Follow through this guide to learn how to configure host-based access control on FreeIPA server. If you are using FreeIPA to manage authentication, you might have realized that by default, any user can login to any host system that is connected or joined to the FreeIPA server. This is because, FreeIPA IdM is configured with a default HBAC rule named allow_all, which allows universal access to every host for every user via every relevant service in the entire IdM domain. This poses a security risk. It is therefore prudent to restrict user access to specific host systems.
Table of Contents
Configure Host-Based Access Control on FreeIPA Server
Install and Setup FreeIPA server
Ensure you have a running FreeIPA server. If you haven’t set it up and you need help on how to, check our guide below.
Install and Setup FreeIPA server
Add User Accounts to FreeIPA Server
Next, you need to have user accounts created on the FreeIPA server.
Add FreeIPA User Accounts via CLI or Web Interface
Install and Configure FreeIPA Client on Ubuntu
To enroll your Linux host into FreeIPA, see our example guide below;
Install and Configure FreeIPA Client on Ubuntu 24.04
Configuring Host-Based Access Control
Now that you have FreeIPA server up and running, with user accounts already added, it is now time to restrict users to specific systems based on their hostnames.
You can configure FreeIPA host-based access control via web user interface or via the command line.
Configure Host-Based Access Control via FreeIPA WebUI
Login to FreeIPA web dashboard as IPA admin and navigate to Policy > Host Based Access Control. Click drop-down button and select HBAC Rules (selected by default).
You will see default HBAC rules. Click Add on the right side to add the rules. Add HBAC rules wizard pops up.
Enter the name of the rule and click “Add and Edit“. Note that I am interested in allowing users to access ONLY their work stations and not any other user’s workstation, for example.
