In this guide, you will learn how to install and setup GVM 20.08 on Ubuntu 20.04. Greenbone Vulnerability Management (GVM), previously known as OpenVAS, is a network security scanner which provides a set of network vulnerability tests (NVTs) to detect security loopholes in systems and applications. As of this writing, GVM 20.08 is the current stable release and is the first release that uses a calendar based versioning (August of 2020).
With the release of GVM 20.08, GVM 10 and GVM 11 were set to retire by end of 2020.
Installing GVM on Ubuntu 20.04
Prerequisites
In this demo, we will install GVM on Ubuntu 20.04 from source code. As such, below are the system requirements I would personally recommend.
- At least 4 GB RAM
- At least 4 vCPUs
- More than 8 GB disk space (We used 16 GB in this demo)
These requirements will vary depending on your use cases, however. Just be sure to provide “enough”.
Run System Update
To begin with, update and upgrade your system packages;
apt updateapt upgradeCreate GVM User on Ubuntu
In this demo, we will run GVM 20.08 as a non privileged system user. Thus, create gvm system user account.
useradd -r -d /opt/gvm -c "GVM User" -s /bin/bash gvmCreate the GVM user directory as specified by option -d in the command above and set the user and group ownership to gvm.
mkdir /opt/gvmchown gvm: /opt/gvmInstall Required Build Tools
In order to successfully build GVM 20.08 on Ubuntu 20.04, you need to install a number of required dependencies and build tools.
apt install gcc g++ make bison flex libksba-dev curl redis libpcap-dev \
cmake git pkg-config libglib2.0-dev libgpgme-dev nmap libgnutls28-dev uuid-dev \
libssh-gcrypt-dev libldap2-dev gnutls-bin libmicrohttpd-dev libhiredis-dev \
zlib1g-dev libxml2-dev libradcli-dev clang-format libldap2-dev doxygen \
gcc-mingw-w64 xml-twig-tools libical-dev perl-base heimdal-dev libpopt-dev \
libsnmp-dev python3-setuptools python3-paramiko python3-lxml python3-defusedxml python3-dev gettext python3-polib xmltoman \
python3-pip texlive-fonts-recommended texlive-latex-extra --no-install-recommends xsltproc libunistring-devInstall Yarn on Ubuntu 20.04
Next, install Yarn JavaScript package manager
curl -sS https://dl.yarnpkg.com/debian/pubkey.gpg | apt-key add -echo "deb https://dl.yarnpkg.com/debian/ stable main" | tee /etc/apt/sources.list.d/yarn.listapt updateapt install yarn -yInstall PostgreSQL on Ubuntu 20.04
GVM 20.08 uses PostgreSQL as the backend database. Therefore, run the command below to install PostgreSQL on Ubuntu 20.04;
apt install postgresql postgresql-contrib postgresql-server-dev-allCreate PostgreSQL User and Database
Once the installation is done, create the PostgreSQL user and database for Greenbone Vulnerability Management Daemon (gvmd). Note that the database and user should be created as PostgreSQL user, postgres.
sudo -Hiu postgres
createuser gvm
createdb -O gvm gvmdGrant PostgreSQL User DBA Roles
psql gvmd
create role dba with superuser noinherit;
grant dba to gvm;
create extension "uuid-ossp";
create extension "pgcrypto";
\q
exitOnce that is done, restart PostgreSQL;
systemctl restart postgresqlsystemctl enable postgresqlBuilding GVM 20.08 from Source Code
There are different tools required to install and setup GVM. These include;
- GVM Libraries
- OpenVAS Scanner
- OSPd
- ospd-openvas
- Greenbone Vulnerability Manager
- Greenbone Security Assistant
- Python-GVM
- GVM-Tools
- OpenVAS SMB
Every component has README.md and a INSTALL.md file that explains how to build and install it.
Since we are running GVM as non-privileged user, gvm, then we will install all the GVM configuration files and libraries under, /opt/gvm.
