Welcome to out tutorial on how to configure Bind DNS server using Webmin on Debian 11. Webmin is a web-based control panel that allows system administrators to administer system administration tasks from web user interface.
Table of Contents
Configuring BIND DNS Server using Webmin on Debian
Install Webmin
You can follow the link below to install Webmin on Debian 11.
Login to Webmin as Administrative User
All the installations and configurations will be run as root in this guide. Therefore, login as a root user or a user with sudo rights.

Run System Update
Launch the terminal by pressing Alt+k. Next, run system package update command.
apt update -yClose the terminal once the update is done.
Install Bind DNS Server Module on Debian 11
Install Bind DNS server module by navigating to Dashboard > Un-used Modules > BIND DNS Server > Install Now. This will start to build Bind package and required dependencies for installation.
Once successfully build, click Install Now to install the Bind packages and all required dependencies.
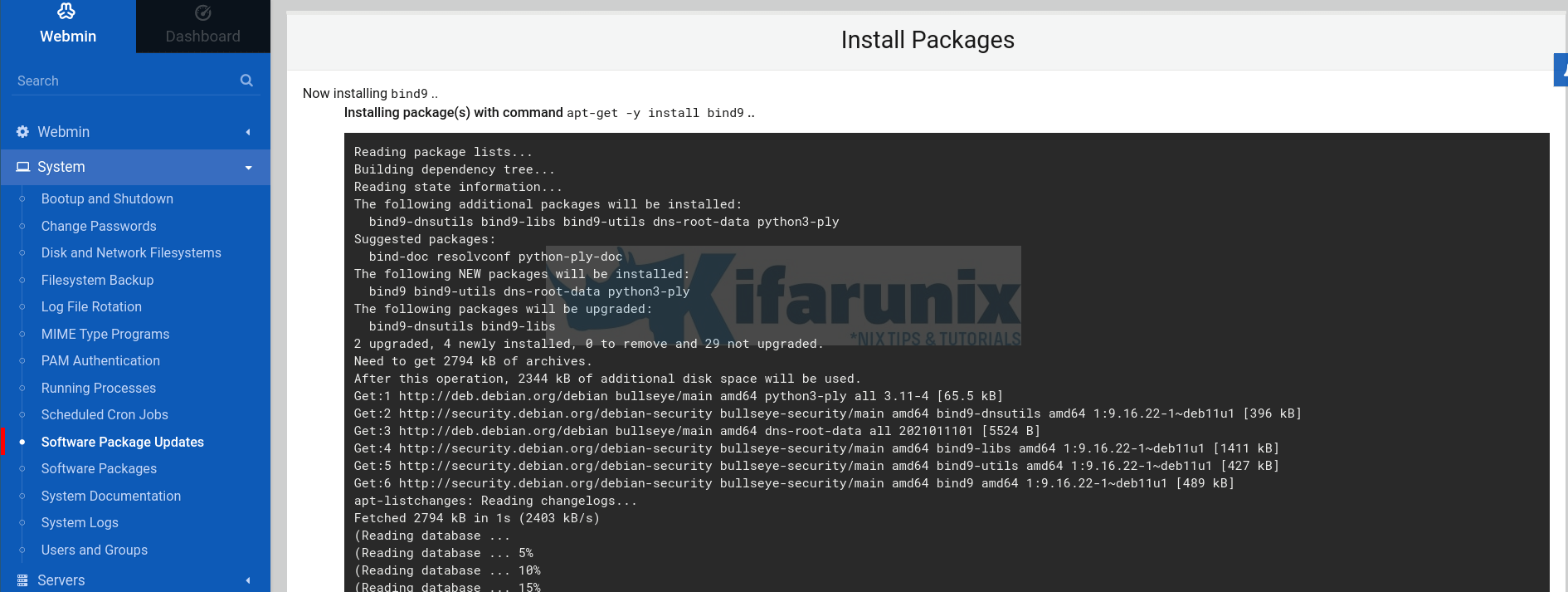
Configuring BIND DNS Server Using Webmin
Once the installation is complete, click Return to BIND DNS Server below the screen to go back to BIND DNS Server configuration interface.
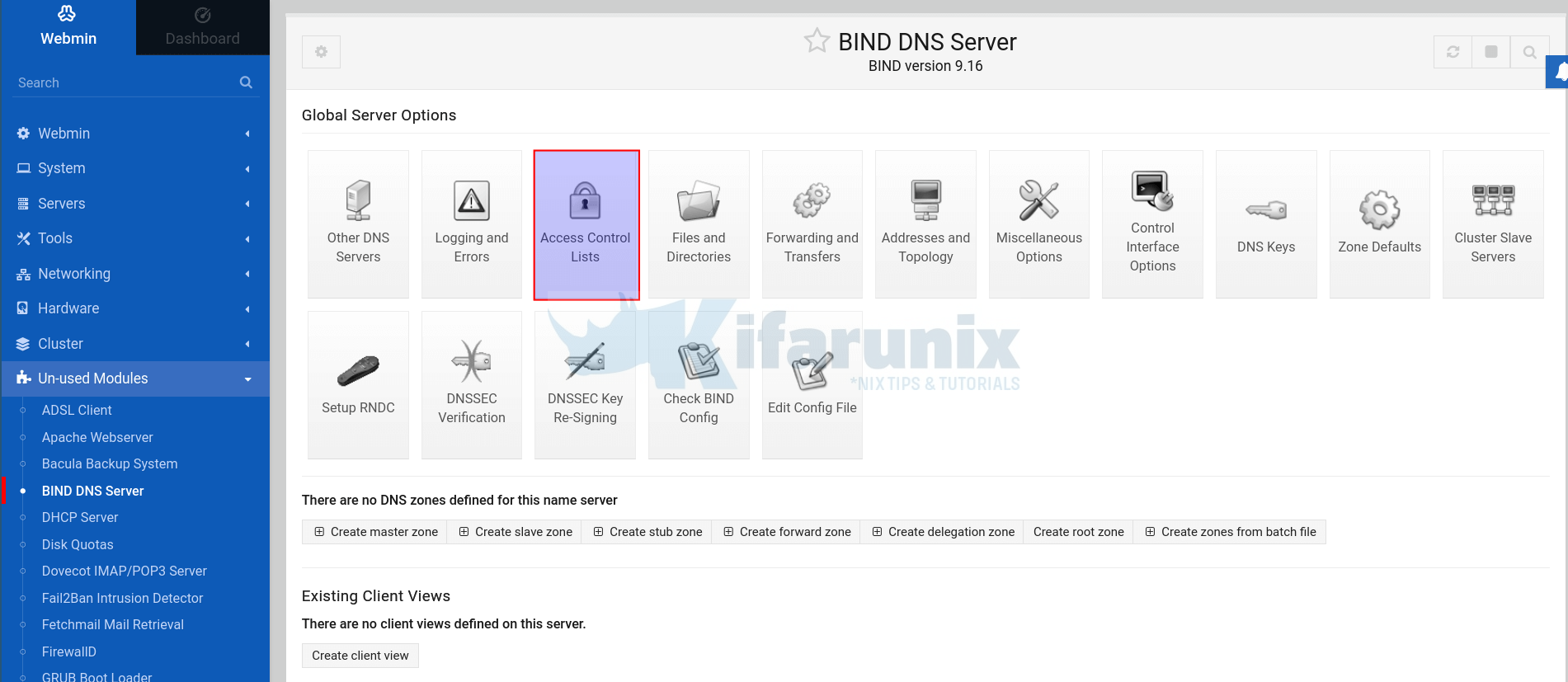
Configure Access Control List
To begin with, create an access control list for your DNS server.
