Welcome to our tutorial on how to configure OpenLDAP authentication on MacOS X. Fortunately, MacOS X systems ship with a utility called Directory Utility. According to Apple Support, Directory Utility can be used to add and configure advanced connections to directory servers. When configured, your Mac OS can access the directory servers for user information and other administrative data stored in the directory domain of directory servers. Some of the directory servers that can be configured include Open Directory, Active Directory, or LDAP directory server.
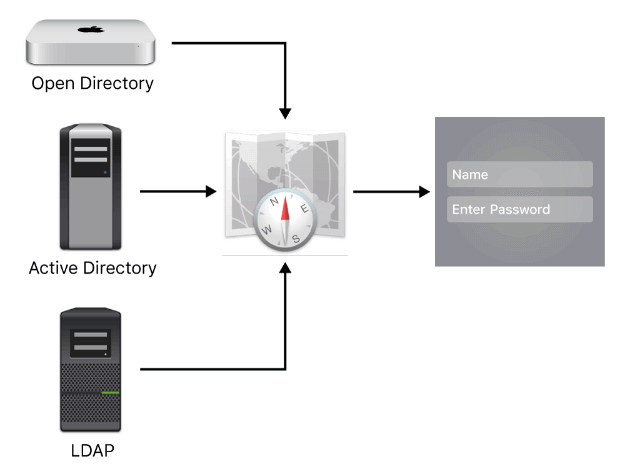
Configure OpenLDAP Authentication on MacOS X
Follow through this guide to join your MacOS X system to an OpenLDAP directory to facilitate user authentication.
NOTE: This guide is based on Mac OS Sierra.
Configure Access OpenLDAP Directory
To begin with, you need to configure access to an OpenLDAP directory server on your MacOS X using the Directory Utility app.
To open the Directory Utility app, click the search icon at the top right corner and type Directory Utility. Press Enter to open the app.
You can as well access the directory utility from Users and Groups preferences > Login Options > Network Account Server > Join > Open Directory Utility.
When the app opens up, click the lock at the bottom left and authenticate as an administrative user for you to be able to modify your directory services configuration.
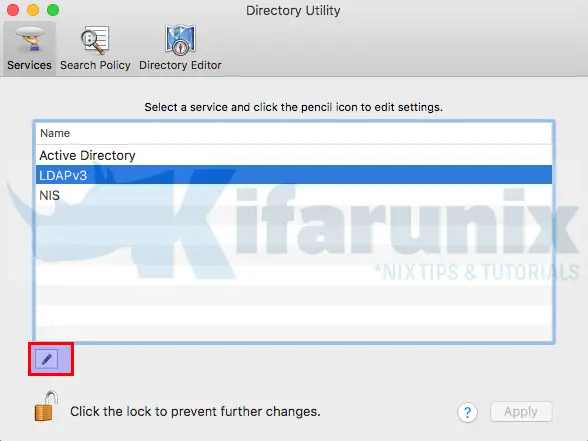
In this demo, we are using OpenLDAP as our directory server. As such, select LDAPv3 from the list and click the pen like Edit button to configure the selected plugin.
On the setup wizard that opens up, click New to add a new OpenLDAP directory server. Enter the resolvable hostname or IP address of the OpenLDAP server.
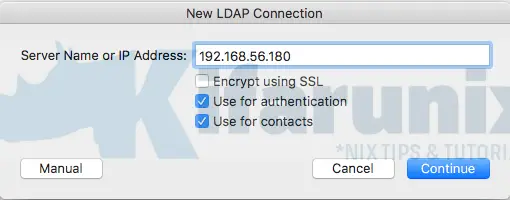
If you are using LDAP with SSL, be sure to check the SSL box.
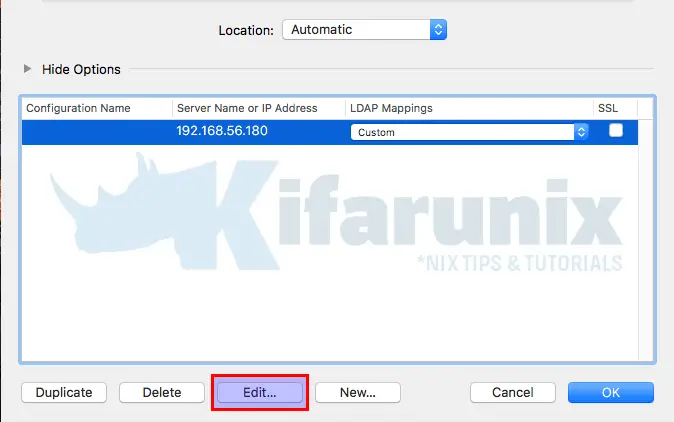
Click Manual to enter manually configure your OpenLDAP server directory settings. Next click Edit to edit the connection.