Update the PATH environment variable on /etc/environment, to include the GVM binary path such that it looks like;
vim /etc/environmentPATH="/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games:/usr/local/games:/opt/gvm/bin:/opt/gvm/sbin:/opt/gvm/.local/bin"Add GVM library path to /etc/ld.so.conf.d.
echo "/opt/gvm/lib" > /etc/ld.so.conf.d/gvm.confBuild and Install GVM 20.08 on Ubuntu 20.04
Switch to GVM user, gvm and create a temporary directory to store GVM source files.
su - gvmmkdir gvm-sourceDownload GVM 20.08 Source Files
Navigate to temporary directory created above and run the subsequent commands to clone the GVM github branch files.
cd gvm-sourcegit clone -b gvm-libs-20.08 https://github.com/greenbone/gvm-libs.gitgit clone -b master https://github.com/greenbone/openvas-smb.gitgit clone -b openvas-20.08 https://github.com/greenbone/openvas.gitgit clone -b ospd-20.08 https://github.com/greenbone/ospd.gitgit clone -b ospd-openvas-20.08 https://github.com/greenbone/ospd-openvas.gitgit clone -b gvmd-20.08 https://github.com/greenbone/gvmd.gitgit clone -b gsa-20.08 https://github.com/greenbone/gsa.gitOnce the source files are in place, proceed to build and install GVM 20.08 on Ubuntu 20.04.
Note the current working directory;
pwd/opt/gvm/gvm-sourcels -1gsa
gvmd
gvm-libs
openvas
openvas-smb
ospd
ospd-openvasNote that we will install all GVM 20.08 files and libraries to a non-standard location, /opt/gvm. As such, you need to set the PKG_CONFIG_PATH environment variable to the location of your pkg-config files before configuring:
export PKG_CONFIG_PATH=/opt/gvm/lib/pkgconfig:$PKG_CONFIG_PATHBe sure to replace the path, /opt/gvm, accordingly.
Build and Install GVM 11 Libraries
From within the source directory, /opt/gvm/gvm-source, in this setup, change to GVM libraries directory;
cd gvm-libsCreate a build directory and change into it;
mkdir build
cd buildConfigure the build;
cmake .. -DCMAKE_INSTALL_PREFIX=/opt/gvmNext, compile and install GVM libraries
makemake installBuild and Install OpenVAS scanner and OpenVAS SMB
Open Vulnerability Assessment Scanner (OpenVAS) is a full-featured scan engine that executes a continuously updated and extended feed of Network Vulnerability Tests (NVTs).
OpenVAS SMB provides modules for the OpenVAS Scanner to interface with Microsoft Windows Systems through the Windows Management Instrumentation API and a winexe binary to execute processes remotely on that system.
Build and install openvas-smb;
cd ../../openvas-smb/
mkdir build
cd build
cmake .. -DCMAKE_INSTALL_PREFIX=/opt/gvm
make
make installBuild and install OpenVAS scanner;
cd ../../openvasProceed to build and install openvas.
mkdir build
cd build
cmake .. -DCMAKE_INSTALL_PREFIX=/opt/gvm
make
make installConfiguring OpenVAS Scanner
The host scan information is stored temporarily on Redis server. The default configuration of Redis server is /etc/redis/redis.conf.
Switch back to privileged user and proceed.
exitTo begin run the command below to create the cache to the installed shared libraries;
ldconfigNext, copy OpenVAS scanner Redis configuration file, redis-openvas.conf, to the same Redis config directory;
cp /opt/gvm/gvm-source/openvas/config/redis-openvas.conf /etc/redis/Update the ownership of the configuration.
chown redis:redis /etc/redis/redis-openvas.confUpdate the path to Redis unix socket on the /opt/gvm/etc/openvas/openvas.conf using the db_address parameter as follows;
echo "db_address = /run/redis-openvas/redis.sock" > /opt/gvm/etc/openvas/openvas.confNote, the Unix socket path is defined on /etc/redis/redis-openvas.conf file.
chown gvm:gvm /opt/gvm/etc/openvas/openvas.confAdd gvm user to redis group;
usermod -aG redis gvmYou can also optimize Redis server itself improve the performance by making the following adjustments;
Increase the value of somaxconn in order to avoid slow clients connections issues.
echo "net.core.somaxconn = 1024" >> /etc/sysctl.confRedis background save may fail under low memory condition. To avoid this, enable memory overcommit (man 5 proc).
echo 'vm.overcommit_memory = 1' >> /etc/sysctl.confReload sysctl variables created above.
sysctl -pTo avoid creation of latencies and memory usage issues with Redis, disable Linux Kernel’s support for Transparent Huge Pages (THP). To easily work around this, create a systemd service unit for this purpose.