ACLs allows you to specify the IP addresses or networks to deny or allow to query the DNS server.
To create the ACL:
- Click Access Control Lists, as higlighted in the screenshot above.
- Set the name of the ACL
- Add the IP addresses or the networks to allow to query your DNS server.
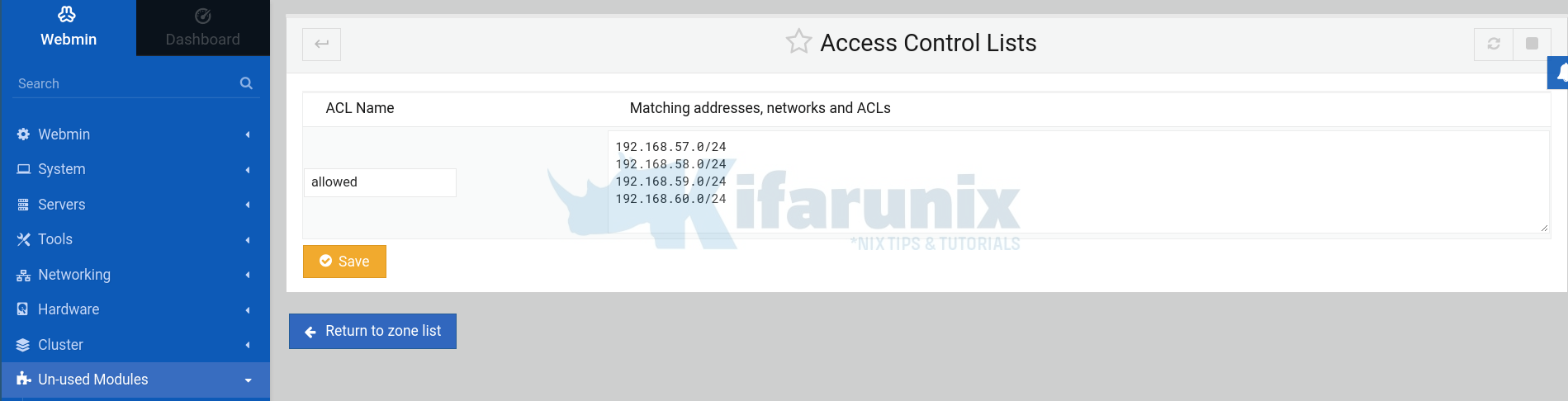
For example, we created an ACL called allowed to define the networks (192.168.[57-60].0/24) of the hosts allowed to query our DNS server.
Click Save and Return to zone list.
Define global server configuration options
Next, you need to configure BIND global configuration options.
The options statement is used to set up global options to be used by BIND such as:
- define the hosts that are allowed to ask ordinary DNS questions
- specify the location of the
namedworking directory - the types of queries allowed
- specify which hosts are allowed to make recursive queries through the DNS server
These configurations can be made on the /etc/bind/named.conf.options configuration file.
