In this tutorial, we are going to learn how to configure Nginx with SSL/TLS certificates on CentOS 8. The use of SSL/TLS certificates ensures secured as well as authentic communications between the web server and the web clients.
Configure Nginx with SSL/TLS certificates
Install Nginx and SSL/TLS module on CentOS 8
In order to configure Nginx HTTP server to use SSL/TLS certificates, you first need to install it and the SSL/TLS module. Nginx as the mod_ssl packages are available on the default CentOS 8 repositories and can simply be installed by executing the command below;
dnf install nginx mod_sslOnce installed, start and enable it to run on system boot.
systemctl enable --now nginxTo allow external access, allow Nginx through the firewall. This can be done by simply opening port 80 (HTTP) or 443 (HTTPS) depending on the traffic to server.
In this guide, since we configuring Nginx to the TLS certificates, we are opening port 443/tcp.
firewall-cmd --add-port=443/tcp --permanentYou can as well open port 80/tcp if you may want to redirect HTTP to HTTPS traffic.
firewall-cmd --add-port=80/tcp --permanentfirewall-cmd --reloadGenerate SSL/TLS Certificates
Well, in this guide, we are going to use Self-signed SSL/TLS certificates for the demonstration purposes.
If you want to use the commercially trusted certificates, you need to generate your Certificate Signing Request (CSR) and submit it to your preferred CA to order for the trusted certificate.
How to generate CSR?
Well, if you choose to go with commercially trusted certificates, you can generate the CSR by running the command below. Replace the names of the key and the CSR accordingly.
openssl req -new -newkey rsa:4096 -nodes -keyout kifarunix-demo.key -out kifarunix-demo.csrYou are required to provide the following details;
- The two-letter code of the country (C) where your organization is located.
- The name of State or Province (S) of where your organization is located
- The Locality Name (eg, city) (L) of where your organization is located
- The name of your Organization (O).
- The name of your Organizational Unit (OU).
- The Common Name (CN) (usually the fully qualified domain name you want to generate the certificates for. You can use wildcard if using for sub-domains, e.g. *.kifarunix-demo.com.
- This is the most important detail since it ties the your domain to the certificate to be generated.
- Optional email contact address.
To enter these details on the command line, use the -subj option as follows. Replace the highlighted values accordingly.
-subj "/C=CN/ST=STATE/L=CITY/O=ORG NAME/OU=Department/CN=DOMAIN_NAME/emailAddress=name@domain"Once generated, submit the CSR content to the signing Certificate Authority.
The command above generates both the private key and the CSR. Keep the private key as safe as it is required later when installing the certificate.
Note that you can also use the Let’s Encrypt, the commercially free certificate instead.
Generate Self-Signed SSL/TLS certificate
Well, for the demonstration purposes, you can generate the self-signed certificate as follows. Replace the domain names and location details accordingly.
openssl req -newkey rsa:4096 -nodes -keyout /etc/pki/tls/private/kifarunix-demo.key -x509 -days 365 -out /etc/pki/tls/certs/kifarunix-demo.crt \
-subj "/C=US/ST=Oregon/L=Springfield/O=kifarunix-demo/OU=IT/CN=*.kifarunix-demo.com/[email protected]"Once the command runs, you should be having the the self signed certificate and the private key under the /etc/pki/tls/certs and /etc/pki/tls/private respectively, if you used the command above.
To improve the SSL/TLS security by ensuring a secure cryptographic key exchange, generate Diffie-Hellman (DH) keys parameters.
openssl dhparam -out /etc/pki/tls/certs/dhparam.pem 4096Generating DH parameters may take some time.
To configure Nginx to use DH parameters, ssl_dhparam directive is used. You will see how in the next section.
Installing SSL/TLS Certificate on Nginx
Once you have the SSL certificates and the key in place, you can now configure Nginx to use them.
Open Nginx configuration file for editing;
vim /etc/nginx/nginx.confThe default Nginx TLS configurations has been modified to include the ciphers from Cipherli.st.
NOTE: If you want to redirect HTTP traffic to HTTPS, you can simply add the line below under the Nginx HTTP configuration section.
return 301 https://$host$request_uri;See below on how the line is added.
Replace the certificates and server name accordingly.