vim /etc/systemd/system/disable_thp.service[Unit]
Description=Disable Kernel Support for Transparent Huge Pages (THP)
[Service]
Type=simple
ExecStart=/bin/sh -c "echo 'never' > /sys/kernel/mm/transparent_hugepage/enabled && echo 'never' > /sys/kernel/mm/transparent_hugepage/defrag"
[Install]
WantedBy=multi-user.targetReload systemd configurations;
systemctl daemon-reloadStart and enable this service to run on system boot.
systemctl enable --now disable_thpRestart OpenVAS Redis server
systemctl enable --now redis-server@openvasA number of Network Vulnerability Tests (NVTs) require root privileges to perform certain operations. Since openvas is launched from an ospd-openvas process, via sudo, add the line below to sudoers file to ensure that the gvm user used in this demo can run the openvas with elevated rights using passwordless sudo.
echo "gvm ALL = NOPASSWD: /opt/gvm/sbin/openvas" > /etc/sudoers.d/gvmAlso, update the secure_path to include the GVM /sbin paths, /opt/gvm/sbin.
visudoDefaults secure_path="/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/snap/bin:/opt/gvm/sbin"Also, enable gvm user to run GSA web application daemon, gsad, with passwordless sudo.
echo "gvm ALL = NOPASSWD: /opt/gvm/sbin/gsad" >> /etc/sudoers.d/gvmUpdate NVTs
Update Network Vulnerability Tests feed from Greenbone Security Feed/Community Feed using the greenbone-nvt-sync command.
The greenbone-nvt-sync command must not be executed as privileged user root, hence switch back to GVM user we created above and update the NVTs.
su - gvmNext, update the NVTs as openvas user;
greenbone-nvt-syncOnce the update is done, you need to update Redis server with the same VT info from VT files;
sudo openvas --update-vt-infoBuild and Install Greenbone Vulnerability Manager
export PKG_CONFIG_PATH=/opt/gvm/lib/pkgconfig:$PKG_CONFIG_PATHcd gvm-source/gvmd
mkdir build
cd build
cmake .. -DCMAKE_INSTALL_PREFIX=/opt/gvm
make
make installBuild and Install Greenbone Security Assistant
cd ../../gsa
mkdir build
cd build
cmake .. -DCMAKE_INSTALL_PREFIX=/opt/gvm
make
make installKeeping the feeds up-to-date
The gvmd Data, SCAP and CERT Feeds should be kept up-to-date by calling the greenbone-feed-sync script regularly (e.g. via a cron entry):
sudo -Hiu gvm greenbone-feed-sync --type GVMD_DATAsudo -Hiu gvm greenbone-feed-sync --type SCAPsudo -Hiu gvm greenbone-feed-sync --type CERTPlease note: The CERT feed sync depends on data provided by the SCAP feed and should be called after syncing the later.
Consider setting cron jobs to run the nvts, cert and scap data update scripts at your preferred frequency to pull updates from the feed servers.
Next, run the command below to generate certificates gvmd. Server certificates are used for authentication while client certificates are primarily used for authorization. More on man gvm-manage-certs.
gvm-manage-certs -aBuild and Install OSPd and OSPd-OpenVAS
Open Scanner Protocol (OSP) creates a unified interface for different security scanners and makes their control flow and scan results consistently available under the central Greenbone Vulnerability Manager service.
export PKG_CONFIG_PATH=/opt/gvm/lib/pkgconfig:$PKG_CONFIG_PATHcd /opt/gvm/gvm-source/ospd
python3 setup.py install --prefix=/opt/gvmcd /opt/gvm/gvm-source/ospd-openvas
python3 setup.py install --prefix=/opt/gvmRunning OpenVAS Scanner, GSA and GVM services
In order to make the management of OpenVAS scanner, GSA (WebUI service) and GVM daemon, create systemd service unit files for each of them as follows.