It is also possible ti create access based on groups and their roles!
Thus:
- under General settings, you can optionally set a description of the access control.
- specify Who the rules applies to. Click Add to select and add the user.
- under Accessing, select and add hosts the user is allowed to access
- on Via Service, select which service to allow the user on the host. FreeIPA server ships with some common services and service groups configured for HBAC rules by default. Check them under Policy > Host-Based Access Control>HBAC Services. Here, am only interested in login service.
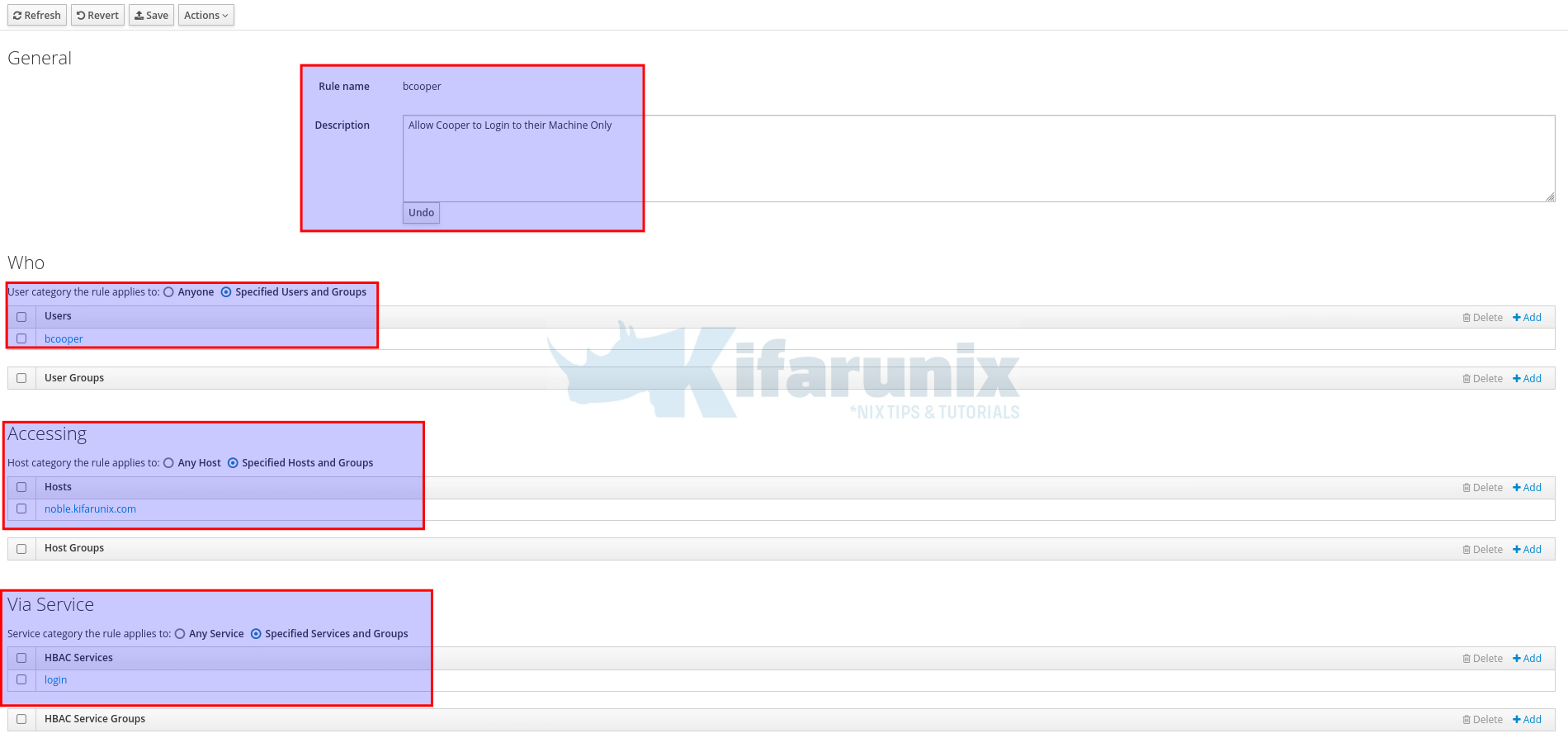
Click Save (just above the General settings) to save the rules.
Testing HBAC Rules on Web UI
You can now test the rules against the host to confirm if they work. Ensure that you have enrolled the host (installed the FreeIPA client and connected the client host to the server already).
Under Policy > Host-Based Access Control, click HBAC Test and:
- Who: Select the user whom you want to test
- Accessing: Select the system to test access against
- Via Service: Select specific service to test. We are doing login here.
- Rules: Select the individual user rule we created before.
- Run test: Click Run test to confirm the user login against the host.
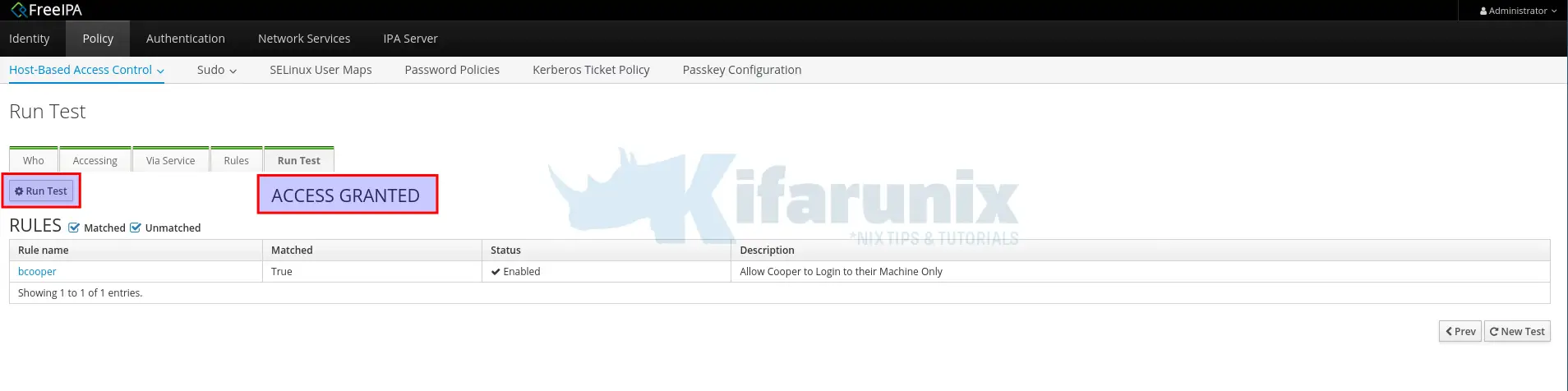
The results of a test can either be:
- ACCESS GRANTED, the user is able to access the host successfully.
- ACCESS DENIED, the user is not granted access in the test.
You can do more access controls based on your use cases!
Disable Allow_All Rule
You can now disable allow_all rule.
Select the rule from HBAC Rules and disable it.
Configure Host-Based Access Control via CLI
Similarly, you can also use IPA command line tools to configure host based access control.
