Welcome to our today’s guide on how to install and Setup FreeIPA server on CentOS 8. FreeIPA is an integrated Identity and Authentication solution for Linux/UNIX networked environments.
Table of Contents
Install and Setup FreeIPA Server on CentOS 8
Prerequisites
Set static hostname for your system. Note that the hostname must be fully qualified and must not be localhost or localhost6.
hostnamectl set-hostname freeipa.kifarunix-demo.com
Make the hostname resolvable. If you have a DNS server with your FreeIPA server entries then it is fine. Otherwise, configure your /etc/hosts file accordingly.
echo "192.168.56.123 freeipa.kifarunix-demo.com" | sudo tee -a /etc/hosts
Install FreeIPA on CentOS 8
FreeIPA packages are provided by the Identity Management system module of CentOS 8 AppStream repos. Therefore, you need to enable the idm:DL1 stream by running the command;
dnf module enable idm:DL1Next, run system update
dnf distro-syncInstall FreeIPA on CentOS 8
dnf install ipa-server ipa-server-dnsSetup FreeIPA with integrated DNS server
To setup FreeIPA server with integrated DNS, simply execute the setup command as shown below;
ipa-server-install --setup-dns
The setup will script will basically configure;
...
* Configure a stand-alone CA (dogtag) for certificate management
* Configure the NTP client (chronyd)
* Create and configure an instance of Directory Server
* Create and configure a Kerberos Key Distribution Center (KDC)
* Configure Apache (httpd)
* Configure DNS (bind)
* Configure the KDC to enable PKINIT
Once the setup script runs, you are prompted to configure a number of options. Provide the necessary input accordingly.
...
To accept the default shown in brackets, press the Enter key.
Enter the fully qualified domain name of the computer
on which you're setting up server software. Using the form
.
Example: master.example.com.
Server host name [freeipa.kifarunix-demo.com]: ENTER
Warning: skipping DNS resolution of host freeipa.kifarunix-demo.com
The domain name has been determined based on the host name.
Please confirm the domain name [kifarunix-demo.com]: ENTER
The kerberos protocol requires a Realm name to be defined.
This is typically the domain name converted to uppercase.
Please provide a realm name [KIFARUNIX-DEMO.COM]: ENTER
Certain directory server operations require an administrative user.
This user is referred to as the Directory Manager and has full access
to the Directory for system management tasks and will be added to the
instance of directory server created for IPA.
The password must be at least 8 characters long.
Directory Manager password: SET YOUR PASSWORD
Password (confirm): SET YOUR PASSWORD
The IPA server requires an administrative user, named 'admin'.
This user is a regular system account used for IPA server administration.
IPA admin password: SET YOUR PASSWORD
Password (confirm): SET YOUR PASSWORD
Checking DNS domain kifarunix-demo.com., please wait ...
Do you want to configure DNS forwarders? [yes]: ENTER
Following DNS servers are configured in /etc/resolv.conf: 8.8.8.8
Do you want to configure these servers as DNS forwarders? [yes]: ENTER
All DNS servers from /etc/resolv.conf were added. You can enter additional addresses now:
Enter an IP address for a DNS forwarder, or press Enter to skip:
Checking DNS forwarders, please wait ...
Do you want to search for missing reverse zones? [yes]: ENTER
Checking DNS domain 56.168.192.in-addr.arpa., please wait ...
Do you want to create reverse zone for IP 192.168.56.123 [yes]: ENTER
Please specify the reverse zone name [56.168.192.in-addr.arpa.]: ENTER
Checking DNS domain 56.168.192.in-addr.arpa., please wait ...
Using reverse zone(s) 56.168.192.in-addr.arpa.
The IPA Master Server will be configured with:
Hostname: freeipa.kifarunix-demo.com
IP address(es): 192.168.56.123
Domain name: kifarunix-demo.com
Realm name: KIFARUNIX-DEMO.COM
The CA will be configured with:
Subject DN: CN=Certificate Authority,O=KIFARUNIX-DEMO.COM
Subject base: O=KIFARUNIX-DEMO.COM
Chaining: self-signed
BIND DNS server will be configured to serve IPA domain with:
Forwarders: 8.8.8.8
Forward policy: only
Reverse zone(s): 56.168.192.in-addr.arpa.
...
After configuring all the values above, proceed with the setup.
...
Continue to configure the system with these values? [no]: yes
...The setup will then proceed and takes some few minutes to complete. Once done, you will be provided with setup summary.
...
==============================================================================
Setup complete
Next steps:
1. You must make sure these network ports are open:
TCP Ports:
* 80, 443: HTTP/HTTPS
* 389, 636: LDAP/LDAPS
* 88, 464: kerberos
* 53: bind
UDP Ports:
* 88, 464: kerberos
* 53: bind
* 123: ntp
2. You can now obtain a kerberos ticket using the command: 'kinit admin'
This ticket will allow you to use the IPA tools (e.g., ipa user-add)
and the web user interface.
