In this tutorial, you will learn how to install OpenLDAP Server on Ubuntu 24.04. OpenLDAP Software is an open source implementation of the Lightweight Directory Access Protocol (LDAP), which is a lightweight client-server protocol for accessing directory services, specifically X. 500-based directory services.
Table of Contents
Installing OpenLDAP Server on Ubuntu 24.04
Run System Update
Before you begin, ensure your system package cache is up-to-date.
apt updateInstall OpenLDAP Server
The default Ubuntu 24.04 repositories provides the latest release version of OpenLDAP. As of this writing, OpenLDAP 2.6.7 is the current stable release, as per the release page.
apt-cache policy slapdslapd:
Installed: (none)
Candidate: 2.6.7+dfsg-1~exp1ubuntu1
Version table:
2.6.7+dfsg-1~exp1ubuntu1 500
500 http://archive.ubuntu.com/ubuntu noble/main amd64 Packages
Hence, you can install OpenLDAP on Ubuntu 24.04 using the command below;
sudo apt install slapd ldapscriptsDuring the installation, you will be prompted to set the OpenLDAP administrative password.
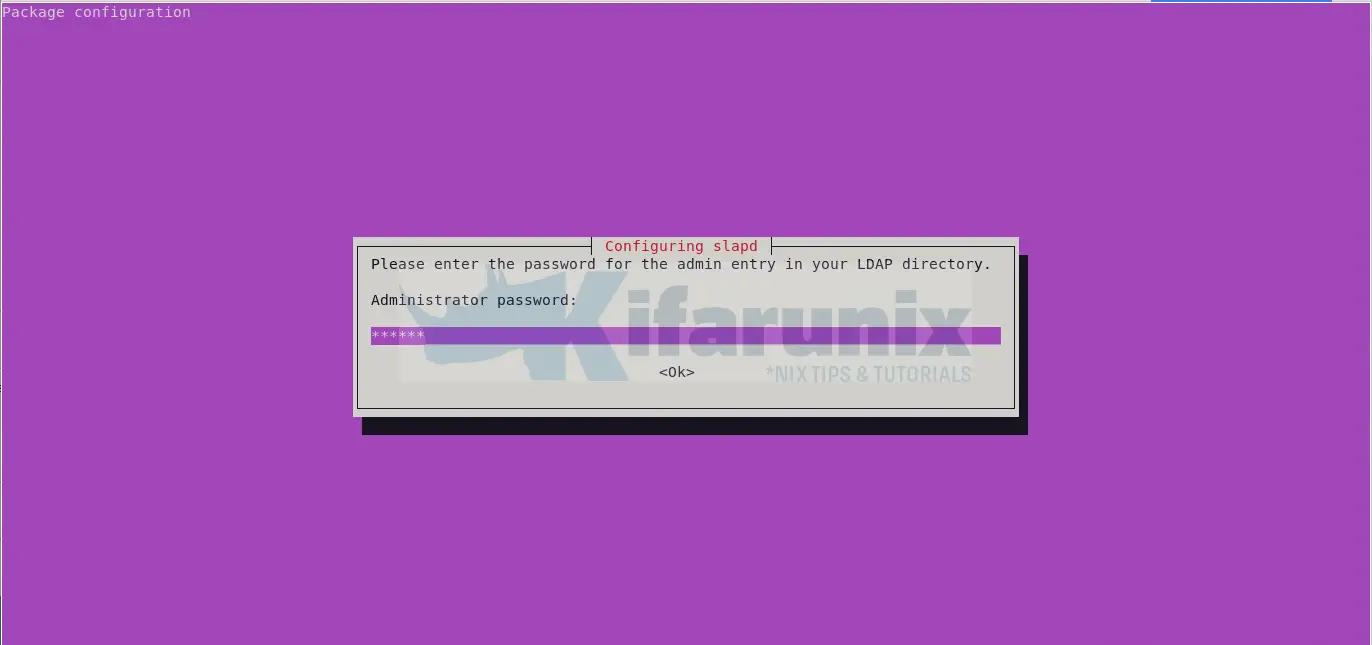
Configure OpenLDAP on Ubuntu 24.04
View LDAP Database Settings
You can check the default OpenLDAP database settings using the slapcat command.
slapcatdn: dc=nodomain
objectClass: top
objectClass: dcObject
objectClass: organization
o: nodomain
dc: nodomain
structuralObjectClass: organization
entryUUID: fa7581ea-6787-103e-9c50-bf1e7fcd254f
creatorsName: cn=admin,dc=nodomain
createTimestamp: 20240224174335Z
entryCSN: 20240224174335.131130Z#000000#000#000000
modifiersName: cn=admin,dc=nodomain
modifyTimestamp: 20240224174335Z
Based on the SLAPD database configuration output above,
- The Base DN is set to
dn: dc=nodomain. - The Organization name is set to
o: nodomain. - The LDAP admin Base DN entry is set to
cn=admin,dc=nodomain.
Update OpenLDAP Database
Based on your organization setup, you need to update the OpenLDAP database.
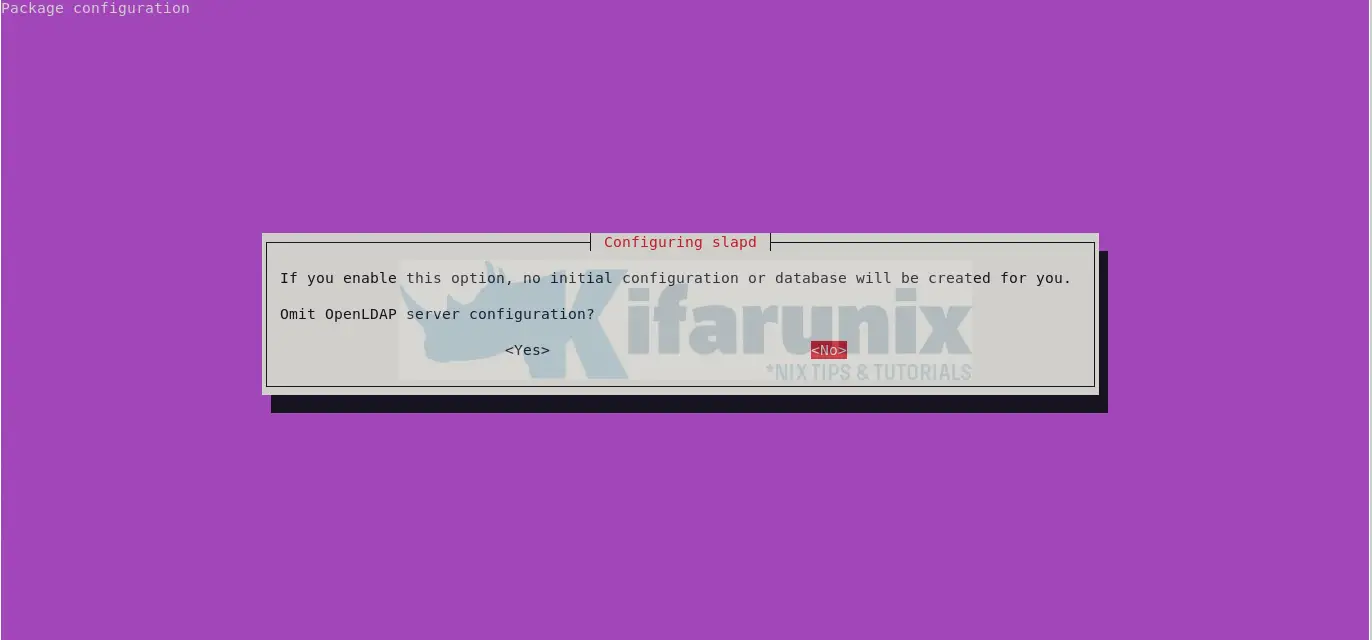
Thus, you need to reconfigure slapd package as shown below and follow through the prompts.