From BIND DNS Server interface:
- Click Edit Config File. By default, you will see the
/etc/bind/named.confconfiguration file selected. - Click on the drop down menu and select the
/etc/bind/named.conf.optionsconfiguration file. - Make the changes on the file as per your environment setup. Here is our sample configuration file;
options {
directory "/var/cache/bind";
recursion yes;
allow-recursion { localhost; allowed; };
listen-on port 53 { localhost; 192.168.58.22; };
allow-query { localhost; allowed; };
allow-transfer { none; };
forwarders {
192.168.58.1;
8.8.8.8;
};
dnssec-validation auto;
auth-nxdomain no;
listen-on-v6 { none; };
};
- Also see screenshot below;
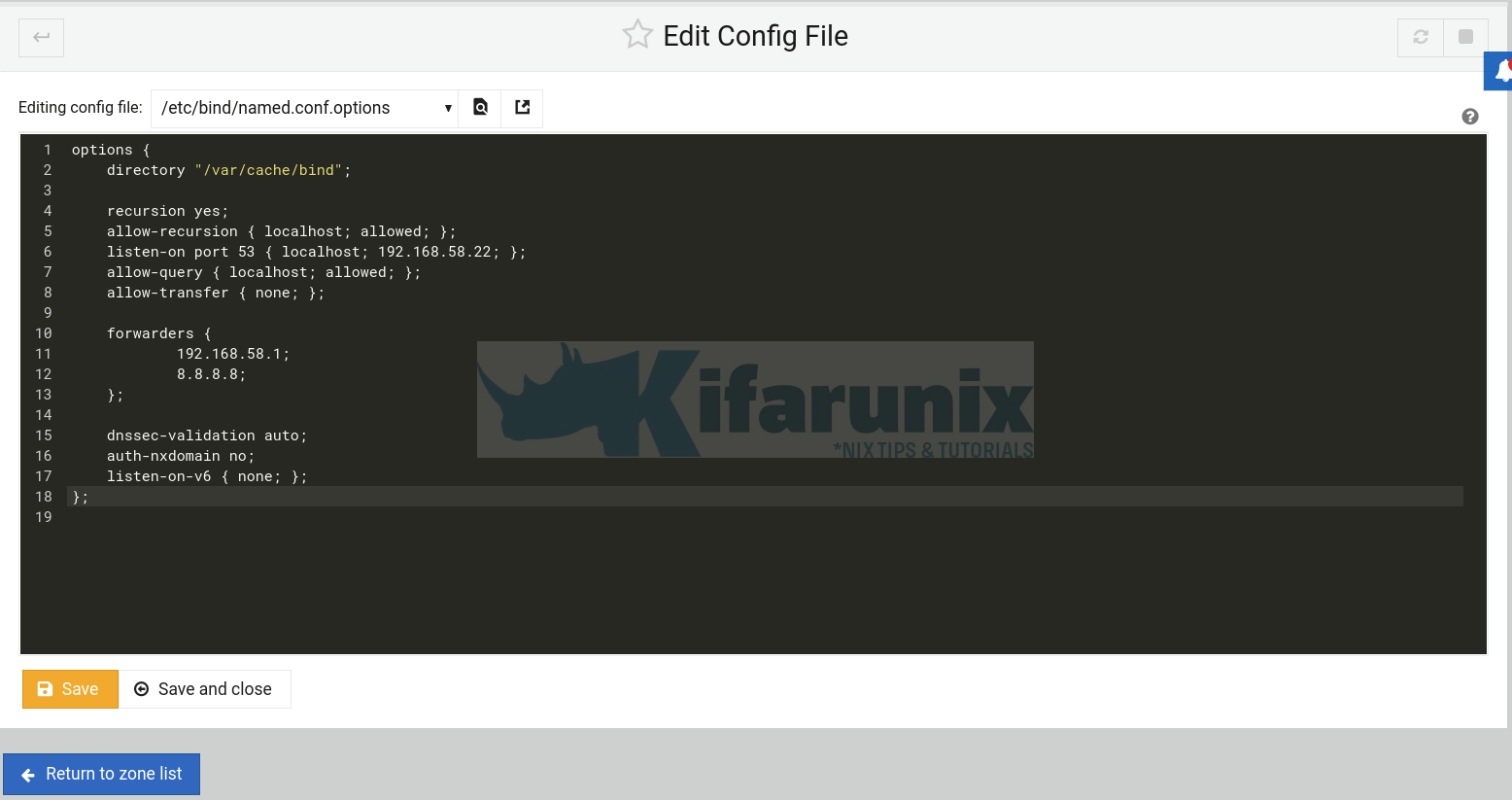
Click Save and close to return to zone list.
Some of the configuration options used above are;
- recursion – Specifies whether to act as a recursive server.
- allow-recursion – Defines hosts to allow recursive queries from.
- listen-on – Specifies the
IPv4network interface on which to listen for queries. - allow-query – Specifies which hosts are allowed to query the nameserver for authoritative resource records.
- allow-transfer – Specifies which secondary servers are allowed to request a transfer of the zone’s information.
- forwarders – Defines one or more IP addresses of name servers to query.
- dnssec-validation – Specifies whether to prove that resource records are authentic through DNSSEC. The default option is
yes. - auth-nxdomain – defines whether the server should answer authoritatively.
