Hello folks, welcome to this very tutorial on how to create locally trusted SSL certificates with mkcert on Ubuntu 18.04. mkcert is a simple zero-config tool that is used to make locally trusted development certificates. It automatically creates and installs a local CA in the system root store, and generates locally-trusted certificates.
Creating Locally Trusted SSL Certificates with mkcert
Installing mkcert on Ubuntu
As a prerequisite, you are required to install certutil, a command-line utility that can create and modify certificate and key databases before you can install mkcert utility.
sudo apt install libnss3-tools -yOnce the installation of certutil is done, download the current version of mkcert pre-built binary from Github releases page.
As of this writing, the current version of mkcert is v1.4.3
So download the current version and install it as shown below
wget https://github.com/FiloSottile/mkcert/releases/download/v1.4.3/mkcert-v1.4.3-linux-amd64sudo cp mkcert-v1.4.3-linux-amd64 /usr/local/bin/mkcert
sudo chmod +x /usr/local/bin/mkcert
Generate Local CA on Ubuntu
Now that the mkcert utility is installed, run the command below to generate your local CA.
mkcert -installThe local CA is now installed in the system trust store! ⚡️
The local CA is now installed in the Firefox and/or Chrome/Chromium trust store (requires browser restart)! 🦊The root CA is stored under #HOME/.local/share/mkcert.
You can print the location directory of the root CA path by running the command below.
mkcert -CAROOT
/home/amos/.local/share/mkcertIf you encounter the error:
ERROR: no Firefox and/or Chrome/Chromium security databases foundJust launch the browsers and re-run the install command.
Creating Locally Trusted SSL Certificates with mkcert
Now that you have your local CA, run the command below to generate local SSL certificates using mkcert command.
mkcert kifarunix-demo.com '*.kifarunix-demo.com' localhost 127.0.0.1 ::1
Sample command output;
Created a new certificate valid for the following names 📜
- "kifarunix-demo.com"
- "*.kifarunix-demo.com"
- "localhost"
- "127.0.0.1"
- "::1"
Reminder: X.509 wildcards only go one level deep, so this won't match a.b.kifarunix-demo.com ℹ️
The certificate is at "./kifarunix-demo.com+4.pem" and the key at "./kifarunix-demo.com+4-key.pem" ✅
It will expire on 31 August 2023 🗓
You have the certificate and key in the current working directory;
ls -1 ./kifarunix-demo.com+* ./kifarunix-demo.com+4-key.pem
./kifarunix-demo.com+4.pemEnable Web Server HTTPS using the Certificates
The certificates are now installed and it is time to enable your webserver to use them for HTTPS connections.
To configure Apache to use these certificates, edit the default ssl configuration file, /etc/apache2/sites-available/default-ssl.conf and change the SSL certificate and key file to point to the locally generated cert and key file above.
See the example below. Note the certificates are in my home directory.
Be sure to replace the paths accordingly.
sudo sed -i 's#/etc/ssl/certs/ssl-cert-snakeoil.pem#/home/koromicha/kifarunix-demo.com+4.pem#; s#/etc/ssl/private/ssl-cert-snakeoil.key#/home/koromicha/kifarunix-demo.com+4-key.pem#' /etc/apache2/sites-available/default-ssl.conf
To verify this;
grep -E "SSLCertificateFile|SSLCertificateKeyFile" /etc/apache2/sites-available/default-ssl.conf # SSLCertificateFile directive is needed.
SSLCertificateFile /home/koromicha/kifarunix-demo.com+4.pem
SSLCertificateKeyFile /home/koromicha/kifarunix-demo.com+4-key.pem
# the referenced file can be the same as SSLCertificateFileEnable Apache to use SSL by loading the ssl modules;
sudo a2enmod ssl
sudo a2ensite default-ssl.confReload and restart Apache to activate the new configuration
sudo systemctl restart apache2Verify Local SSL Certs generated with mkcert
Navigate to the browser and try to access your domain.