Log out as gvm user and execute the commands below as a privileged user.
exitCreating Systemd Service units for GVM services
Create OpenVAS systemd service
cat > /etc/systemd/system/openvas.service << 'EOL'
[Unit]
Description=Control the OpenVAS service
After=redis.service
After=postgresql.service
[Service]
ExecStartPre=-rm -rf /opt/gvm/var/run/ospd-openvas.pid /opt/gvm/var/run/ospd.sock /opt/gvm/var/run/gvmd.sock
Type=simple
User=gvm
Group=gvm
Environment=PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games:/usr/local/games:/opt/gvm/bin:/opt/gvm/sbin:/opt/gvm/.local/bin
Environment=PYTHONPATH=/opt/gvm/lib/python3.8/site-packages
ExecStart=/usr/bin/python3 /opt/gvm/bin/ospd-openvas \
--pid-file /opt/gvm/var/run/ospd-openvas.pid \
--log-file /opt/gvm/var/log/gvm/ospd-openvas.log \
--lock-file-dir /opt/gvm/var/run -u /opt/gvm/var/run/ospd.sock
RemainAfterExit=yes
[Install]
WantedBy=multi-user.target
EOLReload systemd service unit configurations.
systemctl daemon-reloadsystemctl start openvasCheck the status of the service;
systemctl status openvas● openvas.service - Control the OpenVAS service
Loaded: loaded (/etc/systemd/system/openvas.service; disabled; vendor preset: enabled)
Active: active (exited) since Mon 2021-02-08 18:26:16 UTC; 5s ago
Process: 9395 ExecStartPre=/usr/bin/rm -rf /opt/gvm/var/run/ospd-openvas.pid /opt/gvm/var/run/ospd.sock /opt/gvm/var/run/gvmd.sock (code=exited, status=0/SUCCESS)
Process: 9402 ExecStart=/usr/bin/python3 /opt/gvm/bin/ospd-openvas --pid-file /opt/gvm/var/run/ospd-openvas.pid --log-file /opt/gvm/var/log/gvm/ospd-openvas.log --lock>
Main PID: 9402 (code=exited, status=0/SUCCESS)
Tasks: 4 (limit: 3486)
Memory: 25.1M
CGroup: /system.slice/openvas.service
├─9406 /usr/bin/python3 /opt/gvm/bin/ospd-openvas --pid-file /opt/gvm/var/run/ospd-openvas.pid --log-file /opt/gvm/var/log/gvm/ospd-openvas.log --lock-file-di>
└─9408 /usr/bin/python3 /opt/gvm/bin/ospd-openvas --pid-file /opt/gvm/var/run/ospd-openvas.pid --log-file /opt/gvm/var/log/gvm/ospd-openvas.log --lock-file-di>
Feb 08 18:26:16 ubuntu20 systemd[1]: Starting Control the OpenVAS service...
Feb 08 18:26:16 ubuntu20 systemd[1]: Started Control the OpenVAS service.Enable OpenVAS scanner to run on system boot;
systemctl enable openvasCreate GSA systemd service Unit file
cat > /etc/systemd/system/gsa.service << 'EOL'
[Unit]
Description=Control the OpenVAS GSA service
After=openvas.service
[Service]
Type=simple
User=gvm
Group=gvm
Environment=PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games:/usr/local/games:/opt/gvm/bin:/opt/gvm/sbin:/opt/gvm/.local/bin
Environment=PYTHONPATH=/opt/gvm/lib/python3.8/site-packages
ExecStart=/usr/bin/sudo /opt/gvm/sbin/gsad
RemainAfterExit=yes
[Install]
WantedBy=multi-user.target
EOLcat > /etc/systemd/system/gsa.path << 'EOL'
[Unit]
Description=Start the OpenVAS GSA service when gvmd.sock is available
[Path]
PathChanged=/opt/gvm/var/run/gvmd.sock
Unit=gsa.service
[Install]
WantedBy=multi-user.target
EOLCreate GVM Systemd Service unit file
cat > /etc/systemd/system/gvm.service << 'EOL'
[Unit]
Description=Control the OpenVAS GVM service
After=openvas.service
[Service]
Type=simple
User=gvm
Group=gvm
Environment=PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games:/usr/local/games:/opt/gvm/bin:/opt/gvm/sbin:/opt/gvm/.local/bin
Environment=PYTHONPATH=/opt/gvm/lib/python3.8/site-packages
ExecStart=/opt/gvm/sbin/gvmd --osp-vt-update=/opt/gvm/var/run/ospd.sock
RemainAfterExit=yes
[Install]
WantedBy=multi-user.target
EOLcat > /etc/systemd/system/gvm.path << 'EOL'
[Unit]
Description=Start the OpenVAS GVM service when opsd.sock is available
[Path]
PathChanged=/opt/gvm/var/run/ospd.sock
Unit=gvm.service
[Install]
WantedBy=multi-user.target
EOLReload system unit configs and start the services;
systemctl daemon-reload
systemctl enable --now gvm.{path,service}
systemctl enable --now gsa.{path,service}Checking the status;
systemctl status gvm.{path,service}● gvm.path - Start the OpenVAS GVM service when opsd.sock is available
Loaded: loaded (/etc/systemd/system/gvm.path; enabled; vendor preset: enabled)
Active: active (waiting) since Mon 2021-02-08 18:35:51 UTC; 1min 50s ago
Triggers: ● gvm.service
Feb 08 18:35:51 ubuntu20 systemd[1]: Started Start the OpenVAS GVM service when opsd.sock is available.
