In this tutorial, we are going to learn how to monitor OpenVPN connections using openvpn-monitor tool. This tutorial focuses on monitoring OpenVPN connections established using the OpenVPN Community Edition. OpenVPN CE provides a de-facto standard for creating a secure VPN connections over the internet using a custom security protocol that utilizes SSL/TLS.
While scouring the Internet for the tools that can be used to monitor active OpenVPN connections, I came across a python based tool called openvpn-monitor which utilizes OpenVPN management interface to generate an html report that displays the status of an OpenVPN server, including all current connections.
Monitoring OpenVPN Connections using openvpn-monitor tool
Prerequisites
Before you can proceed, there are a few things that needs to have setup.
Install and configure OpenVPN Server
Of course you can be wanting to monitor OpenVPN server connections without having an OpenVPN server running. Follow the links below to install and setup OpenVPN server on CentOS/Ubuntu systems;
Install and Setup OpenVPN Server on CentOS 8
Install and Setup OpenVPN Server on Ubuntu 20.04
Enable Management Interface
openvpn-monitor tools requires that OpenVPN management interface is enabled. The OpenVPN Management interface allows OpenVPN to be administratively controlled from an external program via a TCP or unix domain socket. OpenVPN management server can be enabled on a Unix socket or on a designated TCP port. While using the Unix socket is the recommended method, the openvpn-monitor tool uses OpenVPN management interface TCP connection. It is therefore strongly recommended that you set the OpenVPN management Interface IP to 127.0.0.1 (localhost) to restrict accessibility of the management server to local clients.
OpenVPN management interface TCP connection can be enabled by editing the OpenVPN server configuration file and adding the line, management IP port.
vim /etc/openvpn/server/server.conf...
comp-lzo
persist-key
persist-tun
status /var/log/openvpn/openvpn-status.log
log-append /var/log/openvpn/openvpn.log
verb 3
explicit-exit-notify 1
auth SHA512
# Enable OpenVPN Management Interface on localhost using TCP port 17562
management 127.0.0.1 17562
The line;
management 127.0.0.1 17562
Sets the OpenVPN management interface IP address to 127.0.0.1 (localhost) and TCP port 17562. The openvpn-monitor expects the OpenVPN Management Interface to be listening on TCP port 5555. We will change that later.
Check that the assigned port is not being used by any other program on your system;
lsof -i :17562If no application is using the port, restart OpenVPN server service;
systemctl restart [email protected]Check that port is now opened;
lsof -i :17562COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
openvpn 44178 root 3u IPv4 189028 0t0 TCP localhost:17562 (LISTEN)Ensure that OpenVPN server service is running;
systemctl status [email protected]● [email protected] - OpenVPN service for server
Loaded: loaded (/lib/systemd/system/[email protected]; enabled; vendor preset: enabled)
Active: active (running) since Sun 2020-08-16 16:15:46 UTC; 1h 15min ago
Docs: man:openvpn(8)
https://community.openvpn.net/openvpn/wiki/Openvpn24ManPage
https://community.openvpn.net/openvpn/wiki/HOWTO
Main PID: 44178 (openvpn)
Status: "Initialization Sequence Completed"
Tasks: 1 (limit: 2282)
Memory: 1.9M
CGroup: /system.slice/system-openvpn\x2dserver.slice/[email protected]
└─44178 /usr/sbin/openvpn --status /run/openvpn-server/status-server.log --status-version 2 --suppress-timestamps --config server.conf
Aug 16 16:15:46 ubuntu20.kifarunix-demo.com systemd[1]: Starting OpenVPN service for server...
Aug 16 16:15:46 ubuntu20.kifarunix-demo.com systemd[1]: Started OpenVPN service for server.Install and Setup openvpn-monitor tool
There are different methods of installing openvpn-monitor tool as outlined on the program’s Github repository. In this tutorial, we will use Apache to server the openvpn-monitor OpenVPN connections.
Install Apache for openvpn-monitor
Install Apache and the required package dependencies;
apt install git apache2 libapache2-mod-wsgi python3-geoip2 python3-ipaddr python3-humanize python3-bottle python3-semantic-version geoip-database geoipupdateDownload the openvpn-monitor program
Next, clone the openvpn-monitor Github repository to your default web server root directory. In this setup, we use, /var/www/html/openvpn-monitor directory.
git clone https://github.com/furlongm/openvpn-monitor.git /var/www/html/openvpn-monitorls /var/www/html/openvpn-monitor/AUTHORS COPYING images MANIFEST.in openvpn-monitor.conf.example openvpn-monitor.py README.md requirements.txt setup.py tests VERSION.txtConfigure openvpn-monitor
Rename the sample configuration file, openvpn-monitor.conf.example to openvpn-monitor.conf.
cp /var/www/html/openvpn-monitor/openvpn-monitor.conf{.example,}Replace the OpenVPN management interface if you changed it to a port other than 5555 defined on the openvpn-monitor.py Python program.
cd /var/www/html/openvpn-monitorgrep -irl 5555 . | xargs -I {} sed -i 's/5555/17562/' {}Next, you can now open the configuration file and set site name, add a logo, set the default map location (latitude and longitude, defaults to New York, USA).
