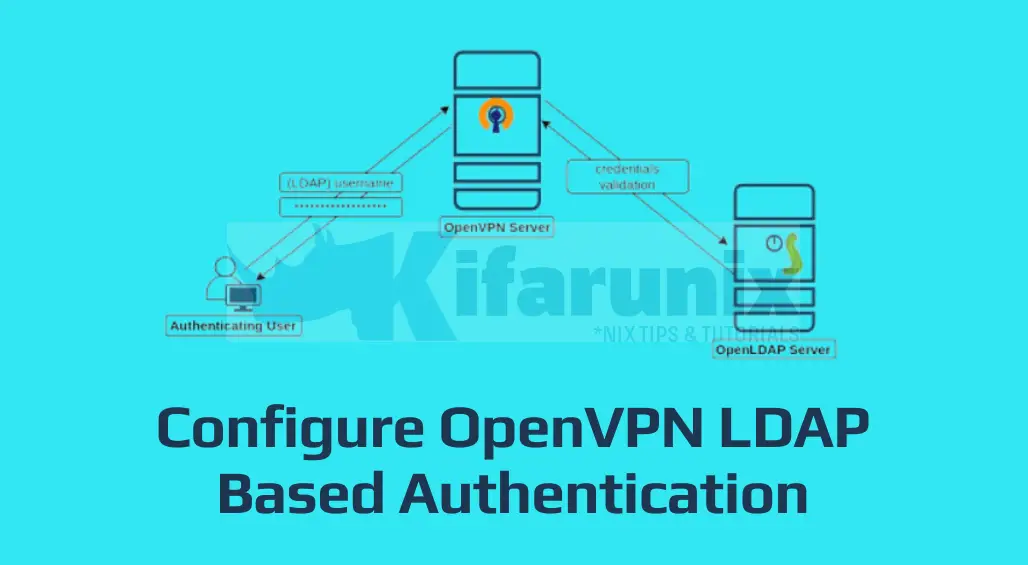
In this guide, we are going to learn how to configure OpenVPN LDAP Based Authentication. Identification and authentication of users is usually the first step in implementing access control. OpenVPN server supports multiple authentication protocols and thus can be configured to obtain connecting client information from an LDAP server, and to use that information as a basis for authenticating the client in addition to the use of the Client certificates and keys.
Also, with OpenLDAP authentication, the issue of having to generate individual OpenVPN client certificates for every client connecting can be eliminated.
Table of Contents
Configuring OpenVPN Authentication via LDAP
Install and Configure OpenLDAP Server
Learn how to install and setup OpenLDAP server by following the link below;
Install and Setup OpenLDAP Server on Linux
Install OpenVPN plugin for LDAP authentication
To configure OpenVPN authentication via LDAP, you need to install OpenVPN plugin for LDAP authentication. The plugin is called openvpn-auth-ldap and it implements username/password authentication via LDAP for OpenVPN.
On CentOS 7, you need EPEL repos to install the plugin;
yum install epel-releaseyum install openvpn-auth-ldapOn Ubuntu systems;
apt install openvpn-auth-ldapOn CentOS 8, unfortunately, the EPEL repos don’t provide this package as of this writing.
In this demo, we are running an OpenVPN server on CentOS 7 system.
After the installation of the openvpn-auth-ldap package, you should now be having the required modules under the /usr/lib64/openvpn directory.
The modules can also be found under, /usr/lib/openvpn, directory.
The package also installs OpenVPN LDAP authentication configuration file, /etc/openvpn/auth/ldap.conf.
On Ubuntu systems, you will find the sample OpenVPN LDAP auth configuration under;
/usr/share/doc/openvpn-auth-ldap/examples/auth-ldap.confConfigure OpenVPN server for LDAP Based Authentication
Once you have the necessary plugins in place, the next thing would be to configure OpenVPN server for LDAP based authentication.
