This guide will take you through how to install and configure SSSD for LDAP authentication on Ubuntu 22.04. SSSD (System Security Services Daemon) is a system service to access remote directories and authentication mechanisms such as an LDAP directory, an Identity Management (IdM) or Active Directory (AD) domain, or a Kerberos realm.
Table of Contents
Configure SSSD for LDAP Authentication on Ubuntu 22.04
Assuming you already have a running OpenLDAP server, proceed with this guide to learn how to install and configure SSSD for LDAP authentication.
Run System Update
Ensure that your system package cache is up-to-date.
apt updateInstall SSSD on Ubuntu 22.04
To install SSSD and other required SSSD tools on Ubuntu 22.04, run the command below;
apt install sssd libpam-sss libnss-sss sssd-toolsConfigure SSSD for OpenLDAP Authentication on Ubuntu 22.04
Create SSSD configuration file
SSSD do not ship with any configuration file by default. As such, you need to create your configuration file that defines your LDAP authentication specifics.
Below is our sample configuration options;
cat > /etc/sssd/sssd.conf << 'EOL'
[sssd]
services = nss, pam
config_file_version = 2
domains = default
[nss]
[pam]
offline_credentials_expiration = 60
[domain/default]
ldap_id_use_start_tls = True
cache_credentials = True
ldap_search_base = dc=ldapmaster,dc=kifarunix-demo,dc=com
id_provider = ldap
auth_provider = ldap
chpass_provider = ldap
access_provider = ldap
ldap_uri = ldap://ldapmaster.kifarunix-demo.com
ldap_default_bind_dn = cn=readonly,ou=system,dc=ldapmaster,dc=kifarunix-demo,dc=com
ldap_default_authtok = P@ssWOrd
ldap_tls_reqcert = demand
ldap_tls_cacert = /etc/ssl/certs/ldapcacert.crt
ldap_tls_cacertdir = /etc/ssl/certs
ldap_search_timeout = 50
ldap_network_timeout = 60
ldap_access_order = filter
ldap_access_filter = (objectClass=posixAccount)
EOL
Check the highlighted lines above and replace their values appropriately.
You can also update your access filters.
For a comprehensive description of options used above, refer to man sssd.conf and man sssd-ldap.
Once you are done with your configurations, save and exit the file.
Install OpenLDAP Server CA Certificate on Ubuntu 22.04 LDAP client
SSSD authentication can only work over an encrypted communication channel. Therefore, your OpenLDAP server must be configured SSL/TLS.
If you have done this already, download the CA certificate from the LDAP server to the LDAP client by executing the command below;
openssl s_client -connect ldapmaster.kifarunix-demo.com:636 -showcerts < /dev/null | openssl x509 -text | sed -ne '/-BEGIN CERTIFICATE-/,/-END CERTIFICATE-/p'if you are downloading the certificates from an OpenLDAP server listening on STARTTLS (port 389/{tcp,udp}), use the command below instead;
openssl s_client -connect ldapmaster.kifarunix-demo.com:389 -starttls ldap -showcerts < /dev/null | openssl x509 -text | sed -ne '/-BEGIN CERTIFICATE-/,/-END CERTIFICATE-/p'Copy the certificate part;
-----BEGIN CERTIFICATE-----
MIIDvzCCAqegAwIBAgIUc8imlOVhEej453dXtvacn7krg1MwDQYJKoZIhvcNAQEL
BQAwbzELMAkGA1UEBhMCS0UxDDAKBgNVBAgMA05haTEMMAoGA1UEBwwDTWFpMRww
GgYDVQQKDBNEZWZhdWx0IENvbXBhbnkgTHRkMSYwJAYDVQQDDB1sZGFwbWFzdGVy
...
...
ExJaMa6cJkIFmepJ6wGvk33DiLRZrAKT2/11yswYm16mdpUynmx6pZvZizjxkq+c
hegnowyEG4db/NktY44v2ryIQdEclnKmhk23vmhgZxl1IUgev2tc//JWPE9dXuP8
Uy7ivNi2PL6mBwxMpyi0zTopqTXSvi54APm48dd0JPsGLTIgPMc1WvaN7TsUeIBs
Igf9K1e9M0Q+j2XEsTeCYVU/v0Jt0kER0+V/NM0IrDOX+6kRz6DNsZrwcMEf5Yvp
ARWZ
-----END CERTIFICATE-----
As per our SSSD configuration, the LDAP CA certificate file is stored as /etc/ssl/certs/ldapcacert.crt on the client. Note that the location of the CA cert file might be different for your case.