I am using local hosts file for my DNS entries.
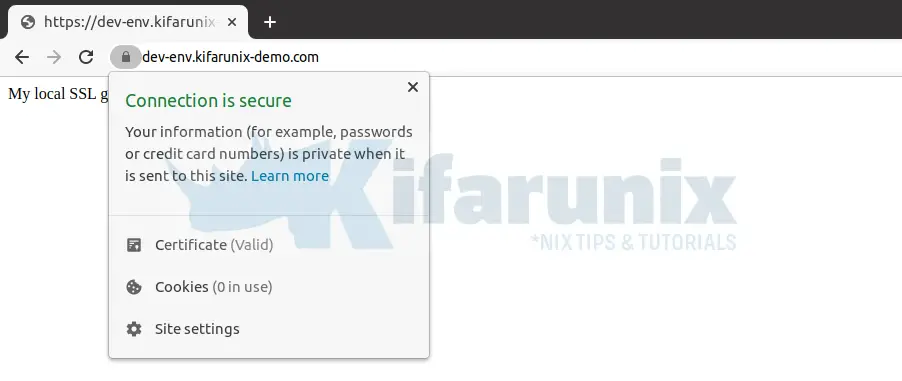
Enable the Certificates for Nginx Web Server
Create your web page configuration as shown below.
Replace the paths to the ceritificate and key accordingly
vim /etc/nginx/sites-available/example.com
server {
listen 80;
listen 443 ssl;
ssl on;
ssl_certificate /home/koromicha/kifarunix-demo.com+4.pem;
ssl_certificate_key /home/koromicha/kifarunix-demo.com+4-key.pem;
server_name example.com;
location / {
root /var/www/html/example;
index index.html;
}
}
Verify that the configuration has no error.
nginx -t
nginx: the configuration file /etc/nginx/nginx.conf syntax is ok
nginx: configuration file /etc/nginx/nginx.conf test is successfulRestart Nginx
systemctl restart nginxNavigate to the browser and test your ssl for your domain.
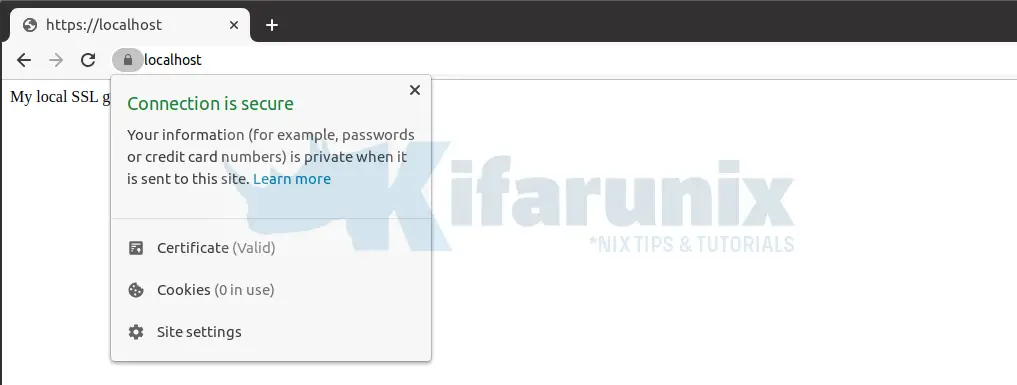
Well, seems up-to that far everything is fine.
And that concludes our guide on how to create locally trusted SSL certificates with mkcert on Ubuntu 18.04.
More mkcert usage information.
mkcert --helpOther Tutorials
Configure Nginx with SSL/TLS certificates on CentOS 8
Monitor SSL/TLS Certificate Expiry with Prometheus and Grafana


Thanks for the article.
I successfully walked through all steps, but my browser writes “Certificate invalid”.
I use Chrome 90 on Ubuntu 20.04
Sounds like you have not installed the local CA. Check the guide create ssl certs with mkcert ubuntu 20.04.