In this guide, we are going to learn how to install Nagios Core on FreeBSD 13. Nagios is an opensource tool that provides an enterprise-class central monitoring engine for IT monitoring, network monitoring, server and applications monitoring. It also provides a web interface for viewing current status, historical logs, and basic reports.
Installing Nagios Core on FreeBSD 13
Nagios Core 4.4.6 is the current stable release as of this writing. Fortunately, Nagios Core 4.4.6 is available on the default FreeBSD 13 repository catalogue.
Prerequisites
Install Apache HTTP Server and PHP on FreeBSD
Install Apache and PHP on FreeBSD by running the command below;
pkg install apache24 mod_php74 php74-gdOnce the installation is done, ensure Apache is able to server PHP content by ensuring index.php is part of your DirectoryIndex.
sed i.bak ‘s/DirectoryIndex index.html/DirectoryIndex index.html index.php/’ /usr/local/etc/apache24/httpd.conf
Also, you should add the following to your Apache configuration file:
cat >> /usr/local/etc/apache24/httpd.conf << 'EOL'
<FilesMatch "\.php$">
SetHandler application/x-httpd-php
</FilesMatch>
<FilesMatch "\.phps$">
SetHandler application/x-httpd-php-source
</FilesMatch>
'EOL'Save and exit the file.
Ensure that Apache can server PHP by creating test file;
echo "<? phpinfo(); ?>" >> /usr/local/www/apache24/data/test.phpYou can then start Apache;
service apache24 onestartand navigate to the url http://server-host-name-or-ip/test.php.
You should see PHP page displayed.
You also need to install Apache utils like htpasswd for creating users for basic authentication. This can be done via FreeBSD ports;
Check how to install FreeBSD ports.
Once the ports are installed, Install htpasswd on FreeBSD as follows;
cd /usr/ports/security/p5-Apache-Htpasswd/make install cleanRun the command below to reload the $PATH after installation;
rehashTo begin with, update and upgrade the local catalogues of the enabled package repositories.
pkg updatepkg upgrade
To verify the availability of the Nagios Core 4.x on FreeBSD;
pkg search nagios4cnagios-nagios4-0.33_1 Curses-based interface for nagios
nagios4-4.4.6_1,1 Powerful network monitoring systemThus, as you can see, we have the latest release version of Nagios Core available on the default FreeBSD catalogue.
Installing Nagios Core on FreeBSD 13
You can therefore install Nagios Core by running the command below;
pkg install nagios4-4.4.6_1,1Sample installation output;
Updating FreeBSD repository catalogue...
FreeBSD repository is up to date.
All repositories are up to date.
Updating database digests format: 100%
The following 5 package(s) will be affected (of 0 checked):
New packages to be INSTALLED:
libltdl: 2.4.6
nagios-plugins: 2.3.3_2,1
nagios4: 4.4.6_1,1
php74-filter: 7.4.16
php74-xml: 7.4.16
Number of packages to be installed: 5
The process will require 10 MiB more space.
2 MiB to be downloaded.
Proceed with this action? [y/N]: yConfigure Nagios Core on FreeBSD 13
Once the installation is complete, proceed to configure Nagios Core on FreeBSD 13.
Enable Apache CGI Modules
Once the installation is done, open the Apache configuration file and enable the CGI modules.
Locate the lines below remove the # on the lines beginning with LoadModule such that they look like;
vi /usr/local/etc/apache24/httpd.conf...
<IfModule !mpm_prefork_module>
LoadModule cgid_module libexec/apache24/mod_cgid.so
</IfModule>
<IfModule mpm_prefork_module>
LoadModule cgi_module libexec/apache24/mod_cgi.so
</IfModule>
...Save and exit the file.