Therefore, copy the certificate above and place it in this file;
vim /etc/ssl/certs/ldapcacert.crt-----BEGIN CERTIFICATE-----
MIIDvzCCAqegAwIBAgIUc8imlOVhEej453dXtvacn7krg1MwDQYJKoZIhvcNAQEL
BQAwbzELMAkGA1UEBhMCS0UxDDAKBgNVBAgMA05haTEMMAoGA1UEBwwDTWFpMRww
GgYDVQQKDBNEZWZhdWx0IENvbXBhbnkgTHRkMSYwJAYDVQQDDB1sZGFwbWFzdGVy
...
...
ExJaMa6cJkIFmepJ6wGvk33DiLRZrAKT2/11yswYm16mdpUynmx6pZvZizjxkq+c
hegnowyEG4db/NktY44v2ryIQdEclnKmhk23vmhgZxl1IUgev2tc//JWPE9dXuP8
Uy7ivNi2PL6mBwxMpyi0zTopqTXSvi54APm48dd0JPsGLTIgPMc1WvaN7TsUeIBs
Igf9K1e9M0Q+j2XEsTeCYVU/v0Jt0kER0+V/NM0IrDOX+6kRz6DNsZrwcMEf5Yvp
ARWZ
-----END CERTIFICATE-----
Verify the validity of the certificate;
openssl s_client -connect ldapmaster.kifarunix-demo.com:389 -CAfile /etc/ssl/certs/ldapcacert.crtIf you get, Verification: OK or Verify return code: 0 (ok) on the command output, then you are all set.
Next, open the /etc/ldap/ldap.conf and replace the value of TLS_CACERT with the path to the CA certificate created above.
vim /etc/ldap/ldap.conf...
# TLS certificates (needed for GnuTLS)
#TLS_CACERT /etc/ssl/certs/ca-certificates.crt
TLS_CACERT /etc/ssl/certs/ldapcacert.crtSave and close the configuration file.
Set Proper Permissions and Ownership on SSSD configurations
After that, assign the root user read/write access to /etc/sssd/.
chmod 600 -R /etc/sssd
chown -R root: /etc/sssdPerform static analysis of SSSD configuration to check if any error;
sssctl config-checkRestart SSSD service
systemctl restart sssdCheck the status of SSSD to ensure that it is running.
systemctl status sssd
● sssd.service - System Security Services Daemon
Loaded: loaded (/lib/systemd/system/sssd.service; enabled; vendor preset: enabled)
Active: active (running) since Fri 2022-03-25 19:39:39 EAT; 5min ago
Main PID: 627 (sssd)
Tasks: 4 (limit: 2306)
Memory: 15.3M
CPU: 662ms
CGroup: /system.slice/sssd.service
├─ 627 /usr/sbin/sssd -i --logger=files
├─ 965 /usr/libexec/sssd/sssd_be --domain default --uid 0 --gid 0 --logger=files
├─1027 /usr/libexec/sssd/sssd_nss --uid 0 --gid 0 --logger=files
└─1028 /usr/libexec/sssd/sssd_pam --uid 0 --gid 0 --logger=files
Mac 25 19:38:30 ubuntu2204 systemd[1]: Starting System Security Services Daemon...
Mac 25 19:38:50 ubuntu2204 sssd[627]: Starting up
Mac 25 19:39:23 ubuntu2204 sssd_be[965]: Starting up
Mac 25 19:39:30 ubuntu2204 sssd_nss[1027]: Starting up
Mac 25 19:39:30 ubuntu2204 sssd_pam[1028]: Starting up
Mac 25 19:39:39 ubuntu2204 systemd[1]: Started System Security Services Daemon.
Mac 25 19:40:50 ubuntu2204 sssd_be[965]: Backend is online
Enable SSSD to run on system boot;
systemctl enable sssdConfigure Auto-Home Directory Creation
To enable automatic creation of user’s home directory on first login, you need to configure the PAM modules (pam_mkhomedir.so) as shown below.
Open the /etc/pam.d/common-session configuration file and edit is ad follows;
vim /etc/pam.d/common-sessionAdd the line;
session required pam_mkhomedir.so skel=/etc/skel/ umask=0022just below the line;
session optional pam_sss.soSuch that it look like;
...
# The pam_umask module will set the umask according to the system default in
# /etc/login.defs and user settings, solving the problem of different
# umask settings with different shells, display managers, remote sessions etc.
# See "man pam_umask".
session optional pam_umask.so
# and here are more per-package modules (the "Additional" block)
session required pam_unix.so
session optional pam_sss.so
session required pam_mkhomedir.so skel=/etc/skel/ umask=0022
session optional pam_systemd.so
# end of pam-auth-update config
...
Save and exit the configuration file.
Verify SSSD OpenLDAP authentication
The installation and configuration of SSSD is done.
To verify that you can login, try to authenticate against your LDAP server.