This is how our modified configuration file looks like;
cat /var/www/html/openvpn-monitor/openvpn-monitor.conf[openvpn-monitor]
site=Kifarunix-demo-VPN
#logo=logo.jpg
latitude=11.016844
longitude=76.955833
maps=True
geoip_data=/var/lib/GeoIP/GeoLite2-City.mmdb
datetime_format=%d/%m/%Y %H:%M:%S
[VPN1]
host=localhost
port=17562
name=Kifarunix-demo VPN
show_disconnect=FalseNote the GeoIP2 City Database location. If it is not available on your system, register and download a free version from MaxMind.
One more thing is that, this setup is tested on Ubuntu 20.04, with python 3 being the default. Since openvpn-monitor uses python, simply create a symbolic link from python 3 to python;
ln -s /usr/bin/python3 /usr/bin/pythonConfigure Apache to Execute openvpn-monitor script
Next, execute the command below to configure Apache to execute the openvpn-monitor Python script.
vim /etc/apache2/sites-available/openvpn-monitor.confScriptAlias / /var/www/html/openvpn-monitor/openvpn-monitor.py
<Directory /var/www/html/openvpn-monitor>
Options +ExecCGI
AddHandler cgi-script .py
DirectoryIndex openvpn-monitor.py
AllowOverride None
Require ip 192.168.0.0/16
</Directory>Save and exit the configuration file.
Set the ownership of the openvpn-monitor web root directory to Apache user, www-data.
chown -R www-data: /var/www/html/openvpn-monitor/Check Apache configuration syntax;
apachectl -tSyntax OKEnable openvpn-monitor Apache site configuration and disable the default site.
a2ensite openvpn-monitor.confa2dissite 000-default.confStart Apache and enable it to run on system boot;
systemctl enable --now apache2Debugging openvpn-monitor
You can run openvpn-monitor from the command line to check if it actually generates the html report correctly:
cd /var/www/html/openvpn-monitor
python openvpn-monitor.pyYou can as well add option -d for debugging;
python openvpn-monitor.py -dSample output;
...
oms.addListener("click", function(marker) {
popup.setContent(marker.alt);
popup.setLatLng(marker.getLatLng());
map.openPopup(popup);
});
oms.addListener("spiderfy", function(markers) {
map.closePopup();
});
bounds.extend(centre);
map.fitBounds(bounds);
</script>
</div></div>
<div class="well well-sm">
Page automatically reloads every 5 minutes.
Last update: <b>16/08/2020 19:10:26</b></div>
</div></body></html>
DEBUG:
=== begin vpns
{'VPN1': {'host': 'localhost',
'name': 'Staff VPN',
'port': '17562',
'release': 'OpenVPN 2.4.7 x86_64-pc-linux-gnu [SSL (OpenSSL)] [LZO] '
'[LZ4] [EPOLL] [PKCS11] [MH/PKTINFO] [AEAD] built on Sep '
'5 2019',
'sessions': {},
'show_disconnect': False,
'socket_connected': True,
'state': {'connected': 'CONNECTED',
'local_ip': IPv4Address('10.8.0.1'),
'mode': 'Server',
'remote_ip': '',
'success': 'SUCCESS',
'up_since': datetime.datetime(2020, 8, 16, 16, 15, 46)},
'stats': {'bytesin': 0, 'bytesout': 0, 'nclients': 0},
'version': Version('2.4.7')}}
=== end vpns
Accessing openvpn-monitor on Browser
If all is well, you can now access your OpenVPN statistics via the address http://<OpenVPN-server-Address/openvpn-monitor or http://<OpenVPN-server-Address/ as per our redirection.