dpkg-reconfigure slapdWhen the command runs, you are prompted on whether to omit OpenLDAP server configuration. Select No to have the configuration created for you.
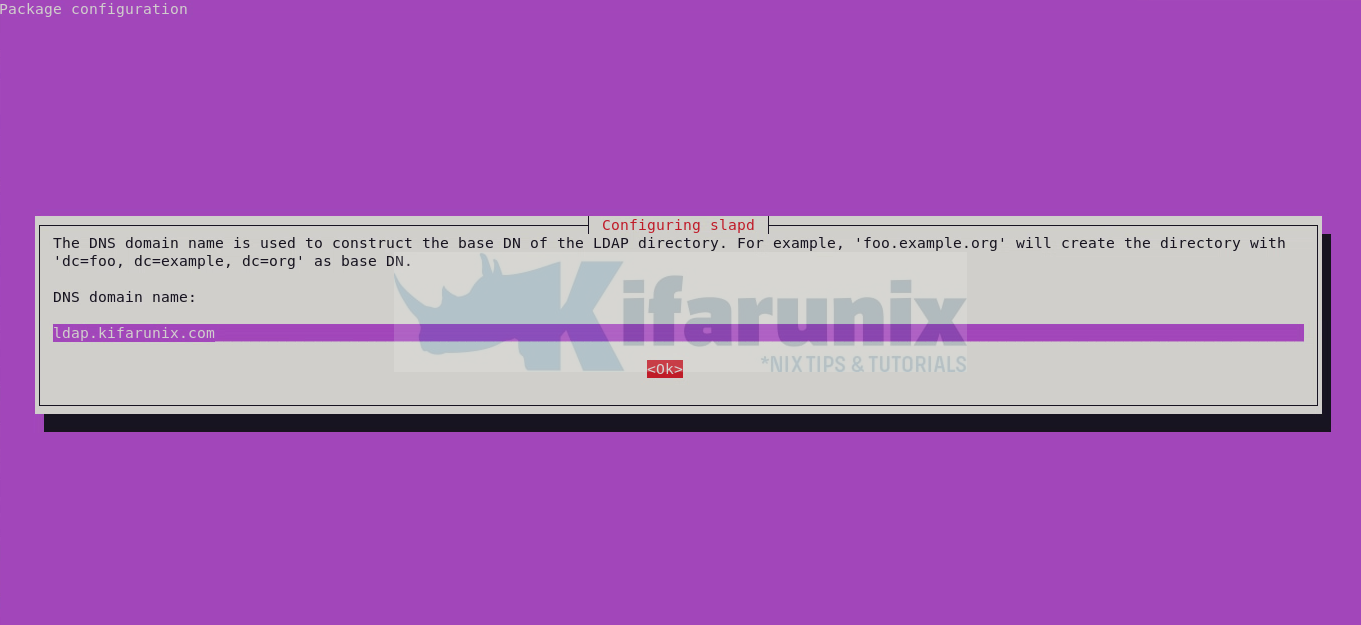
Update the DNS domain name for constructing the base DN of the LDAP directory.
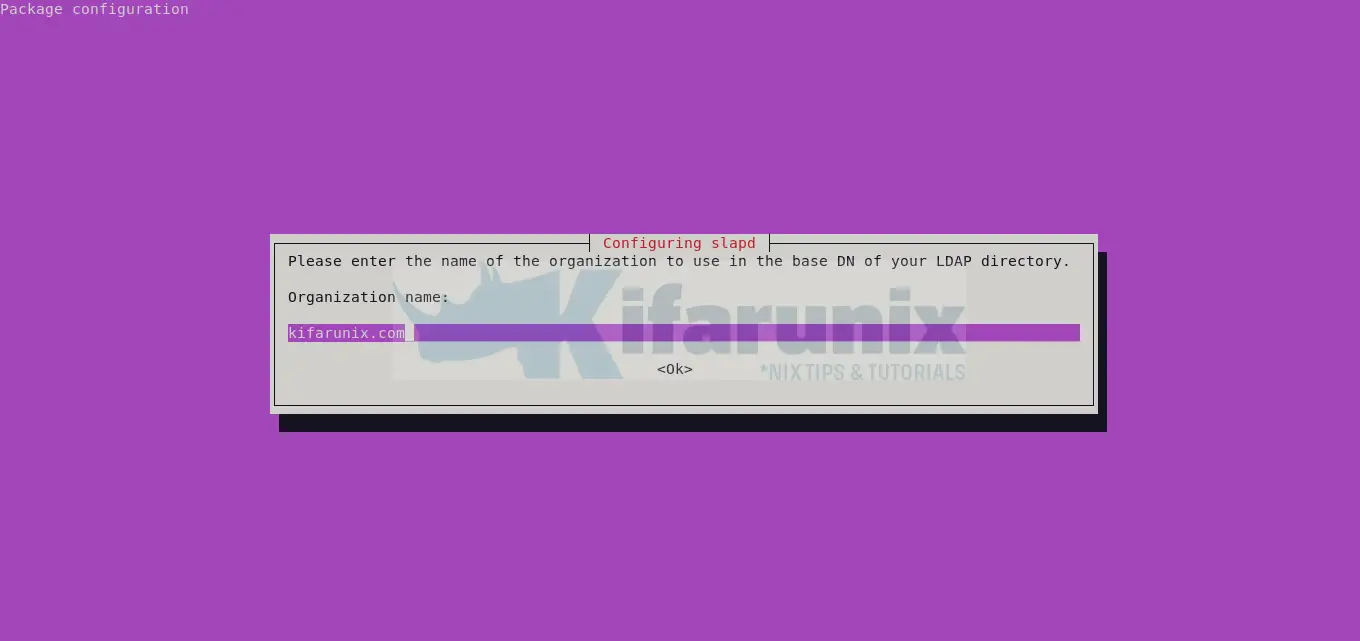
Define the name of your Organization for use in the base DN.