...
server {
listen 80 default_server;
listen [::]:80 default_server;
server_name _;
root /usr/share/nginx/html;
return 301 https://$host$request_uri;
...
# Settings for a TLS enabled server.
#
server {
listen 443 ssl http2 default_server;
server_name web01.kifarunix-demo.com; # The Server FQDN
root /usr/share/nginx/html;
ssl_protocols TLSv1.3; # Enable TLS v1.3 only
ssl_certificate "/etc/pki/tls/certs/kifarunix-demo.crt";
ssl_certificate_key "/etc/pki/tls/private/kifarunix-demo.key";
ssl_session_cache shared:SSL:1m;
ssl_session_timeout 10m;
ssl_ciphers EECDH+AESGCM:EDH+AESGCM;
ssl_ecdh_curve secp384r1;
ssl_prefer_server_ciphers on;
ssl_session_tickets off;
resolver 8.8.8.8 valid=300s;
resolver_timeout 5s;
add_header Strict-Transport-Security "max-age=63072000; includeSubDomains; preload";
add_header X-Frame-Options DENY;
add_header X-Content-Type-Options nosniff;
add_header X-XSS-Protection "1; mode=block";
# Add DH parameters
ssl_dhparam /etc/pki/tls/certs/dhparam.pem;
# # Load configuration files for the default server block.
include /etc/nginx/default.d/*.conf;
location / {
}
error_page 404 /404.html;
location = /40x.html {
}
error_page 500 502 503 504 /50x.html;
location = /50x.html {
}
}
}Save and quit the configuration file.
If you are using the certificates from CA, you will be provided with two certificate files, the Intermediate certificate and the server certificate. To use them, you need to put them together in a single certificate file.
cat server.crt intermediate.crt >> /etc/pki/tls/certs/ser-int-cert.crtReplace the names and paths accordingly.
Verify Nginx configuration for syntax errors.
nginx -tnginx: the configuration file /etc/nginx/nginx.conf syntax is ok
nginx: configuration file /etc/nginx/nginx.conf test is successfulRestart Nginx
systemctl restart nginxAccess Nginx from Browser using HTTPS
Navigate to the browser and try to access Nginx using HTTPS to check if all is well using the address, https://server-IP-or-FQDN.
If using self-signed SSL. accept the “Your connection is not private” warning and proceed. You should land on Nginx test page.
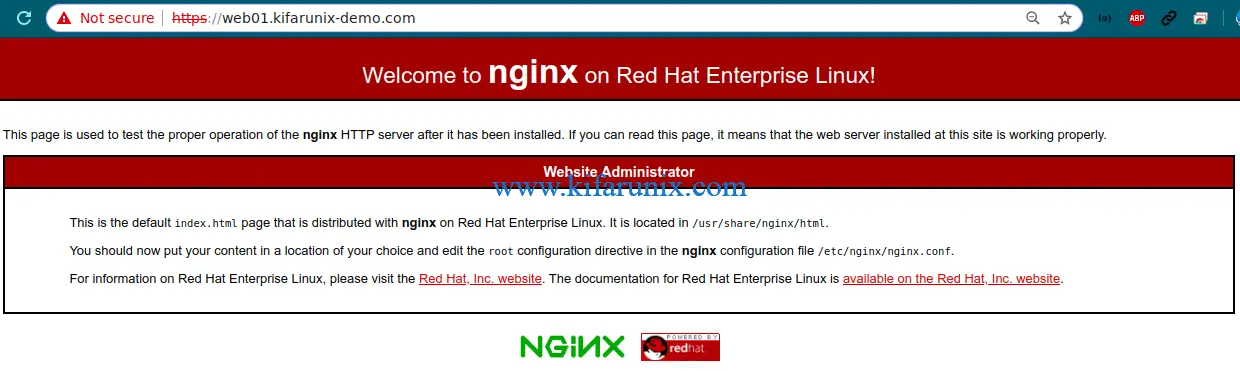
That is all. You’ve successfully installed your SSL certificate and your site is now configured to use SSL/TLS certificates.
Related Tutorials
Configure Guacamole SSL/TLS with Nginx Reverse Proxy
Configure HAProxy Load Balancer with SSL on Ubuntu 18.04/Debian 10/9
How to Create Locally Trusted SSL Certificates with mkcert on Ubuntu 18.04