Create Apache Nagios Configuration file
Next, configure Apache to Server Nagios CGIs by creating a nagios.conf file that specify how Apache should server Nagios resources by running the command below;
cat >> /usr/local/etc/apache24/httpd.conf << 'EOL'
<VirtualHost *:80>
ServerName nagios.kifarunix-demo.com
DocumentRoot "/usr/local/www/nagios"
ScriptAlias /nagios/cgi-bin/ /usr/local/www/nagios/cgi-bin/
ScriptAlias /nagios/cgi-bin /usr/local/www/nagios/cgi-bin/
<Directory "/usr/local/www/nagios/cgi-bin">
Options ExecCGI
AllowOverride None
#Require all denied
Require ip 127.0.0.1 192.168.60.1
</Directory>
Alias /nagios/ /usr/local/www/nagios/
Alias /nagios /usr/local/www/nagios/
<Directory "/usr/local/www/nagios">
Options None
AllowOverride None
#Require all denied
Require ip 127.0.0.1 192.168.60.1
php_flag engine on
php_admin_value open_basedir /usr/local/www/nagios/:/var/spool/nagios/
</Directory>
<Location "/">
AuthName "Restricted Nagios Access"
AuthType Basic
AuthUserFile /usr/local/www/nagios/htpasswd.users
Require valid-user
</Location>
</VirtualHost>
'EOL'As you can see above, we have allowed access to our local Nagios from everywhere (Require all granted) and also enabled basic authentication to access Nagios web resources.
Configure Nagios Templates
Configuration templates are available in /usr/local/etc/nagios as *.cfg-sample files.
ls -1 /usr/local/etc/nagios/cgi.cfg-sample
nagios.cfg-sample
objects
resource.cfg-samplels -1 /usr/local/etc/nagios/objects/commands.cfg-sample
contacts.cfg-sample
localhost.cfg-sample
printer.cfg-sample
switch.cfg-sample
templates.cfg-sample
timeperiods.cfg-sample
windows.cfg-sampleCopy them to *.cfg files where required and edit to suit your needs.
cd /usr/local/etc/nagios/find . -type f -name "*.cfg-sample" -exec sh -c 'cp {} $(dirname {})/$(basename {} .cfg-sample).cfg' \;Just to confirm;
ls -1 /usr/local/etc/nagios/cgi.cfg
cgi.cfg-sample
nagios.cfg
nagios.cfg-sample
objects
resource.cfg
resource.cfg-samplels -1 /usr/local/etc/nagios/objects/commands.cfg
commands.cfg-sample
contacts.cfg
contacts.cfg-sample
localhost.cfg
localhost.cfg-sample
printer.cfg
printer.cfg-sample
switch.cfg
switch.cfg-sample
templates.cfg
templates.cfg-sample
timeperiods.cfg
timeperiods.cfg-sample
windows.cfg
windows.cfg-sampleIf you want, you can configure the Nagios objects as you wish. for in this setup, we will go with the default settings.
Set the ownership of Nagios configuration files to nagios user.
chown -R nagios:nagios /usr/local/etc/nagios/Create Nagios Basic Authentication Users
Create users and password for authenticating to Nagios web resources;
htpasswd -c /usr/local/www/nagios/htpasswd.users kifarunixThe default authentication user is nagiosadmin. If you use a different user, you will need to make changes on the cgi.cfg file by replacing the user nagiosadmin appropriatetly.
For example, in our case, we use the user kifarunix and hence, to replace the default nagiosadmin user use the command below;
sed -i.org 's/nagiosadmin/kifarunix/g' /usr/local/etc/nagios/cgi.cfgTo add another user to the file, omit option -c in the command above.
Verify Nagios configuration data
You can now verify all configuration data just to ensure that there is no error;
nagios -v /usr/local/etc/nagios/nagios.cfgSample output;
Nagios Core 4.4.6
Copyright (c) 2009-present Nagios Core Development Team and Community Contributors
Copyright (c) 1999-2009 Ethan Galstad
Last Modified: 2020-04-28
License: GPL
Website: https://www.nagios.org
Reading configuration data...
Read main config file okay...
Read object config files okay...
Running pre-flight check on configuration data...
Checking objects...
Checked 8 services.
Checked 1 hosts.
Checked 1 host groups.
Checked 0 service groups.
Checked 1 contacts.
Checked 1 contact groups.
Checked 24 commands.
Checked 5 time periods.
Checked 0 host escalations.
Checked 0 service escalations.
Checking for circular paths...
Checked 1 hosts
Checked 0 service dependencies
Checked 0 host dependencies
Checked 5 timeperiods
Checking global event handlers...
Checking obsessive compulsive processor commands...
Checking misc settings...
Total Warnings: 0
Total Errors: 0
Things look okay - No serious problems were detected during the pre-flight checkRunning Nagios on FreeBSD
Start and enable Nagios to run on system boot;
sysrc nagios_enable="YES"service nagios startCheck status;
service nagios statusnagios is running as pid 3584.Running Apache
Enable Apache to run on system boot;
sysrc apache24_enable="YES"Perform sanity check of Apache configuration;
apachectl configtestIf you get the output, Syntax OK, start Apache.
service apache24 restartAccessing Nagios Web Interface on FreeBSD
You can now access your Nagios Web interface using the url http://server-host-name-OR-IP or http://server-host-name-OR-IP/nagios or http://server-host-name-OR-IP/nagios/.