Reset the OpenLDAP administrator password.
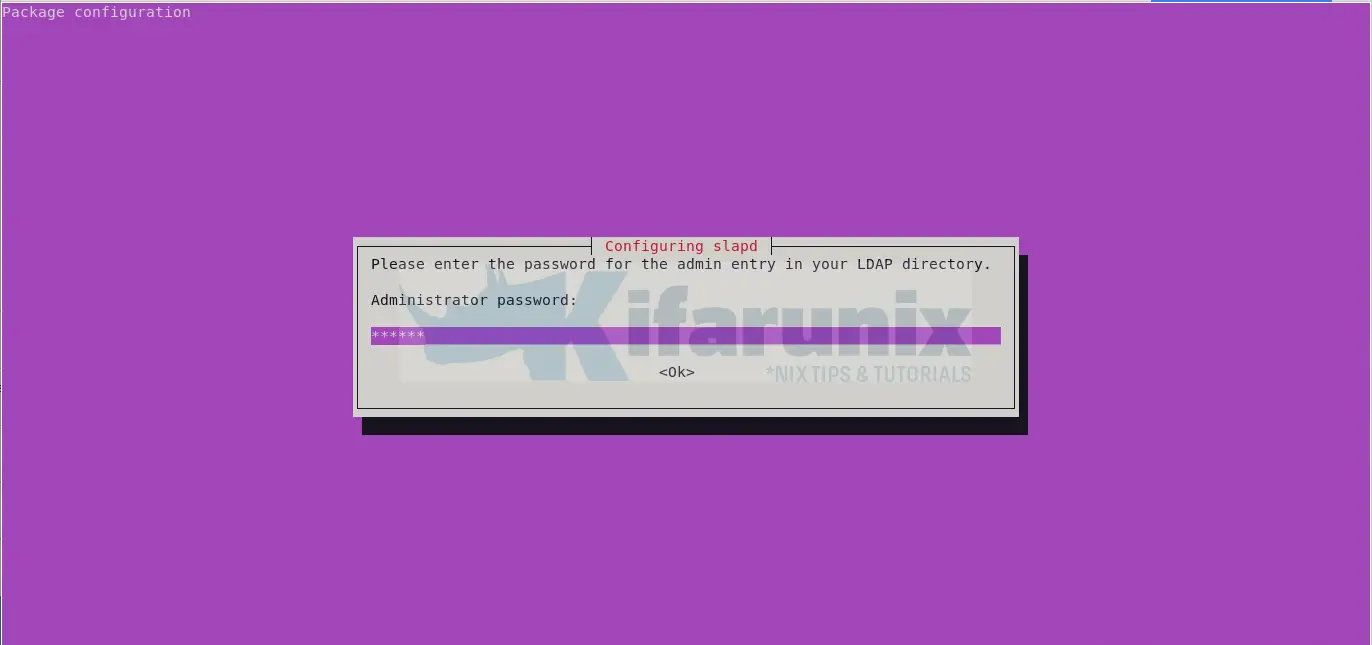
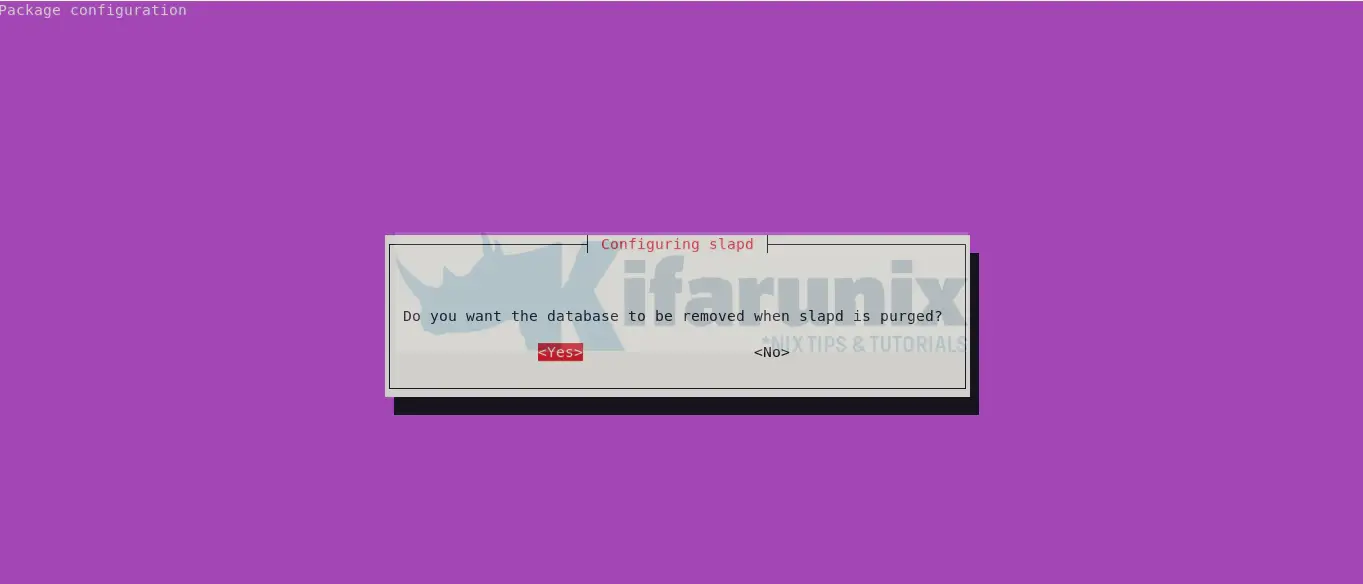
Choose whether to remove the OpenLDAP database whenever you purge the OpenLDAP package, slapd.
