Welcome to our guide on how to install and setup HAProxy on Ubuntu 20.04. HAProxy (High Availability Proxy), as you might already be aware, is a free, very fast and reliable solution offering high availability, load balancing, and proxying for TCP and HTTP-based applications. It is particularly suited for very high traffic web sites and powers quite a number of the world’s most visited ones.
It features connection persistence through HTTP cookies, load balancing, header addition, modification, deletion both ways. It has request blocking capabilities and provides interface to display server status.
Installing HAProxy on Ubuntu 20.04
HAProxy is available on the default Ubuntu 20.04 repos. However, the available package might not be up-to-date.
apt show haproxyPackage: haproxy
Version: 2.0.13-2
Priority: optional
Section: net
Origin: Ubuntu
Maintainer: Ubuntu Developers <[email protected]>
Original-Maintainer: Debian HAProxy Maintainers <[email protected]>
Bugs: https://bugs.launchpad.net/ubuntu/+filebug
Installed-Size: 3,287 kB
Pre-Depends: dpkg (>= 1.17.14)
Depends: libc6 (>= 2.17), libcrypt1 (>= 1:4.1.0), libgcc-s1 (>= 3.0), liblua5.3-0, libpcre2-8-0 (>= 10.22), libssl1.1 (>= 1.1.1), libsystemd0, zlib1g (>= 1:1.1.4), adduser, lsb-base (>= 3.0-6)
Suggests: vim-haproxy, haproxy-doc
Homepage: http://www.haproxy.org/
Download-Size: 1,519 kB
APT-Sources: http://ke.archive.ubuntu.com/ubuntu focal/main amd64 PackagesAs you can see, the HAProxy package available on the default repos is version 2.0.13 while the current stable release is version 2.1.5.
Create HAProxy PPA Repository for Ubuntu
There are however, PPA repos that provides the latest stable release versions of HAProxy maintained by Vincent Bernat. These PPA repos can be installed as follows;
install software-properties-commonadd-apt-repository ppa:vbernat/haproxy-2.1 --yesRun system update
Once the PPA repos are added to system, update your system package cache;
apt updateInstall HAProxy on Ubuntu 20.04
You can now be able to install the latest stable version of HAProxy;
apt-cache policy haproxyhaproxy:
Installed: (none)
Candidate: 2.1.5-1ppa1~focal
Version table:
2.1.5-1ppa1~focal 500
500 http://ppa.launchpad.net/vbernat/haproxy-2.1/ubuntu focal/main amd64 Packages
2.0.13-2 500
500 http://ke.archive.ubuntu.com/ubuntu focal/main amd64 PackagesNote the versions provided by individual repos.
You can now install HAProxy;
apt install haproxyTo check the version of installed HAProxy, run the command below;
haproxy -vHA-Proxy version 2.1.5-1ppa1~focal 2020/06/01 - https://haproxy.org/
Status: stable branch - will stop receiving fixes around Q1 2021.
Known bugs: http://www.haproxy.org/bugs/bugs-2.1.5.html
Running on: Linux 5.4.0-33-generic #37-Ubuntu SMP Thu May 21 12:53:59 UTC 2020 x86_64Configure HAProxy Load Balancer on Ubuntu 20.04
With HAProxy, you can define multiple proxy services and configure HAProxy to load balance the traffic for the defined proxies. Proxies are made up of frontend system and one or more back-end systems. The front-end system defines the IP address and port on which the proxy listens as well as the back-end systems to use for a particular proxy.
The main configuration file for HAProxy is /etc/haproxy/haproxy.cfg.
The HAProxy configuration file is made up of four sections;
global: The global section defines process-wide security and performance tunings that affect HAProxy at a low level.defaults: The global section defines the configuration settings that are applied to all of thefrontendandbackendsections. You can define multiple default sections but the sub-sequent defaults sections override that came before it.frontend: When HAProxy is placed as a reverse proxy, thefrontendsection defines the IP addresses and ports that clients can connect to.backend: The backend section defines the group of servers that will be load balanced and assigned to handle requests.
