In this tutorial, you will learn on detecting malicious files with Wazuh and VirusTotal. Wazuh is an open source security monitoring system that supports file integrity monitoring by monitoring the file system, identifying changes in content, permissions, ownership, and attributes of files that you need to keep an eye on. In addition, it natively identifies users and applications used to create or modify files.
In order to detect malicious files on the system, Wazuh can be integrated with VirusTotal, an online system that analyzes suspicious files and URLs to detect types of malware, trojans, worms.
Sycheck daemon on the Wazuh agent running on the server monitors any file added and calculate its hash. It then submits the calculated hash value to VirusTotal via VirusTotal API. VirusTotal will analyze the hash for any known malware and sents alert back to Wazuh which then alerts on the same.
Using Wazuh and VirusTotal to Detecting Malicious Files
Install and Setup Wazuh Server
Before we proceed, we assume that you already have Wazuh server setup and agents connected and active.
In this demo, we use Rocky Linux 8 as the Wazuh server. You can use below tutorials to setup Wazuh server on Rocky Linux 8.
Install and setup Wazuh Server on Rocky Linux 8
Install Wazuh Agent on Rocky Linux 8
Integrate Wazuh Manager with VirusTotal
Obtain VirusTotal API Key
Next, you need to integrate Wazuh manager with VirusTotal. For this, you need to obtain a VirusTotal API key. API key can be a public or a private one. We use a public one in this setup.
So, sign up to VirusTotal Community to get an API key.
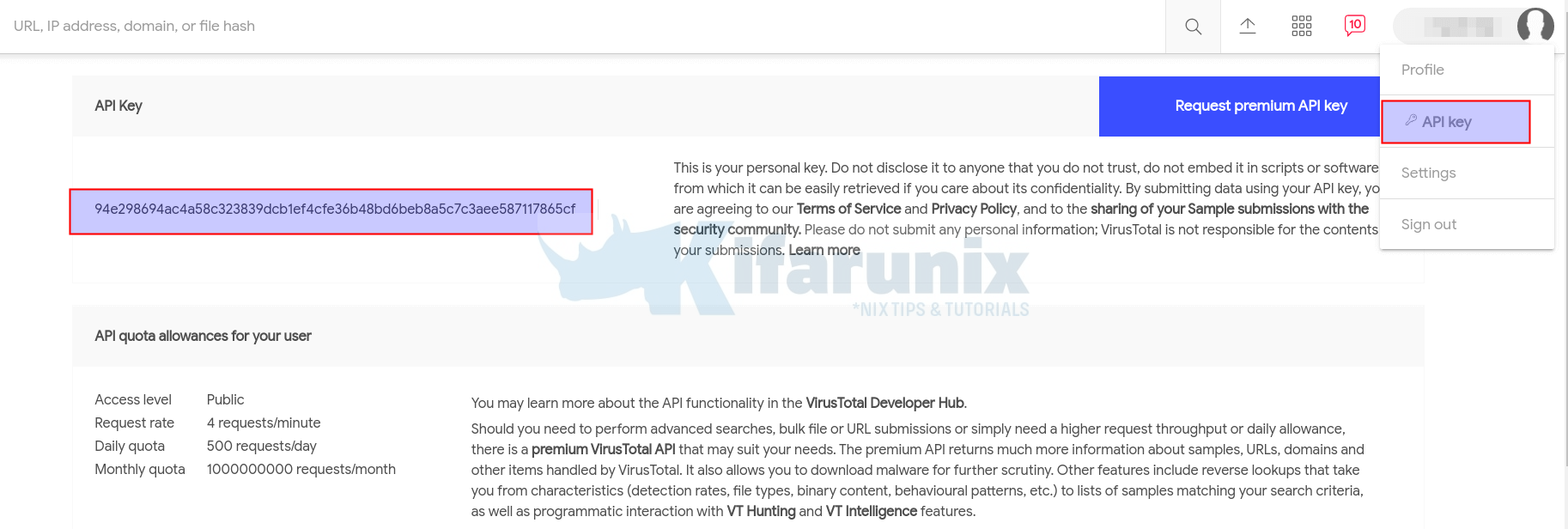
Once you have created an account and logged into VirusTotal, click on your username at the top right corner > API Key.