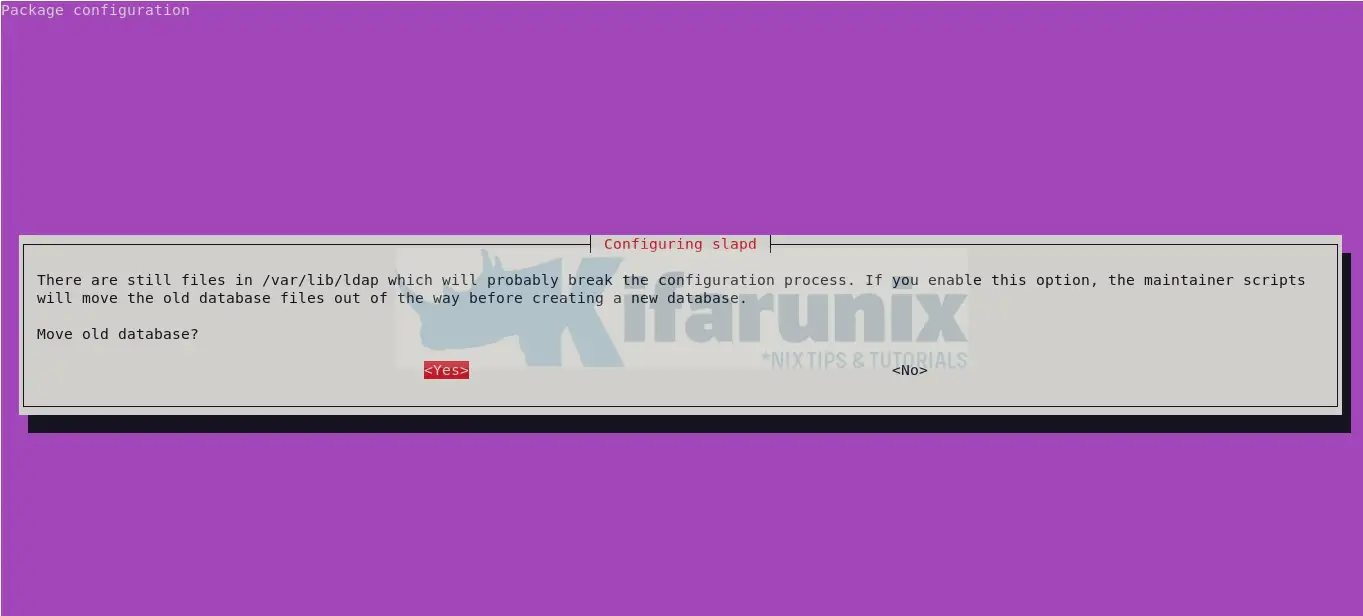
Remove old OpenLDAP database configuration files to finalize the reconfiguration. The old database is stored on /var/backups.
Check the OpenLDAP database again after reconfiguration.
slapcatdn: dc=ldap,dc=kifarunix,dc=com
objectClass: top
objectClass: dcObject
objectClass: organization
o: kifarunix.com
dc: ldap
structuralObjectClass: organization
entryUUID: 35f90bca-678c-103e-86f7-25bd8e4e56dc
creatorsName: cn=admin,dc=ldap,dc=kifarunix,dc=com
createTimestamp: 20240224181352Z
entryCSN: 20240224181352.965664Z#000000#000#000000
modifiersName: cn=admin,dc=ldap,dc=kifarunix,dc=com
modifyTimestamp: 20240224181352Z
You can also check LDAP Base DN using the ldapsearch command as shown below;
ldapsearch -H ldapi:/// -x -LLL -s base -b "" namingContextsdn:
namingContexts: dc=ldap,dc=kifarunix,dc=com
To view the RootDN, run the command below
ldapsearch -H ldapi:/// -Y EXTERNAL -b "cn=config" "(olcRootDN=*)"sample output;
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
# extended LDIF
#
# LDAPv3
# base with scope subtree
# filter: (olcRootDN=*)
# requesting: ALL
#
# {0}config, config
dn: olcDatabase={0}config,cn=config
objectClass: olcDatabaseConfig
olcDatabase: {0}config
olcAccess: {0}to * by dn.exact=gidNumber=0+uidNumber=0,cn=peercred,cn=external
,cn=auth manage by * break
olcRootDN: cn=admin,cn=config
# {1}mdb, config
dn: olcDatabase={1}mdb,cn=config
objectClass: olcDatabaseConfig
objectClass: olcMdbConfig
olcDatabase: {1}mdb
olcDbDirectory: /var/lib/ldap
olcSuffix: dc=ldap,dc=kifarunix,dc=com
olcAccess: {0}to attrs=userPassword by self write by anonymous auth by * none
olcAccess: {1}to attrs=shadowLastChange by self write by * read
olcAccess: {2}to * by * read
olcLastMod: TRUE
olcRootDN: cn=admin,dc=ldap,dc=kifarunix,dc=com
olcRootPW: {SSHA}+fuCaVAvF5wkhXdzsQzGyj9/YWu+kVRB
olcDbCheckpoint: 512 30
olcDbIndex: objectClass eq
olcDbIndex: cn,uid eq
olcDbIndex: uidNumber,gidNumber eq
olcDbIndex: member,memberUid eq
olcDbMaxSize: 1073741824
# search result
search: 2
result: 0 Success
# numResponses: 3
# numEntries: 2
To test the connection to LDAP server, use the ldapwhoami command as shown below.
ldapwhoami -H ldapi:/// -xanonymousThe expected output is anonymous if the connection to LDAP server is fine since the test is run without logging in to LDAP server.
To search for all the DNs based on the Base DN;
ldapsearch -H ldapi:/// -x -LLL -b dc=ldap,dc=kifarunix,dc=com dndn: dc=ldap,dc=kifarunix,dc=comConfigure OpenLDAP with SSL/TLS
In this guide, we are going to use self signed certificates. You can as well use commercial SSL/TLS certificates from your trusted CA if you have them.
To configure OpeLDAP server with SSL/TLS certificate, you need a CA certificate, server certificate and server certificate key file.
Generate SSL/TLS Certificate Files
Create a directory to store the certificates.
mkdir -p /etc/ssl/openldap/{private,certs,newcerts}Once you have created the directories above, open the /usr/lib/ssl/openssl.cnf configuration file and set the directory for storing SSL/TLS certificates and keys under the [ CA_default ] section. It is set to /usr
vim /usr/lib/ssl/openssl.cnf...
####################################################################
[ CA_default ]
#dir = ./demoCA # Where everything is kept
dir = /etc/ssl/openldap
certs = $dir/certs # Where the issued certs are kept
crl_dir = $dir/crl # Where the issued crl are kept
database = $dir/index.txt # database index file.
#unique_subject = no # Set to 'no' to allow creation of
# several certs with same subject.
new_certs_dir = $dir/newcerts # default place for new certs.
...