Open the OpenVPN LDAP based authentication configuration file and define your OpenLDAP server specifics;
Create a backup of the configuration.
cp /etc/openvpn/auth/ldap.{conf,.old}If the directory/file doesn’t exist, simply create one;
mkdir /etc/openvpn/authOnce that is done, copy the sample configuration file;
cp /usr/share/doc/openvpn-auth-ldap/examples/auth-ldap.conf /etc/openvpn/auth/ldap.confNext, open the configuration file for editing.
vim /etc/openvpn/auth/ldap.confBelow is our sample configuration (with no commented lines) as per our OpenLDAP server setup. Make your appropriate configurations;
URL ldap://ldapmaster.kifarunix-demo.com
BindDN cn=readonly,ou=system,dc=ldapmaster,dc=kifarunix-demo,dc=com
Password P@ssW0rd
Timeout 15
TLSEnable no
FollowReferrals no
BaseDN "ou=people,dc=ldapmaster,dc=kifarunix-demo,dc=com"
SearchFilter "(uid=%u)"
RequireGroup false
In regards to group authentication, if you want to enforce a more fine grained OpenVPN access control such that only specific users authenticating via OpenLDAP can connect to OpenVPN server, you can utilize OpenLDAP group membership.
For example, in our OpenLDAP server, we have a VPN only group which contains only users that are allowed to connect to OpenVPN server;
ldapsearch -Y ExTERNAL -H ldapi:/// -b ou=groups,dc=ldapmaster,dc=kifarunix-demo,dc=com -LLL -Q "(cn=vpnonly)"dn: cn=vpnonly,ou=groups,dc=ldapmaster,dc=kifarunix-demo,dc=com
objectClass: groupOfNames
cn: vpnonly
member: uid=koromicha,ou=people,dc=ldapmaster,dc=kifarunix-demo,dc=com
member: uid=johndoe,ou=people,dc=ldapmaster,dc=kifarunix-demo,dc=com
See how to create OpenLDAP group membership by following the guide below;
How to Create OpenLDAP Member Groups
Therefore, to enable group membership authentication, set the value of the RequireGroup option to true and edit the group section such that you configuration may look like;
URL ldap://ldapmaster.kifarunix-demo.com
BindDN cn=readonly,ou=system,dc=ldapmaster,dc=kifarunix-demo,dc=com
Password P@ssW0rd
Timeout 15
TLSEnable no
FollowReferrals no
BaseDN "ou=people,dc=ldapmaster,dc=kifarunix-demo,dc=com"
SearchFilter "(uid=%u)"
RequireGroup true
BaseDN "ou=groups,dc=ldapmaster,dc=kifarunix-demo,dc=com"
SearchFilter "memberOf=cn=vpnonly,ou=groups,dc=ldapmaster,dc=kifarunix-demo,dc=com"
MemberAttribute uniqueMember
In this case, only user koromicha and johndoe can connect to OpenVPN server.
Save and exit the configuration after making your appropriate changes.
Next, configure OpenVPN server to use OpenLDAP for authentication by adding the line below to the OpenVPN server configuration file.
plugin /usr/lib64/openvpn/plugin/lib/openvpn-auth-ldap.so /etc/openvpn/auth/ldap.confYou can simply add this line to the OpenVPN server configuration file as follows;
echo "plugin /usr/lib64/openvpn/plugin/lib/openvpn-auth-ldap.so /etc/openvpn/auth/ldap.conf" >> /etc/openvpn/server/server.confBe sure to set the correct path to the module. For example, on Ubuntu 18.04/20.04, the path is /usr/lib/openvpn/openvpn-auth-ldap.so.
Hence, the line would look like;
plugin /usr/lib/openvpn/openvpn-auth-ldap.so /etc/openvpn/auth/ldap.confEnable Client Username/Password Authentication
Next, edit the client configuration file to include the auth-user-pass directive to enable username/password authentication method.
For example, this is a our sample Client configuration file based on our OpenVPN server setup.
client
tls-client
pull
dev tun
proto udp
remote 192.168.2.132 1194
resolv-retry infinite
nobind
#user nobody
#group nogroup
persist-key
persist-tun
key-direction 1
remote-cert-tls server
comp-lzo
verb 3
auth-nocache
dhcp-option DNS 8.8.8.8
dhcp-option DNS 10.8.0.1
auth SHA512
auth-user-pass
tls-auth /home/johndoe/ta-key
ca /home/johndoe/ca.crt
cert /home/johndoe/johndoe.crt
key /home/johndoe/johndoe.key
Restart OpenVPN Server service;
systemctl restart openvpn-server@serverVerify OpenVPN Client LDAP Authentication
Our configuration is now done. To verify that all is well, initiate OpenVPN connection on the client;
sudo openvpn johndoe.ovpnSat Apr 18 08:50:11 2020 OpenVPN 2.4.8 x86_64-redhat-linux-gnu [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [PKCS11] [MH/PKTINFO] [AEAD] built on Nov 1 2019
Sat Apr 18 08:50:11 2020 library versions: OpenSSL 1.1.1 FIPS 11 Sep 2018, LZO 2.08
Enter Auth Username: johndoe
Enter Auth Password: *************
...