Integrate Wazuh Manager with VirusTotal
To integrate Wazuh manager with VirusTotal, you need to add the configuration below to /var/ossec/etc/ossec.conf file.
<integration>
<name>virustotal</name>
<api_key>API_KEY</api_key>
<group>syscheck</group>
<alert_format>json</alert_format>
</integration>Replace the API_KEY with your respective VirusTotal API Key. For example, this is how my configuration is like;
<integration>
<name>virustotal</name>
<api_key>94e298694ac4a58c323839dcb1ef4cfe36b48bd6beb8a5c7c3aee587117865cf</api_key>
<group>syscheck</group>
<alert_format>json</alert_format>
</integration>
Thus, you need to add this configuration file to ossec.conf file.
vim /var/ossec/etc/ossec.confIn our demo, we will insert the configs above just above the <!– Osquery integration –>. such that my configuration looks like;
<!-- Wazuh VirusTotal Integration -->
<integration>
<name>virustotal</name>
<api_key>94e298694ac4a58c323839dcb1ef4cfe36b48bd6beb8a5c7c3aee587117865cf</api_key>
<group>syscheck</group>
<alert_format>json</alert_format>
</integration>
<!-- Osquery integration -->
<wodle name="osquery">
<disabled>yes</disabled>
<run_daemon>yes</run_daemon>
<log_path>/var/log/osquery/osqueryd.results.log</log_path>
<config_path>/etc/osquery/osquery.conf</config_path>
<add_labels>yes</add_labels>
</wodle>
Once you have updated the configuration file, restart Wazuh manager service;
systemctl restart wazuh-managerEnable Wazuh VirusTotal Module
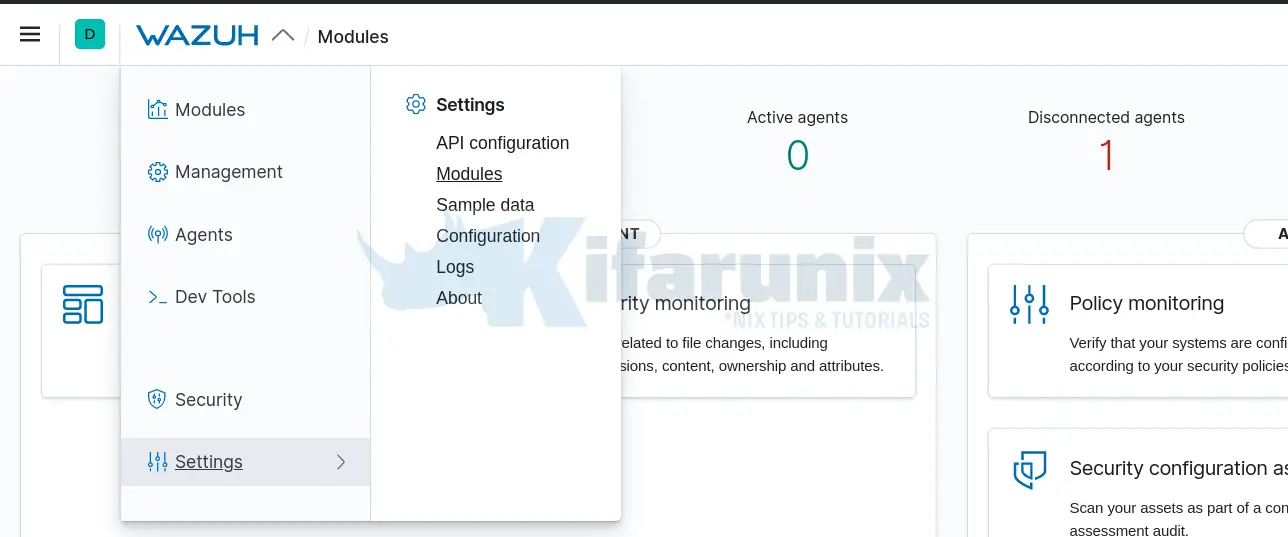
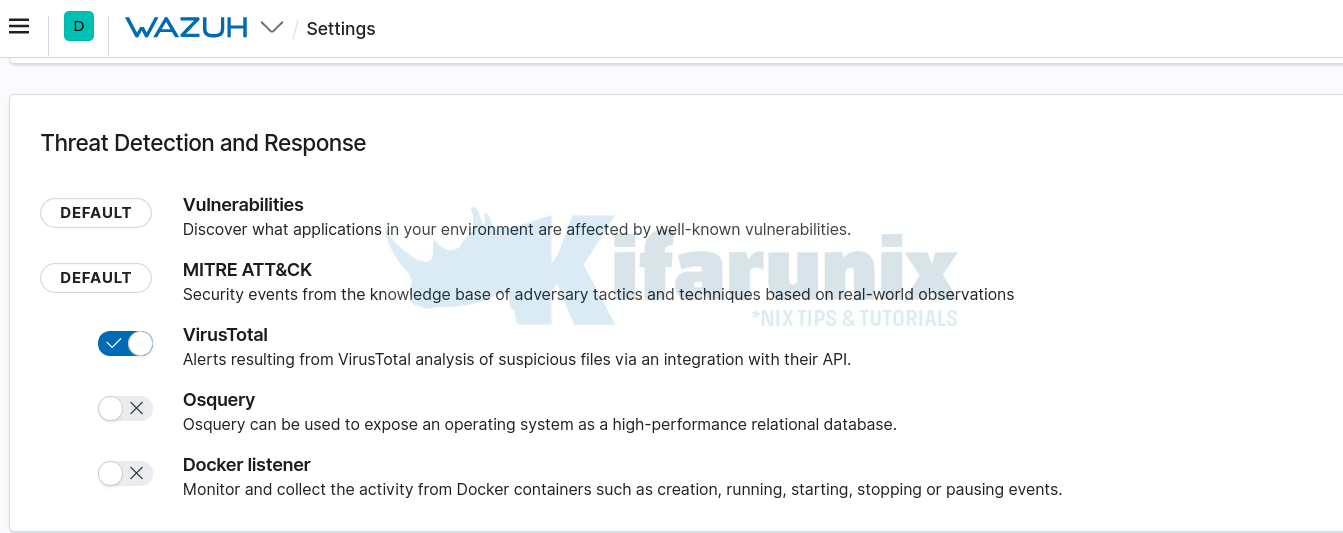
Wazuh VirusTotal module is usually disabled by default. To enable the module, navigate to Kibana Web interface > Wazuh App > Wazuh Settings > Modules.
Scroll down to Threat Detection and Response section and toggle VirusTotal button to enable it.
