: true" \
--form [email protected] \
-u elastic
Or from Kibana saved Objects (Management > Stack management > Saved Objects and click Import, select your json file and import).
Viewing Wazuh Dashboards on Kibana
Once you import the dashboards, navigate to Analytics > Dashboards.
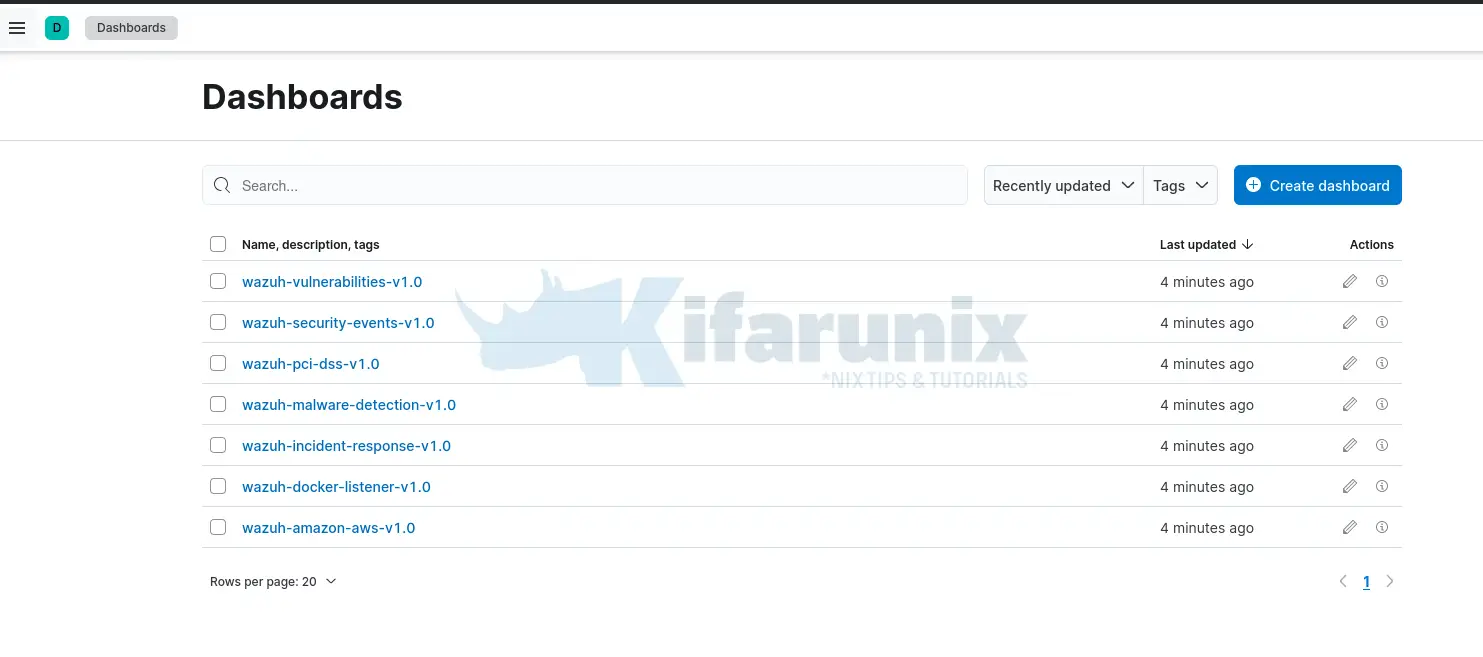
Install Wazuh Agents and Visualize the Events Data
You can now follow the guide below to learn how to install Wazuh agents.
Easy Way to Install Wazuh Agents on Ubuntu/Debian
Once the agents are intalled and enrolled into the manager, you should be able to utilize the imported dashboards to visualize the events from those systems.
Sample security events.