The frontend and backend sections can be combined using the listen section. It can also be used to server HAProxy statistics page.
Read more about these sections on Essential Sections of an HAProxy Configuration.
The default HAProxy file configuration looks like as shown below;
grep -v '^\s*#' /etc/haproxy/haproxy.cfgglobal
log /dev/log local0
log /dev/log local1 notice
chroot /var/lib/haproxy
stats socket /run/haproxy/admin.sock mode 660 level admin expose-fd listeners
stats timeout 30s
user haproxy
group haproxy
daemon
ca-base /etc/ssl/certs
crt-base /etc/ssl/private
ssl-default-bind-ciphers ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384
ssl-default-bind-ciphersuites TLS_AES_128_GCM_SHA256:TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256
ssl-default-bind-options ssl-min-ver TLSv1.2 no-tls-tickets
defaults
log global
mode http
option httplog
option dontlognull
timeout connect 5000
timeout client 50000
timeout server 50000
errorfile 400 /etc/haproxy/errors/400.http
errorfile 403 /etc/haproxy/errors/403.http
errorfile 408 /etc/haproxy/errors/408.http
errorfile 500 /etc/haproxy/errors/500.http
errorfile 502 /etc/haproxy/errors/502.http
errorfile 503 /etc/haproxy/errors/503.http
errorfile 504 /etc/haproxy/errors/504.httpIn our configuration file, we will modify the above to include the frontend and backend sections.
Before you can proceed, make a backup of the default config file;
cp /etc/haproxy/haproxy.cfg{,.factory}Define HAProxy Frontend Configuration Settings
As stated above, the frontend section defines the IP addresses and ports that clients can connect to (The IP address and ports on the HAProxy server itself). Therefore, this is how our frontend configuration is like;
frontend
bind 192.168.57.8:443 ssl crt /etc/ssl/certs/haproxy.pem
default_backend webapps
option forwardforbind: Define one or more listening addresses and/or ports in a frontend server.ssl crt: Configures HAProxy SSL Termination and specifies the path to SSL/TLS certificate.default_backend: Specifies the backend to use when no “use_backend” rule has been matched.option forwardfor: HAProxy operates in reverse-proxy mode. This option enable the backend servers to see the IP addresses of the clients instead of the IP address for HAProxy server.
NOTE:
In this demo, our proxied backends uses SSL/TLS certificates. As such, instead of configuring each backend application to terminate its SSL/TLS connection (SSL Pass through), we will configure HAProxy as an SSL/TLS certificate termination point (SSL Termination).
If you are not using SSL/TLS termination, remove the SSL part of the bind line, ssl crt /etc/ssl/certs/haproxy.pem.
Define HAProxy Backend Configuration Settings
In this section, we will, in the basic form, define the HAProxy Scheduling Algorithms and the backend servers whose requests are being proxied/load balanced.
backend webapps
balance roundrobin
server app01 192.168.59.6:80 check
server app02 192.168.60.4:80 check- balance parameter defines the load balancer scheduling algorithm.
- roundrobin selects the servers in turns.
- Other common algorithms is leastconn which enabled the load balancer to forward request to servers with least connections.
- server setting specify the servers available in the back end.
- check option enables health checks on the server such that if one of them is down, requests are directed to the available backend servers.
Define HAProxy Statistics Configuration Settings
According to HAProxy Stats page, HAProxy ships with a dashboard called the HAProxy Stats page that shows an abundance of metrics covering the health of the servers, current request rates, response times, and more. These metrics gives granular data on a per-frontend, backend, and server basis. This can be enabled using the stats enable directive, which can be added to either frontend or listen section. We used a listen section in this tutorial.
listen stats
bind 192.168.57.8:8443 ssl crt /etc/ssl/certs/haproxy.pem
stats enable # enable statistics reports
stats hide-version # Hide the version of HAProxy
stats refresh 30s # HAProxy refresh time
stats show-node # Shows the hostname of the node
stats auth haadmin:P@ssword # Enforce Basic authentication for Stats page
stats uri /stats # Statistics URLNote that the line, bind 192.168.57.8:8443 ssl crt /etc/ssl/certs/haproxy.pem, defines the frontend IP and port to access the HAProxy stats as well as the SSL/TLS cert to use.
