
In this blog post, you’ll learn how to patch sudo CVEs 2025-32462 & 2025-32463 using Ansible AWX to secure your Linux infrastructure against critical privilege escalation vulnerabilities that allow local attackers to gain root access. These recently discovered flaws impact millions of systems worldwide and require immediate attention from security teams.
In late June 2025, cybersecurity researchers at Stratascale Cyber Research Unit (CRU) disclosed two critical vulnerabilities in the widely used sudo utility that powers privileged access across Linux and Unix systems. With sudo installed on virtually every Linux distribution and macOS system, these vulnerabilities represent a significant security risk for organizations managing large-scale infrastructure.
Table of Contents
Patch Sudo CVEs 2025-32462 & 2025-32463 using Ansible AWX
Understanding the 2025 Sudo Vulnerabilities
CVE-2025-32462: Host Check Bypass Vulnerability
CVE-2025-32462 is a subtle yet impactful vulnerability affecting sudo versions:
- Legacy: 1.8.8 through 1.8.32
- Stable: 1.9.0 through 1.9.17
Although currently rated with a relatively low MITRE CNA CVSS score of 2.8, this flaw allows attackers to bypass host-based restrictions and execute commands as root, posing a significant risk in environments that rely heavily on hostname-based sudo policies.
Technical Details:
- Vulnerability Type: Policy-check flaw causing host restriction bypass
- Attack Vector: Local privilege escalation
- Affected Component: Improper handling of the
-h/--hostoption in sudo’s policy evaluation - Duration: Undetected for approximately 12 years since version 1.8.8
The vulnerability stems from sudo’s mishandling of the -h/--host option, which was intended only for listing privileges on other hosts (sudo -l), but was accepted with other commands. This allows attackers to bypass hostname restrictions and escalate privileges despite configured policies.
CVE-2025-32463: Critical Chroot Privilege Escalation
CVE-2025-32463 represents a more severe threat with a MITRE CNA CVSS score of 9.3 (Critical). Dubbed a “chroot to root” bug, carries a Critical rating (CVSS 9.3) and affects versions 1.9.14 through 1.9.17; it enables attackers to load malicious libraries with root privileges.
Technical Details:
- Vulnerability Type: Privilege escalation via shared library loading
- Attack Vector: Local exploitation through chroot option
- Affected Versions: Sudo 1.9.14 through 1.9.17
- Introduction Timeline: CVE-2025-32463 was introduced in June 2023 with version 1.9.14
The vulnerability exploits sudo’s chroot functionality. The vulnerability arises from a change introduced in sudo v1.9.14, which allows an attacker to trick sudo into loading an arbitrary shared library by creating a /etc/nsswitch.conf file under a user-specified root directory. Although the vulnerability involves the sudo chroot feature, it does not require any sudo rules to be defined for the user.
Affected Sudo Versions
Understanding which sudo versions are vulnerable is crucial for prioritizing patching efforts:
CVE-2025-32462 (Host Check Bypass)
- Affected Versions: 1.8.8 – 1.8.32, 1.9.0 – 1.9.17
- First Vulnerable Release: sudo 1.8.8 (released approximately 12 years ago)
- Scope: Extremely broad, affecting virtually all sudo installations
CVE-2025-32463 (Chroot Privilege Escalation)
- Affected Versions: 1.9.14 – 1.9.17
- First Vulnerable Release: sudo 1.9.14 (released June 2023)
- Scope: More recent installations, but still widespread
Fixed Sudo Versions
The current stable release of the sudo 1.9 branch is version 1.9.17p1, which addresses both vulnerabilities.
