In this tutorial, you will learn how to install Wazuh agents on Ubuntu/Debian systems. Wazuh operates in server-client architecture. It is made up of a Wazuh server and Wazuh agents.
Table of Contents
Installing Wazuh Agents on Ubuntu/Debian
Wazuh Agent Capabilities
Wazuh agents collect data from the end-points and ships it to the Wazuh manager for processing. It is capable of;
- Log and data collection
- File integrity monitoring
- Rootkit and malware detection
- Security policy monitoring.
- Configuration assessments
- Software inventory
There are two options here
Install and Manually Register the Wazuh Agent
Wazuh agent can be install on various platforms including AIX, HP-UX, Solaris, Windows systems. However, this tutorial focuses on how to install Wazuh agents on Linux systems. We are using Ubuntu 24.04.
Install Wazuh Repository
Wazuh provides APT repositories which makes the installation of Wazuh agents easy on Ubuntu/Debian systems.
Install Repository GPG signing Key
sudo su -apt install curl gnupg2 apt-transport-https
curl -s https://packages.wazuh.com/key/GPG-KEY-WAZUH | \ gpg --dearmor > /etc/apt/trusted.gpg.d/wazuh.gpg
Add Wazuh repository:
echo "deb https://packages.wazuh.com/4.x/apt/ stable main" | tee -a /etc/apt/sources.list.d/wazuh.list
Installing Wazuh Agents
Update system package cache:
apt update
So if you need to install the Wazuh agent and later connect it to the server for manual registration, simply run the command below to install it;
apt install wazuh-agent
Manually Register Wazuh Agent on Wazuh SIEM/Manager
If you choose to install the Wazuh agent this way, then you need to add the agent to the server by running the command below (on the server where the agent is installed):
/var/ossec/bin/agent-auth -m MANAGER-IP [-A AGENT_NAME]
Before you can proceed, ensure you can connect to the Wazuh-manager registration ports 1515/TCP. Ensure that this port is open on firewall, if any is running.
Wazuh Server/Manager uses port 1515/tcp for Agent enrollment services.
Hence, confirm that you can connect to this port from the Wazuh agent server.
telnet 192.168.122.149 1515
Trying 192.168.122.149...
Connected to 192.168.122.149.
Escape character is '^]'.
^]
telnet> quit
Connection closed.
To register the agent with the automatic system hostname name just omit the [-A AGENT_NAME].
/var/ossec/bin/agent-auth -m 192.168.122.149
Sample command output;
2024/02/29 20:59:04 agent-auth: INFO: Started (pid: 3356).
2024/02/29 20:59:04 agent-auth: INFO: Requesting a key from server: 192.168.122.149
2024/02/29 20:59:04 agent-auth: INFO: No authentication password provided
2024/02/29 20:59:04 agent-auth: INFO: Using agent name as: noble-numbat
2024/02/29 20:59:04 agent-auth: INFO: Waiting for server reply
2024/02/29 20:59:04 agent-auth: INFO: Valid key received
Next, set the Wazuh server IP in the Wazuh agent configuration file, /var/ossec/etc/ossec.conf.
Simple replace MANAGER_IP with the IP address of the Wazuh server/manager;
sed -i.bak 's/MANAGER_IP/192.168.122.149/' /var/ossec/etc/ossec.conf
Start and enable the Wazuh Agent service;
systemctl enable --now wazuh-agentCheck the status;
systemctl status wazuh-agent● wazuh-agent.service - Wazuh agent
Loaded: loaded (/usr/lib/systemd/system/wazuh-agent.service; enabled; preset: enabled)
Active: active (running) since Thu 2024-02-29 21:01:28 UTC; 42s ago
Tasks: 32 (limit: 4576)
Memory: 317.2M (peak: 343.1M)
CPU: 14.761s
CGroup: /system.slice/wazuh-agent.service
├─3661 /var/ossec/bin/wazuh-execd
├─3669 /var/ossec/bin/wazuh-agentd
├─3683 /var/ossec/bin/wazuh-syscheckd
├─3693 /var/ossec/bin/wazuh-logcollector
└─3704 /var/ossec/bin/wazuh-modulesd
Feb 29 21:01:24 noble-numbat systemd[1]: Starting wazuh-agent.service - Wazuh agent...