You also need some files for tracking the signed certificates.
echo "1001" > /etc/ssl/openldap/serialtouch /etc/ssl/openldap/index.txtCreate a CA Key file by running the command below. When prompted, enter the passphrase.
openssl genrsa -aes256 \
-out /etc/ssl/openldap/private/cakey.pem \
4096
To remove the passphrase from the CA key;
openssl rsa \
-in /etc/ssl/openldap/private/cakey.pem \
-out /etc/ssl/openldap/private/cakey.pem
Create the CA certificate. Be sure to set the common to match your server FQDN.
openssl req -new -x509 \
-days 3650 \
-key /etc/ssl/openldap/private/cakey.pem \
-out /etc/ssl/openldap/certs/cacert.pem
You can also simplify the process using the -subj option to specify the information. The subject information typically includes details like country, state, locality, organization, organizational unit, common name, and email address. Here’s an example command with the -subj option added:
openssl req -new -x509 \
-days 3650 \
-key /etc/ssl/openldap/private/cakey.pem \
-out /etc/ssl/openldap/certs/cacert.pem \
-subj "/C=US/ST=California/L=SanFrancisco/O=Kifarunix Inc/OU=IT Infrastructure/CN=ldap.kifarunix.com/[email protected]"
You can also use wildcard SSL cert to match your various domain names;
openssl req -new -x509 \
-days 3650 \
-key /etc/ssl/openldap/private/cakey.pem \
-out /etc/ssl/openldap/certs/cacert.pem \
-subj "/C=US/ST=California/L=SanFrancisco/O=Kifarunix Inc/OU=IT Infrastructure/CN=ldap.kifarunix.com/[email protected]" \
-addext "subjectAltName = DNS:*.kifarunix.com,DNS:kifarunix.com"
Also specify the extensions in the openssl.cnf configuration.
vim /usr/lib/ssl/openssl.cnf####################################################################
[ req ]
default_bits = 2048
default_keyfile = privkey.pem
distinguished_name = req_distinguished_name
attributes = req_attributes
x509_extensions = v3_ca # The extensions to add to the self signed cert
# Passwords for private keys if not present they will be prompted for
# input_password = secret
# output_password = secret
# This sets a mask for permitted string types. There are several options.
# default: PrintableString, T61String, BMPString.
# pkix : PrintableString, BMPString (PKIX recommendation before 2004)
# utf8only: only UTF8Strings (PKIX recommendation after 2004).
# nombstr : PrintableString, T61String (no BMPStrings or UTF8Strings).
# MASK:XXXX a literal mask value.
# WARNING: ancient versions of Netscape crash on BMPStrings or UTF8Strings.
string_mask = utf8only
req_extensions = v3_req # The extensions to add to a certificate request
We define the extensions to add to a certificate request under the section v3_req.
[ v3_req ]
# Extensions to add to a certificate request
basicConstraints = CA:FALSE
keyUsage = nonRepudiation, digitalSignature, keyEncipherment
subjectAltName = @alt_names
[alt_names]
DNS.1 = *.kifarunix.com
DNS.2 = kifarunix.com
Next generate LDAP server key;
openssl genrsa -aes256 -out /etc/ssl/openldap/private/ldapserver-key.key 4096Remove assigned key passphrase.
openssl rsa \
-in /etc/ssl/openldap/private/ldapserver-key.key \
-out /etc/ssl/openldap/private/ldapserver-key.key
Generate the certificate signing request (CSR). Be sure to configure the same details as you did when generating the CA certificate file above.
openssl req -new \
-key /etc/ssl/openldap/private/ldapserver-key.key \
-out /etc/ssl/openldap/certs/ldapserver-cert.csr \
-subj "/C=US/ST=California/L=SanFrancisco/O=Kifarunix Inc/OU=IT Infrastructure/CN=ldap.kifarunix.com/[email protected]"
Generate the LDAP server certificate and sign it with CA key and certificate generated above.
openssl ca -keyfile /etc/ssl/openldap/private/cakey.pem \
-cert /etc/ssl/openldap/certs/cacert.pem \
-in /etc/ssl/openldap/certs/ldapserver-cert.csr \
-out /etc/ssl/openldap/certs/ldapserver-cert.crt
Sample output;
Using configuration from /usr/lib/ssl/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 4097 (0x1001)
Validity
Not Before: Feb 24 20:54:50 2024 GMT
Not After : Feb 23 20:54:50 2025 GMT
Subject:
countryName = US
stateOrProvinceName = California
organizationName = Kifarunix Inc
organizationalUnitName = IT Infrastructure
commonName = ldap.kifarunix.com
emailAddress = [email protected]
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
X509v3 Subject Key Identifier:
41:68:00:99:97:5D:83:D8:E3:88:2C:43:9D:5B:0A:B7:33:2A:F0:44
X509v3 Authority Key Identifier:
BC:3C:1E:3C:D2:C4:BA:FD:5A:DB:AD:9B:90:A8:BD:57:4D:85:C1:B9
Certificate is to be certified until Feb 23 20:54:50 2025 GMT (365 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Database updated
To verify the LDAP server againt the CA;
openssl verify -CAfile /etc/ssl/openldap/certs/cacert.pem /etc/ssl/openldap/certs/ldapserver-cert.crt/etc/ssl/openldap/certs/ldapserver-cert.crt: OKNow, we have:
- the CA certificate file: /etc/ssl/openldap/certs/cacert.pem
- the server certificate: /etc/ssl/openldap/certs/ldapserver-cert.crt
- the server key file: /etc/ssl/openldap/private/ldapserver-key.key
Next, set the ownership of the OpenLDAP certificates directory to openldap user.
chown -R openldap: /etc/ssl/openldap/Update OpenLDAP Server TLS Certificates
Next, you need to update the OpenLDAP Server TLS certificates. Therefore, create the an LDIF file to define the TLS attributes as shown below;
vim ldap-tls.ldifdn: cn=config
changetype: modify
add: olcTLSCACertificateFile
olcTLSCACertificateFile: /etc/ssl/openldap/certs/cacert.pem
-
replace: olcTLSCertificateFile
olcTLSCertificateFile: /etc/ssl/openldap/certs/ldapserver-cert.crt
-
replace: olcTLSCertificateKeyFile
olcTLSCertificateKeyFile: /etc/ssl/openldap/private/ldapserver-key.key
Replace the locations of your certificates and key files accordingly.
To update the LDAP database, use ldapmodify command as shown below;
ldapmodify -Y EXTERNAL -H ldapi:/// -f ldap-tls.ldifSASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
modifying entry "cn=config"
To verify that the files are in place;
slapcat -b "cn=config" | grep -E "olcTLS"olcTLSCACertificateFile: /etc/ssl/openldap/certs/cacert.pem
olcTLSCertificateFile: /etc/ssl/openldap/certs/ldapserver-cert.crt
olcTLSCertificateKeyFile: /etc/ssl/openldap/private/ldapserver-key.key
To check the validity of the LDAP configuration, run the command below;
slaptest -uconfig file testing succeededNext, open the /etc/ldap/ldap.conf configuration file and change the location of the CA certificate.
vim /etc/ldap/ldap.conf...
