Hello folks, today we are going to learn how to install and use Nikto web scanner on Ubuntu 18.04 server.
Nikto is a Perl based open-source web vulnerability scanner that can unearth every other potential threat on your web server including but not limited to;
- Insecure files and programs
- Outdated servers and programs
- Server and software misconfigurations
- Default files and programs
Nikto can run on almost any Operating system with Perl interpreter installed. It supports SSL, proxies, host authentication, attack encoding, IDS evation etc.
You may also want to check our previous tutorials on Nessus, OpenVAS, ClamAV.
Without much theory, let us quickly have a look at how to install and use Nikto.
Installing Nikto Web Scanner on Ubuntu 18.04
Install Nikto on Ubuntu 18.04
Installation of nikto on Ubuntu 18.04 is pretty straight forward as the package is available on the default repositories. Thus, run the commands below to install nikto.
Update your package repos and upgrade your server;
apt updateapt upgrade
Install nikto.
Perl is already installed on Ubuntu 18.04. Therefore, the command below will install nikto and all the required dependencies.
apt install nikto -yOnce the installation is done, nikto is ready perform its magics. Wait and see.
Basic Usage of Nikto
The basic nikto command line syntax is:
nikto [options...]When run without any command line options, it shows basic description of various command options;
nikto
- Nikto v2.1.5
---------------------------------------------------------------------------
+ ERROR: No host specified
-config+ Use this config file
-Display+ Turn on/off display outputs
-dbcheck check database and other key files for syntax errors
-Format+ save file (-o) format
-Help Extended help information
-host+ target host
-id+ Host authentication to use, format is id:pass or id:pass:realm
-list-plugins List all available plugins
-output+ Write output to this file
-nossl Disables using SSL
-no404 Disables 404 checks
-Plugins+ List of plugins to run (default: ALL)
-port+ Port to use (default 80)
-root+ Prepend root value to all requests, format is /directory
-ssl Force ssl mode on port
-Tuning+ Scan tuning
-timeout+ Timeout for requests (default 10 seconds)
-update Update databases and plugins from CIRT.net
-Version Print plugin and database versions
-vhost+ Virtual host (for Host header)
+ requires a value
Note: This is the short help output. Use -H for full help text.
If you want to see more details about the options above, run the command below;
nikto -HLaunching Nikto Web Scan
In this section, we are going to see how Nikto is used with various command line options shown above to perform web scanning.
In its basic functionality, Nikto requires just an host an to scan. The target host can be specified with the -h or -host option e.g to scan a web server whose IP address is 192.168.43.154, run Nikto as follows;
nikto -host 192.168.43.154
- Nikto v2.1.5
---------------------------------------------------------------------------
+ Target IP: 192.168.43.154
+ Target Hostname: test.com
+ Target Port: 80
+ Start Time: 2018-11-01 18:01:35 (GMT3)
---------------------------------------------------------------------------
+ Server: Apache/2.4.29 (Ubuntu)
+ The anti-clickjacking X-Frame-Options header is not present.
+ Cookie PHPSESSID created without the httponly flag
+ Root page / redirects to: login.php
+ Server leaks inodes via ETags, header found with file /robots.txt, fields: 0x1a 0x5797709ba2009
+ File/dir '/' in robots.txt returned a non-forbidden or redirect HTTP code (302)
+ "robots.txt" contains 1 entry which should be manually viewed.
+ OSVDB-3268: /config/: Directory indexing found.
+ /config/: Configuration information may be available remotely.
+ OSVDB-3268: /docs/: Directory indexing found.
+ OSVDB-3233: /icons/README: Apache default file found.
+ /login.php: Admin login page/section found.
+ OSVDB-3092: /.git/index: Git Index file may contain directory listing information.
+ 6545 items checked: 0 error(s) and 11 item(s) reported on remote host
+ End Time: 2018-11-01 18:01:48 (GMT3) (13 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
As you can see from the output, when the target host is specified without a port, nikto scans port 80 by default. However, if your web server is running on a different port, you have to specify the port using the -p or -port option. See example below;
nikto -h 192.168.43.154 -p 8080If you have multiple virtualhosts on the same host server listening on different ports, you can specify multiple ports by separating them with comma.
nikto -h 192.168.43.154 -p 8080,8888You can also specify a range of ports in the format port1-portN for example,
nikto -h 192.168.43.154 -p 8080-8888Instead of using the IP address to specify the target host, URLs can also be used for example;
nikto -h mydvwa.example.com
nikto -h https://mydvwa.example.comYou can also specify the port when you use URL;
nikto -h mydvwa.example.com -p 8080
nikto -h https://mydvwa.example.com -p 8443or
nikto -h mydvwa.example.com:8080
nikto -h https://mydvwa.example.com:8443/As much as target hosts can be specified using the -p option, it is also possible to specify a file containing a list of target hosts one per line. For instance, you file should should contains the targets in the format;
less scan-targets
https://mydvwa.example.com:443/
192.168.43.154:8888
192.168.43.101To scan these hosts at the same time, run the command below;
nikto -h scan-targetsIt is also possible to scan the hosts in a network listening on web server ports using Nmap and pass the output to nikto. For example to scan for open port 80 in a network, 192.168.43.0/24,
nmap -p80 192.168.43.0/24 -oG - | nikto -h -If you are going through a proxy server, you can ask nikto to use proxy by using the -useproxy option. You can set the proxy details on the nikto configuration file, /etc/nikto/config.txt or you can it on the command line as shown below;
To define the proxy server details in the /etc/nikto/config.txt file, use the format;
PROXYHOST=192.168.70.45
PROXYPORT=3128
PROXYUSER=username
PROXYPASS=passwordWhen you have defined the proxy details as shown above, then run nikto as follows;
nikto -h 192.168.70.128 -useproxyTo specify the proxy connection details on the command line;
nikto -h 192.168.70.128 -useproxy http://id:[email protected]:3128/nikto -h 192.168.70.128 -useproxy http://@192.168.70.23:3128/Nikto can export scan results in different formats; CSV, HTML, XML, NBE, text. To save the results in a specific output format, you need to specify the -o/-output option as well as the -Format option to define the output format. See examples below to save the scan results in html format.