Feb 29 21:01:24 noble-numbat env[3384]: Starting Wazuh v4.7.2...
Feb 29 21:01:24 noble-numbat env[3384]: Started wazuh-execd...
Feb 29 21:01:25 noble-numbat env[3384]: Started wazuh-agentd...
Feb 29 21:01:25 noble-numbat env[3384]: Started wazuh-syscheckd...
Feb 29 21:01:26 noble-numbat env[3384]: Started wazuh-logcollector...
Feb 29 21:01:26 noble-numbat env[3384]: Started wazuh-modulesd...
Feb 29 21:01:28 noble-numbat env[3384]: Completed.
Feb 29 21:01:28 noble-numbat systemd[1]: Started wazuh-agent.service - Wazuh agent.
Verify Wazuh Agent Connection to Wazuh Server
Verify Wazuh agent connection to the server;
tail -f /var/ossec/logs/ossec.log...
2024/02/29 21:01:29 wazuh-execd: INFO: (1314): Shutdown received. Deleting responses.
2024/02/29 21:01:29 wazuh-execd: INFO: (1225): SIGNAL [(15)-(Terminated)] Received. Exit Cleaning...
2024/02/29 21:01:30 wazuh-execd: INFO: Started (pid: 3661).
2024/02/29 21:01:30 wazuh-agentd: INFO: (1410): Reading authentication keys file.
2024/02/29 21:01:30 wazuh-agentd: INFO: Using notify time: 10 and max time to reconnect: 60
2024/02/29 21:01:30 wazuh-agentd: INFO: Version detected -> Linux |noble-numbat |6.6.0-14-generic |#14-Ubuntu SMP PREEMPT_DYNAMIC Thu Nov 30 10:27:29 UTC 2023 |x86_64 [Ubuntu|ubuntu: 24.04 (Noble Numbat)] - Wazuh v4.7.2
2024/02/29 21:01:30 wazuh-agentd: INFO: Started (pid: 3669).
2024/02/29 21:01:30 wazuh-agentd: INFO: Using AES as encryption method.
2024/02/29 21:01:30 wazuh-agentd: INFO: Trying to connect to server ([192.168.122.149]:1514/tcp).
2024/02/29 21:01:30 wazuh-agentd: INFO: (4102): Connected to the server ([192.168.122.149]:1514/tcp).
Note that Wazuh agent communicates with the server via port 1514/tcp by default. Ensure that this port is opened on the firewall and on the Wazuh server host level firewall.
Similary, check agent status on the server CLI;
/var/ossec/bin/agent_control -l
Wazuh agent_control. List of available agents:
ID: 000, Name: wazuh.kifarunix-demo.com (server), IP: 127.0.0.1, Active/Local
ID: 001, Name: noble-numbat, IP: any, Active
List of agentless devices:
Install and Automatically Register Wazuh Agent
Install and Enroll the Wazuh agent
To install and automatically register your Wazuh agent, execute the command below. Replace the Wazuh-manager IP accordingly.
WAZUH_MANAGER="192.168.122.149" apt install wazuh-agent
You can see other deployment variables on variables page.
You can also download the installation command to automatically enroll the agent right from the Wazuh manager agents dashboard.
Generate Wazuh Agent Install and Enrollment Command from Wazuh manager
Navigate to Wazuh App > Agents > Deploy new agent and follow the procedure.
New agent enrollment wizard.
