How do you configure OpenLDAP host based authentication such that access is restricted based on host name of the computer being accessed and the user associated with the host name?
Table of Contents
Configuring OpenLDAP Host Based Authentication
Disclaimer: This guide is based on the configurations I made on my OpenLDAP server to get the host based authentication with SSSD work. Can’t guarantee it will work for you.
Before you can proceed with this guide, we assume that you already have an OpenLDAP server setup and running. You can as well follow the link below to setup OpenLDAP server on Linux.
Install and Setup OpenLDAP on Linux
Well, you might have tried adding the host attribute to user account with inetOrgPerson objectclass set but in vain. There is another LDAP objectclass called account ObjectClass which enables you to define entries representing computer accounts, including the host attribute. You can confirm if your LDAP server includes this objectclass by querying the subchema entries.
ldapsearch -H ldapi:/// -Y EXTERNAL -s base -b "cn=subschema" objectclasses
...
objectClasses: ( 0.9.2342.19200300.100.4.5 NAME 'account' SUP top STRUCTURAL MUST userid MAY ( description $ seeAlso $ localityName $ organizationName $ or ganizationalUnitName $ host ) )
...
Well, as you can see from the output above, account ObjectClass requires that when you use it to define an entry, the entry MUST have a userid attribute and optionally have the attributes; description, seeAlso, localityName, organizationName, organizationalUnitName, host.
The account objectclass is usually provided by the cosine.schema.
Read more on LDAP Schemas, objectClasses and Attributes.
Add host Attribute to LDAP users
You can only add host attribute to users with account ObjectClass set. If you try to add the host attribute to users with inetOrgPerson objectclass, you might get an error like;
ldap_modify: Object class violation (65) additional info: attribute 'host' not allowed
In such a case, simply create another LDAP user account with account ObjectClass.
vim new-user.ldif
dn: uid=june,ou=people,dc=ldapmaster,dc=kifarunix-demo,dc=com
objectClass: account
objectClass: posixAccount
objectClass: shadowAccount
uid: june
cn: june
host: june.kifarunix.com
loginShell: /bin/bash
uidNumber: 10050
gidNumber: 10050
homeDirectory: /home/june
shadowMax: 60
shadowMin: 1
shadowWarning: 7
shadowInactive: 7
shadowLastChange: 0
dn: cn=june,ou=groups,dc=ldapmaster,dc=kifarunix-demo,dc=com
objectClass: posixGroup
cn: june
gidNumber: 10050
memberUid: june
Note the highlighted lines.
Add the user to the LDAP database.
ldapadd -Y EXTERNAL -H ldapi:/// -f new-user.ldif
If you already have a user with account objectClass defined, you can simply add the host attribute. Create an LDIF file to modify the user’s attributes.
vim edit-user.ldif
dn: uid=june,ou=people,dc=ldapmaster,dc=kifarunix-demo,dc=com
changetype: modify
add: host
host: june.kifarunix-demo.comUpdate the LDAP database.
ldapadd -Y EXTERNAL -H ldapi:/// -f edit-user.ldifIf a previous user entry has no objectclass account already defined?
ldapsearch -Y EXTERNAL -H ldapi:/// -b "uid=june,ou=people,dc=ldapmaster,dc=kifarunix-demo,dc=com" -LLL -QQOr to use authenticated method;
ldapsearch -x -D "cn=admin,dc=ldapmaster,dc=kifarunix-demo,dc=com" -W -H ldapi:/// -b "uid=johndoe,ou=people,dc=ldapmaster,dc=kifarunix-demo,dc=com" -LLLdn: uid=johndoe,ou=people,dc=ldapmaster,dc=kifarunix-demo,dc=com
objectClass: inetOrgPerson
objectClass: posixAccount
objectClass: shadowAccount
uid: johndoe
cn: John
sn: Doe
loginShell: /bin/bash
uidNumber: 10000
gidNumber: 10000
homeDirectory: /home/johndoe
shadowMax: 60
shadowMin: 1
shadowWarning: 7
shadowInactive: 7
shadowLastChange: 0
Then you delete the entry and create new one that uses account object class instead of inetOrgPerson objectClass. At the same time define the host entry.
Run the command;
ldapadd -Y EXTERNAL -H ldapi:///then paste the following to remove this specific user DN;
dn: uid=johndoe,ou=people,dc=ldapmaster,dc=kifarunix-demo,dc=com
changetype: deleteThe press ENTER twice and ctrl+d to stop the command.