# TLS certificates (needed for GnuTLS)
#TLS_CACERT /etc/ssl/certs/ca-certificates.crt
TLS_CACERT /etc/ssl/openldap/certs/cacert.pemRestart OpenLDAP daemon.
systemctl restart slapdConfirm the status;
systemctl status slapd● slapd.service - LSB: OpenLDAP standalone server (Lightweight Directory Access Protocol)
Loaded: loaded (/etc/init.d/slapd; generated)
Drop-In: /usr/lib/systemd/system/slapd.service.d
└─slapd-remain-after-exit.conf
Active: active (running) since Sat 2024-02-24 21:03:40 UTC; 7s ago
Docs: man:systemd-sysv-generator(8)
Process: 2984 ExecStart=/etc/init.d/slapd start (code=exited, status=0/SUCCESS)
Tasks: 3 (limit: 2238)
Memory: 3.4M (peak: 4.3M)
CPU: 22ms
CGroup: /system.slice/slapd.service
└─2994 /usr/sbin/slapd -h "ldap:/// ldapi:///" -g openldap -u openldap -F /etc/ldap/slapd.d
Feb 24 21:03:40 noble systemd[1]: Starting slapd.service - LSB: OpenLDAP standalone server (Lightweight Directory Access Protocol)...
Feb 24 21:03:40 noble slapd[2984]: * Starting OpenLDAP slapd
Feb 24 21:03:40 noble slapd[2993]: @(#) $OpenLDAP: slapd 2.6.7+dfsg-1~exp1ubuntu1 (Feb 6 2024 19:46:16) $
Ubuntu Developers
Feb 24 21:03:40 noble slapd[2994]: slapd starting
Feb 24 21:03:40 noble slapd[2984]: ...done.
Feb 24 21:03:40 noble systemd[1]: Started slapd.service - LSB: OpenLDAP standalone server (Lightweight Directory Access Protocol).
To verify OpenLDAP TLS connectivity, run the command below. If connection is fine, you should get the output, anonymous.
ldapwhoami -H ldap://ldap.kifarunix.com -x -ZZldapwhoami -H ldapi:/// -x -ZZOutput of the commands should be, anonymous.
Configure OpenLDAP to Provide SUDO
Create OpenLDAP SUDO Schema
To configure LDAP with support sudo, first, install sudo-ldap package.
SUDO_FORCE_REMOVE=yes apt install sudo-ldap -yYou can then verify the sudo OpenLDAP.
sudo -V | grep -i "ldap"If sudo supports LDAP, you should see the lines below;
Configure options: --build=x86_64-linux-gnu --prefix=/usr --includedir=${prefix}/include --mandir=${prefix}/share/man --infodir=${prefix}/share/info --sysconfdir=/etc --localstatedir=/var --disable-option-checking --disable-silent-rules --libdir=${prefix}/lib/x86_64-linux-gnu --runstatedir=/run --disable-maintainer-mode --disable-dependency-tracking --with-all-insults --with-pam --with-pam-login --with-fqdn --with-logging=syslog --with-logfac=authpriv --with-devel --with-env-editor --with-editor=/usr/bin/editor --with-timeout=15 --with-password-timeout=0 --with-passprompt=[sudo] password for %p: --with-tty-tickets --without-lecture --disable-root-mailer --with-sendmail=/usr/sbin/sendmail --with-rundir=/run/sudo --with-sssd --with-sssd-lib=/usr/lib/x86_64-linux-gnu --enable-zlib=system --enable-admin-flag --with-apparmor --with-selinux --with-linux-audit --enable-tmpfiles.d=/usr/lib/tmpfiles.d MVPROG=/bin/mv --with-exampledir=/usr/share/doc/sudo-ldap/examples --docdir=/usr/share/doc/sudo-ldap --with-ldap --with-ldap-conf-file=/etc/sudo-ldap.conf
ldap.conf path: /etc/sudo-ldap.conf
ldap.secret path: /etc/ldap.secret
Check if LDAP sudo schema is available.
find /usr/share/doc/ -iname schema.openldap/usr/share/doc/sudo-ldap/schema.OpenLDAPCopy the schema.OpenLDAP to the schema directory.
cp /usr/share/doc/sudo-ldap/schema.OpenLDAP /etc/ldap/schema/sudo.schemaConfigure OpenLDAP to include SUDO schema in its database
Next, you need to create sudo schema ldif file.
Convert the sudo schema to LDIF before you can configure SLAPD to include it in its database.
mkdir ldap-sudoecho "include /etc/ldap/schema/sudo.schema" > ldapsudo.confGenerate SUDO LDIF file from the schema;
cd ldap-sudoslaptest -f ../ldapsudo.conf -F .config file testing succeededThe sudo LDIF file should now be located under the cn\=config/cn\=schema/
ls cn\=config/cn\=schema/'cn={0}sudo.ldif'Edit the LDAP SUDO LDIF file;
vim cn\=config/cn\=schema/cn\=\{0\}sudo.ldifREMOVE comment lines (Lines beginning with #) at the top and update the lines;
dn: cn={0}sudo
objectClass: olcSchemaConfig
cn: {0}sudosuch that they look like;
dn: cn=sudo,cn=schema,cn=config
objectClass: olcSchemaConfig
cn: sudoAlso, REMOVE these lines at the bottom;
structuralObjectClass: olcSchemaConfig
entryUUID: 431580bc-67ab-103e-932b-a1c41a5943c1
creatorsName: cn=config
createTimestamp: 20240224215609Z
entryCSN: 20240224215609.360408Z#000000#000#000000
modifiersName: cn=config
modifyTimestamp: 20240224215609Z
Final sudo LDIF file looks like;
dn: cn=sudo,cn=schema,cn=config
objectClass: olcSchemaConfig
cn: sudo
olcAttributeTypes: {0}( 1.3.6.1.4.1.15953.9.1.1 NAME 'sudoUser' DESC 'User(s)
who may run sudo' EQUALITY caseExactMatch SUBSTR caseExactSubstringsMatch SY
NTAX 1.3.6.1.4.1.1466.115.121.1.15 )
olcAttributeTypes: {1}( 1.3.6.1.4.1.15953.9.1.2 NAME 'sudoHost' DESC 'Host(s)
who may run sudo' EQUALITY caseExactIA5Match SUBSTR caseExactIA5SubstringsMat
ch SYNTAX 1.3.6.1.4.1.1466.115.121.1.26 )
olcAttributeTypes: {2}( 1.3.6.1.4.1.15953.9.1.3 NAME 'sudoCommand' DESC 'Comma
nd(s) to be executed by sudo' EQUALITY caseExactIA5Match SYNTAX 1.3.6.1.4.1.1
466.115.121.1.26 )
olcAttributeTypes: {3}( 1.3.6.1.4.1.15953.9.1.4 NAME 'sudoRunAs' DESC 'User(s)
impersonated by sudo (deprecated)' EQUALITY caseExactIA5Match SYNTAX 1.3.6.1
.4.1.1466.115.121.1.26 )
olcAttributeTypes: {4}( 1.3.6.1.4.1.15953.9.1.5 NAME 'sudoOption' DESC 'Option
s(s) followed by sudo' EQUALITY caseExactIA5Match SYNTAX 1.3.6.1.4.1.1466.115
.121.1.26 )
olcAttributeTypes: {5}( 1.3.6.1.4.1.15953.9.1.6 NAME 'sudoRunAsUser' DESC 'Use
r(s) impersonated by sudo' EQUALITY caseExactMatch SYNTAX 1.3.6.1.4.1.1466.11
5.121.1.15 )
olcAttributeTypes: {6}( 1.3.6.1.4.1.15953.9.1.7 NAME 'sudoRunAsGroup' DESC 'Gr
oup(s) impersonated by sudo' EQUALITY caseExactMatch SYNTAX 1.3.6.1.4.1.1466.