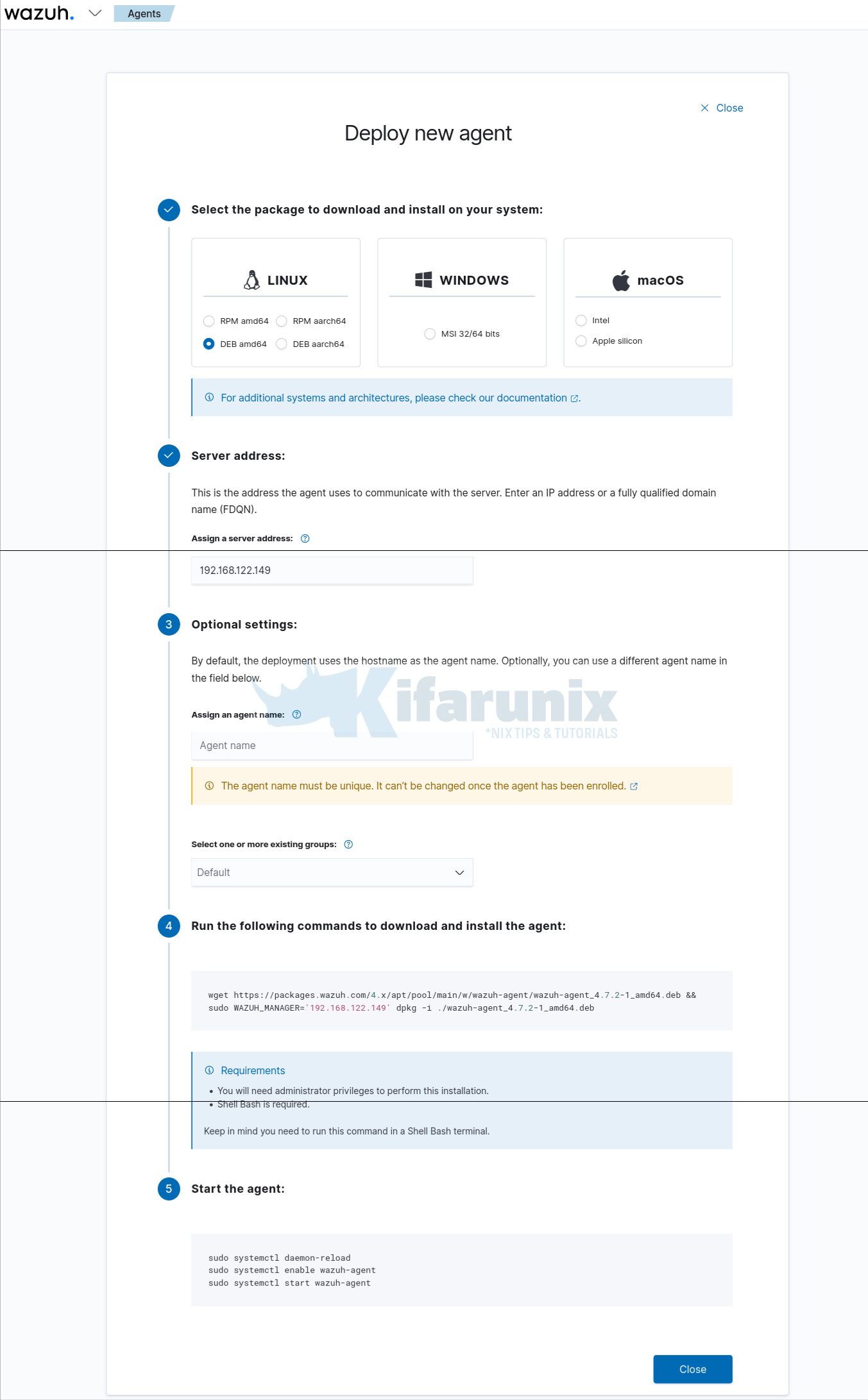
Copy the installation and enrollment command from UI and execute on the host to install and enroll Wazuh agent onto the Wazuh server.
wget https://packages.wazuh.com/4.x/apt/pool/main/w/wazuh-agent/wazuh-agent_4.7.2-1_amd64.deb && sudo WAZUH_MANAGER='192.168.122.149' dpkg -i ./wazuh-agent_4.7.2-1_amd64.debVerify Wazuh Agent Connection to Wazuh Server
Verify Wazuh Agent connection to the Wazuh server/manager.
tail -f /var/ossec/logs/ossec.logEnsure you get string Connected to the server.