Distribution-Specific Patching Status
Ubuntu Systems
CVE-2025-32462:
| Ubuntu Release | Codename | Fixed sudo Version | Notes |
|---|---|---|---|
| Ubuntu 25.04 | Plucky | 1.9.16p2-1ubuntu1.1 | Available via security updates |
| Ubuntu 24.10 | Oracular | 1.9.15p5-3ubuntu5.24.10.1 | Available via security updates |
| Ubuntu 24.04 LTS | Noble | 1.9.15p5-3ubuntu5.24.04.1 | Available via security updates |
| Ubuntu 22.04 LTS | Jammy | 1.9.9-1ubuntu2.5 | Available via security updates |
| Ubuntu 20.04 LTS | Focal | 1.8.31-1ubuntu1.5+esm1 | Requires ESM |
| Ubuntu 18.04 LTS | Bionic | 1.8.21p2-3ubuntu1.6+esm1 | Requires ESM |
| Ubuntu 16.04 LTS | Xenial | 1.8.16-0ubuntu1.10+esm3 | Requires ESM |
| Ubuntu 14.04 LTS | Trusty | 1.8.9p5-1ubuntu1.5+esm8 | Requires ESM |
CVE-2025-32463:
| Ubuntu Release | Codename | Status | Fixed sudo Version |
|---|---|---|---|
| Ubuntu 25.04 | Plucky | Fixed | 1.9.16p2-1ubuntu1.1 |
| Ubuntu 24.10 | Oracular | Fixed | 1.9.15p5-3ubuntu5.24.10.1 |
| Ubuntu 24.04 LTS | Noble | Fixed | 1.9.15p5-3ubuntu5.24.04.1 |
| Ubuntu 22.04 LTS | Jammy | Not affected | — |
| Ubuntu 20.04 LTS | Focal | Not affected | — |
| Ubuntu 18.04 LTS | Bionic | Not affected | — |
| Ubuntu 16.04 LTS | Xenial | Not affected | — |
| Ubuntu 14.04 LTS | Trusty | Not affected | — |
Refer to:
Debian Systems
CVE-2025-32462:
| Debian Suite | Codename | Vulnerable Version | Fixed Version |
|---|---|---|---|
| Stable | Bookworm | 1.9.13p3-1+deb12u1 | 1.9.13p3-1+deb12u2 |
| Oldstable | Bullseye | 1.9.5p2-3+deb11u1 | 1.9.5p2-3+deb11u2 |
| Testing | Trixie | < 1.9.16p2-3 | 1.9.16p2-3 |
| Unstable | Sid | < 1.9.16p2-3 | 1.9.16p2-3 |
Refer to https://security-tracker.debian.org/tracker/CVE-2025-32462
CVE-2025-32463:
| Debian Suite | Codename | Vulnerable Version | Fixed Version |
|---|---|---|---|
| Stable | Bookworm | Not Affected | Not Affected |
| Oldstable | Bullseye | Not Affected | Not Affected |
| Testing | Trixie | < 1.9.16p2-3 | 1.9.16p2-3 |
| Unstable | Sid | < 1.9.16p2-3 | 1.9.16p2-3 |
Refer to https://security-tracker.debian.org/tracker/CVE-2025-32463
Red Hat Enterprise Linux
Red Hat has acknowledged both vulnerabilities and has prepared security updates for affected RHEL versions.
CVE-2025-32462:
| Product / Service | Status | Errata (RHSA) | Fixed Version |
|---|---|---|---|
| RHEL 7 ELS | Fixed | RHSA-2025:10871 | sudo-1.8.23-10 |
| RHEL 8 | Fixed | RHSA-2025:10110 | sudo-1.9.5p2-1 |
| RHEL 8.2 AUS | Fixed | RHSA-2025:10518 | sudo-1.8.29-5 |
| RHEL 8.4 AMCUS & EUS-LL | Fixed | RHSA-2025:10383 | sudo-1.8.29-7 |
| RHEL 8.6 AMCUS / SAP / Telecom | Fixed | RHSA-2025:10520 | sudo-1.9.5p2-1 |
| RHEL 8.8 SAP / Telecom | Fixed | RHSA-2025:10836 | sudo-1.9.5p2-1 |
| RHEL 9 | Fixed | RHSA-2025:9978 | sudo-1.9.5p2-10 |
| RHEL 9.0 SAP | Fixed | RHSA-2025:10835 | sudo-1.9.5p2-7 |
| RHEL 9.2 SAP | Fixed | RHSA-2025:10779 | sudo-1.9.5p2-9 |
| RHEL 9.4 EUS | Fixed | RHSA-2025:10707 | sudo-1.9.5p2-10 |
| RHEL 10 | Affected | — | — |
| RHEL 6 | Not Affected | — | — |
| OpenShift 4.16 | Fixed | RHSA-2025:10781 | — |
| OpenShift 4.18 | Fixed | RHSA-2025:10767 | — |
| OpenShift 4.19 | Fixed | RHSA-2025:10771 | — |
You need Extended Lifecycle Support repos for RHEL 7.