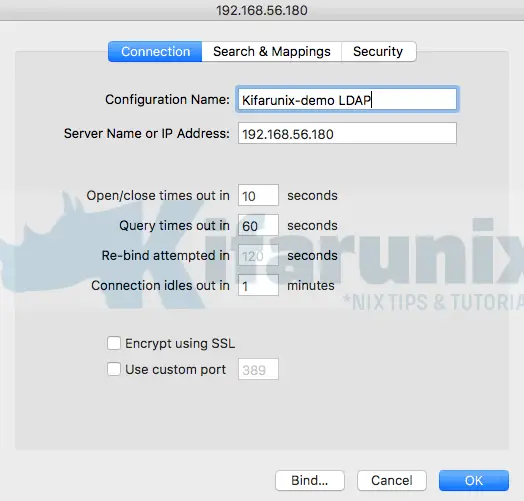
Under the Connection tab, set the name of the connection, change address if need be, choose whether to use SSL and custom port, if need be, and you can leave other default settings.
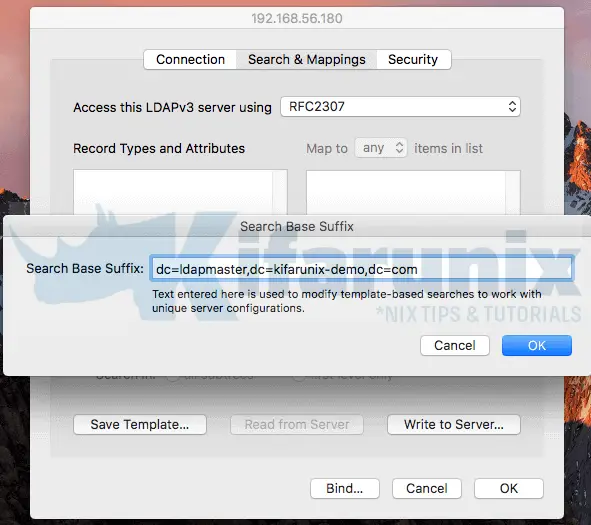
Under Search and Mappings, select RFC2307 as the mapping template for LDAPv3 and enter your OpenLDAP directory search base suffix.
Under Security, click the check box, Use Authentication when connecting, and enter your OpenLDAP BIND DN and its password.
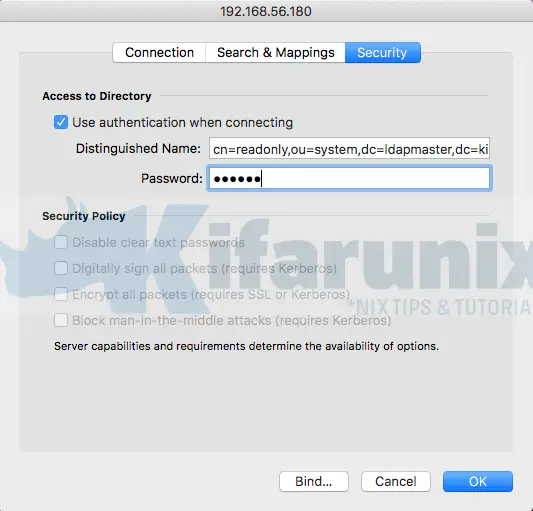
Click OK when done with settings. Your connection settings now looks like as in below;
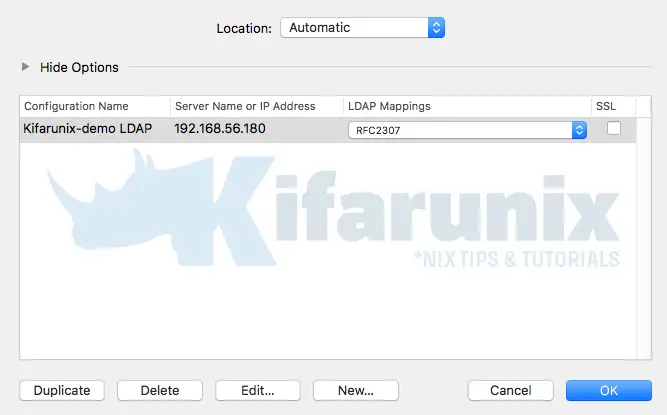
Click OK to close the configuration wizard. This takes you back to Directory Utility app.