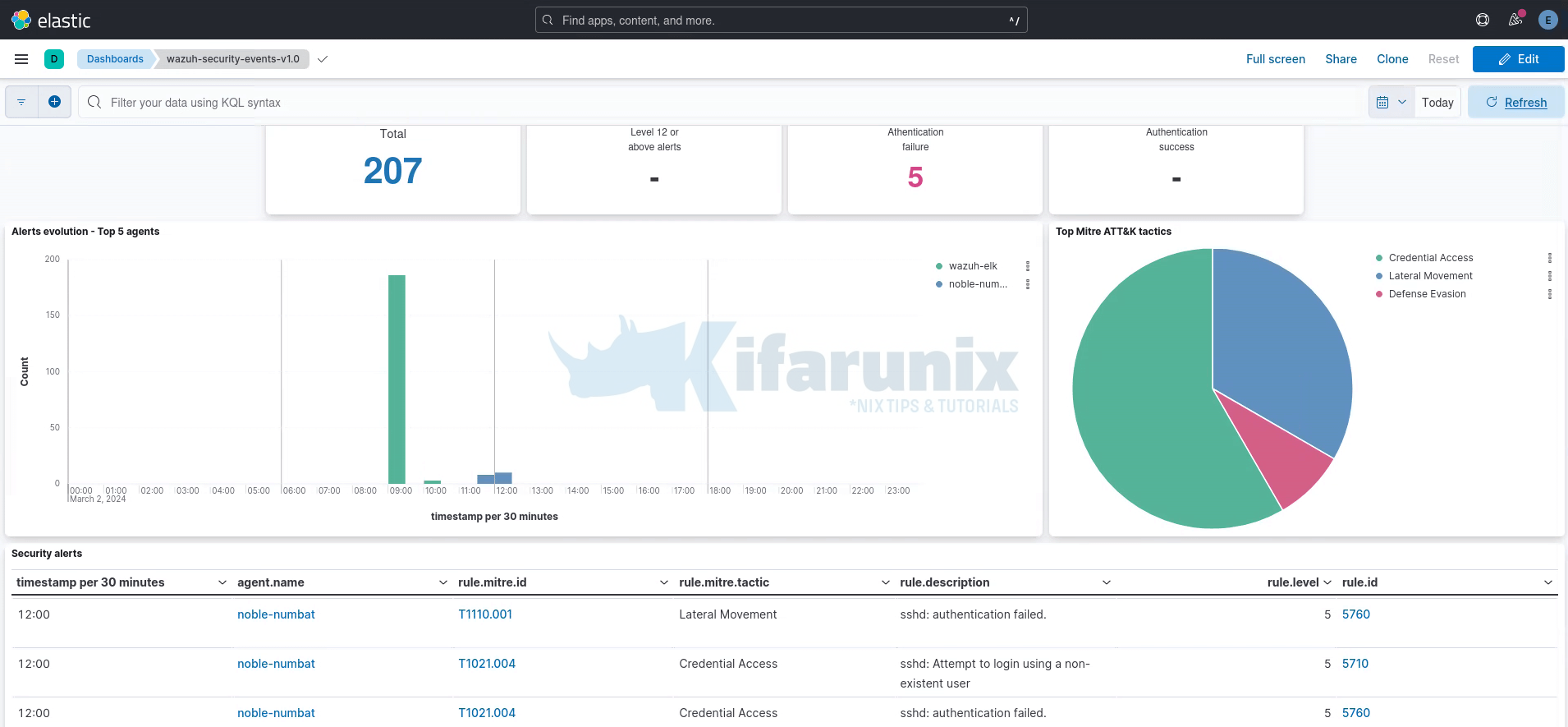
And that is it! One this you will lose with this architecture is the previous capability to manage agents from Kibana/Wazuh app dashboard.
Remember this?
Either way, you can utilize Wazuh Indexer and Wazuh dashboards for that. See the guide below;
Install Wazuh SIEM Server on Ubuntu 24.04
Reference
Other Tutorials
Configure ELK Stack Alerting with ElastAlert