Sat Apr 18 08:50:26 2020 /sbin/ip addr add dev tun0 10.8.0.60/24 broadcast 10.8.0.255
Sat Apr 18 08:50:26 2020 /sbin/ip route add 192.168.2.132/32 via 10.0.2.2
Sat Apr 18 08:50:26 2020 /sbin/ip route add 0.0.0.0/1 via 10.8.0.1
Sat Apr 18 08:50:26 2020 /sbin/ip route add 128.0.0.0/1 via 10.8.0.1
Sat Apr 18 08:50:26 2020 Initialization Sequence Completed
If the authentication fails;
...
Sat Apr 18 08:53:36 2020 SENT CONTROL [server]: 'PUSH_REQUEST' (status=1)
Sat Apr 18 08:53:36 2020 AUTH: Received control message: AUTH_FAILED
Sat Apr 18 08:53:36 2020 SIGTERM[soft,auth-failure] received, process exiting
On the OpenVPN Server, you will see such a line on the logs;
tail -f /var/log/openvpn/openvpn.log...
192.168.56.1:53489 [johndoe] Peer Connection Initiated with [AF_INET]192.168.56.1:53489
johndoe/192.168.56.1:53489 OPTIONS IMPORT: reading client specific options from: /etc/openvpn/ccd/johndoe
johndoe/192.168.56.1:53489 PLUGIN_CALL: POST /usr/lib64/openvpn/plugin/lib/openvpn-auth-ldap.so/PLUGIN_CLIENT_CONNECT status=0
johndoe/192.168.56.1:53489 OPTIONS IMPORT: reading client specific options from: /tmp/openvpn_cc_565148162b7cd88618c8c5e6efba7007.tmp
johndoe/192.168.56.1:53489 MULTI: Learn: 10.8.0.60 -> johndoe/192.168.56.1:53489
johndoe/192.168.56.1:53489 MULTI: primary virtual IP for johndoe/192.168.56.1:53489: 10.8.0.60
johndoe/192.168.56.1:53489 PUSH: Received control message: 'PUSH_REQUEST'
Try to connect to OpenVPN server as janedoe, who is not in the allowed vpnonly group. This will automatically fail.
sudo openvpn janedoe.ovpnSat Apr 18 10:00:05 2020 OpenVPN 2.4.8 x86_64-redhat-linux-gnu [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [PKCS11] [MH/PKTINFO] [AEAD] built on Nov 1 2019
Sat Apr 18 10:00:05 2020 library versions: OpenSSL 1.1.1 FIPS 11 Sep 2018, LZO 2.08
Enter Auth Username: janedoe
Enter Auth Password: **************
...
Sat Apr 18 10:00:19 2020 SENT CONTROL [server]: 'PUSH_REQUEST' (status=1)
Sat Apr 18 10:00:19 2020 AUTH: Received control message: AUTH_FAILED
Sat Apr 18 10:00:19 2020 SIGTERM[soft,auth-failure] received, process exiting
Great. You have successfully configured your OpenVPN clients to authenticate via OpenLDAP server.
Related Tutorials
Assign Static IP Addresses for OpenVPN Clients
Connect to OpenVPN using Network Manager on CentOS 8/Ubuntu 18.04


Hi,
Thank you very much for this topic, a great help for me to set a new VPN with ldap authentication. Just a few remarks.
The openvpn-auth-ldap package is not yet available for centOS8, but you can install the one for for the Fedora 28 with its dependances : gnustep-base-libs libobjc-8.3.1-2. It works fine.
I had a problem with the routage. I did not use the : push “redirect-gateway def1 bypass-dhcp” in my server.conf because I did not want all the traffic of the clients to go through the vpn. I push the route with : “push route IP.0/24 255.255.255.0”, mais the client could not connect to the network I had pushed, the with the other networks, he could connect. But if I was pushing the “redirect-gateway def1 bypass-dhcp”, it was working. I understood that I had to exclude the IP of my VPN server who was in the subnet I wanted to push.
This was working with : push “route serverIP 255.255.255.255 net_gateway”.
This said that my VPN server go through the local gateway of the client, not in the tunnel.
Thanks for the feedback philippe.