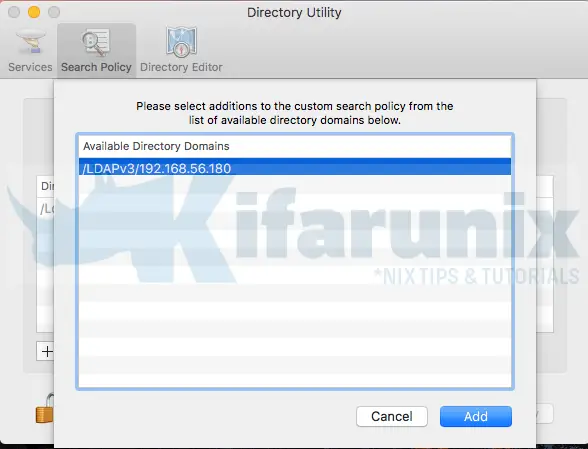
Click on Search Policy tab and choose where to search for user information. In this case, we will select Custom Path and click the + (plus) sign to add your LDAP directory domain. Select the domain connection and click add.
The Search Policy tab should now look like;
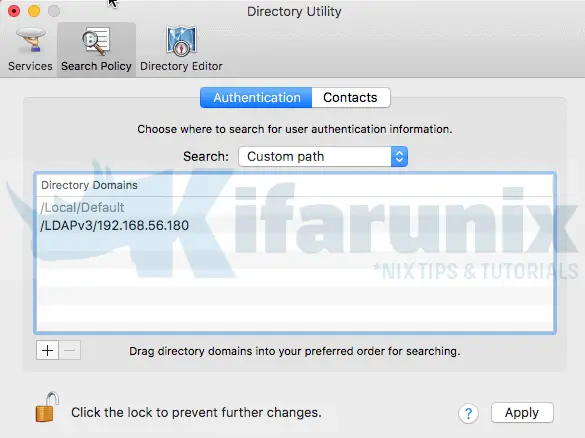
You can do the same for Contacts.
Verify MacOS OpenLDAP User Authentication
You can now verify user authentication by clicking on Directory Editor tab on Directory Utility app.
Select Viewing Users in node /LDAPv3/yourLDAPaddress. To verify user authentication, click the padlock (Not authenticated). Enter the LDAP username and password to verify authentication. If authentication is successful, you should now be able to see your LDAP users and their details;
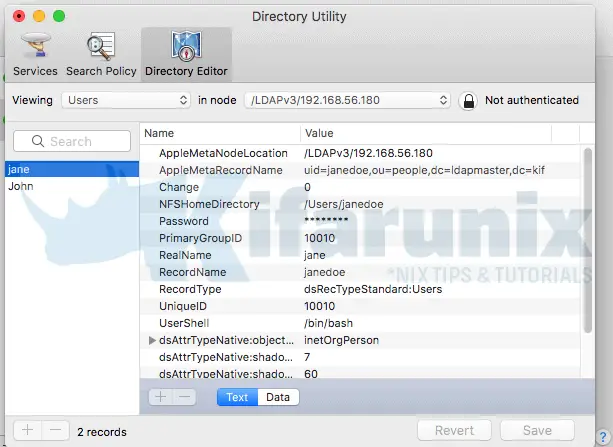
Next, save the settings by clicking on the Services tab and clicking Apply. If you want, click the lock to prevent further changes.
You can as well verify user information using id command on the terminal. For example, we have user, janedoe, on our LDAP directory. To verify its details;
id janedoeuid=10010(janedoe) gid=10010(janedoe) groups=10010(janedoe),223(com.apple.access_loginwindow),702(com.apple.sharepoint.group.2),12(everyone),62(netaccounts),701(com.apple.sharepoint.group.1)Login as OpenLDAP User on MacOS
Before you can be able to login as an LDAP user or a directory user, you need to enable network users to login. Hence;
- Open Users and Groups preference settings
- Click the padlock to make changes
- Click on Login Options.
- Ensure that your Network Account Server is connected. Otherwise join the server.
- Check the Allow network users to login at login Window. Click Options to allow all users or specific network users to login at login.
- Once done, click the lock to prevent further changes.