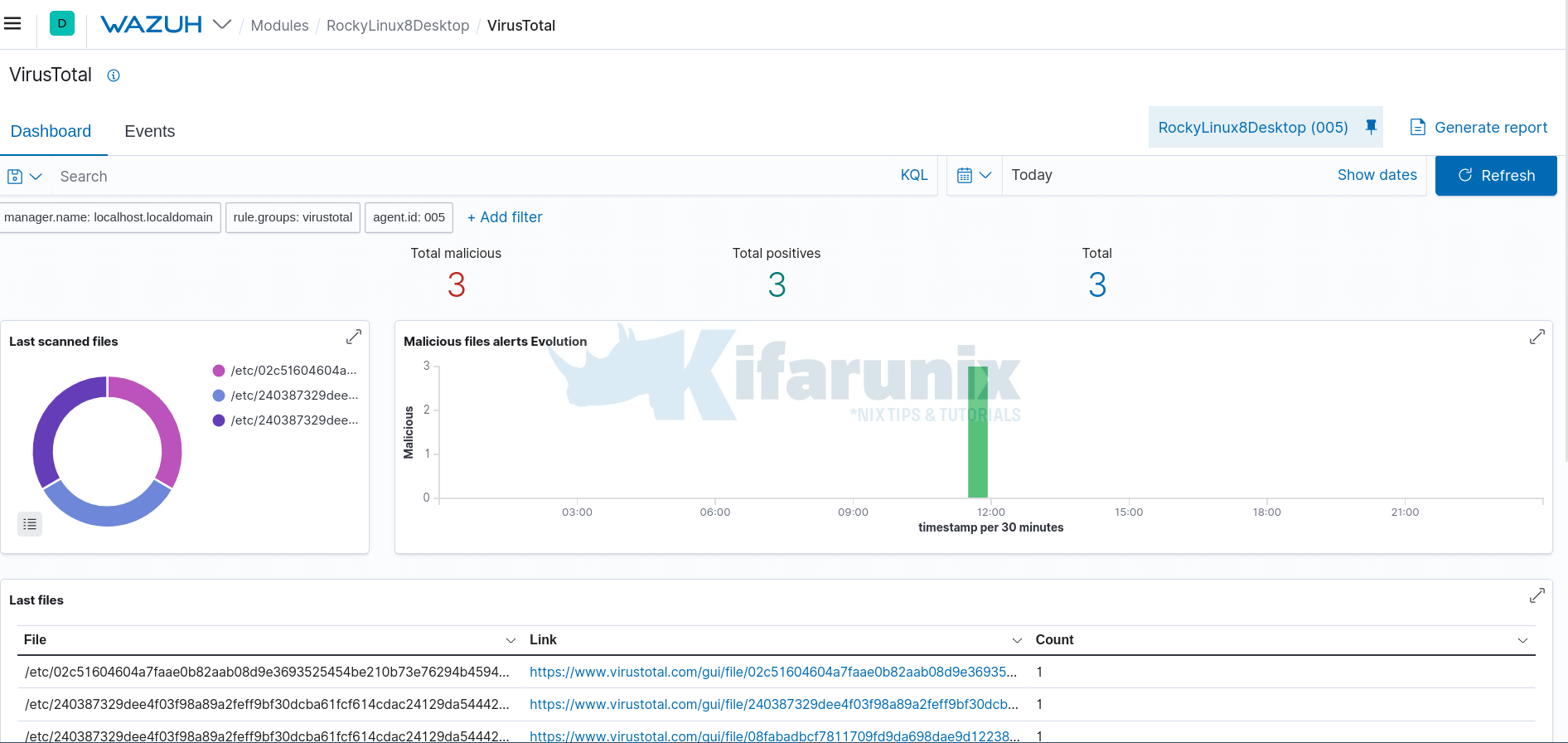
Once you have enabled, you should now be able to access VirusTotal dashboard under Wazuh > Modules > Threat Detection and Response > VirusTotal.
For now, since we don’t already have any events, the dashboard is empty.
Demonstrating how Wazuh monitors the directories for Malicious Files
By default, Wazuh agent monitors a number of directories as defined on the Agents ossec.conf file as defined under the <!-- File integrity monitoring --> section.
To effectively demonstrate this, we are gonna place a malicious file under the /etc directory and see what kind of events we get on the Wazuh dashboard.
NOTE: This is done on an isolated temporary test system. Do not place malicious files on your systems!!!! We cannot be held responsible on what malicious files may do to your system.