Also, ensure that connection to port 1514/tcp is opened on the server.
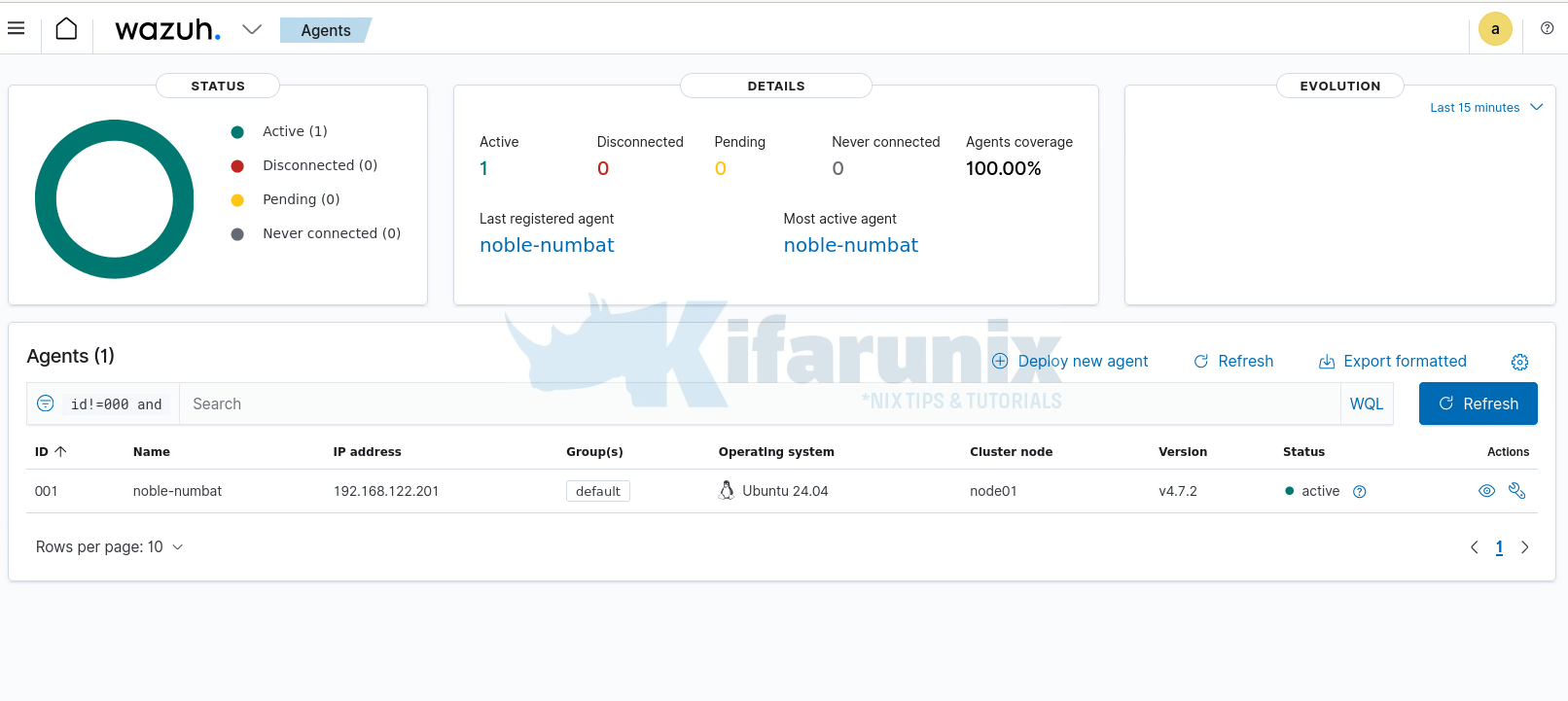
You can also list the agents on the Wazuh manager, you should see that the agent is registered but not connected.