- listen-on-v6 – Specifies the
IPv6network interface on which to listen for queries.
Validate the Configuration Options
Next, you need to validate the configuration options made in the file above by clicking on Check BIND Config under the Bind DNS server global server options.
If there is no syntax error with the configuration file, you will see such a message as:
No errors were found in the BIND configuration file /etc/bind/named.conf or referenced zone files.
Click Return to zone list.
Create BIND DNS Server Master Zone Statements
Next, you need to create the master forward and reverse zone statements.
Click Create master zone on the BIND DNS server interface.
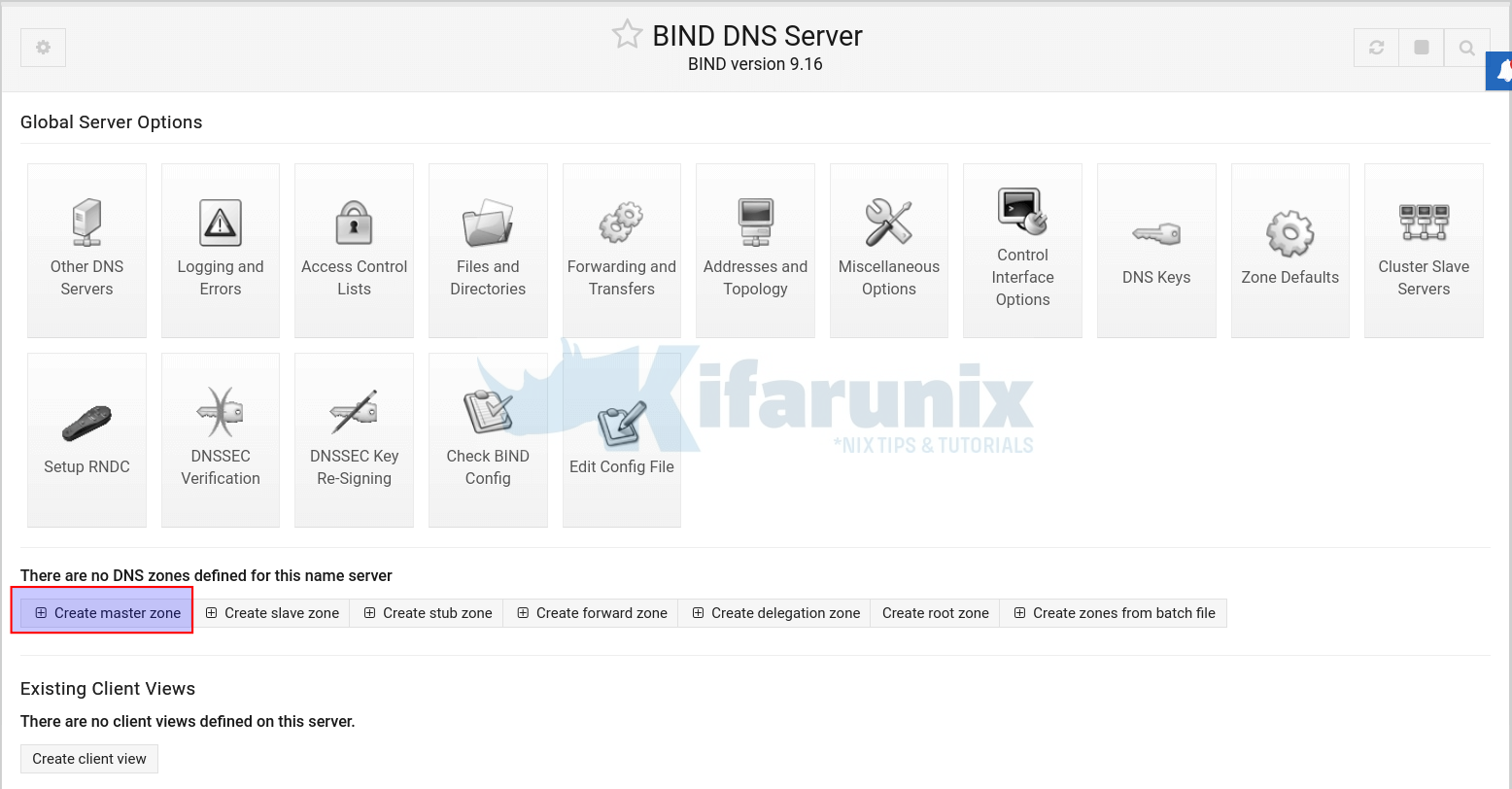
This will open up a wizard where you can define the zone statement details.
To begin with;
- Select the Zone type, Forward: Names to Addresses to create the forward zone statement.
- Enter the Domain name
- Automatic Records file
- Master DNS server FQDN, Add NS record
- Email address. Note, the @ in the email address will be converted to dot (.) in SOA records.
- Use zone template, we choose No.
- Add reverses fro template addresses
- Refresh time, Transfer retry time, Expiry time, cache time.
- Click Create to create the master forward zone statement.
- Click Return to zone list
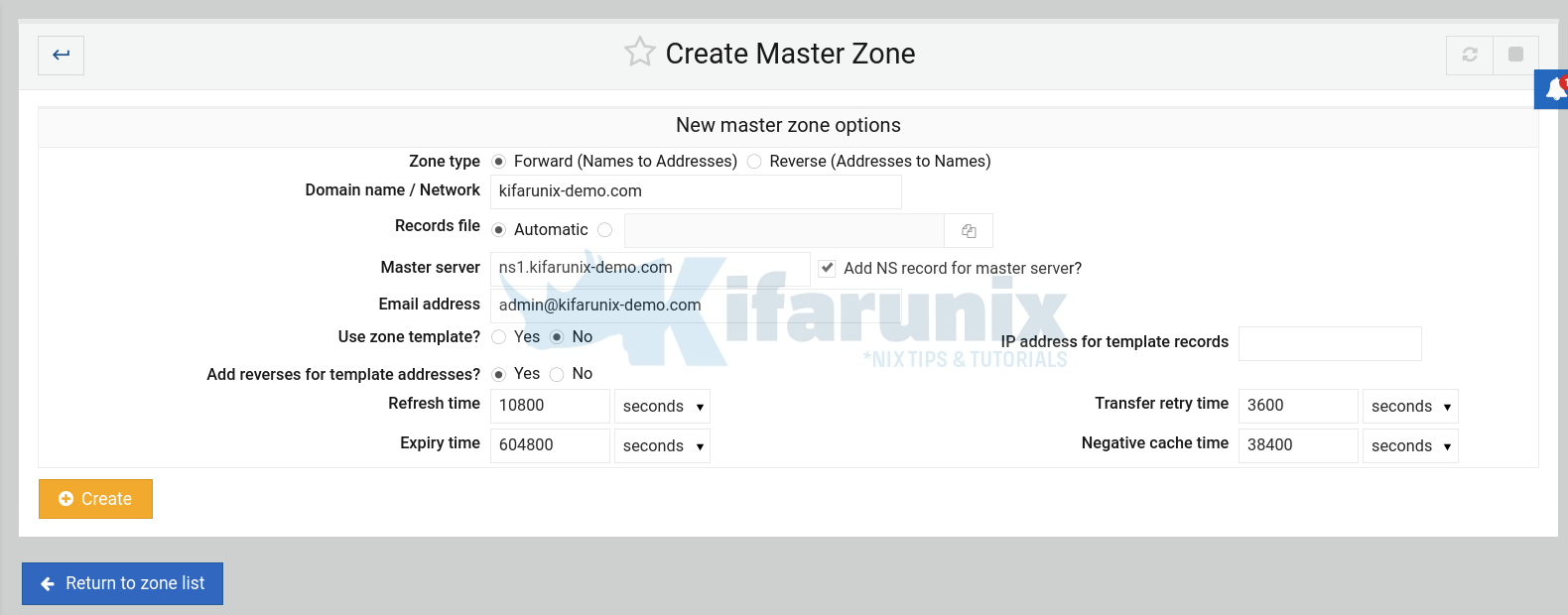
Next, create reverse zone statement by > Create master zone. This time round, select Reverse: Addresses to Names.
Note how the IP address is set.