In this guide, we have two users, janedoe and johndoe, created on our OpenLDAP Server for demo purposes.
The command below is ran on my LDAP Server;
ldapsearch -H ldapi:/// -Y EXTERNAL -b "ou=people,dc=ldapmaster,dc=kifarunix-demo,dc=com" dn -LLL -QSample Output;
dn: ou=people,dc=ldapmaster,dc=kifarunix-demo,dc=com
dn: uid=janedoe,ou=people,dc=ldapmaster,dc=kifarunix-demo,dc=com
dn: uid=johndoe,ou=people,dc=ldapmaster,dc=kifarunix-demo,dc=com
These information about the users above should now be printable on the Ubuntu 22.04 ldap client.
root@ubuntu2204:~# id johndoeuid=10000(johndoe) gid=10000(johndoe) groups=10000(johndoe)root@ubuntu20:~# id janedoeuid=10010(janedoe) gid=10010(janedoe) groups=10010(janedoe)To demonstrate the SSSD LDAP authentication, we will use both SSH and GUI based authentication;
Verify SSH Authentication via OpenLDAP SSSD
ssh johndoe@ubuntu2204
The authenticity of host 'ubuntu2204 (192.168.59.38)' can't be established.
ECDSA key fingerprint is SHA256:Wx4prraXmi5rdkjbgXGXixeToBXCuIpTSE6Tw5nGQJ0.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'ubuntu2204' (ECDSA) to the list of known hosts.
johndoe@ubuntu2204's password:
Creating directory '/home/johndoe'.
Welcome to Ubuntu Jammy Jellyfish (development branch) (GNU/Linux 5.15.0-18-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
481 updates can be applied immediately.
To see these additional updates run: apt list --upgradable
Your Hardware Enablement Stack (HWE) is supported until April 2025.
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
Last login: Fri Mar 25 19:55:03 2022 from 192.168.59.1
johndoe@ubuntu2204:~$
Verify GUI authentication via OpenLDAP SSSD
Reboot your Ubuntu 22.04 desktop after SSSD setup and and verify authentication.
Once it boots, on the GDM login interface, click Not listed to enter your OpenLDAP username and password.
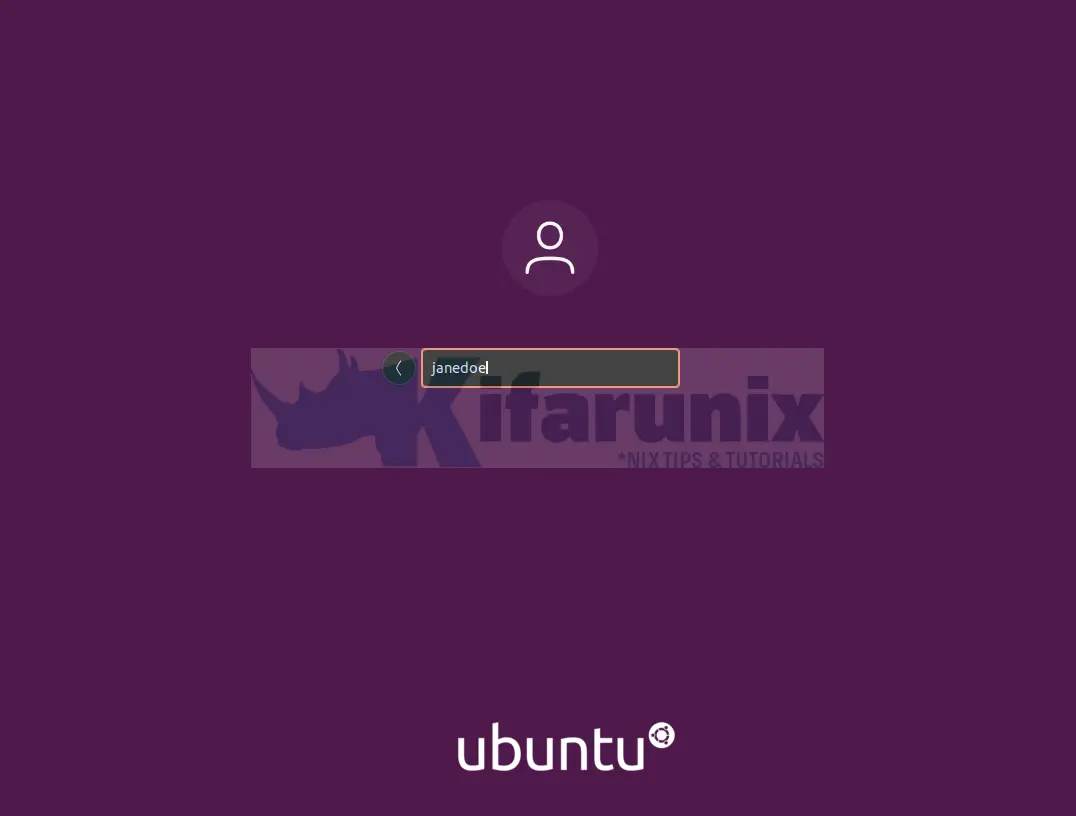
Upon successful login, you land on Ubuntu 22.04 desktop.