115.121.1.15 )
olcAttributeTypes: {7}( 1.3.6.1.4.1.15953.9.1.8 NAME 'sudoNotBefore' DESC 'Sta
rt of time interval for which the entry is valid' EQUALITY generalizedTimeMat
ch ORDERING generalizedTimeOrderingMatch SYNTAX 1.3.6.1.4.1.1466.115.121.1.24
)
olcAttributeTypes: {8}( 1.3.6.1.4.1.15953.9.1.9 NAME 'sudoNotAfter' DESC 'End
of time interval for which the entry is valid' EQUALITY generalizedTimeMatch
ORDERING generalizedTimeOrderingMatch SYNTAX 1.3.6.1.4.1.1466.115.121.1.24 )
olcAttributeTypes: {9}( 1.3.6.1.4.1.15953.9.1.10 NAME 'sudoOrder' DESC 'an int
eger to order the sudoRole entries' EQUALITY integerMatch ORDERING integerOrd
eringMatch SYNTAX 1.3.6.1.4.1.1466.115.121.1.27 )
olcObjectClasses: {0}( 1.3.6.1.4.1.15953.9.2.1 NAME 'sudoRole' DESC 'Sudoer En
tries' SUP top STRUCTURAL MUST cn MAY ( sudoUser $ sudoHost $ sudoCommand $ s
udoRunAs $ sudoRunAsUser $ sudoRunAsGroup $ sudoOption $ sudoOrder $ sudoNotB
efore $ sudoNotAfter $ description ) )
You can also copy the default ldif file from /usr/share/doc/sudo-ldap/schema.olcSudo and just modified it.
Once done editing the sudo LDIF file, update the SLAPD database to include SUDO schema;
ldapadd -Q -Y EXTERNAL -H ldapi:/// -f 'cn=config/cn=schema/cn={0}sudo.ldif'You should see a line;
adding new entry "cn=sudo,cn=schema,cn=config"Enable sudo user and host indexing;
ldapadd -Y EXTERNAL -H ldapi:/// -QWhen the command runs, paste the content below and press ENTER twice.
dn: olcDatabase={1}mdb,cn=config
changetype: modify
add: olcDbIndex
olcDbIndex: sudoUser,sudoHost pres,eq
Once you see the line, modifying entry "olcDatabase={1}mdb,cn=config", press ctrl+d.
To verify indexing;
slapcat -n 0 | grep olcDbIndexolcDbIndex: objectClass eq
olcDbIndex: cn,uid eq
olcDbIndex: uidNumber,gidNumber eq
olcDbIndex: member,memberUid eq
olcDbIndex: sudoUser,sudoHost pres,eq
Your OpenLDAP should now be able to provide SUDO access for users. This is subject to further configuration, however.
Adjust OpenLDAP Database Access Control Lists
Next, adjust the SLAPD database access controls;
vim update-mdb-acl.ldifdn: olcDatabase={1}mdb,cn=config
changetype: modify
replace: olcAccess
olcAccess: to attrs=userPassword,shadowLastChange,shadowExpire
by self write
by anonymous auth
by dn.subtree="gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth" manage
by dn.exact="cn=readonly,ou=people,dc=ldap,dc=kifarunix,dc=com" read
by * none
olcAccess: to dn.exact="cn=readonly,ou=people,dc=ldap,dc=kifarunix,dc=com" by dn.subtree="gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth" manage by * none
olcAccess: to dn.subtree="dc=ldap,dc=kifarunix,dc=com" by dn.subtree="gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth" manage
by users read
by * none
Save and exit the file.
Note that we have included the access controls for the Read Only Bind DN user that we will create later in this guide.
Update database ACL with the above information by running the command below;
ldapadd -Y EXTERNAL -H ldapi:/// -f update-mdb-acl.ldifOpenLDAP User Accounts
Create OpenLDAP User Accounts
Before we can create OpenLDAP user accounts, we need to create the organization unit containers for storing users and their group information. See our example below. Be sure to make the relevant changes as per your environment setup.
vim users-ou.ldifdn: ou=people,dc=ldap,dc=kifarunix,dc=com
objectClass: organizationalUnit
objectClass: top
ou: people
dn: ou=groups,dc=ldap,dc=kifarunix,dc=com
objectClass: organizationalUnit
objectClass: top
ou: groups
Once that is done, you should now be able, as the admin, to create the users OU as shown above. Therefore, to update the database with the user OU information above, run the command below;
ldapadd -Y EXTERNAL -H ldapi:/// -f users-ou.ldifSASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
adding new entry "ou=people,dc=ldap,dc=kifarunix,dc=com"
adding new entry "ou=groups,dc=ldap,dc=kifarunix,dc=com"
Once you have the user OU containers created, you can now add user accounts. In this demo, we will create a user called johndoe in our OpenLDAP database.
