In this guide, we are going to learn how to install OSSEC agent on Mac OS X.
Table of Contents
Installing OSSEC Agent on Mac OS X
Well as usual, we are going to install OSSEC agent on Mac OS X from the source code. As a result ensure that you have C compiler (gcc) installed.
Check if GCC Compile is Available
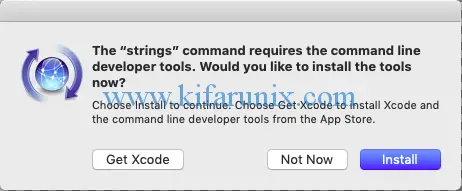
To verify that the the GNU Compiler collection is installed, run the command below;
which gcc/usr/bin/gccIf, however, you are prompted to install the developer tools during OSSEC agent installation, please do install and proceed with installation.
Download OSSEC Agent Tarball
Next, download OSSEC agent for Unix from the downloads page.
wget https://github.com/ossec/ossec-hids/archive/3.7.0.tar.gzExtract OSSEC Agent Tarball
Once the download completes, extract the source archive.
tar xzf 3.7.0.tar.gzInstall OSSEC Agent on Mac OS
Navigate to extracted source directory and run the OSSEC install script.
cd ossec-hids-3.7.0/./install.shWhen the install script runs, you will be prompted to choose the installation language. In this case, English is chosen.
...
(en/br/cn/de/el/es/fr/hu/it/jp/nl/pl/ru/sr/tr) [en]:
enPress Enter again to proceed with the installation. Choose agent as the type of installation.
1- What kind of installation do you want (server, agent, local, hybrid or help)?
agent
- Agent(client) installation chosen.Select /var/ossec as the installation directory for OSSEC.
2- Setting up the installation environment.
- Choose where to install the OSSEC HIDS [/var/ossec]:
- Installation will be made at /var/ossec .Set the IP address of the OSSEC server. This can be OSSEC server itself or the AlienVault.
3- Configuring the OSSEC HIDS.
3.1- What's the IP Address or hostname of the OSSEC HIDS server?:
192.168.43.22
- Adding Server IP 192.168.43.22Enable system integrity check.
3.2- Do you want to run the integrity check daemon? (y/n) [y]:
y
- Running syscheck (integrity check daemon).Enable Rootkit detection.
3.3- Do you want to run the rootkit detection engine? (y/n) [y]:
y
- Running rootcheck (rootkit detection).Disable active response
3.4 - Do you want to enable active response? (y/n) [y]:
n
- Active response disabled.3.5- Setting the configuration to analyze the following logs:
-- /var/log/system.log
- If you want to monitor any other file, just change
the ossec.conf and add a new localfile entry.
Any questions about the configuration can be answered
by visiting us online at http://www.ossec.net .
--- Press ENTER to continue ---If the installation is successful, you should the output stating that configuration finished properly.
- Configuration finished properly.
- To start OSSEC HIDS:
/var/ossec/bin/ossec-control start
- To stop OSSEC HIDS:
/var/ossec/bin/ossec-control stop
- The configuration can be viewed or modified at /var/ossec/etc/ossec.conf
Thanks for using the OSSEC HIDS.
If you have any question, suggestion or if you find any bug,
contact us at [email protected] or using our public maillist at
[email protected]
( http://www.ossec.net/main/support/ ).
More information can be found at http://www.ossec.net
--- Press ENTER to finish (maybe more information below). ---
- You first need to add this agent to the server so they
can communicate with each other. When you have done so,
you can run the 'manage_agents' tool to import the
authentication key from the server.
/var/ossec/bin/manage_agents
More information at:
http://www.ossec.net/en/manual.html#ma
Connect OSSEC Agent to OSSEC Server
Once the installation is done, add the agent to the server to ensure that they can communicate. After that extract the agent-server key and import. Run the command below to install the key on the agent.
/var/ossec/bin/manage_agentsPress I to import the key. Paste the key and press Enter to add it.
****************************************
* OSSEC HIDS v3.7.0 Agent manager. *
* The following options are available: *
****************************************
(I)mport key from the server (I).