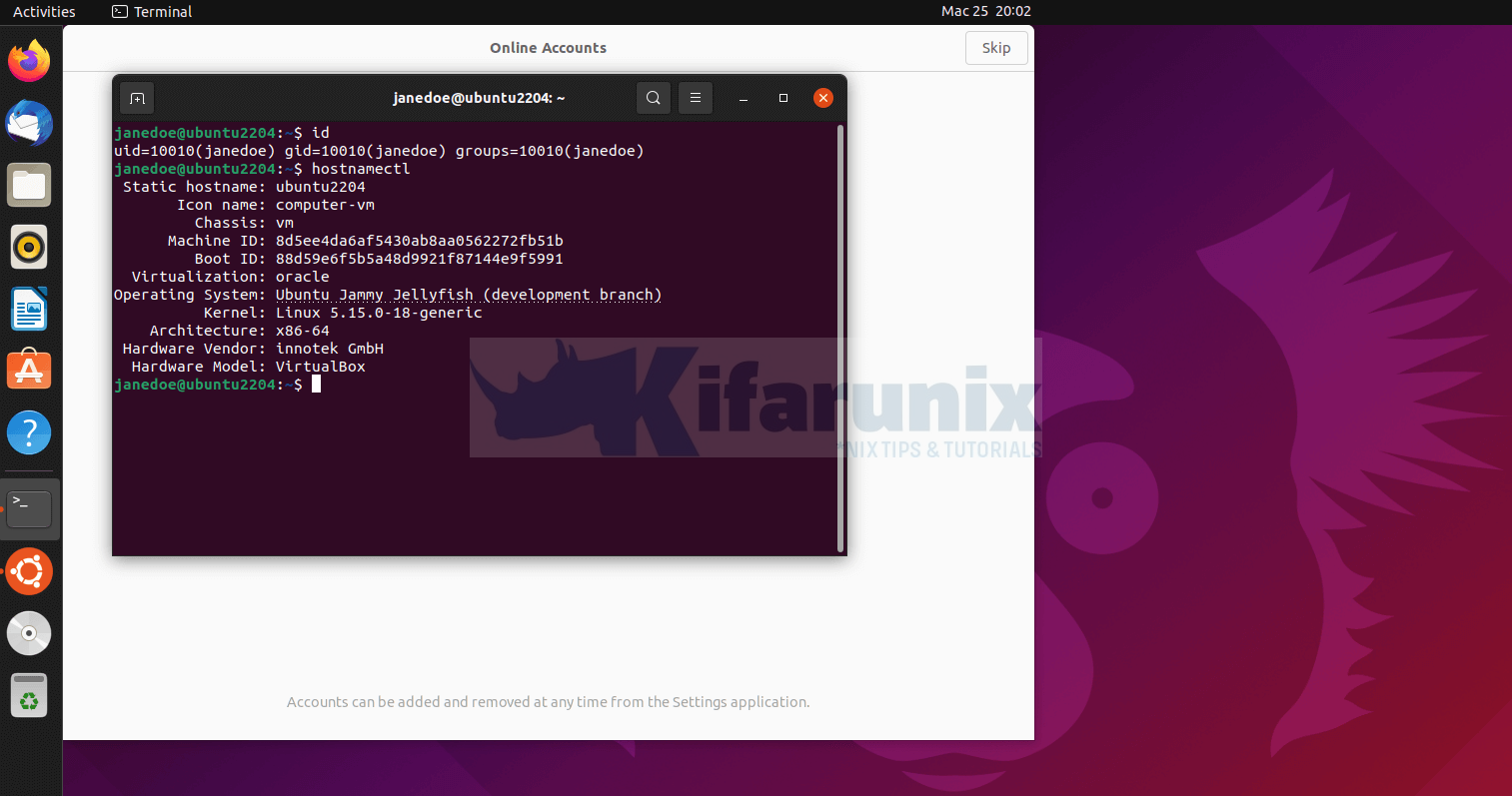
And there you go. That closes our guide on how to configure SSSD for LDAP Authentication on Ubuntu 22.04
Related Tutorials
Configure SSSD for OpenLDAP Authentication on Ubuntu 18.04
Install phpLDAPadmin on CentOS 8
Configure ownCloud OpenLDAP Authentication

