Hello folks. Today we are going to learn how to install GRR incident response framework on Ubuntu 18.04. Google Rapid Response (GRR) is a python based incident response framework that focuses on live forensics and investigations. It enables security analysts to examine and attacks and perform analysis remotely.
GRR is deployed in a server-client architecture. The GRR server provides a web based user interface that allows analysts to analyze data collected from the clients. The GRR client on the other side is deployed on the host to be investigated and it polls the GRR server from time to time for different actions such as listing a directory, downloading files.
Installing GRR Incident Response Framework on Ubuntu
Before you fire up the installation of GRR on Ubuntu 18.04, update and upgrade your system packages.
apt updateInstall MySQL database server
GRR uses MySQL as the default database backend. Hence you can install MySQL on Ubuntu 18.04 by running the command below;
apt install mysql-serverNext, run the MySQL security script to set the root password, remove anonymous, etc.
mysql_secure_installationAfter that, login to MySQL as root user and create GRR database and user. Creation of database user is optional since GRR can use the root password.
create database grr;
grant all privileges on grr.* to grr@localhost identified by 'password';
flush privileges;Now, install GRR on Ubuntu 18.04. The recommended way of installing GRR is to use the DEB package. Hence download the latest server DEB from here. You can simply, run the command below;
wget https://storage.googleapis.com/releases.grr-response.com/grr-server_3.2.4-6_amd64.debOnce the download is done, install using APT package manager which will take care of all the dependencies.
sudo apt install ./grr-server_3.2.4-6_amd64.debDuring installation, the installer will prompt you to define a few settings.
Running grr_config_updater initialize
...
-=GRR Datastore=-
For GRR to work each GRR server has to be able to communicate with
the datastore. To do this we need to configure a datastore.
GRR will use MySQL as its database backend. Enter connection details:
MySQL Host [localhost]: Enter
MySQL Port (0 for local socket) [0]: #####################################.]
MySQL Database [grr]: Enter
MySQL Username [root]: grr << user set above
Please enter password for database user grr: Password for grr db user
Successfully connected to MySQL with the provided details.
Define the GRR server hostname server. Note that this hostname should locally resolvable by the clients.
-=GRR URLs=-
For GRR to work each client has to be able to communicate with the
server. To do this we normally need a public dns name or IP address
to communicate with. In the standard configuration this will be used
to host both the client facing server and the admin user interface.
Please enter your hostname e.g. grr.example.com [grr.example.com]: Enter
Set the GRR server as well the administration UI URL
-=Server URL=-
The Server URL specifies the URL that the clients will connect to
communicate with the server. For best results this should be publicly
accessible. By default this will be port 8080 with the URL ending in /control.
Frontend URL [http://grr.example.com:8080/]: Enter
-=AdminUI URL=-:
The UI URL specifies where the Administrative Web Interface can be found.
AdminUI URL [http://grr.example.com:8000]: Enter
Next define the email address for alerting, logging and various updates. Email configuration assumes that you have an MTA already running.
Set the GRR admin user password.
Step 3: Adding GRR Admin User
Please enter password for user 'admin': P@SSWORDRepackage the client templates with new configurations.
Step 4: Repackaging clients with new configuration.
Server debs include client templates. Re-download templates? [yN]: [N]: Enter
Repack client templates? [Yn]: [Y]: yThe installation will proceed and if everything goes well, you should be able to see such an output.
GRR Initialization complete! You can edit the new configuration in /etc/grr//server.local.yaml.
Please restart the service for the new configuration to take effect.
#################################################################
Install complete.
If upgrading, make sure you read the release notes:
https://grr-doc.readthedocs.io/en/latest/release-notes.html
...
Restart the GRR service for the new configuration to take effect.
sudo systemctl restart grr-serverTo verify that the service is running, run the command below;
sudo systemctl status grr-server
* grr-server.service - GRR Service
Loaded: loaded (/lib/systemd/system/grr-server.service; enabled; vendor preset: enabled)
Active: active (exited) since Sat 2019-02-02 08:11:46 UTC; 39s ago
Docs: https://github.com/google/grr
Process: 11968 ExecStop=/bin/systemctl --no-block stop grr-server@admin_ui.service [email protected] [email protected] [email protected]
Process: 11992 ExecStart=/bin/systemctl --no-block start grr-server@admin_ui.service [email protected] [email protected] grr-server@worker2
Main PID: 11992 (code=exited, status=0/SUCCESS)
Running GRR UI behind Nginx Proxy with HTTPS
As a security measure, we are going to configure GRR admin UI to be served through Nginx Proxy via HTTPS. Also,be sure to limit access to GRR web UI.