(Q)uit.
Choose your action: I or Q: I
* Provide the Key generated by the server.
* The best approach is to cut and paste it.
*** OBS: Do not include spaces or new lines.
Paste it here (or '\q' to quit): OTYgbHVhbmRtaSAxOTIuMTY4LjM1LjEwOCA2NzA4N2ZmNjhiZDhjZGQ3NjgwMjlhODA0ZmNjMzQyOTUyODE0YTM1NTdhNjRkOWIxNGFhNDljYTJhOTJhNzhh
If all is well, you should be able to see the details of the agent as is on the server.
Agent information:
ID:96
Name:macosx
IP Address:192.168.43.108Type y and Press Enter to confirm adding the key.
Confirm adding it?(y/n): y
Added.
** Press ENTER to return to the main menu.
****************************************
* OSSEC HIDS v3.7.0 Agent manager. *
* The following options are available: *
****************************************
(I)mport key from the server (I).
(Q)uit.
Choose your action: I or Q: q
** You must restart OSSEC for your changes to take effect.
manage_agents: Exiting.
Start OSSEC Agent on Mac OS
Next start OSSEC agent service.
/var/ossec/bin/ossec-control startStarting OSSEC HIDS v3.7.0...
Started ossec-execd...
2023/05/30 17:00:57 ossec-agentd: INFO: Using notify time: 600 and max time to reconnect: 1800
Started ossec-agentd...
Started ossec-logcollector...
Started ossec-syscheckd...
Completed.To verify that the agent has started and connected to the server, tail the OSSEC agent logs. You should be able to see a line stating that the agent is connected to the server.
tail /var/ossec/logs/ossec.log | grep -i connected2023/05/23 17:06:58 INFO: Connected to 192.168.43.22 at address 192.168.43.22, port 1514
2023/05/23 17:23:54 INFO: Connected to 192.168.43.22 at address 192.168.43.22, port 1514That is all.
Configure OSSEC Agent to Run on System Boot
Now to ensure that the service runs in case the system reboots, create a start up service as shown below;
vim /Library/LaunchDaemons/autostartossec.plist
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>Label</key>
<string>autostartossec</string>
<key>ProgramArguments</key>
<array>
<string>/Users/kifarunix/myscripts/autostartossec.sh</string>
</array>
<key>RunAtLoad</key>
<true/>
<key>StandardErrorPath</key>
<string>/var/ossec/logs/ossec.err</string>
<key>StandardOutPath</key>
<string>/var/ossec/logs/ossec.out</string>
</dict>
</plist>
The lauch daemon is created. Next create the service startup script.
vim /Users/kifarunix/myscripts/autostartossec.sh#!/bin/sh
/var/ossec/bin/ossec-control startMake the script executable.
chmod u+x /Users/kifarunix/myscripts/autostartossec.shTo test if this works, reboot the system and check the status of OSSEC agent.
/var/ossec/bin/ossec-control statusossec-logcollector is running...
ossec-syscheckd is running...
ossec-agentd is running...
ossec-execd not running...The service should now running. Great and congratulations.
Other Tutorials
We have covered similar setups in our other guides. You can check them by following the links below;
How to Install OSSEC Agent on Solaris 11.4
How to Install and Setup OSSEC agent on Ubuntu 18.04/CentOS 7
How to Install and Setup AlienVault HIDS Agent on a Windows Host
How to Install and Configure AlienVault HIDs Agent on a Linux Host


Nice writeup. I did one last year, and ran into an issue on the platform we were using, so you may want to add that as a prerequisite, xcode tools need to be installed in some cases:
Xcode-select –install. That may have covered your gcc though.
I also found a useful removal command:
/var/ossec/bin/ossec-control stop && rm -rf /var/ossec && rm /etc/init.d/*ossec* && rm /etc/ossec-init.conf
Your writeup is great, especially one startup scripts. I am having trouble where the agent won’t keep running, I will see if the startup scripts help.
Thank you Ryan and thanks for sharing this.
Please try the startup script and let us know if it works for you.