● gvm.service - Control the OpenVAS GVM service
Loaded: loaded (/etc/systemd/system/gvm.service; enabled; vendor preset: enabled)
Active: active (exited) since Mon 2021-02-08 18:35:51 UTC; 1min 50s ago
TriggeredBy: ● gvm.path
Main PID: 9717 (code=exited, status=0/SUCCESS)
Tasks: 5 (limit: 3486)
Memory: 1.1G
CGroup: /system.slice/gvm.service
├─9745 gvmd: Waiting for incoming connections
├─9807 gpg-agent --homedir /opt/gvm/var/lib/gvm/gvmd/gnupg --use-standard-socket --daemon
├─9816 gvmd: Reloading NVTs
├─9817 gvmd: Syncing SCAP: Updating CPEs
└─9818 gvmd: OSP: Updating NVT cache
Feb 08 18:35:51 ubuntu20 systemd[1]: Started Control the OpenVAS GVM service.systemctl status gsa.{path,service}● gsa.path - Start the OpenVAS GSA service when gvmd.sock is available
Loaded: loaded (/etc/systemd/system/gsa.path; enabled; vendor preset: enabled)
Active: active (running) since Mon 2021-02-08 18:35:52 UTC; 1min 53s ago
Triggers: ● gsa.service
Feb 08 18:35:52 ubuntu20 systemd[1]: Started Start the OpenVAS GSA service when gvmd.sock is available.
● gsa.service - Control the OpenVAS GSA service
Loaded: loaded (/etc/systemd/system/gsa.service; enabled; vendor preset: enabled)
Active: active (exited) since Mon 2021-02-08 18:30:37 UTC; 7min ago
TriggeredBy: ● gsa.path
Main PID: 9533 (code=exited, status=0/SUCCESS)
Tasks: 4 (limit: 3486)
Memory: 3.2M
CGroup: /system.slice/gsa.service
├─9552 /opt/gvm/sbin/gsad
└─9553 /opt/gvm/sbin/gsad
Feb 08 18:30:37 ubuntu20 systemd[1]: Started Control the OpenVAS GSA service.
Feb 08 18:30:37 ubuntu20 sudo[9533]: gvm : TTY=unknown ; PWD=/ ; USER=root ; COMMAND=/opt/gvm/sbin/gsad
Feb 08 18:30:37 ubuntu20 sudo[9533]: pam_unix(sudo:session): session opened for user root by (uid=0)
Feb 08 18:30:37 ubuntu20 sudo[9544]: Oops, secure memory pool already initialized
Feb 08 18:30:37 ubuntu20 sudo[9533]: pam_unix(sudo:session): session closed for user rootCreate GVM Scanner
Since we launched the scanner and set it to use our non-standard scanner host path (/opt/gvm/var/run/ospd.sock), we need to create and register our scanner;
sudo -Hiu gvm gvmd --create-scanner="Kifarunix-demo OpenVAS Scanner" --scanner-type="OpenVAS" --scanner-host=/opt/gvm/var/run/ospd.sockNext, you need to verify your scanner. For this, you first need to get the scanner identifier;
sudo -Hiu gvm gvmd --get-scanners08b69003-5fc2-4037-a479-93b440211c73 OpenVAS /var/run/ospd/ospd.sock 0 OpenVAS Default
6acd0832-df90-11e4-b9d5-28d24461215b CVE 0 CVE
50afbf2b-d854-4b6d-879f-c62aa62254d2 OpenVAS /opt/gvm/var/run/ospd.sock 9390 Kifarunix-demo OpenVAS ScannerBased on the output above, our scanner UUID is, 50afbf2b-d854-4b6d-879f-c62aa62254d2.