vim johndoe.ldifdn: uid=johndoe,ou=people,dc=ldap,dc=kifarunix,dc=com
objectClass: inetOrgPerson
objectClass: posixAccount
objectClass: shadowAccount
uid: johndoe
cn: John
sn: Doe
loginShell: /bin/bash
uidNumber: 10000
gidNumber: 10000
homeDirectory: /home/johndoe
shadowMax: 60
shadowMin: 1
shadowWarning: 7
shadowInactive: 7
shadowLastChange: 0
dn: cn=johndoe,ou=groups,dc=ldap,dc=kifarunix,dc=com
objectClass: posixGroup
cn: johndoe
gidNumber: 10000
memberUid: johndoe
To add the user johndoe to the database using the information above, run the command below;
ldapadd -Y EXTERNAL -H ldapi:/// -f johndoe.ldif -Qadding new entry "uid=johndoe,ou=people,dc=ldap,dc=kifarunix,dc=com"
adding new entry "cn=johndoe,ou=groups,dc=ldap,dc=kifarunix,dc=com"
Setting Password for LDAP Users
If you noticed, in the above, we didn’t set any password for the user. To set/reset the password for the user, run the command below;
ldappasswd -H ldapi:/// -Y EXTERNAL -S "uid=johndoe,ou=people,dc=ldap,dc=kifarunix,dc=com"To verify user’s password;
ldapwhoami -H ldap://ldap.kifarunix.com -x -D "uid=johndoe,ou=people,dc=ldap,dc=kifarunix,dc=com" -WIf the password is correct, you should see the user’s DN;
dn:uid=johndoe,ou=people,dc=ldap,dc=kifarunix,dc=comCreate OpenLDAP BIND DN
There are two OpenLDAP BIND DNs;
Administrator Bind DN: defines admin username and password. It is used only for querying the directory server and so this user must have privileges to search the directory.User Bind DN: defines the user username and password is used for authentication and password change operations.
Create Bind DN Read Only User
In this demo, we will create a user Bind DN called readonly for read operations.
Generate the password hash for the bind DN user;
slappasswdNew password: password
Re-enter new password: password
{SSHA}eTWwv010qnaaYeKPVGxe1mbPGdNKA75/
Copy the hash above and replace it with the value of userPassword below;
vim readonly-user.ldifdn: cn=readonly,ou=people,dc=ldap,dc=kifarunix,dc=com
objectClass: organizationalRole
objectClass: simpleSecurityObject
cn: readonly
userPassword: {SSHA}eTWwv010qnaaYeKPVGxe1mbPGdNKA75/
description: Bind DN user for LDAP Operations
Add the bind user to the LDAP database;
ldapadd -Y EXTERNAL -H ldapi:/// -f readonly-user.ldifadding new entry "cn=readonly,ou=people,dc=ldap,dc=kifarunix,dc=com"Define Access Control Lists for ReadOnly User
Define the access controls for the user bind DN. See what we have in our ACL file above. Or simply run the command below to check the ACLs defined;
ldapsearch -Q -LLL -Y EXTERNAL -H ldapi:/// -b cn=config '(olcDatabase={1}mdb)' olcAccessSample ACLs;
dn: olcDatabase={1}mdb,cn=config
olcAccess: {0}to attrs=userPassword,shadowLastChange,shadowExpire by self writ
e by anonymous auth by dn.subtree="gidNumber=0+uidNumber=0,cn=peercred,cn=ext
ernal,cn=auth" manage by dn.exact="cn=readonly,ou=people,dc=ldap,dc=kifaruni
x,dc=com" read by * none
olcAccess: {1}to dn.exact="cn=readonly,ou=people,dc=ldap,dc=kifarunix,dc=com"
by dn.subtree="gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth" manag
e by * none
olcAccess: {2}to dn.subtree="dc=ldap,dc=kifarunix,dc=com" by dn.subtree="gidNu
mber=0+uidNumber=0,cn=peercred,cn=external,cn=auth" manage by users read by
* none
Create OpenLDAP System Bind DN and User
Bind DN user is used for performing LDAP operations such as resolving User IDs and group IDs.
In this guide, we create a bind DN ou called system.
Note the access controls associated with this ou as defined on the root DN above.
You can list the Access control lists on the database;
ldapsearch -Q -LLL -Y EXTERNAL -H ldapi:/// -b cn=config '(olcDatabase={1}mdb)' olcAccessCreate the LDAP system Bind DN user password.
slappasswdNew password:
Re-enter new password:
{SSHA}OlOxrrrIpdrVovFj4QeD/lc8cF/Z0yl6
Copy and Paste the password hash value above as the value of userPassword attribute in the file below;
cat > bindDNuser.ldif << 'EOL'
dn: ou=system,dc=ldap,dc=kifarunix,dc=com
objectClass: organizationalUnit
objectClass: top
ou: system
dn: cn=readonly,ou=system,dc=ldap,dc=kifarunix,dc=com
objectClass: organizationalRole
objectClass: simpleSecurityObject
cn: readonly
userPassword: {SSHA}OlOxrrrIpdrVovFj4QeD/lc8cF/Z0yl6
description: Bind DN user for LDAP Operations
EOL
ldapadd -Y EXTERNAL -H ldapi:/// -f bindDNuser.ldifNext, read the guide below to learn how to implement password policies.
Implement OpenLDAP Password Policies
Note that the password policies modules are already loaded, hence skip the part, "Load Password Policy Module".
Configure OpenLDAP Logging on Ubuntu 24.04
By default, OpenLDAP logging level is set to none which is required to have high priority messages only logged.
You can change this to a different log level, say to stats level (logs connections/operations/results), run the command below;
ldapmodify -Y EXTERNAL -H ldapi:/// -QThe copy and paste the content below on the prompt to modify the log level.
dn: cn=config
changeType: modify
replace: olcLogLevel
olcLogLevel: stats
Next, press ENTER twice. Once you see a line, modifying entry "cn=config", then press Ctrl+d.
You can as well use LDIF files to update this information if you like.
To confirm the changes;
ldapsearch -Y EXTERNAL -H ldapi:/// -b cn=config "(objectClass=olcGlobal)" olcLogLevel -LLL -Qdn: cn=config
olcLogLevel: stats
Next, you need to specify the log file for OpenLDAP on Rsyslog configuration. By default, OpenLDAP logs to local4 facility, hence, to configure it to log to /var/log/slapd.log for example, execute the command below;
echo "local4.* /var/log/slapd.log" >> /etc/rsyslog.d/51-slapd.confRestart Rsyslog and SLAPD service
systemctl restart rsyslog slapdYou should now be able to read the LDAP logs on, /var/log/slapd.log.
You can as well configure log rotation;
cat > /etc/logrotate.d/slapd << EOL
/var/log/slapd.log
{
rotate 7
daily
missingok
notifempty
delaycompress
compress
postrotate
/usr/lib/rsyslog/rsyslog-rotate
endscript
}
EOL
Restart log rotation service;
systemctl restart logrotateAllow OpenLDAP Service on Firewall
If UFW is running, allow OpenLDAP (both LDAP and LDAPS) external access;
ufw allow "OpenLDAP LDAP"ufw allow "OpenLDAP LDAPS"If using Iptables, allow the services accordingly.
Authenticate Via OpenLDAP Server
And that is it on how to install OpenLDAP Server.
To verify that users can actually connect to the systems via the OpenLDAP server, you need to configure OpenLDAP clients on the remote systems.
See the guides below;

