In this guide, we are going to learn how to configure SSSD for OpenLDAP Authentication on Ubuntu 18.04. SSSD is an acronym for System Security Services Daemon. It provide access to local or remote identity and authentication resources through a common framework that can provide caching and offline support to the system. It also provides several interfaces, including NSS and PAM modules or a D-Bus interface.
Before you can proceed, ensure that your got a running OpenLDAP server. You can follow the link below to learn how to setup OpenLDAP server on CentOS 8.
Install and Setup OpenLDAP on CentOS 8
Configuring SSSD for OpenLDAP Authentication
In this demo, we are going to setup SSSD on Ubuntu 18.04 desktop.
Update your System
apt updateInstall SSSD and Required Packages
Run the command below to install SSSD onUbuntu 18.04 and other required packages.
apt install sssd libpam-sss libnss-sssConfigure SSSD on Ubuntu 18.04
Once the installation is done, proceed to configure SSSD for OpenLDAP authentication.
Create SSSD configuration file (Not created by default) with the following content;
vim /etc/sssd/sssd.conf[sssd]
services = nss, pam
config_file_version = 2
domains = default
[sudo]
[nss]
[pam]
offline_credentials_expiration = 60
[domain/default]
ldap_id_use_start_tls = True
cache_credentials = True
ldap_search_base = dc=ldapmaster,dc=kifarunix-demo,dc=com
id_provider = ldap
auth_provider = ldap
chpass_provider = ldap
access_provider = ldap
ldap_uri = ldap://ldapmaster.kifarunix-demo.com
ldap_default_bind_dn = cn=readonly,ou=system,dc=ldapmaster,dc=kifarunix-demo,dc=com
ldap_default_authtok = P@ssWOrd
ldap_tls_reqcert = demand
ldap_tls_cacert = /etc/ssl/certs/cacert.crt
ldap_tls_cacertdir = /etc/ssl/certs
ldap_search_timeout = 50
ldap_network_timeout = 60
ldap_access_order = filter
ldap_access_filter = (objectClass=posixAccount)
Replace the values of the highlighted lines above according to your OpenLDAP setup.
Read more about the configuration options on man sssd.conf.
Save the file and exit.
Install OpenLDAP Server CA Certificate
To perform authentication, SSSD requires that the communication channel be encrypted. This means that the LDAP server must be configured to run in SSL or TLS with a valid certificate trust.
Install the LDAP server CA certificate, under the file defined by the directive, ldap_tls_cacert, /etc/ssl/certs/cacert.crt.
To download the CA certificate from the LDAP server, run the command below;
openssl s_client -connect ldapmaster.kifarunix-demo.com:636 -showcerts < /dev/null | openssl x509 -text | sed -ne '/-BEGIN CERTIFICATE-/,/-END CERTIFICATE-/p'Copy the certificate part;
-----BEGIN CERTIFICATE-----
MIIDzzCCAregAwIBAgIUMJkYu/S+fQbyGjUOLsMoar6owfowDQYJKoZIhvcNAQEL
BQAwdzELMAkGA1UEBhMCS0UxDDAKBgNVBAgMA05haTEMMAoGA1UEBwwDTmFpMRcw
...
...
J4VrJYImrnvTNiDGcrXVQhKY2amBPb6g1Mwp5DiHPplvOF63F+Uzx9NFG1DhHMTq
kqkfQw96SLItvsAXpeosfYkH6uEG36svqAJ6rzxZcJzl3OTrUZnFX3OOsmFeHupC
Qxv7gjfE5jqdD6iQR0cohGLpaA==
-----END CERTIFICATE-----Paste in the file, /etc/ssl/certs/cacert.crt.
vim /etc/ssl/certs/cacert.crt-----BEGIN CERTIFICATE-----
MIIDzzCCAregAwIBAgIUMJkYu/S+fQbyGjUOLsMoar6owfowDQYJKoZIhvcNAQEL
BQAwdzELMAkGA1UEBhMCS0UxDDAKBgNVBAgMA05haTEMMAoGA1UEBwwDTmFpMRcw
...
...
J4VrJYImrnvTNiDGcrXVQhKY2amBPb6g1Mwp5DiHPplvOF63F+Uzx9NFG1DhHMTq
kqkfQw96SLItvsAXpeosfYkH6uEG36svqAJ6rzxZcJzl3OTrUZnFX3OOsmFeHupC
Qxv7gjfE5jqdD6iQR0cohGLpaA==
-----END CERTIFICATE-----Next, open the /etc/ldap/ldap.conf and replace the value of TLS_CACERT with the path to the above certificate.
vim /etc/ldap/ldap.conf...