So as already mentioned that we are using a test system, we have downloaded some sample malware files from InQuest/malware-samples github repository to /etc directory of the Wazuh agent;
ls -1 /etc/[0-9]*/etc/02c51604604a7faae0b82aab08d9e3693525454be210b73e76294b4594762c78
/etc/240387329dee4f03f98a89a2feff9bf30dcba61fcf614cdac24129da54442762
/etc/240387329dee4f03f98a89a2feff9bf30dcba61fcf614cdac24129da54442762.zipNote that we have also adjusted the Wazuh agent syscheck scan frequency from 12 hours to a min, just for demo purposes.
...
<!-- Frequency that syscheck is executed default every 12 hours -->
<frequency>60</frequency>
...For any changes made to ossec.conf, you need to restart the agent.
Verify Malware Detection Events on Wazuh Manager
Once the file is placed on the Wazuh agent system, you should be able to get events on the Wazuh manager dashboard.
Hence navigate Wazuh > Modules > Threat Detection and Response > VirusTotal.
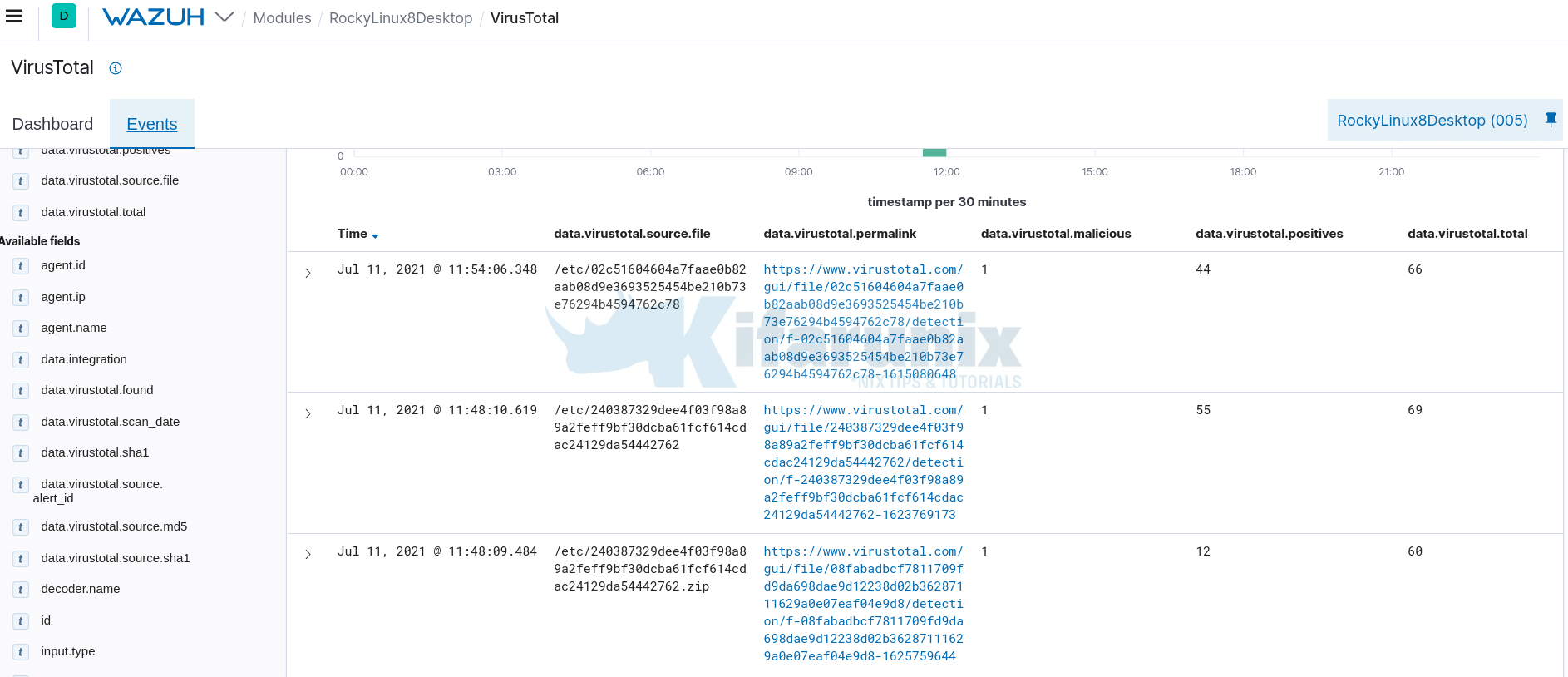
You can click Events to see the related events.