For the affected versions that have their fixes released already, you can simply update the sudo package. Be sure to check the change log for the releases. Read more on Red Hat CVE 2025-32462 page.
CVE-2025-32463:
| Product / Service | Status | Notes |
|---|---|---|
| RHEL 10 | Affected | No fix yet |
| RHEL 6–9 | Not affected | No action needed |
| OpenShift 4 | Not affected | No action needed |
No action needed for RHEL 6, 7, 8, 9, or OpenShift. Monitor for updates for RHEL 10. Read more on Red Hat CVE 2025-32463 page.
Why Use Ansible AWX for Sudo Patching
Ansible AWX is a powerful tool for automating IT tasks, offering a web-based interface, role-based access control, and integration with version control systems. Unlike manual patching via package managers (e.g., apt or yum), AWX enables:
- Scalability: Apply patches across hundreds or thousands of servers simultaneously.
- Consistency: Ensure uniform application of updates and configurations.
- Auditability: Track changes and verify patch status through AWX’s job logs.
By using AWX, you can reduce human error, save time, and maintain compliance with security standards like CIS benchmarks.
Prerequisites for Patching with Ansible AWX
Before patching, ensure your environment is ready:
- Ansible AWX Setup: Install AWX on a supported platform. Refer to this guide to deploy AWX on Kubernetes cluster: Working Guide: Deploy AWX on Kubernetes Cluster with AWX Operator.
- Inventory Configuration: Define your target Linux hosts (e.g., Ubuntu, Red Hat) in AWX’s inventory.
- Package Repository Access: Ensure hosts have access to updated package repositories (e.g., Ubuntu’s main repository, Red Hat’s yum repos).
- Credentials: Configure AWX with SSH or sudo credentials for host access.
- Playbook Availability: Create an Ansible playbook to upgrade Sudo.
Here is my sample sudo patching via Ansible AWX project structure (on the local host):
cd ~/Documents/projects/sudo-patchingtree .Sample output;
.
├── hosts
├── ping.yaml
├── README.md
└── sudo-patch.yaml
1 directory, 3 files
Here is the sample hosts inventory content:
cat hosts[rhel7]
192.168.233.218
[rhel8]
192.168.233.249
[rhel9]
192.168.233.151
[ubuntu2204]
192.168.233.113
[ubuntu2404]
192.168.233.185
[debian12]
192.168.233.152
[rhel:children]
rhel7
rhel8
rhel9
[ubuntu:children]
ubuntu2204
ubuntu2404
[debian:children]
debian12
Here is the sample playbook for patching sudo via AWX Ansible.