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
dn: uid=johndoe,ou=people,dc=ldapmaster,dc=kifarunix-demo,dc=com
changetype: delete
deleting entry "uid=johndoe,ou=people,dc=ldapmaster,dc=kifarunix-demo,dc=com"
Create new user entry;
Run the command;
ldapadd -Y EXTERNAL -H ldapi:///then paste the following to add the user with new object class and host entry.
dn: uid=johndoe,ou=people,dc=ldapmaster,dc=kifarunix-demo,dc=com
objectClass: account
objectClass: posixAccount
objectClass: shadowAccount
uid: johndoe
cn: johndoe
host: noble-numbat
loginShell: /bin/bash
uidNumber: 10000
gidNumber: 10000
homeDirectory: /home/johndoe
shadowMax: 60
shadowMin: 1
shadowWarning: 7
shadowInactive: 7
shadowLastChange: 0
The press ENTER twice and ctrl+d to stop the command.
Note that you can as well create the user using phpLDAPadmin.
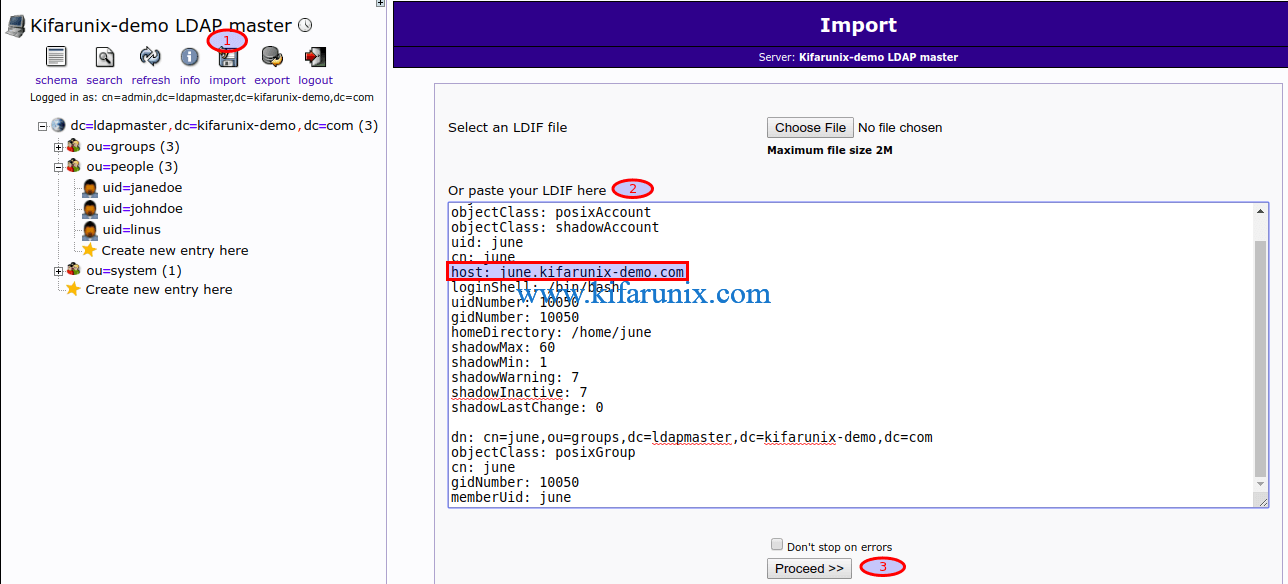
Login to your phpLDAPadmin and click on import. Paste the user attributes defined above, as shown below, and click Proceed>> to create the user.
If you did not add user password while creating the user, you can set the password by clicking the user ID on the left pane and click Add new attribute. Select Password from the attributes drop down.
Enter you password and choose the hashing technique, ssha is selected by default.