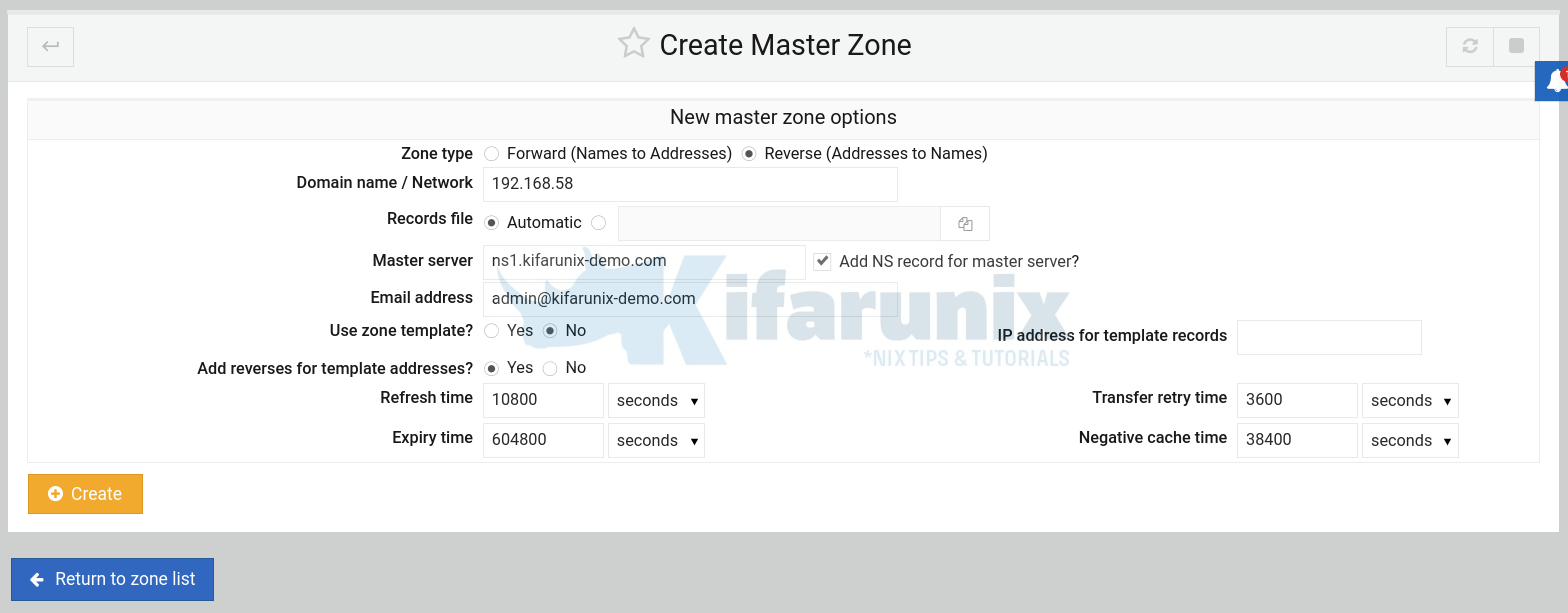
Click Create to create the master reverse zone statement.
Next, click Return to Zone list.
If you have other Networks, ensure you create the reverse records for those networks. In this example, we have other networks, 192.168.60.0/24, 192.168.59.0/24.
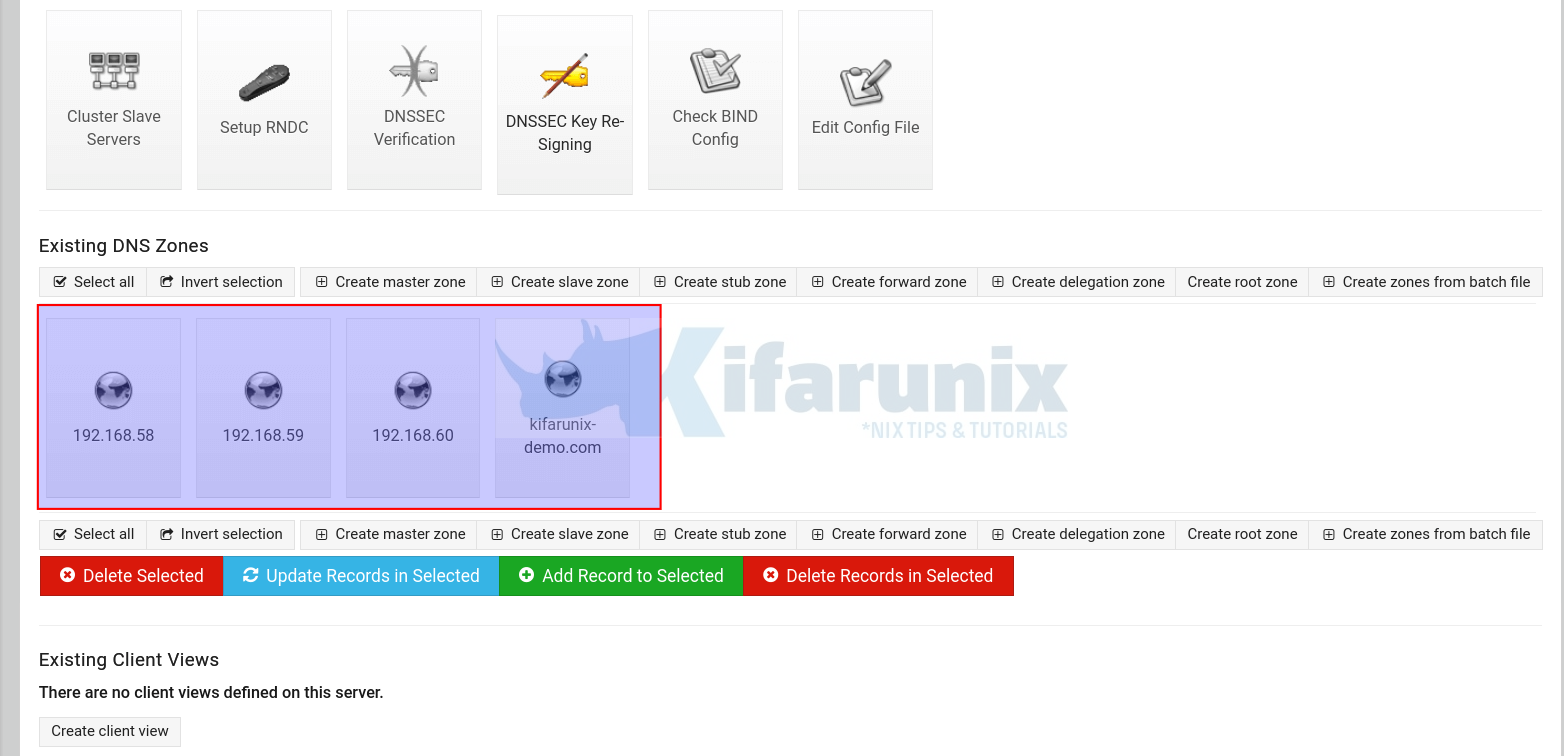
Setup the DNS A Records
Under existing DNS Zones, click your master forward zone, see example highlighted.