cat sudo-patch.yaml---
- name: RHEL Registration and Sudo CVE audit for CVE-2025-32462 and CVE-2025-32463
hosts: all
gather_facts: yes
become: yes
vars:
# RHEL Registration variables
use_cdn: true # true = CDN, false = Satellite
force_register: true # Force clean re-registration by default
# CDN credentials
rhsm_username: username
rhsm_password: password
# Satellite registration
satellite_org_id: your-org-ID
satellite_fqdn: your-satellite-address
# Activation keys per OS major version
rhel_activation_keys:
"6": "rhel6"
"7": "rhel7"
"8": "rhel8"
"9": "rhel9"
# Sudo CVE variables
supported_ubuntu:
- "20.04"
- "22.04"
- "24.04"
- "25.04"
supported_debian:
- "11"
- "12"
supported_rhel:
- "7"
- "8"
- "9"
fixed_versions:
CVE-2025-32462:
Ubuntu:
"20.04": "1.8.31-1ubuntu1.5+esm1"
"22.04": "1.9.9-1ubuntu2.5"
"24.04": "1.9.15p5-3ubuntu5.24.04.1"
"25.04": "1.9.15p5-3ubuntu5.25.04.1"
Debian:
"11": "1.9.5p2-3+deb11u2"
"12": "1.9.13p3-1+deb12u2"
RedHat:
"7": "1.8.23-10"
"8": "1.9.5p2-1"
"9": "1.9.5p2-10"
CentOS:
"7": "1.8.23-10"
"8": "1.9.5p2-1"
"9": "1.9.5p2-10"
AlmaLinux:
"8": "1.9.5p2-1"
"9": "1.9.5p2-10"
Rocky:
"8": "1.9.5p2-1"
"9": "1.9.5p2-10"
CVE-2025-32463:
Ubuntu:
"20.04": "not affected"
"22.04": "not affected"
"24.04": "1.9.15p5-3ubuntu5.24.04.1"
"25.04": "1.9.15p5-3ubuntu5.25.04.1"
Debian:
"11": "not affected"
"12": "not affected"
RedHat:
"7": "not affected"
"8": "not affected"
"9": "not affected"
CentOS:
"7": "not affected"
"8": "not affected"
"9": "not affected"
AlmaLinux:
"8": "not affected"
"9": "not affected"
Rocky:
"8": "not affected"
"9": "not affected"
tasks:
# ========================================
# RHEL REGISTRATION TASKS
# ========================================
- name: Set activation key based on OS major version (RHEL only)
set_fact:
satellite_activation_key: "{{ rhel_activation_keys[ansible_distribution_major_version] }}"
when: ansible_distribution == "RedHat"
- name: Full RHSM cleanup (unregister, remove, clean) - RHEL only
shell: |
subscription-manager unregister || true
subscription-manager remove --all || true
subscription-manager clean || true
when:
- ansible_distribution == "RedHat"
- force_register
register: rhsm_cleanup
- name: Clean old RHSM certificates and facts - RHEL only
file:
path: "{{ item }}"
state: absent
loop:
- /etc/pki/consumer
- /etc/pki/entitlement
- /etc/rhsm/facts
when:
- ansible_distribution == "RedHat"
- force_register
- name: Uninstall Katello CA consumer RPM - RHEL only
yum:
name: "katello-ca-consumer*"
state: absent
autoremove: yes
when: ansible_distribution == "RedHat"
- name: Install Katello CA consumer RPM - RHEL only
yum:
name: "https://{{ satellite_fqdn }}/pub/katello-ca-consumer-latest.noarch.rpm"
state: present
when:
- ansible_distribution == "RedHat"
- not use_cdn
register: katello_install
- name: Configure no_proxy and register to Satellite - RHEL only
shell: |
subscription-manager config --server.no_proxy=*.{{ satellite_fqdn | regex_replace('^.*?([^.]+\.[^.]+)$', '\\1') }}
subscription-manager register \
--org="{{ satellite_org_id }}" \
--activationkey="{{ satellite_activation_key }}" \
--force
when:
- ansible_distribution == "RedHat"
- not use_cdn
register: satellite_register
- name: Register to Red Hat CDN - RHEL only
command: >
subscription-manager register
--username="{{ rhsm_username }}"
--password="{{ rhsm_password }}"
--force
when:
- ansible_distribution == "RedHat"
- use_cdn
register: cdn_register
- name: Refresh subscription - RHEL only
command: subscription-manager refresh
when:
- ansible_distribution == "RedHat"
- (satellite_register is defined and satellite_register.changed) or (cdn_register is defined and cdn_register.changed)
- name: Verify RHEL registration status
command: subscription-manager status
register: rhsm_status
when: ansible_distribution == "RedHat"
failed_when: false
changed_when: false
- name: Set registration success status
set_fact:
rhel_registration_success: >-
{{ true if rhsm_status is defined and
(rhsm_status.stdout is search('Simple Content Access') or
rhsm_status.stdout is search('Current') or
rhsm_status.stdout is search('content, regardless of subscription status'))
else false }}
when: ansible_distribution == "RedHat"
- name: Display RHEL registration status
debug:
msg:
- "RHEL Registration Status for {{ inventory_hostname }}"
- "{{ rhsm_status.stdout_lines }}"
when:
- ansible_distribution == "RedHat"
- rhsm_status is defined
# ========================================
# SUDO CVE AUDIT AND PATCHING TASKS
# ========================================
- name: Validate supported OS
fail:
msg: "Unsupported OS: {{ ansible_distribution }}. Supported OSes: Ubuntu, Debian, RedHat, CentOS, AlmaLinux, Rocky Linux."