You can click the VirusTotal links to learn more about the files.
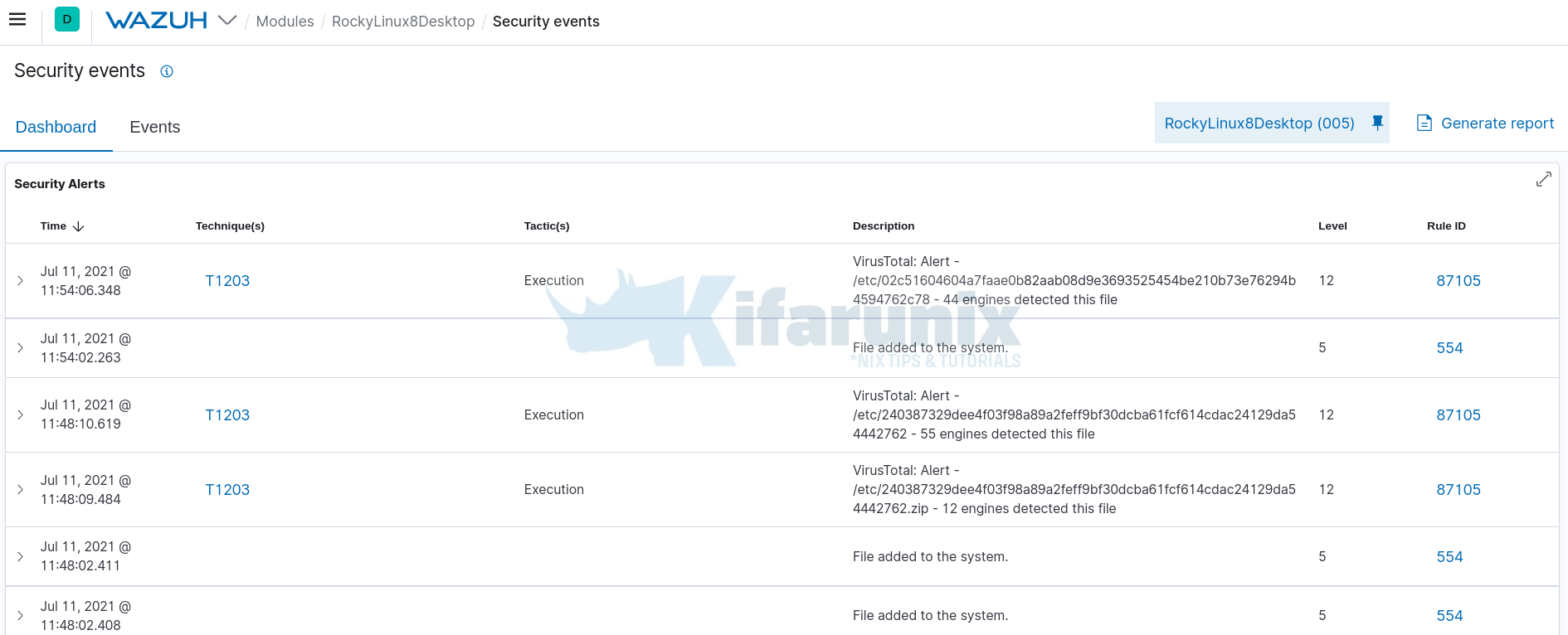
Also, if you check on Security Events, you should be able to see alerts related to files added to the system.
And that is all on our guide on how to integrate Wazuh with VirusTotal for detecting malicious files.