# TLS certificates (needed for GnuTLS)
#TLS_CACERT /etc/ssl/certs/ca-certificates.crt
TLS_CACERT /etc/ssl/certs/cacert.crtSave and close the configuration file.
After that, assign the root user read/write access to /etc/sssd/.
chmod 600 -R /etc/sssdRestart SSSD service
systemctl restart sssdCheck the status of SSSD to ensure that it is running.
systemctl status sssd● sssd.service - System Security Services Daemon
Loaded: loaded (/lib/systemd/system/sssd.service; enabled; vendor preset: enabled)
Active: active (running) since Fri 2020-01-17 14:27:51 EAT; 6s ago
Main PID: 3033 (sssd)
Tasks: 4 (limit: 2315)
CGroup: /system.slice/sssd.service
├─3033 /usr/sbin/sssd -i --logger=files
├─3034 /usr/lib/x86_64-linux-gnu/sssd/sssd_be --domain default --uid 0 --gid 0 --logger=files
├─3035 /usr/lib/x86_64-linux-gnu/sssd/sssd_nss --uid 0 --gid 0 --logger=files
└─3036 /usr/lib/x86_64-linux-gnu/sssd/sssd_pam --uid 0 --gid 0 --logger=files
Jan 17 14:27:50 amos systemd[1]: Starting System Security Services Daemon...
Jan 17 14:27:51 amos sssd[3033]: Starting up
Jan 17 14:27:51 amos sssd[be[3034]: Starting up
Jan 17 14:27:51 amos sssd[3036]: Starting up
Jan 17 14:27:51 amos sssd[3035]: Starting up
Jan 17 14:27:51 amos systemd[1]: Started System Security Services Daemon.
Configure Auto-Home Directory Creation
To ensure that a user’s home directory is automatically created on first login, you need to configure the PAM modules (pam_mkhomedir.so) as shown below.
Open the /etc/pam.d/common-session configuration file and edit is ad follows;
vim /etc/pam.d/common-sessionAdd the line below just below the line, session optional pam_sss.so.
session required pam_mkhomedir.so skel=/etc/skel/ umask=0022...
# The pam_umask module will set the umask according to the system default in
# /etc/login.defs and user settings, solving the problem of different
# umask settings with different shells, display managers, remote sessions etc.
# See "man pam_umask".
session optional pam_umask.so
# and here are more per-package modules (the "Additional" block)
session required pam_unix.so
session optional pam_sss.so
session required pam_mkhomedir.so skel=/etc/skel/ umask=0022
session optional pam_systemd.so
# end of pam-auth-update config
...
Save and exit the configuration file.
Verify OpenLDAP authentication via SSH
You can now verify if you can login as an LDAP user to your Ubuntu 18.04 system via SSH.
Note that the users used here are already added to our OpenLDAP server.
ssh [email protected][email protected]'s password:
Creating directory '/home/johndoe'.
Welcome to Ubuntu 18.04.2 LTS (GNU/Linux 4.18.0-15-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
450 packages can be updated.
223 updates are security updates.
Your Hardware Enablement Stack (HWE) is supported until April 2023.
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
johndoe@amos:~$ pwd
/home/johndoe
Verify OpenLDAP authentication via GUI
In this demo, we are using the default Ubuntu 18.04 GDM display manager.
On the login interface, click Not listed to enter your OpenLDAP username and password.