Save and exit the file once done with configuration.
In general, this is how our configuration is like. NOTE that we added the line, tune.ssl.default-dh-param 2048, to SSL/TLS configuration options section.
global
log /dev/log local0
log /dev/log local1 notice
chroot /var/lib/haproxy
stats socket /run/haproxy/admin.sock mode 660 level admin expose-fd listeners
stats timeout 30s
user haproxy
group haproxy
daemon
ca-base /etc/ssl/certs
crt-base /etc/ssl/private
ssl-default-bind-ciphers ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384
ssl-default-bind-ciphersuites TLS_AES_128_GCM_SHA256:TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256
ssl-default-bind-options ssl-min-ver TLSv1.2 no-tls-tickets
tune.ssl.default-dh-param 2048
defaults
log global
mode http
option httplog
option dontlognull
timeout connect 5000
timeout client 50000
timeout server 50000
errorfile 400 /etc/haproxy/errors/400.http
errorfile 403 /etc/haproxy/errors/403.http
errorfile 408 /etc/haproxy/errors/408.http
errorfile 500 /etc/haproxy/errors/500.http
errorfile 502 /etc/haproxy/errors/502.http
errorfile 503 /etc/haproxy/errors/503.http
errorfile 504 /etc/haproxy/errors/504.http
frontend kifarunixlb
bind 192.168.57.8:443 ssl crt /etc/ssl/certs/haproxy.pem
default_backend webapps
option forwardfor
backend webapps
balance roundrobin
server app01 192.168.59.6:80 check
server app02 192.168.60.4:80 check
listen stats
bind 192.168.57.8:8443 ssl crt /etc/ssl/certs/haproxy.pem
stats enable # enable statistics reports
stats hide-version # Hide the version of HAProxy
stats refresh 30s # HAProxy refresh time
stats show-node # Shows the hostname of the node
stats auth haadmin:P@ssword # Enforce Basic authentication for Stats page
stats uri /stats # Statistics URLValidate HAProxy Configuration Syntax
Once done with configuration, run the command below to verify the HAProxy config syntax validation before you can start it;
haproxy -f /etc/haproxy/haproxy.cfg -c -VIf all is well, you should get the output;
Configuration file is validOtherwise, you will get errors on stdout. Be sure to fix before you can proceed.
Running HAProxy
When installed, HAProxy is started and enabled to run on system boot by default. You can restart it by running the command below
systemctl restart haproxyTo check the status;
systemctl status haproxy● haproxy.service - HAProxy Load Balancer
Loaded: loaded (/lib/systemd/system/haproxy.service; enabled; vendor preset: enabled)
Active: active (running) since Fri 2020-06-05 20:45:33 UTC; 7s ago
Docs: man:haproxy(1)
file:/usr/share/doc/haproxy/configuration.txt.gz
Process: 21423 ExecStartPre=/usr/sbin/haproxy -f $CONFIG -c -q $EXTRAOPTS (code=exited, status=0/SUCCESS)
Main PID: 21425 (haproxy)
Tasks: 3 (limit: 2282)
Memory: 39.5M
CGroup: /system.slice/haproxy.service
├─21425 /usr/sbin/haproxy -Ws -f /etc/haproxy/haproxy.cfg -p /run/haproxy.pid -S /run/haproxy-master.sock
└─21440 /usr/sbin/haproxy -Ws -f /etc/haproxy/haproxy.cfg -p /run/haproxy.pid -S /run/haproxy-master.sock
Jun 05 20:45:33 haproxy.kifarunix-demo.com systemd[1]: Starting HAProxy Load Balancer...
Jun 05 20:45:33 haproxy.kifarunix-demo.com haproxy[21425]: Proxy kifarunixlb started.
Jun 05 20:45:33 haproxy.kifarunix-demo.com haproxy[21425]: Proxy kifarunixlb started.
Jun 05 20:45:33 haproxy.kifarunix-demo.com haproxy[21425]: Proxy webapps started.