nikto -h 192.168.43.154 -o test.html -F htmlYou can therefore access the report via web browser. See screenshot below;
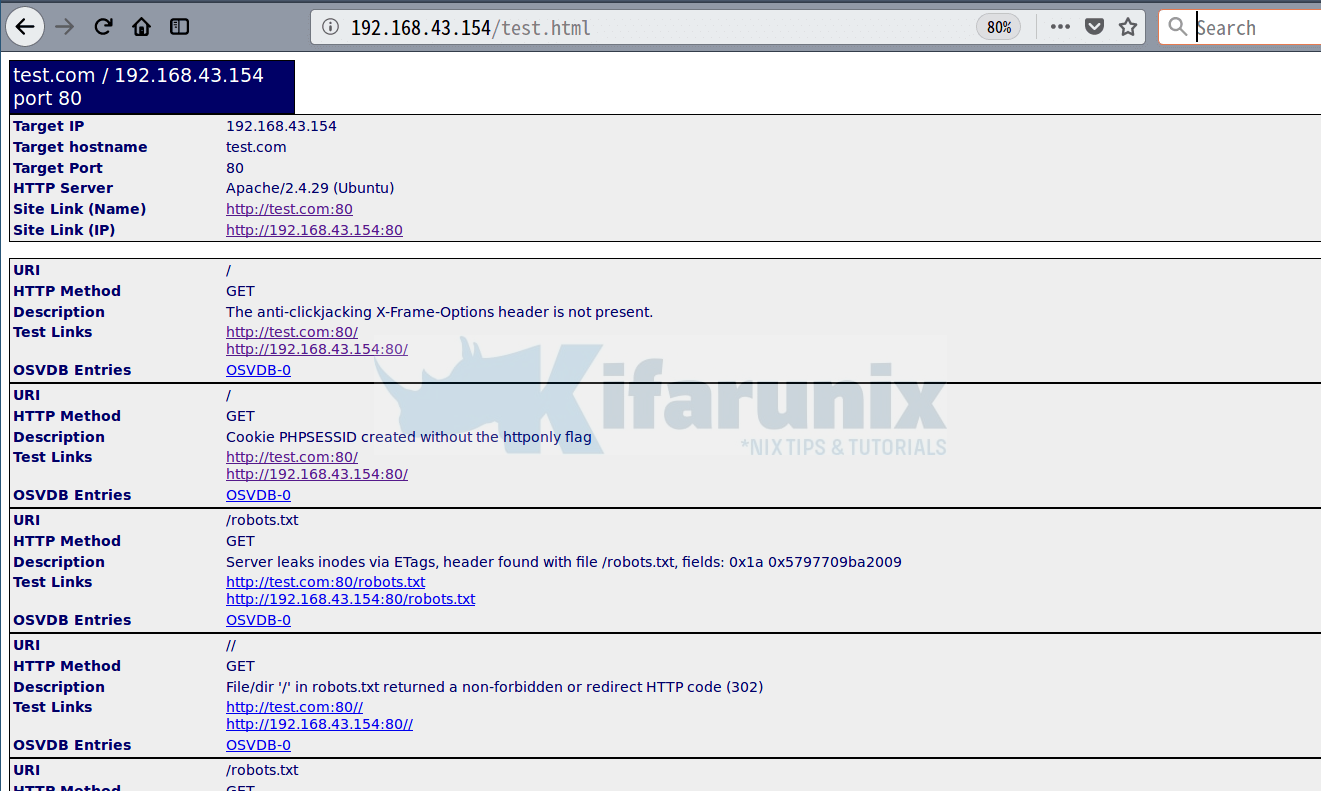
Nikto can also be fine tuned to perform specific scans. Below is a description of the tuning options that can be used to achieve this functionality.
1 - Interesting File / Seen in logs
2 - Misconfiguration / Default File
3 - Information Disclosure
4 - Injection (XSS/Script/HTML)
5 - Remote File Retrieval - Inside Web Root
6 - Denial of Service
7 - Remote File Retrieval - Server Wide
8 - Command Execution / Remote Shell
9 - SQL Injection
0 - File Upload
a - Authentication Bypass
b - Software Identification
c - Remote Source Inclusion
x - Reverse Tuning Options (i.e., include all except specified)
For example, to test for SQL Injection and Remote File Retrieval – Server Wide, you would use nikto like;
nikto -h 192.168.43.154 -Tuning 79 -o test.html -F htmlFeel free to explore the basic usage of other command line options from Nikto Documentation page.