Be sure to back up the CA certificates stored in /root/cacert.p12
These files are required to create replicas. The password for these files is the Directory Manager password
The ipa-server-install command was successful
Open Required FreeIPA ports on Firewall
FreeIPA uses a number of ports to communicate with its services which must be opened on firewall to allow external connections. You can simply open all the required ports using the service names by running the command below;
firewall-cmd --add-service={freeipa-ldap,freeipa-ldaps,dns,ntp} --permanentfirewall-cmd --reloadGenerate kerberos ticket
In order to use the IPA tools/commands, use the web user interface and perform any other administrative tasks, you need to obtain a kerberos ticket by running the command below;
kinit adminWhen prompted, enter the administrator password set during the installation setup.
You can as well list kerberos tickets using the klist command.
klistTicket cache: KCM:0
Default principal: [email protected]
Valid starting Expires Service principal
10/14/2019 13:06:09 10/15/2019 13:06:06 krbtgt/[email protected]
Accessing FreeIPA Web interface
The FreeIPA server is now installed and setup on CentOS 8. Other configuration settings can be done from the web interface. On the browser, you can access FreeIPA using the address https://freeipa.kifarunix-demo.com.
Ignore the private SSL warning and proceed to FreeIPA server login page. Use the username, admin and the admin password provided during the installation setup.

The default CentOS 8 FreeIPA server dashboard looks like;
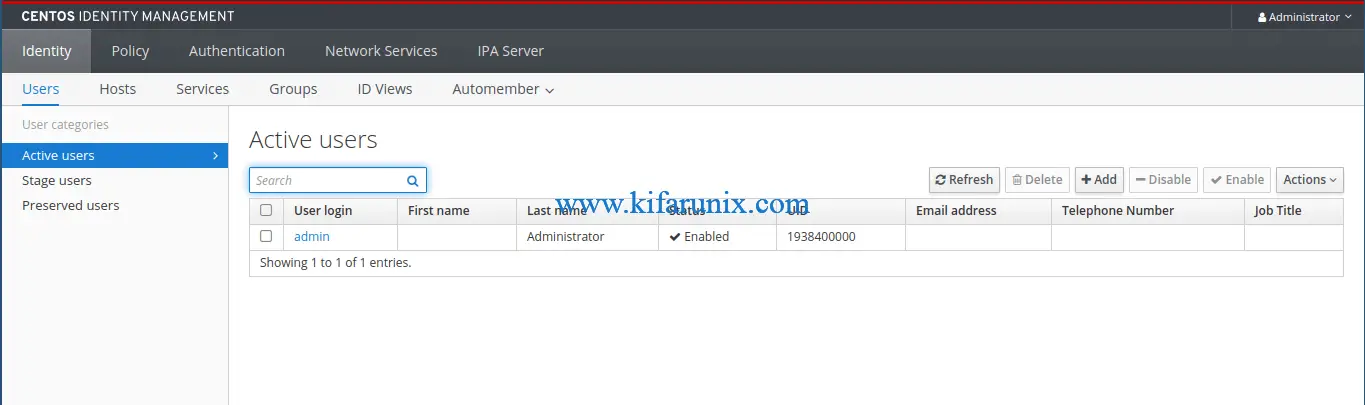
You can now perform the FreeIPA administrative tasks from the web interface.
You can as well run the administrative tasks from command line using the ipa command.
For example, to list the available FreeIPA users on the server, simply run the command;
ipa user-find
--------------
1 user matched
--------------
User login: admin
Last name: Administrator
Home directory: /home/admin
Login shell: /bin/bash
Principal alias: [email protected]
UID: 1938400000
GID: 1938400000
Account disabled: False
----------------------------
Number of entries returned 1
----------------------------
Great. That is all on our guide on how to install and setup FreeIPA server on on CentOS 8. Stay connected for more guides on FreeIPA.
Related Tutorials
How to Install FreeIPA Server on Fedora 29/Fedora 28/CentOS 7
Setup OpenLDAP Server with SSL/TLS on Debian 10
Install and Configure OpenLDAP server on Fedora 29
Install and Configure OpenLDAP Server on Debian 9 Stretch
Configure SSSD for OpenLDAP Client Authentication on Debian 10/9


Seems straight forward. I am a novice when it comes to Linux. I am looking to build a home server based on Linux to replace my aging Windows 2012 A.D. server. Trying to piece together everything that I will need to do it. I plan to use CentOS 8, as I am more familiar with it then anything else. Suggestions on how to do go about this (for dummies) would be appreciated.