/var/ossec/bin/agent_control -l
Wazuh agent_control. List of available agents:
ID: 000, Name: wazuh.kifarunix-demo.com (server), IP: 127.0.0.1, Active/Local
ID: 001, Name: noble-numbat, IP: any, Active
List of agentless devices:
Ensure that no hosts shares the same names.
Once the agents are installed and registered, start and enable the agents to run on system boot:
systemctl enable --now wazuh-agent.service
Verify Wazuh Agents Status from Wazuh Manager Dashboard
You can also verify from Wazuh interface. Wondering how? See our guide on integrating Wazuh Server with ELK stack.
Integrate Wazuh Manager with ELK Stack
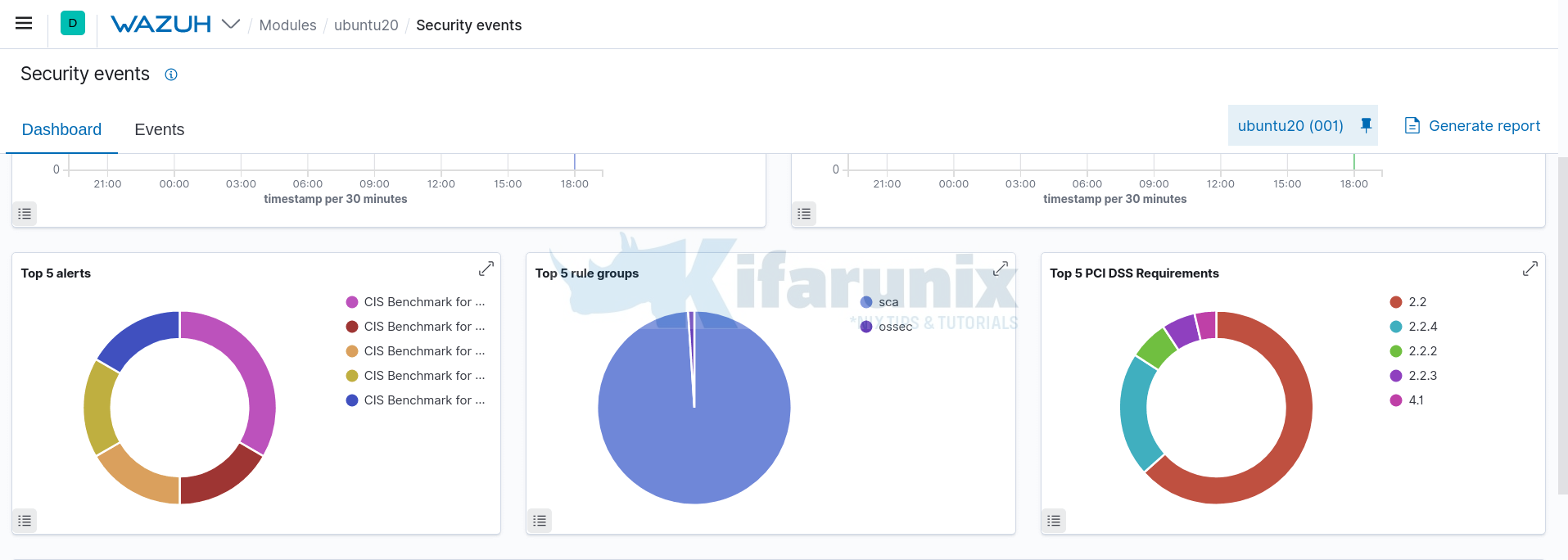
You can then be able to view the events collected from the systems.


Hello, thanks for the guide. I successfully installed the wazuh agent on recently released ubuntu 24.04, but I can’t get the vulnerability scanner or SCA to run. On the server, the Ubuntu version is not in the list of supported operating systems. I would appreciate your help on this topic.