Verify the scanner;
sudo -Hiu gvm gvmd --verify-scanner=50afbf2b-d854-4b6d-879f-c62aa62254d2Command output;
Scanner version: OpenVAS 20.8.2.Create OpenVAS (GVM) Admin User
Create OpenVAS administrative user by running the command below;
sudo -Hiu gvm gvmd --create-user adminThis command generates a random password for the user. See sample output below;
User created with password 'fee42e66-117c-42f8-9b48-429e51194a13'.If you want to create a user and at the same time create your own password;
sudo -Hiu gvm gvmd --create-user gvmadmin --password=StronGP@SSOtherwise, you can reset the password of an already existing user;
sudo -Hiu gvm gvmd --user=<USERNAME> --new-password=<PASSWORD>An administrator user can later create further users or administrators via clients like the Greenbone Security Assistant (GSA).
Set the Feed Import Owner
According to gvmd/INSTALL.md, certain resources that were previously part of the gvmd source code are now shipped via the feed. An example is the config “Full and Fast”.
gvmd will only create these resources if a “Feed Import Owner” is configured:
sudo -Hiu gvm gvmd --modify-setting 78eceaec-3385-11ea-b237-28d24461215b --value <uuid_of_user>The UUIDs of all created users can be found using
sudo -Hiu gvm gvmd --get-users --verboseSample output;
admin 9a9e5070-d2f0-4802-971e-c9d61e682c21Then modify the gvmd settings with the user UUID.
sudo -Hiu gvm gvmd --modify-setting 78eceaec-3385-11ea-b237-28d24461215b --value 9a9e5070-d2f0-4802-971e-c9d61e682c21GVM Log Files
Various Log files are located under the /opt/gvm/var/log/gvm directory.
ls /opt/gvm/var/log/gvmgsad.log gvmd.log openvas.log ospd-openvas.logAccessing GVM 20.08 (OpenVAS)
Greenbone Security Assistant (GSA) WebUI daemon opens port 443 and listens on all interfaces. If firewall is running, open this port to allow external access.
ufw allow 443/tcpYou can now access GSA via the url https:<serverIP-OR-hostname>. Accept the self-signed SSL warning and proceed.
Login with the administrative credentials generated above.
Port lists
And there you go. That is all it take to install and Setup GVM. You can now start running your scans.
NOTE: When creating a scan task, be sure to select the Scanner we created above.
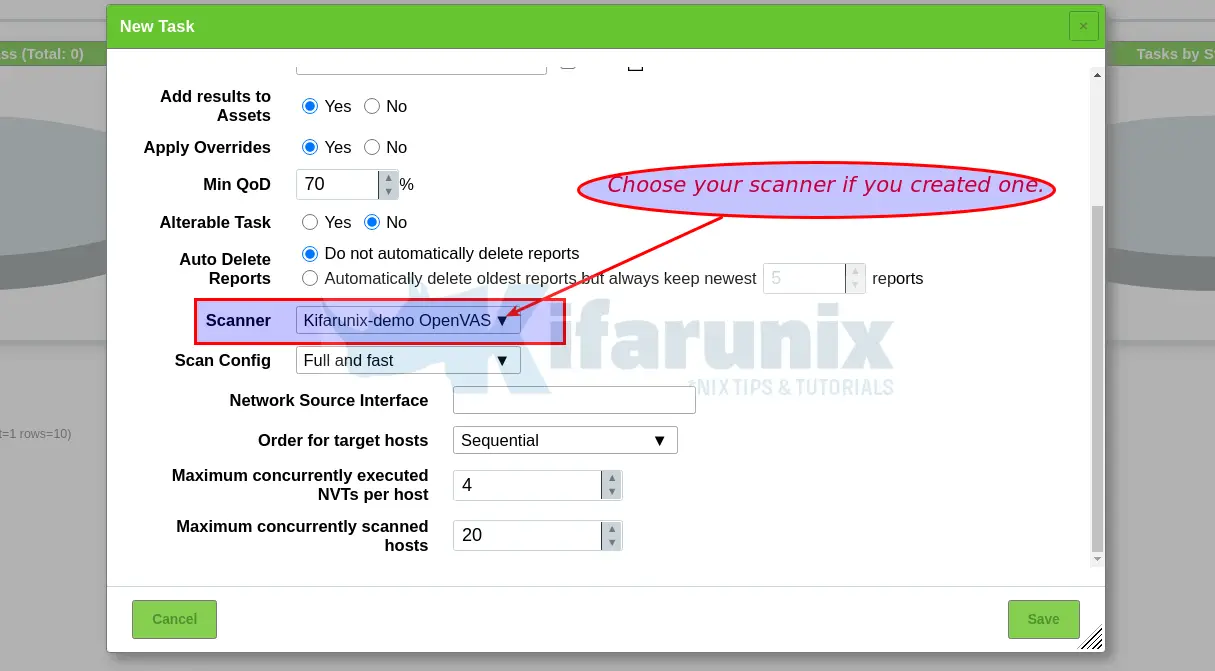
You can now create your target hosts to scan and schedule the scans to run at your own preferred time.