Note that you also need to create a home directory for the user on the system as per the LDAP entry. Below is our sample LDAP user information.
ldapsearch -Y EXTERNAL -H ldapi:/// -b "ou=people,dc=ldapmaster,dc=kifarunix-demo,dc=com" uid=janedoe -LLL -Qdn: uid=janedoe,ou=people,dc=ldapmaster,dc=kifarunix-demo,dc=com
objectClass: inetOrgPerson
objectClass: posixAccount
objectClass: shadowAccount
objectClass: extensibleObject
uid: janedoe
cn: jane
sn: Doe
loginShell: /bin/bash
uidNumber: 10010
gidNumber: 10010
shadowMax: 60
shadowMin: 1
shadowWarning: 7
shadowInactive: 7
shadowLastChange: 0
homeDirectory: /Users/janedoe
userPassword:: e1NTSEF9Rmpjb0VzRE8rRlFBcEp1UWNFclVhWGdmNFYyNGdxdkI=Therefore, the home directory we will create for the user, janedoe, is /Users/janedoe.
mkdir /Users/janedoechown -R janedoe:janedoe /Users/janedoeNow, log out and try to login as an LDAP user.

If the login fails, reboot your machine and retry. Ensure that your system is connected to LDAP directory server.
Upon successful authentication, go through your new account setup and there you go, logged in to your Mac OS X via your OpenLDAP directory server.
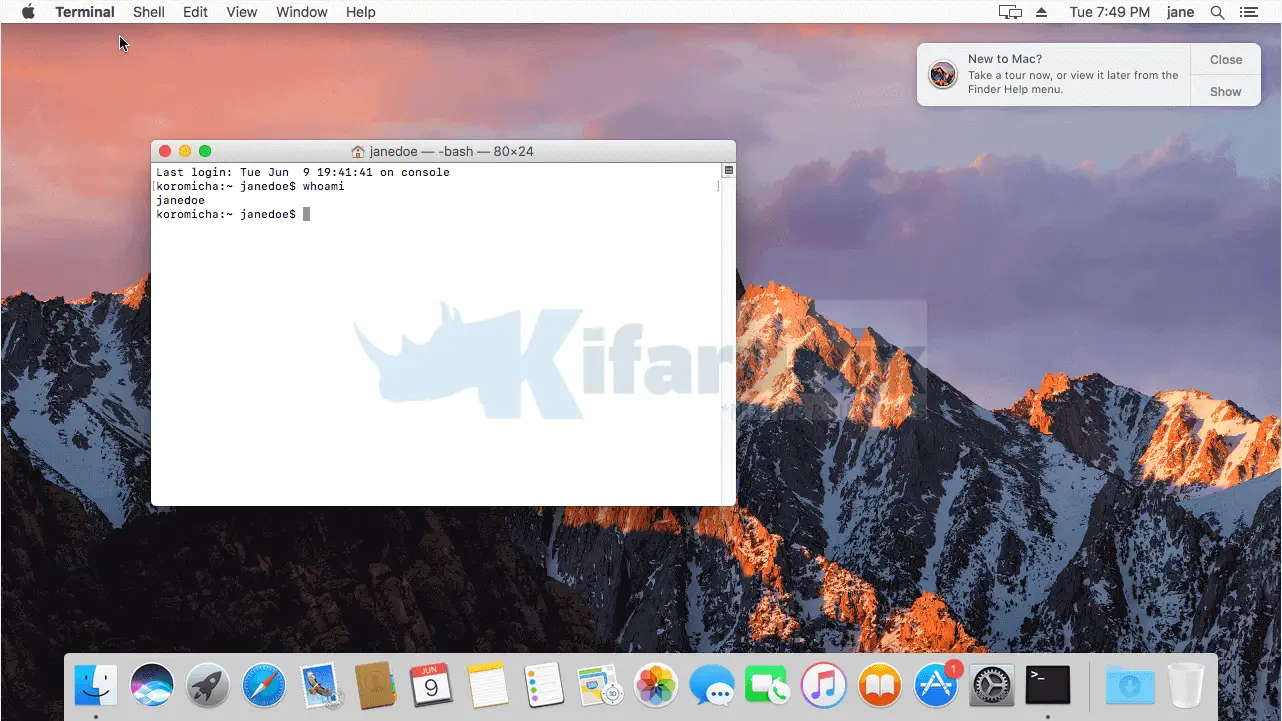
You have successfully configured OpenLDAP authentication on MacOS X. One thing to note is that, any network user, provided by the OpenLDAP directory can login to your system. In our next guide, we will learn how to restrict OpenLDAP authentication on MacOS X to specific user.
Configure Offline Authentication by following the link below;
Configure Offline Authentication via OpenLDAP on MacOS X
That brings us to the end of our tutorial on how to configure OpenLDAP authentication on MacOS X.
Reference
Related Tutorials
Install and Setup OpenLDAP Server on Ubuntu 20.04
Install and Setup phpLDAPadmin on Ubuntu 20.04