There is quite a number of IPA command line arguments that you can use to manage HBAC on FreeIPA.
hbacrule-add hbacrule-add-user hbacrule-enable hbacrule-remove-host hbacrule-show
hbacrule-add-host hbacrule-del hbacrule-find hbacrule-remove-service
hbacrule-add-service hbacrule-disable hbacrule-mod hbacrule-remove-user
You can list all the rules using;
ipa hbacrule-find --allTo add HBAC rule, use the command, ipa hbacrule-add.
ipa hbacrule-addYou will be prompted for rule name ;
Rule name: bparker
-------------------------
Added HBAC rule "bparker"
-------------------------
Rule name: bparker
Enabled: True
Next, apply the rule to the user;
ipa hbacrule-add-user --users=bparkerWhere bparker is my user.
Rule name: bparker
Rule name: bparker
Enabled: True
Users: bparker
-------------------------
Number of members added 1
-------------------------
Next define the hosts as well as the service to grant user access to:
ipa hbacrule-add-host bparker --hosts=node02.kifarunix.com Rule name: bparker
Enabled: True
Users: bparker
Hosts: node02.kifarunix.com
-------------------------
Number of members added 1
-------------------------
ipa hbacrule-add-service bparker --hbacsvcs=login Rule name: bparker
Enabled: True
Users: bparker
Hosts: node02.kifarunix.com
HBAC Services: login
-------------------------
Number of members added 1
-------------------------
And that is it.
Confirm availability of the rule;
ipa hbacrule-find--------------------
4 HBAC rules matched
--------------------
Rule name: allow_all
User category: all
Host category: all
Service category: all
Description: Allow all users to access any host from any host
Enabled: True
Rule name: allow_systemd-user
User category: all
Host category: all
Description: Allow pam_systemd to run [email protected] to create a system user session
Enabled: True
Rule name: bcooper
Description: Allow Cooper to Login to their Machine Only
Enabled: True
Rule name: bparker
Enabled: True
----------------------------
Number of entries returned 4
----------------------------
Check details;
ipa hbacrule-show bparker Rule name: bparker
Enabled: True
Users: bparker
Hosts: node02.kifarunix.com
HBAC Services: login
Test the HBAC Rule on Command Line
You can now use the command, ipa hbactest, to test the access granted to the user on the respective host.
ipa hbactest --user=<user> --host=<host> --service=<service> --rules=<rule-name>E.g
ipa hbactest --user=bparker --host=node02.kifarunix.com --service=login --rules=bparkerIf success, you get Access granted: True otherwise False.
--------------------
Access granted: True
--------------------
Matched rules: bparker
Disable Allow_all Rule on CLI
You can disable allow all rule on CLI;
ipa hbacrule-disable allow_allVerify Host Based Authentication
You can now try to login to the respective systems using respective user accounts.
For example, let’s SSH into Node02 as Bparker;
ssh [email protected]if success, you are prompted to first reset the password (if first login);
ssh [email protected]
([email protected]) Password:
Password expired. Change your password now.
([email protected]) Current Password:
([email protected]) New password:
([email protected]) Retype new password:
Creating directory '/home/bparker'.
Welcome to Ubuntu 24.04 LTS (GNU/Linux 6.8.0-31-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
System information as of Sat May 4 01:52:35 PM UTC 2024
System load: 0.04 Processes: 154
Usage of /: 45.4% of 11.21GB Users logged in: 1
Memory usage: 8% IPv4 address for enp1s0: 192.168.122.81
Swap usage: 0%
* Strictly confined Kubernetes makes edge and IoT secure. Learn how MicroK8s
just raised the bar for easy, resilient and secure K8s cluster deployment.
https://ubuntu.com/engage/secure-kubernetes-at-the-edge
Expanded Security Maintenance for Applications is not enabled.
0 updates can be applied immediately.
Enable ESM Apps to receive additional future security updates.
See https://ubuntu.com/esm or run: sudo pro status
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
$ hostname
node02
$
If you try to login as another user or to a system whose access is not granted, then, it will fail. Such example logs for SSH.
2024-05-04T16:57:32.396021+03:00 noble sshd[12352]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=192.168.122.1 user=bparker
2024-05-04T16:57:32.456847+03:00 noble sshd[12352]: pam_sss(sshd:auth): authentication success; logname= uid=0 euid=0 tty=ssh ruser= rhost=192.168.122.1 user=bparker
2024-05-04T16:57:32.479841+03:00 noble sshd[12352]: pam_sss(sshd:account): Access denied for user bparker: 6 (Permission denied)
2024-05-04T16:57:32.480226+03:00 noble sshd[12349]: error: PAM: User account has expired for bparker from 192.168.122.1
2024-05-04T16:57:32.491282+03:00 noble sshd[12349]: fatal: monitor_read: unpermitted request 104
And that is it. You can fine grain your rules to suit your needs.
That concludes our guide on how to setup host based access control on FreeIPA.
If you are using OpenLDAP, check;