That marks the end of our tutorial on how to install and setup GVM.
Did I miss anything, drop it in the comments section!! Enjoy
Reference
Source files README.md and INSTALL.md files
Related Tutorials
Install OpenVAS 10 (GVM) on Debian 10 Buster
Install OpenVAS 9 with PostgreSQL in Ubuntu 18.04
How to Add and Scan a Target for Vulnerabilities on OpenVAS Scanner
How to Install and Setup OpenVAS 9 Vulnerability Scanner on Ubuntu 18.04
How to Install and Use WPScan WordPress Vulnerability Scanner Ubuntu 18.04


Hey, thanks for this. It was critical in helping me get this running.
A couple of notes from my experience:
1. I got an error (“/usr/bin/ld: cannot find -lunistring”) at one point and needed the libunistring-dev package. Install with apt and retrying the make fixed that.
2. In your instructions for the install of openvas has directory /opt/gvm/ospd-openvas, but the correct directory is /opt/gvm/gvm-source/ospd-openvas.
Thanks again for this resource. Huge help!
Thanks for the feedback Ron, updates as per feedback made.
Yeeeaah, thank you 😀
I have created user but i am getting error at this point
“sudo -Hiu gvm gvmd –get-users –verbose” not getting the output. im not getting UUID of user
” sudo -Hiu gvm gvmd –get-users –verbose ” — This command gives nothing. I cant login
Great guide, thank you!
Could you confirm, the commands that should be run in a cron job to keep everything up to date are:
sudo runuser -u _gvm — greenbone-nvt-sync
sudo runuser -u _gvm — greenbone-feed-sync –type SCAP
sudo runuser -u _gvm — greenbone-feed-sync –type CERT
sudo runuser -u _gvm — greenbone-feed-sync –type GVMD_DATA
Did I miss anything else?
that is pretty much it.
Run it as what user though? gvm or root? If gvm, they will not work.
Hi, i tried to install it on debian buster but after
“systemctl start openvas.service” i get this error.
pkg_resources.DistributionNotFound: The ‘ospd-openvas==20.8.2.dev1’ distribution was not found and is required by the application
Try this debian 10 guide.
Could anyone please look at the following issue we raised on the Greenbone forums, we seem to be having issues with reports.
https://community.greenbone.net/t/failed-to-find-report-format-a994b278-1f62-11e1-96ac-406186ea4fc5/8662
Is there any way to scan another computer that is in a different network environment?
Yes, as long as there is network connection between the network on which you scanner is located and the other computer network, then it is as simple as creating the scan and running it
Thanks for this detailed description!
I got it up and running, but if i start scanning a host with the wizard it stops at 0% with:
Could not connect to Scanner
Interrupting scan because GVM is exiting.
But all services are up and running. Any idea what the problem might be?
When creating a target, better use “Consider Alive” for “Alive Test”. It will not depend of ICMP.
Hi,
thank you for your work.
I’ve tryied it out but i’m stuck on Create GVM Scanner.
When I try
sudo -Hiu gvm gvmd –get-scanners
I get no results but I don’t understand where there’s the problem.
can you advise?
thank you
Thanks for sharing this extremely nice document. I have one issue with scanners:) and with this row
sudo -Hiu gvm gvmd –modify-setting 78eceaec-3385-11ea-b237-28d24461215b –value 9a9e5070-d2f0-4802-971e-c9d61e682c21
I got always error:
Error in setting UUID
Any idea for this one?