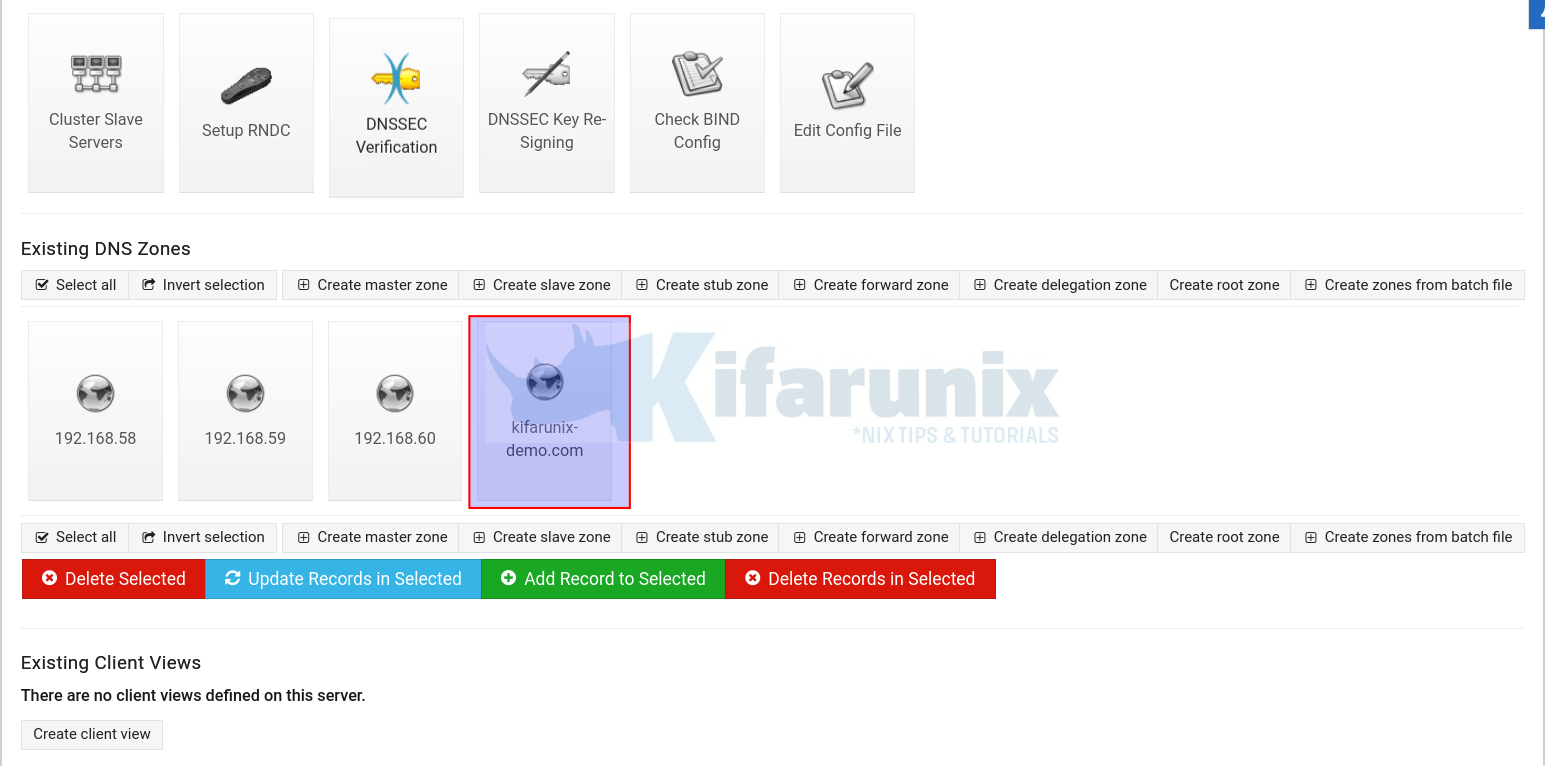
Click Addresses.
To begin with, set the A record for your DNS server.
Click Create to set the DNS server address A record.
Next, you can add more addresses for other hosts.
- Name, without the domain part
- IP address
- Update reverse records
- Click Create.