Jun 05 20:45:33 haproxy.kifarunix-demo.com haproxy[21425]: Proxy webapps started.
Jun 05 20:45:33 haproxy.kifarunix-demo.com haproxy[21425]: Proxy stats started.
Jun 05 20:45:33 haproxy.kifarunix-demo.com haproxy[21425]: Proxy stats started.
Jun 05 20:45:33 haproxy.kifarunix-demo.com haproxy[21425]: [NOTICE] 156/204533 (21425) : New worker #1 (21440) forked
Jun 05 20:45:33 haproxy.kifarunix-demo.com systemd[1]: Started HAProxy Load Balancer.If UFW is running, Open port 443 as well as the statistics port;
ufw allow 443/tcpufw allow 8443/tcpVerify HAProxy Load Balancing Setup on Ubuntu 20.04
You can now access your HAProxy from browser to confirm your LB setup. Use the address, https[s]://lb-server-IP-or-hostname.
The first page shows content from the first defined backend, in this demo, app01. Remember the LB algorithm used here, roundrobin.
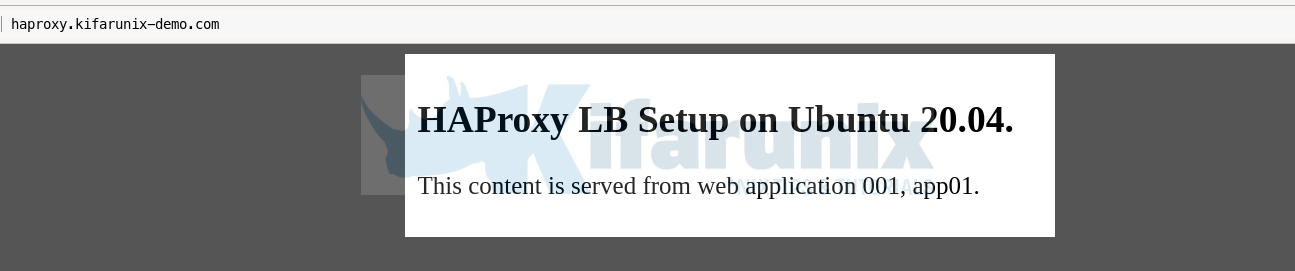
If you reload the url, the content from the second app shows;
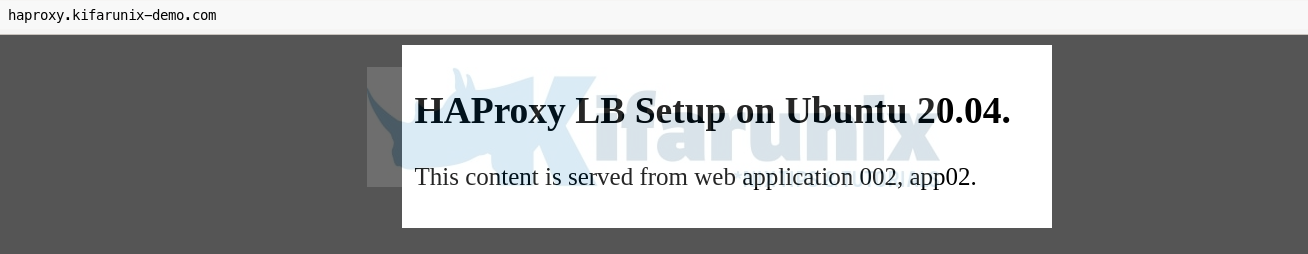
You can also check the statistics of your HAProxy, http[s]://lb-server-IP-or-hostname[:port]/stats. If you enabled basic authentication, you are prompted to authenticate.