Enter your basic authentication credentials;
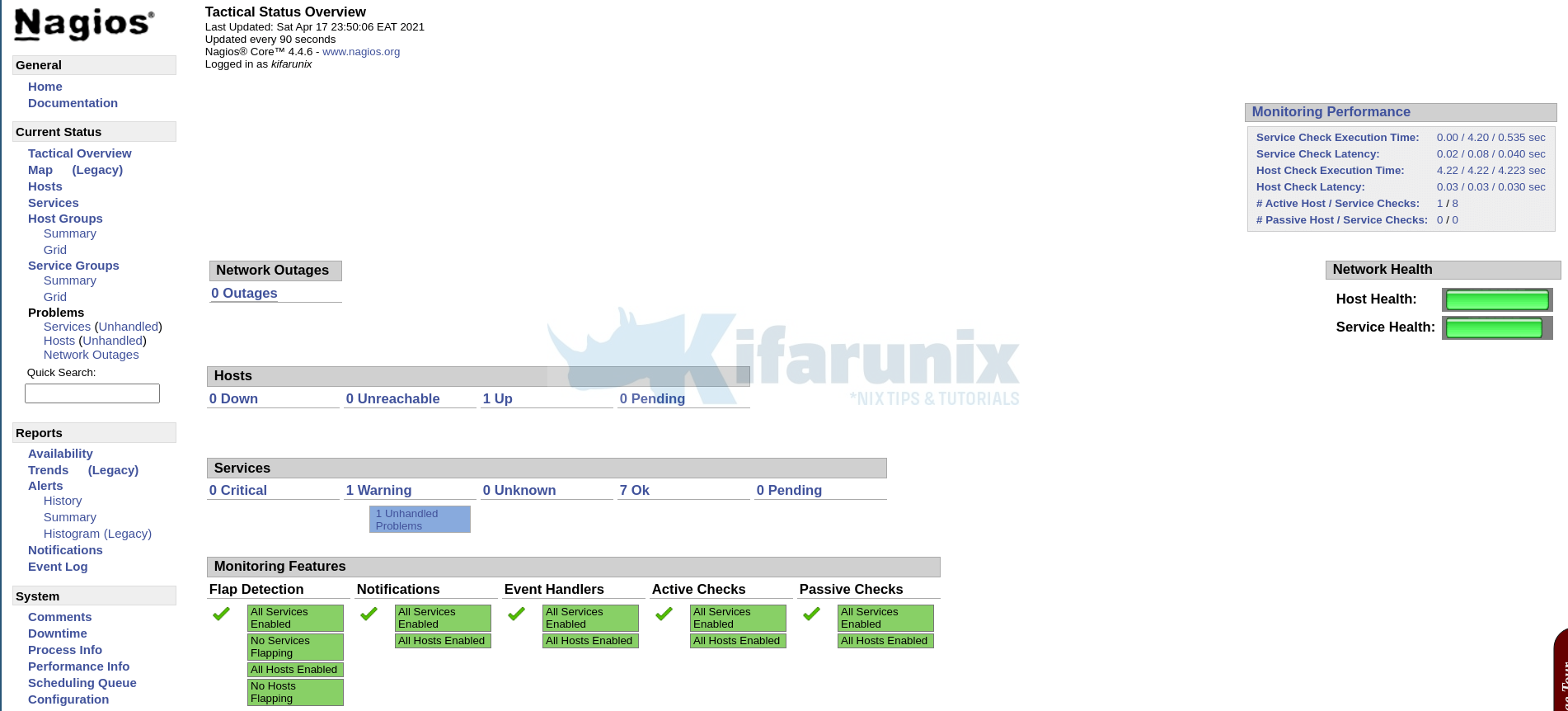
Click sign in to proceed to dashboard.
And there you go.
Other Tutorials
Add Hosts to Nagios Server For Monitoring
Configure Nagios Email Notification Using Gmail
Monitor SSL/TLS Certificates Expiry with Nagios
Monitor Linux Hosts using Nagios check_by_ssh Plugin
Nagios SNMP Monitoring of Linux Hosts on AlienVault USM/OSSIM