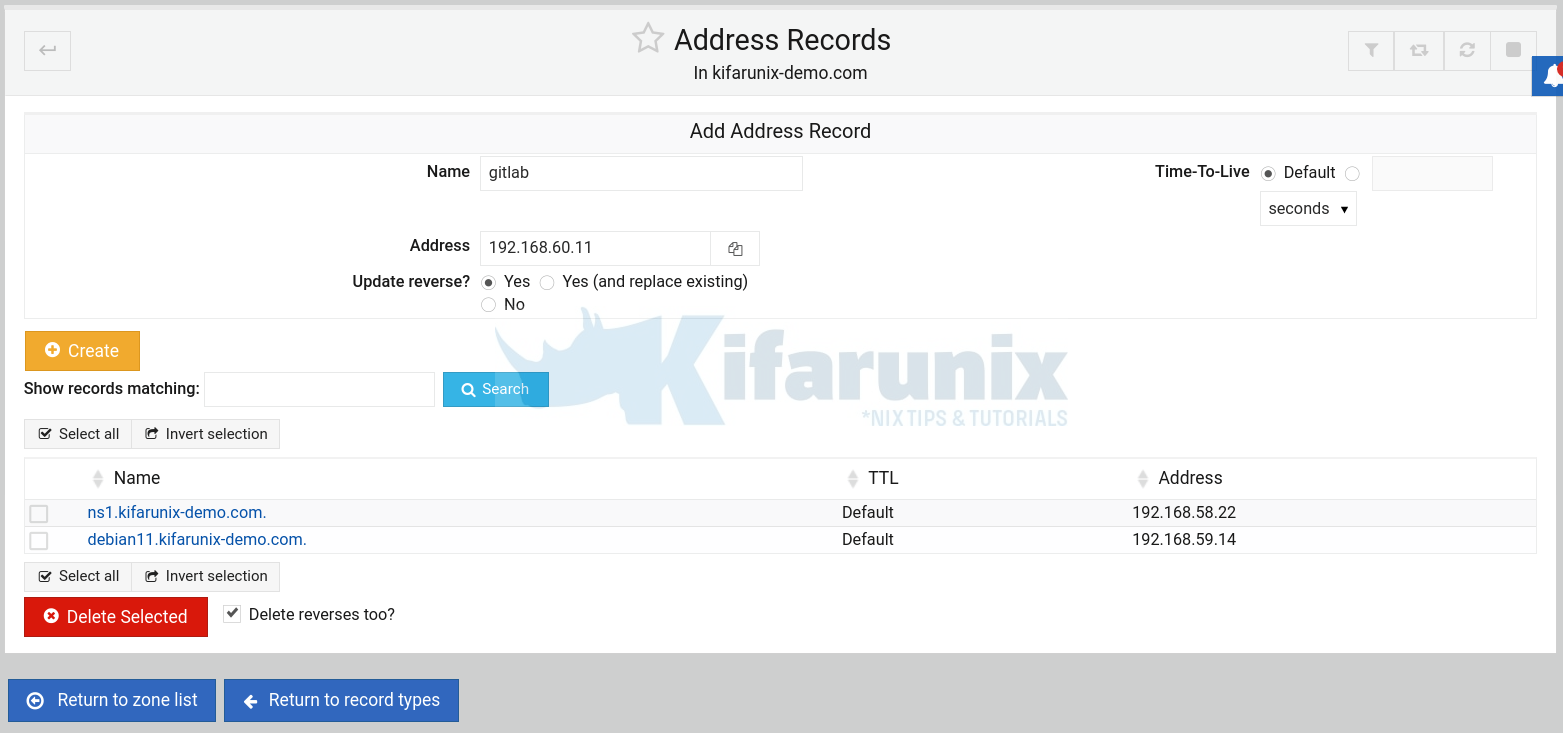
Once done, click Return to records type.
Create Name Server (NS) Records
Click Name Server on Master zone configuration page.
If the name server record is not already set:
- for the zone name, enter the your domain for example, kifarunix-demo.com
- for Name Server enter the FQDN of the DNS server, e.g ns1.kifarunix-demo.com
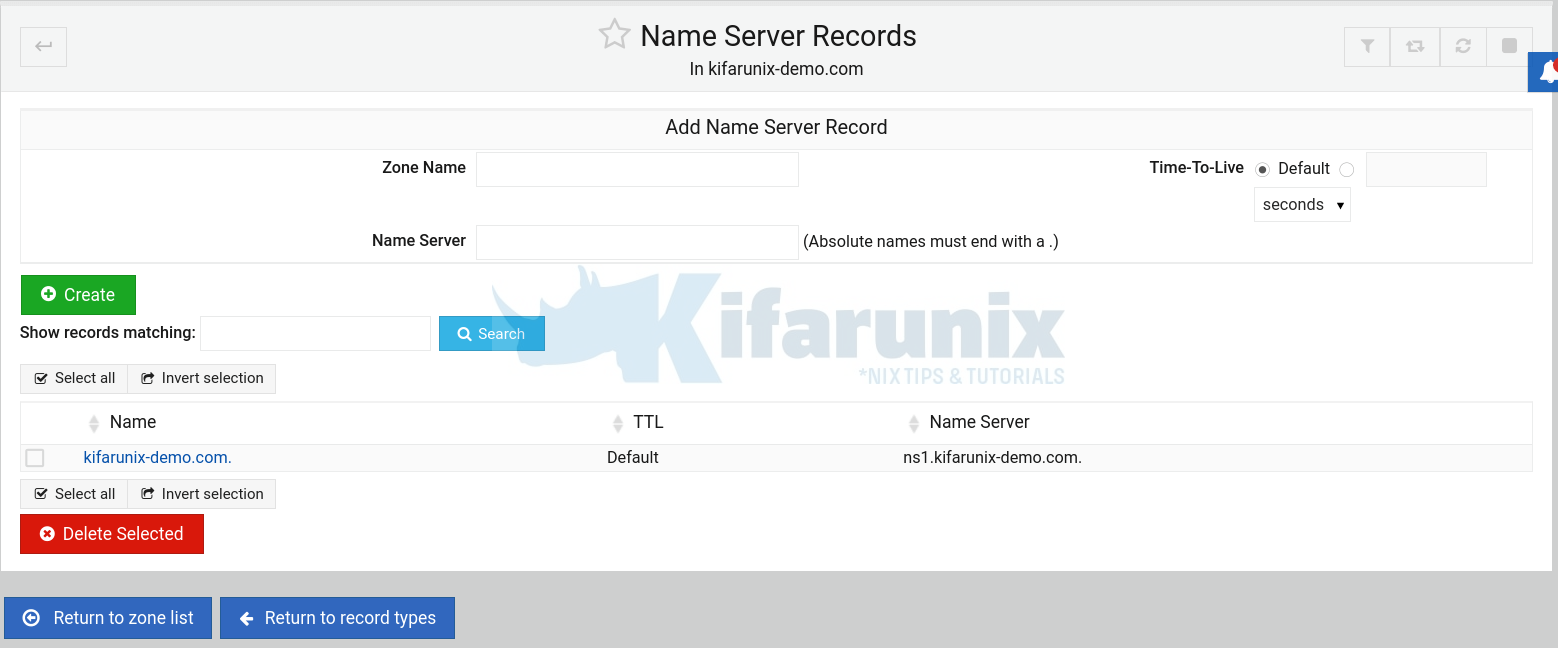
Click Create to add the name server records. Once done, click Return to zone list
You should now have master zones set (forward and reverse zones) with each having defined A records and PTR records respectively.