Install Nginx
Nginx can be installed from the default Ubuntu repositories as shown below;
apt install nginxAfter the installation is done, generate SSL/TLS certificate. In this guide, we are going to use the self-signed SSL certificates.
sudo openssl req -x509 -nodes -days 365 -newkey rsa:2048 -keyout /etc/nginx/grr-server.key -out /etc/nginx/grr-server.crtSet the permissions for both the SSL certificate and key as follows;
chmod 644 /etc/nginx/grr-server.crt
chmod 400 /etc/nginx/grr-server.keyConfigure Nginx to server HTTPS traffic and proxies the GRR HTTP requests.
vim /etc/nginx/sites-available/defaultThe configuration should look like below without comments;
server {
listen 443;
server_name localhost;
ssl_certificate /etc/nginx/grr-server.crt;
ssl_certificate_key /etc/nginx/grr-server.key;
ssl on;
ssl_session_cache builtin:1000 shared:SSL:10m;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_ciphers HIGH:!aNULL:!eNULL:!EXPORT:!CAMELLIA:!DES:!MD5:!PSK:!RC4;
ssl_prefer_server_ciphers on;
access_log /var/log/nginx/grr.access.log;
location / {
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_pass http://localhost:8000;
proxy_read_timeout 180;
proxy_redirect http://localhost:8000 https://grr.example.com;
}
}
The https://grr.example.com on the proxy_redirect directive is the on you will use to publicly access GRR Admin UI. Therefore, edit the GRR server configuration file and adjust the value of AdminUI directive to this URL.
vim /etc/grr/server.local.yaml...AdminUI.url: https://grr.example.com
...Check Nginx for errors.
nginx -tnginx: the configuration file /etc/nginx/nginx.conf syntax is ok
nginx: configuration file /etc/nginx/nginx.conf test is successfulAllow HTTP and HTTPS traffic as well as the GRR ports on firewall.
ufw allow 80/tcp
ufw allow 443/tcp
ufw allow 8080/tcp
ufw allow 8000/tcp
ufw reloadRestart Nginx and GRR server to effect the changes.
systemctl restart nginx
systemctl restart grr-serverTo access GRR administration user interface, login using the https://grr.example.com as specified in the configurations above. Ignore the invalid SSL certificate warning. GRR’s page protected by a Basic Auth dialog thus you will be prompted to authenticate before you get to the dashboard. Use admin as the user and the password you set for the admin while doing installation.
 After a successful authentication, you will be taken GRR web user interface.
After a successful authentication, you will be taken GRR web user interface.
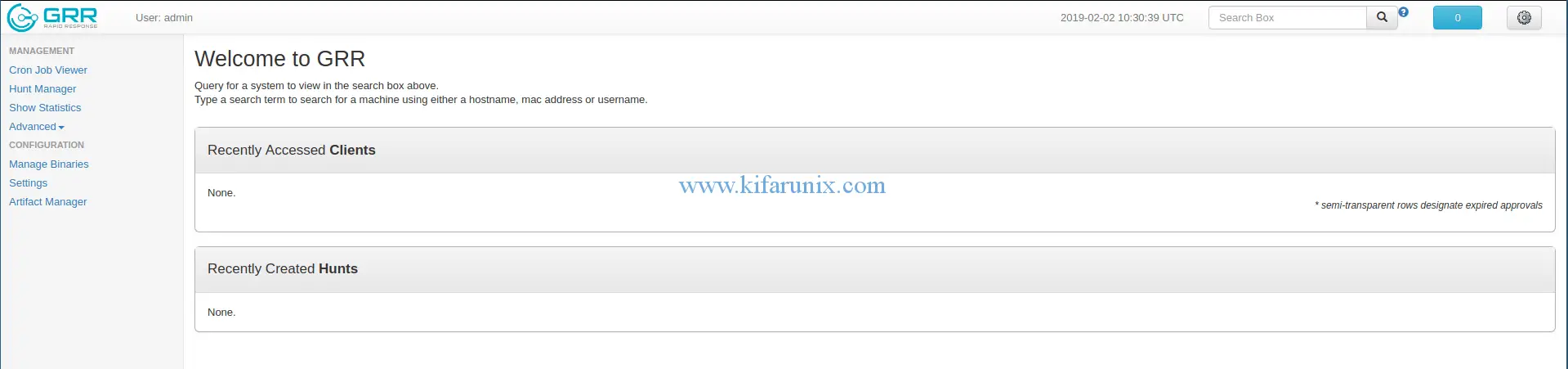
Beautiful. In our next tutorial,you will learn how to deploy GRR clients and start investigations. Enjoy.

