In this tutorial, we are going to learn how to configure Offline Authentication via OpenLDAP on MacOS X. If you have configured network-based authentication on MacOS X through directory servers such as OpenLDAP, Active Directory, FreeIPA, chances are you might want to use the same directory account to authenticate to you MacOS system when you are not connected to your directory services provider servers or in the event that these servers are offline.
If you were on Unix systems, you would use System Security Services Daemon (SSSD) which provides offline credential caching for a specified period of time to help in offline authentication. On MacOS X systems, this is made possible through the use of mobile user accounts.
What is a mobile user account? A mobile account is a type of account that lets you access your server-based network user account remotely. You use your network account username and password to log in, whether or not you’re connected to the network.
Configure Offline Authentication via OpenLDAP on MacOS X
Before you can proceed, we assume that you already configured OpenLDAP authentication on your MacOS X system. If not, check the link below;
Configure OpenLDAP Authentication on MacOS X
In order to enable Offline authentication via OpenLDAP on MacOS X, you need to create a mobile user account with the same user username as the LDAP username for the user in question.
There are different ways in which you can create a mobile account on a MacOS X system. You can do it via the UI as described here for MacOS Catalina or Mojave.
In this tutorial, we will create the mobile account via the terminal using the createmobileaccount command, /System/Library/CoreServices/ManagedClient.app/Contents/Resources/createmobileaccount.
Below is the syntax of the createmobileaccount command.
usage: createmobileaccount -n username [-h homepath] [-P | [-p password]] [-e] [-q] [[-x] | [-X]] [-d] [-v]
-n username : user record name.
-h homepath : user home path; Default is "/Users/".
-p password : user password.
-P : prompt for user password. A user password is required to create a FileVault home.
-e encrypt : encrypt new home with FileVault.
-q quota : max size in bytes of FileVault home.
-x : create as external account on non-boot volumes. Default.
-X : create as mobile account account non-boot volumes.
-d : disable external account creation.
-v : verbose output.
Examples:
createmobileaccount -n jsmith
createmobileaccount -v -P -n jsmith
createmobileaccount -vsxn jsmith -h /Volumes/HD3/jhome
Notes:
- createmobileaccount must run as root.
- If you do not specify a password, the account's cached password will be created during the account's first log in. Just so as to be sure about our LDAP user account that we will be using, below are the LDAP directory details;
ldapsearch -Y EXTERNAL -H ldapi:/// -b "ou=people,dc=ldapmaster,dc=kifarunix-demo,dc=com" uid=janedoe -LLL -Qdn: uid=janedoe,ou=people,dc=ldapmaster,dc=kifarunix-demo,dc=com
objectClass: inetOrgPerson
objectClass: posixAccount
objectClass: shadowAccount
objectClass: extensibleObject
uid: janedoe
cn: jane
sn: Doe
loginShell: /bin/bash
uidNumber: 10010
gidNumber: 10010
shadowMax: 60
shadowMin: 1
shadowWarning: 7
shadowInactive: 7
shadowLastChange: 0
homeDirectory: /Users/janedoe
userPassword:: e1NTSEF9Rmpjb0VzRE8rRlFBcEp1UWNFclVhWGdmNFYyNGdxdkI=Therefore, create a mobile account for the user, Jane Doe (janedoe) by running the command below. Ensure that you are connected to OpenLDAP before you run the command.
/System/Library/CoreServices/ManagedClient.app/Contents/Resources/createmobileaccount -n jane -h /Users/janedoe/ -vcreatemobileaccount built Aug 5 2016 16:20:50
verbose output on.
user name = "jane"
home path = "/Users/janedoe"
user password = "(null)"
prompt for password = FALSE
encrypt new home = FALSE
create as external account = TRUE
Mobile account record:
dsAttrTypeStandard:RealName = "jane"
dsAttrTypeStandard:RecordName = "janedoe"
dsAttrTypeStandard:GeneratedUID = "7E48FE18-6EA0-4294-B6C2-3CF0F9DA5824"
dsAttrTypeStandard:UniqueID = "10010"
dsAttrTypeStandard:PrimaryGroupID = "10010"
dsAttrTypeStandard:NFSHomeDirectory = "/Users/janedoe"
dsAttrTypeStandard:OriginalNFSHomeDirectory = "/Users/janedoe"Notice that the command extracts OpenLDAP directory user account details.