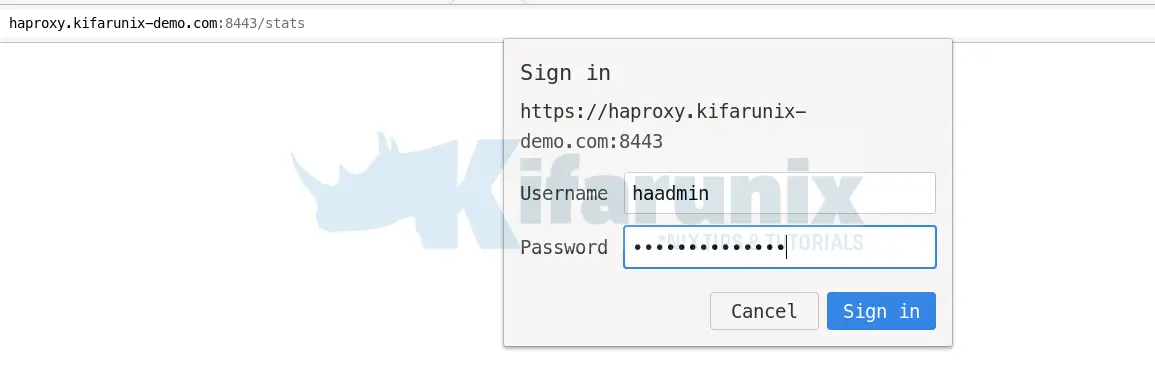
And there you got your statistics.
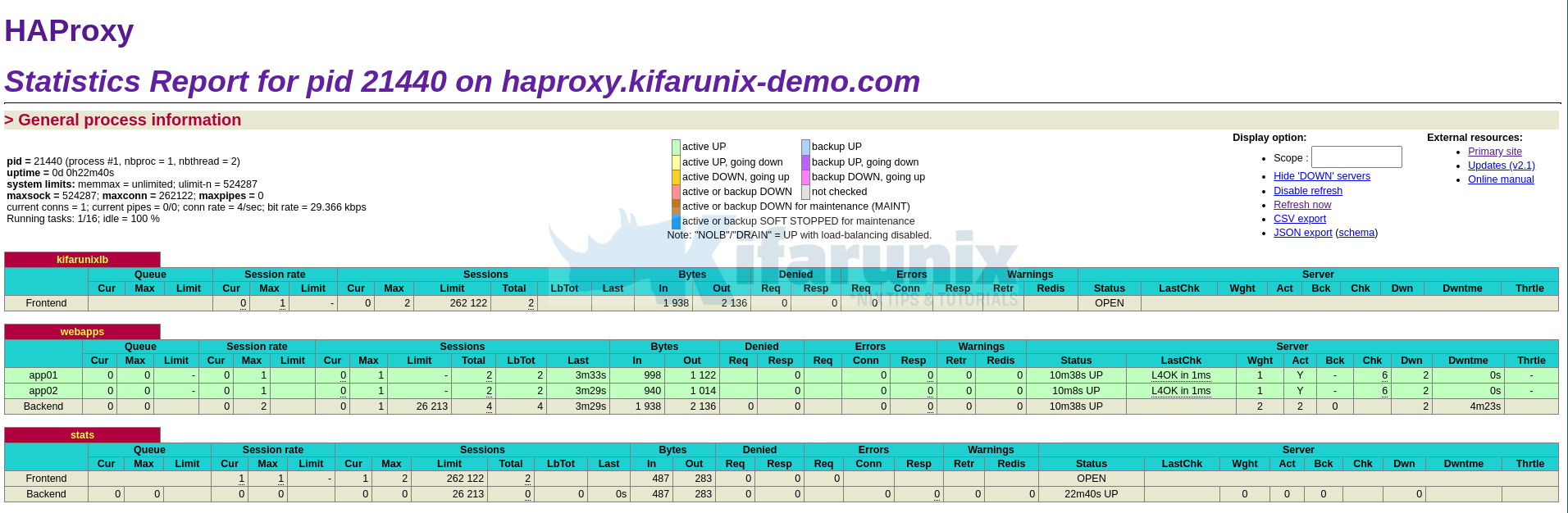
That brings us to the end of our tutorial on how to installing HAProxy on Ubuntu 20.04.
Further Reading
Related Tutorials
Install and Setup HAProxy on CentOS 8
Setup HAProxy Load Balancer on Fedora 30/Fedora 29
How to Install and Configure Pound as Apache HTTP Load balancer on Ubuntu 16.04