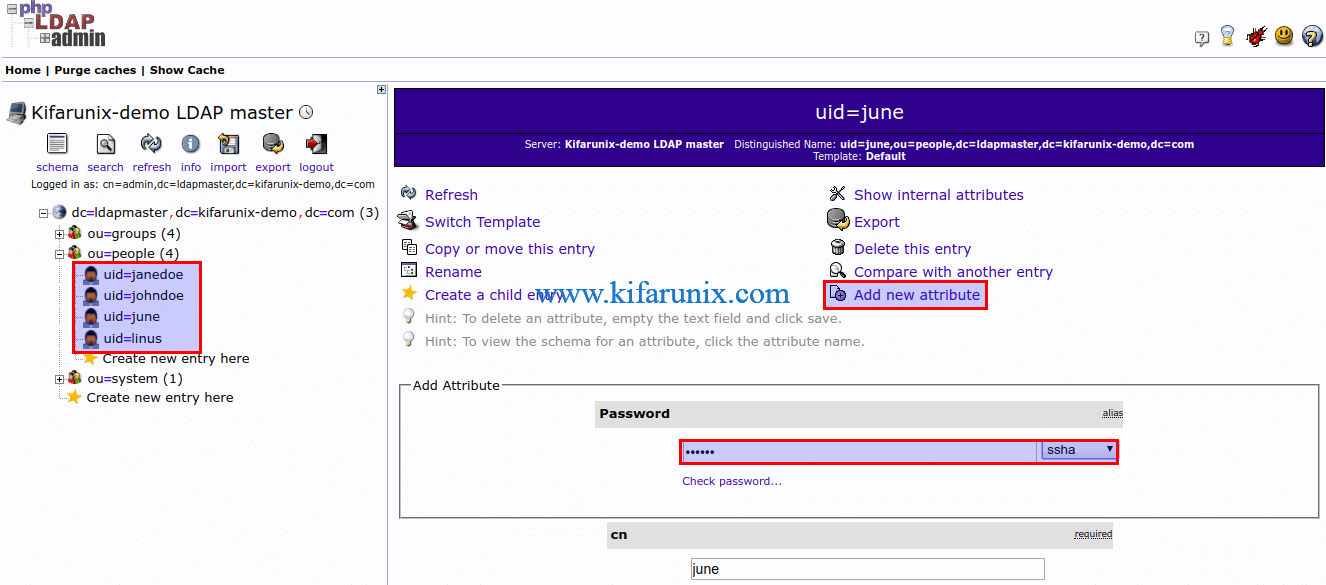
Scroll down and click Update object to save the password.
Learn how to setup phpLDAPadmin on CentOS 8 by following the link below;
Install phpLDAPadmin on CentOS 8
Restrict Access to Client Based on Host Attribute
So you now have users that are bound to specific host systems . How can you set up your LDAP clients such that specific users can only login to them?
If you are using SSSD for authentication, set the access_provider to ldap and ldap_access_filter to host=<hostname> to enable SSSD host based authentication.
See example SSSD configuration file below;
cat /etc/sssd/sssd.conf[sssd]
services = nss, pam, sudo
config_file_version = 2
domains = default
[sudo]
[nss]
[pam]
offline_credentials_expiration = 60
[domain/default]
ldap_id_use_start_tls = True
cache_credentials = True
debug_level = 10
ldap_search_base = dc=ldapmaster,dc=kifarunix-demo,dc=com
id_provider = ldap
auth_provider = ldap
chpass_provider = ldap
access_provider = ldap
ldap_uri = ldaps://ldapmaster.kifarunix-demo.com:636
ldap_default_bind_dn = cn=readonly,ou=system,dc=ldapmaster,dc=kifarunix-demo,dc=com
ldap_default_authtok = P@ssWord
ldap_tls_reqcert = demand
ldap_tls_cacert = /etc/ssl/certs/cacert.crt
ldap_tls_cacertdir = /etc/ssl/certs
ldap_search_timeout = 50
ldap_network_timeout = 60
ldap_access_order = host
ldap_access_filter = host=june.kifarunix-demo.com
This will therefore restrict access to a system whose hostname is set to june.kifarunix-demo.com to only a user that bears the attribute june.kifarunix-demo.com on LDAP server and nobody else.
Therefore, authentication can only be successful if the server hostname matches the login user host attribute.
Consult man sssd.conf, man sssd-ldap for the options used in the SSSD configuration above.
Testing Host Based Authentication
Now, before we proceed, the hostname of our test client server is;
hostnamectl Static hostname: wk01.kifarunix-demo.com
Icon name: computer-vm
Chassis: vm
Machine ID: 79625b6a4ce74de78bf9206aa0a1cc22
Boot ID: d9417032197e49f2a305e83caca14bd0
Virtualization: oracle
Operating System: Ubuntu 18.04.2 LTS
Kernel: Linux 4.18.0-15-generic
Architecture: x86-64
Now try to authenticate as june, whose host attribute defined on LDAP server and SSSD config file is, june.kifarunix-demo.com.
ssh -l june 192.168.56.160
[email protected]'s password: password
Connection to 192.168.56.160 closed by remote host.