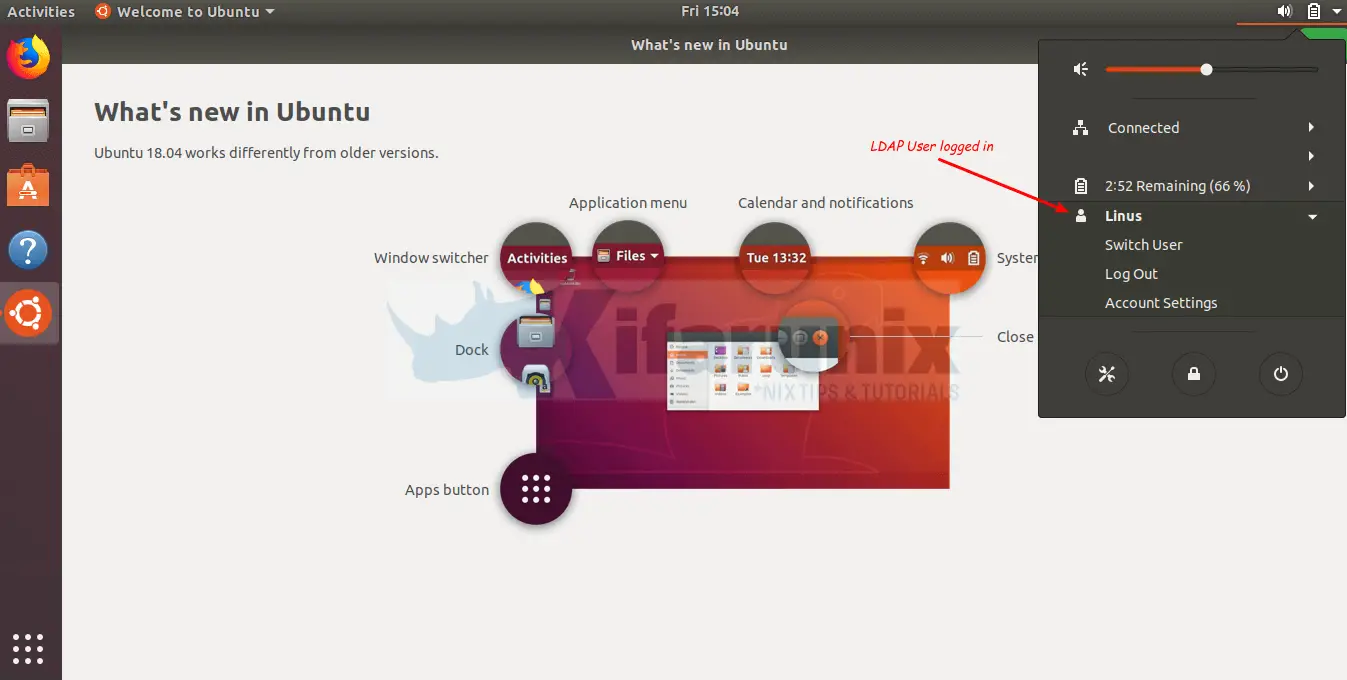
Upon successful login, your home directory will be auto-created and boom, you land on your desktop.
You can check our other tutorials on OpenLDAP by following the links below;
Install phpLDAPadmin on CentOS 8
Configure ownCloud OpenLDAP Authentication


Hi Koromicha,
Firstly thank you for this article. It was very helpful as my team coincidentally needed to do this. We have one different requirement though. We need to create our HOME directory on a central remote server using CIFS.
Means check if HOME directory exist or not, if not create it otherwise just mount it at logon using the credentials from OpenLDAP. Is that possible?
Hi Richard,
We are glad this helped your team.
However, on the CIFS one, am afraid i have not tried that yet.
Hi Koromicha,
Thanks for the article, it’s very informative. Have you tested this with Windows AD and Secure LDAP? The process will most likely be the same, but some of the attributes on Open LDAP and Widnows AD is different. I’m hoping you have some insight on this.
hello Andrew. I am sorry I haven’t test on a Windows AD yet.
I tried using sssd with Windows AD and it works : https://computingforgeeks.com/join-ubuntu-debian-to-active-directory-ad-domain/
sssd works with AD for me. See https://computingforgeeks.com/join-ubuntu-debian-to-active-directory-ad-domain/
Hi Koromicha, this is a great article and I followed each step except that I haven’t set up LDAPs on my OpenLDAP so I turned those options to False or never to use plain ldap over port 389 in my LAN. It fails me with the errors. Any suggestions?
Nov 2 23:01:59 paul-nuc2 sshd[2940]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=10.10.1.103 user=paul
Nov 2 23:01:59 paul-nuc2 sshd[2940]: pam_sss(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=10.10.1.103 user=paul
Nov 2 23:01:59 paul-nuc2 sshd[2940]: pam_sss(sshd:auth): received for user paul: 6 (Permission denied)
Nov 2 23:01:59 paul-nuc2 sshd[2940]: pam_sss(sshd:account): Access denied for user paul: 6 (Permission denied)
Nov 2 23:01:59 paul-nuc2 sshd[2940]: Failed password for paul from 10.10.1.103 port 9051 ssh2
Nov 2 23:01:59 paul-nuc2 sshd[2940]: fatal: Access denied for user paul by PAM account configuration [preauth]
Ensure the SSSD filter matches exactly as on LDAP?
What filter you are using, Peter?
Looks like tls is a must from the logs under /var/log/sssd?
Is there a way to disable it?
Thanks
You can use:
ldap_tls_reqcert = neverin sssd.conf.Hi Koromicha,
Thanks for the article; it’s gotten me very close to the end of a long rabbit hole. I can now ssh to a client with ldap users! But I cannot log into the client normally? I’m testing with VMs and if I open the vmware window and try to log in, it fails. I can ssh to the VM as an ldap user, or su to an ldap *after I ssh in with a local user*, but if I log in as a local user, I cannot su to an ldap user.
I’m guessing this is a strange pam setting I haven’t gotten right? I basically followed these exact instructions on a brand new VM.
Thanks,
John