If you can check from Users and Groups preference settings, a mobile user has been created.
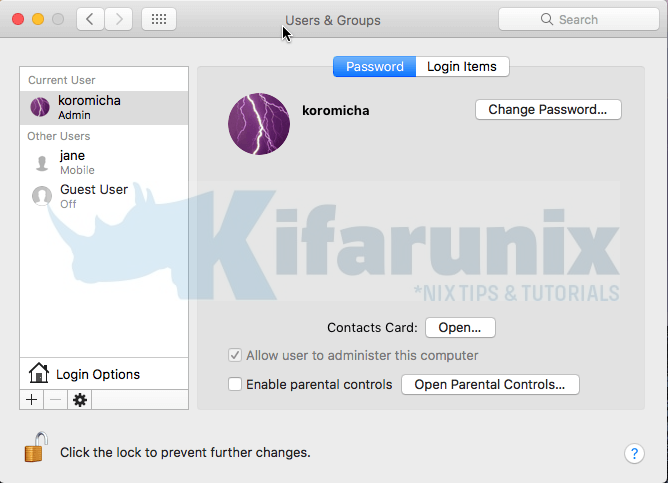
If you noticed, we didn’t provide any password for the account. If you do not specify a password, the account’s cached password will be created during the account’s first log in.
Therefore, logout of your system and login using the same LDAP account while the system is still connected to OpenLDAP directory so that the password is cached to enable you to login when you are offline.
Verify Offline Authentication
You can now disable your network to take the system offline for you to verify if you can actually authenticate when your directory service provider is unreachable or when you are offline.
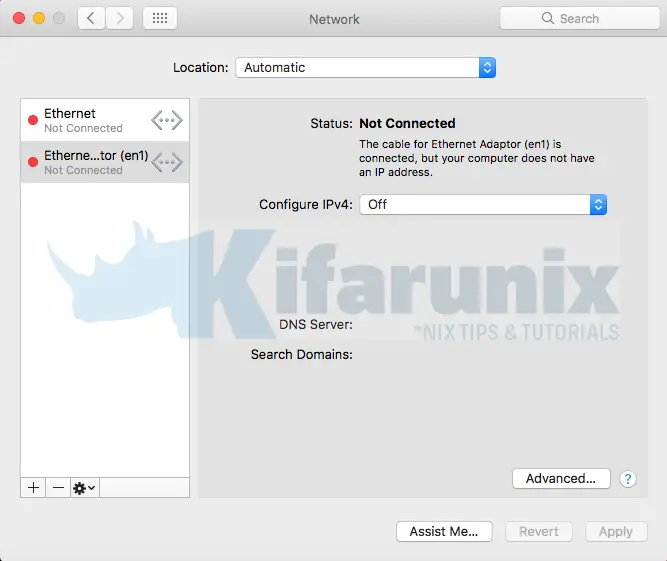
Next, log out of your system.
On the login window, select your mobile LDAP account and enter the OpenLDAP credentials for that account.

If all goes well, you should be land on your desktop.

And ther you go. You have successfully authenticated to your MacOS system via an offline mobile LDAP account.
That marks the end of our guide on how to configure offline authentication via OpenLDAP on MacOS X.
We hope that was informative. Enjoy.
Related Tutorials
Configure OpenLDAP Authentication on MacOS X
Install and Setup OpenLDAP Server on Ubuntu 20.04
Install and Setup phpLDAPadmin on Ubuntu 20.04