Verify Zone Configuration Syntax
To check the validity of the zone configuration, click on Check BIND config.
Running BIND
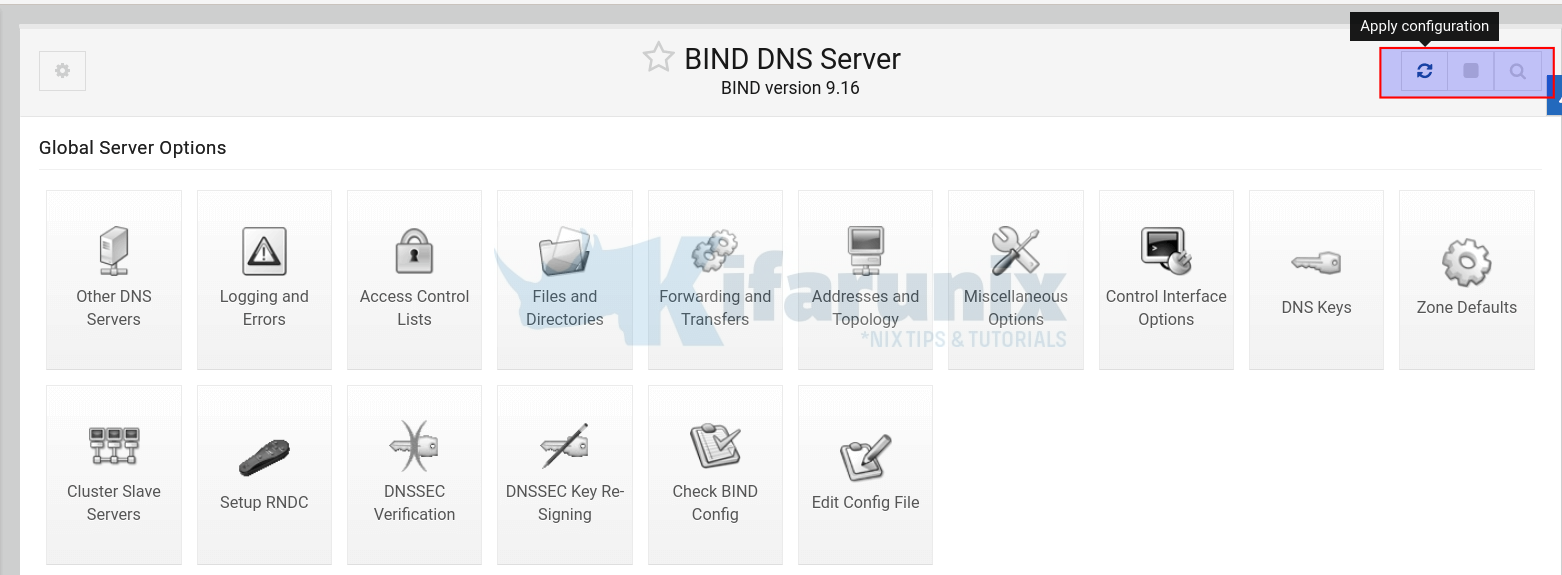
Click on the refresh button to apply the configurations.
Next, restart BIND on the web interface, stop and start it by clicking the stop and play buttons on the top right corner of the interface. See the highlighted section in the screenshot below.
If UFW is running, simply open the terminal (Alt+k) and run the command below to allow BIND.
ufw allow Bind9Verify if BIND is Working
To check if our DNS is working;
Try to resolve the DNS server hostnames using dig command.
dig ns1.kifarunix-demo.com @192.168.58.22
; <<>> DiG 9.16.1-Ubuntu <<>> ns1.kifarunix-demo.com @192.168.58.22
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 715
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 1232
; COOKIE: 4d8110c8fc7ed2cd01000000618774210bd99733b3045675 (good)
;; QUESTION SECTION:
;ns1.kifarunix-demo.com. IN A
;; ANSWER SECTION:
ns1.kifarunix-demo.com. 38400 IN A 192.168.58.22
;; Query time: 0 msec
;; SERVER: 192.168.58.22#53(192.168.58.22)
;; WHEN: Sun Nov 07 09:37:22 EAT 2021
;; MSG SIZE rcvd: 95
dig ns1.kifarunix-demo.com @192.168.58.22 +short192.168.58.22Perform Reverse Lookup (PTR Records)
dig -x 192.168.58.22 @192.168.58.22
; <<>> DiG 9.16.1-Ubuntu <<>> -x 192.168.58.22 @192.168.58.22
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 46718
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 1232
; COOKIE: c6927d40a2a20bb001000000618774c74e25a3ed4b260fbe (good)
;; QUESTION SECTION:
;22.58.168.192.in-addr.arpa. IN PTR
;; ANSWER SECTION:
22.58.168.192.in-addr.arpa. 38400 IN PTR ns1.kifarunix-demo.com.
;; Query time: 0 msec
;; SERVER: 192.168.58.22#53(192.168.58.22)
;; WHEN: Sun Nov 07 09:40:08 EAT 2021
;; MSG SIZE rcvd: 119
using nslookup command;
nslookup debian11.kifarunix-demo.com 192.168.58.22Server: 192.168.58.22
Address: 192.168.58.22#53
Name: debian11.kifarunix-demo.com
Address: 192.168.59.14nslookup 192.168.59.14 192.168.58.2214.59.168.192.in-addr.arpa name = debian11.kifarunix-demo.com.Using host command;
host gitlab.kifarunix-demo.com 192.168.58.22Using domain server:
Name: 192.168.58.22
Address: 192.168.58.22#53
Aliases:
gitlab.kifarunix-demo.com has address 192.168.60.11Reverse Lookup of DNS Server hostname.
host 192.168.60.11 192.168.58.22Using domain server:
Name: 192.168.58.22
Address: 192.168.58.22#53
Aliases:
11.60.168.192.in-addr.arpa domain name pointer gitlab.kifarunix-demo.com.Well, there you go. You have learnt how to Setup Bind DNS Using Webmin on Debian 11.
Related Tutorials
Install and Setup BIND DNS server on Rocky Linux 8