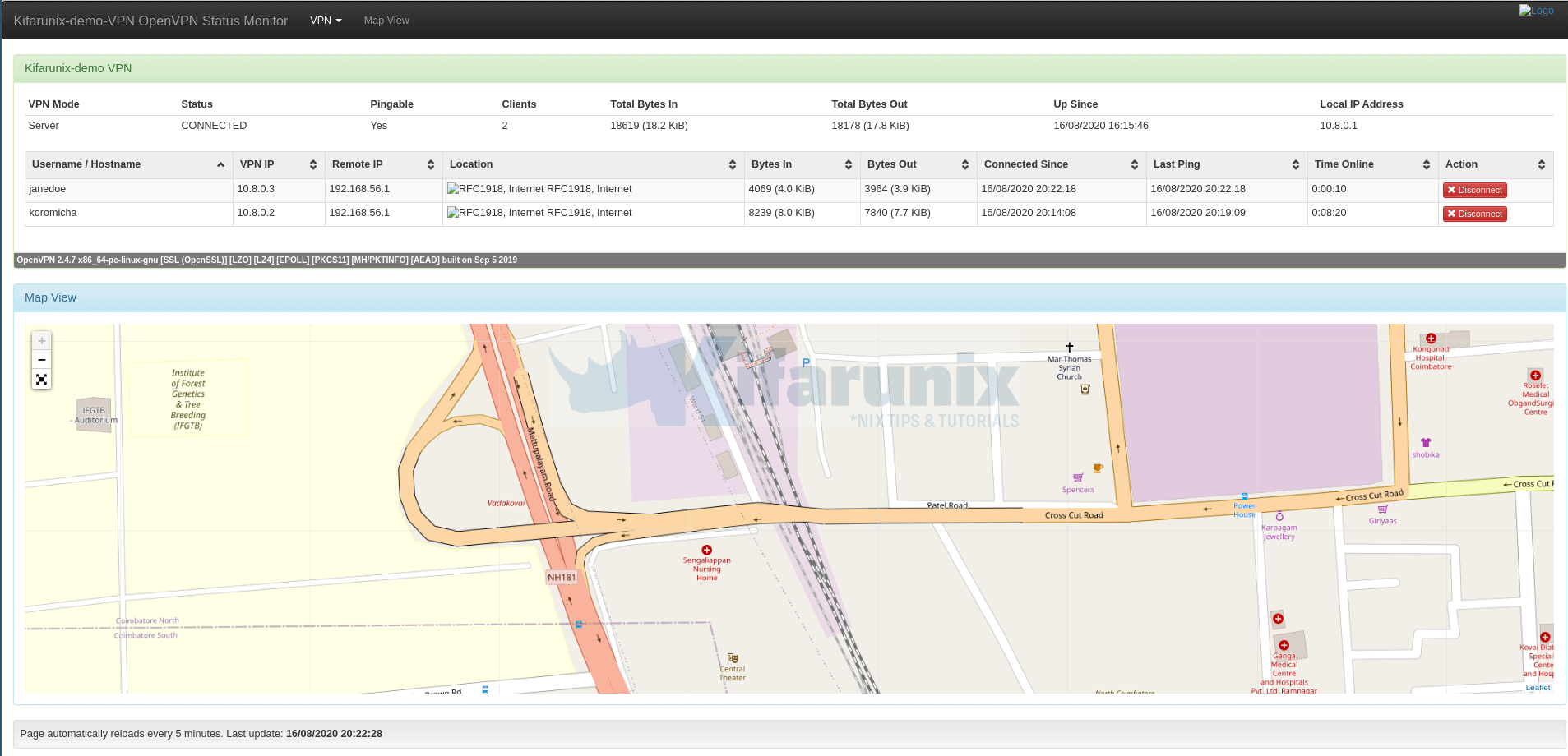
And there you go. Beautiful, isn’t? All credit goes to furlongm. As you can see, we have connection status for my locally connected OpenVPN clients.
Reference
Related Tutorials
Install and Setup OpenVPN Server on Ubuntu 20.04
Configure OpenVPN LDAP Based Authentication


two bugs in your instructions:
– in the instructions for editing openvpn-monitor.conf, you say to rename openvpn-monitor.conf.example to openvpn-monitor.py.
– apache needs the cgi module enabled in order for the openvpn-monitor.py to work
otherwise thanks, good instructions. maybe a little too fancy though…? why change the port number with a fancy one-liner when “edit the file and change port to ” would work just as well and not deliberately obfuscate things for new/junior linux nerds.
Thanks for the feedback!!
To load the cgi module for apache2 run:
sudo a2enmod cgid
Took me forever to figure this out.
Thank you!! My monitor page does not present the “Action tab”. However, everything else is working. Do I need to turn something on for this feature?
Just enable that in the configuration file: show_disconnect=True
If you have duplicate-cn on your openvpn server, how does that show up in the monitor with multiple connections?
Doesn’t work.
Followed step by step.
Get a index view of files when going to http://xxxx/openvpn-monitor
I have this all working, but was hoping to add a favicon icon to the web page, but can’t seem to get it working. Is there a way to do that?
Outdated for Debian 12. The libapache2-mod-wsg, python3-ipaddr packages
and geoipupdate’ has no candidate for installation. Any way to work on Debian 12?