Hi there.
Did you confirm you are using the right scanner UUID?
Hi Koromicha,
Having a problem trying to create the GVM Scanner; the OS doesn’t seem to think root, or even gvm, has access to the clientkey.pem file, though I can prove it does have in the ls -la output below:
root@openvas:~# sudo -Hiu gvm gvmd –create-scanner=”Kifarunix-demo OpenVAS Scanner” –scanner-type=”OpenVAS” –scanner-host=/opt/gvm/var/run/ospd.sock
Failed to open file “/opt/gvm/var/lib/gvm/private/CA/clientkey.pem”: Permission denied.
root@openvas:~# ls -la /opt/gvm/var/lib/gvm/private/CA/
total 32
drwx—— 2 root root 4096 Apr 13 10:50 .
drwxr-xr-x 3 root root 4096 Apr 13 10:50 ..
-rwxrwxrwx 1 root root 8170 Apr 13 10:50 cakey.pem
-rwxrwxrwx 1 root root 8170 Apr 13 10:50 clientkey.pem
-rwxrwxrwx 1 root root 8170 Apr 13 10:50 serverkey.pem
When changing ownership of these .pem files, I get the same error:
root@openvas:~# sudo -Hiu gvm gvmd –create-scanner=”Kifarunix-demo OpenVAS Scanner” –scanner-type=”OpenVAS” –scanner-host=/opt/gvm/var/run/ospd.sock
Failed to open file “/opt/gvm/var/lib/gvm/private/CA/clientkey.pem”: Permission denied.
root@openvas:~# ls -la /opt/gvm/var/lib/gvm/private/CA/
total 32
drwx—— 2 root root 4096 Apr 13 10:50 .
drwxr-xr-x 3 root root 4096 Apr 13 10:50 ..
-rwxrwxrwx 1 gvm gvm 8170 Apr 13 10:50 cakey.pem
-rwxrwxrwx 1 gvm gvm 8170 Apr 13 10:50 clientkey.pem
-rwxrwxrwx 1 gvm gvm 8170 Apr 13 10:50 serverkey.pem
Any assistance or feedback would be greatly appreciated.
Hi Tiaan, can you try to set the ownership of /opt/gvm directory to gvm user and check?
I see there is a new High Vulnerability, as new GVM is released. As it is not enough to download only feeds, how to update it correctly?
I would like to skip this one:
High (CVSS: 10.0)
NVT: Report outdated / end-of-life Scan Engine / Environment (local)
Vulnerability Detection Result
Installed GVM Libraries (gvm-libs) version: 20.8.0
Latest available GVM Libraries (gvm-libs) version: 20.8.1
Reference URL(s) for the latest available version: https://community.greenbone.n
,!et/t/gvm-20-08-stable-initial-release-2020-08-12/6312
Thanks in advance for your help here
hello, really nice tutorial. I thought I would be clever and use the git branch “21.04” instead of “20.08”.
I got fairly far in the process. but Im encountering an error. I was hoping you might have some insight on how to correct? I am in the section to set up the cron jobs to keep the feeds updated.
I get this error. any ideas on how to properly set permissions? where to look? thank you
gvm@greenbone:~$ whoami
gvm
gvm@greenbone:~$ sudo -Hiu gvm greenbone-feed-sync –type GVMD_DATA
Sorry, user gvm is not allowed to execute ‘/bin/bash -c greenbone-feed-sync –type GVMD_DATA’ as gvm on greenbone.
gvm@greenbone:~$
update. I deleted my VM and started over, using xubuntu 20.04. 🙂 and followed this tutorial. exactly.
and there is a weird problem. I run this command
pip_search ospd
and it shows these versions.
ospd-openvas │ 21.4.0
ospd │ 21.4.0
ospd-openvas –help fails with this error.
pkg_resources.DistributionNotFound: The ‘ospd-openvas==20.8.3.dev1’ distribution was not found and is required by the application
how is 21.4.0 getting installed?
greenbone-nvt-sync command always throws an error that connecting to dl.greenbone.net is not reachable while installing GVM 20.08.
Please someone guide me here.
did you try adding –rsync option?