Connection to 192.168.56.160 closed.
Now, set the hostname of the system to, june.kifarunix-demo.com.
hostnamectl set-hostname june.kifarunix-demo.com
hostnamectl
Static hostname: june.kifarunix-demo.com
Icon name: computer-vm
Chassis: vm
Machine ID: 79625b6a4ce74de78bf9206aa0a1cc22
Boot ID: d9417032197e49f2a305e83caca14bd0
Virtualization: oracle
Operating System: Ubuntu 18.04.2 LTS
Kernel: Linux 4.18.0-15-generic
Architecture: x86-64
After that, clear SSSD cache.
systemctl stop sssd;rm -rf /var/lib/sss/db/*;systemctl restart sssd
Next, try to authenticate as june;
ssh -l june 192.168.56.160
[email protected]'s password:
Welcome to Ubuntu 18.04.2 LTS (GNU/Linux 4.18.0-15-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
* Canonical Livepatch is available for installation.
- Reduce system reboots and improve kernel security. Activate at:
https://ubuntu.com/livepatch
451 packages can be updated.
224 updates are security updates.
Your Hardware Enablement Stack (HWE) is supported until April 2023.
Last login: Tue Jan 21 20:24:21 2020 from 192.168.56.1
june@june:~$ hostname
june.kifarunix-demo.com
You check how to configure SSSD for LDAP Authentication by following the link;
Configure SSSD for OpenLDAP Authentication on CentOS 8
Configure SSSD for OpenLDAP Authentication on Ubuntu 18.04
Configure SSSD for OpenLDAP Client Authentication on Debian 10/9
Configure SSSD for Multiple Authentications
SSSD can be configured to allow multiple authentications to the client based on their SSSD configuration parameters. By default, SSSD reads the main configuration file, /etc/sssd/sssd.conf and all *.conf files in the /etc/sssd/conf.d/ directory. The *.conf files in /etc/sssd/conf.d/ are read in alphabetical order. However, if similar parameters are defined on all the configuration file, SSSD will default to parameters read last.
Suppose you want to connect to an OpenLDAP client as a specific user using the host attribute while at the same time you need to connect as another user? Well, take for example, you have a group of users that needs you need to cconnect and also there is another user who can only connect using the host attribute, you would simply add an access filter like as shown below;
[sssd]
services = nss, pam, sudo
config_file_version = 2
domains = default
[sudo]
[nss]
[pam]
offline_credentials_expiration = 60
[domain/default]
ldap_id_use_start_tls = True
cache_credentials = True
debug_level = 10
ldap_search_base = dc=ldapmaster,dc=kifarunix-demo,dc=com
id_provider = ldap
auth_provider = ldap
chpass_provider = ldap
access_provider = ldap
ldap_uri = ldaps://ldapmaster.kifarunix-demo.com:636
ldap_default_bind_dn = cn=readonly,ou=system,dc=ldapmaster,dc=kifarunix-demo,dc=com
ldap_default_authtok = P@ssWord
ldap_tls_reqcert = demand
ldap_tls_cacert = /etc/ssl/certs/cacert.crt
ldap_tls_cacertdir = /etc/ssl/certs
ldap_search_timeout = 50
ldap_network_timeout = 60
ldap_access_filter = (|(memberOf=cn=admins,ou=groups,dc=ldapmaster,dc=kifarunix-demo,dc=com)(host=june.kifarunix-demo.com))This filter will allow any member of admins group or the user associated with defined host attribute, june.kifarunix-demo.com to login to the system.
For example a user whose host attribute does not match the defined filter or who is not a member of the group defined on SSSD config file wont login.
ssh -l johndoe 192.168.56.160
[email protected]'s password:
Connection to 192.168.56.160 closed by remote host.
Connection to 192.168.56.160 closed.Note that unlike the above where the hostname ought to have matched the user’s host attribute, this will allow user to login irrespective of the hostname of the target system as long as the defined host attribute matches that of a user.
Related Tutorials;
Install and Setup FreeIPA Server on CentOS 8
How to Install FreeIPA Server on Fedora 29/Fedora 28/CentOS 7