when: ansible_distribution not in ["Ubuntu", "Debian", "RedHat", "CentOS", "AlmaLinux", "Rocky"]
- name: Set OS release version short
set_fact:
os_release_short: >-
{{ ansible_distribution_version if ansible_distribution == "Ubuntu" else
ansible_distribution_major_version | default(ansible_distribution_version.split('.')[0] | default('unknown')) if ansible_distribution == "Debian" else
ansible_distribution_version.split('.')[0] | default('unknown') if ansible_distribution in ["RedHat", "CentOS", "AlmaLinux", "Rocky"] else
ansible_distribution_version | default('unknown') }}
- name: Skip unsupported OS versions
fail:
msg: |
Unsupported {{ ansible_distribution }} version: {{ os_release_short }}.
Supported versions: {{ supported_ubuntu if ansible_distribution == 'Ubuntu' else supported_debian if ansible_distribution == 'Debian' else supported_rhel }}.
when: >
(ansible_distribution == "Ubuntu" and os_release_short not in supported_ubuntu) or
(ansible_distribution == "Debian" and os_release_short not in supported_debian) or
(ansible_distribution in ["RedHat", "CentOS", "AlmaLinux", "Rocky"] and os_release_short not in supported_rhel)
- name: Validate fixed_versions entry
fail:
msg: "No fixed_versions entry for {{ ansible_distribution }} {{ os_release_short }}."
when: >
ansible_distribution not in fixed_versions['CVE-2025-32462'] or
os_release_short not in fixed_versions['CVE-2025-32462'][ansible_distribution] or
ansible_distribution not in fixed_versions['CVE-2025-32463'] or
os_release_short not in fixed_versions['CVE-2025-32463'][ansible_distribution]
- name: Check if sudo is installed
command: which sudo
register: sudo_check
changed_when: false
failed_when: false
ignore_errors: true
- name: Fail if sudo is not installed
fail:
msg: "Sudo is not installed on {{ inventory_hostname }}."
when: sudo_check.rc != 0
- name: Gather package facts
ansible.builtin.package_facts:
manager: auto
- name: Get detailed sudo version info
shell: |
if command -v rpm >/dev/null 2>&1; then
# For RPM systems, strip distribution-specific suffixes like .el8_9, .el9, etc.
rpm -q --queryformat '%{VERSION}-%{RELEASE}' sudo 2>/dev/null | sed 's/\.el[0-9][_0-9]*.*$//' || echo "unknown"
elif command -v dpkg >/dev/null 2>&1; then
dpkg-query -W -f='${Version}' sudo 2>/dev/null || echo "unknown"
else
echo "unknown"
fi
register: detailed_sudo_version
changed_when: false
failed_when: false
- name: Set initial sudo version
set_fact:
initial_sudo_version: "{{ detailed_sudo_version.stdout | default('unknown') }}"
fixed_version_32462: "{{ fixed_versions['CVE-2025-32462'][ansible_distribution][os_release_short] }}"
fixed_version_32463: "{{ fixed_versions['CVE-2025-32463'][ansible_distribution][os_release_short] }}"
- name: Set CVE affected status
set_fact:
cve_32462_not_affected: "{{ fixed_version_32462 == 'not affected' }}"
cve_32463_not_affected: "{{ fixed_version_32463 == 'not affected' }}"
- name: Check initial vulnerability for CVE-2025-32462 (Debian/Ubuntu)
command: dpkg --compare-versions "{{ initial_sudo_version }}" lt "{{ fixed_version_32462 }}"
register: initial_32462_deb_check
changed_when: false
failed_when: false
when: >
ansible_os_family == "Debian" and
not cve_32462_not_affected and
initial_sudo_version != 'unknown'
- name: Check initial vulnerability for CVE-2025-32463 (Debian/Ubuntu)
command: dpkg --compare-versions "{{ initial_sudo_version }}" lt "{{ fixed_version_32463 }}"
register: initial_32463_deb_check
changed_when: false
failed_when: false
when: >
ansible_os_family == "Debian" and
not cve_32463_not_affected and
initial_sudo_version != 'unknown'
- name: Check if rpmdev-vercmp is available (RedHat)
command: which rpmdev-vercmp
register: rpmdev_available
changed_when: false
failed_when: false
when: ansible_os_family == "RedHat"
- name: Check initial vulnerability for CVE-2025-32462 (RedHat)
command: rpmdev-vercmp "{{ initial_sudo_version }}" "{{ fixed_version_32462 }}"
register: initial_32462_rpm_check
changed_when: false
failed_when: false
when: >
ansible_os_family == "RedHat" and
not cve_32462_not_affected and
initial_sudo_version != 'unknown' and
rpmdev_available.rc == 0
- name: Check initial vulnerability for CVE-2025-32463 (RedHat)
command: rpmdev-vercmp "{{ initial_sudo_version }}" "{{ fixed_version_32463 }}"
register: initial_32463_rpm_check
changed_when: false
failed_when: false
when: >
ansible_os_family == "RedHat" and
not cve_32463_not_affected and
initial_sudo_version != 'unknown' and
rpmdev_available.rc == 0
- name: Determine initial vulnerability status
set_fact:
initially_vulnerable_32462: >-
{{ false if cve_32462_not_affected or initial_sudo_version == 'unknown' else
(initial_32462_deb_check.rc == 0) if ansible_os_family == "Debian" and initial_32462_deb_check is defined and 'rc' in initial_32462_deb_check else
(initial_32462_rpm_check.rc == 11) if ansible_os_family == "RedHat" and initial_32462_rpm_check is defined and 'rc' in initial_32462_rpm_check else
false }}
initially_vulnerable_32463: >-
{{ false if cve_32463_not_affected or initial_sudo_version == 'unknown' else
(initial_32463_deb_check.rc == 0) if ansible_os_family == "Debian" and initial_32463_deb_check is defined and 'rc' in initial_32463_deb_check else
(initial_32463_rpm_check.rc == 11) if ansible_os_family == "RedHat" and initial_32463_rpm_check is defined and 'rc' in initial_32463_rpm_check else
false }}
- name: Update sudo package (Debian/Ubuntu)
apt:
name: sudo
state: latest
update_cache: yes
when: >
ansible_os_family == "Debian" and
(initially_vulnerable_32462 or initially_vulnerable_32463)
register: sudo_update_debian
- name: Update sudo package (RedHat) - Only if registration successful
yum:
name: sudo
state: latest
when: >
ansible_os_family == "RedHat" and
(initially_vulnerable_32462 or initially_vulnerable_32463) and
(ansible_distribution != "RedHat" or (rhel_registration_success | default(false)))
register: sudo_update_redhat
- name: Gather package facts after update
ansible.builtin.package_facts:
manager: auto
when: >
(sudo_update_debian is defined and sudo_update_debian.changed) or
(sudo_update_redhat is defined and sudo_update_redhat.changed)
- name: Get final sudo version after update
shell: |
if command -v rpm >/dev/null 2>&1; then
# For RPM systems, strip distribution-specific suffixes like .el8_9, .el9, etc.
rpm -q --queryformat '%{VERSION}-%{RELEASE}' sudo 2>/dev/null | sed 's/\.el[0-9][_0-9]*.*$//' || echo "unknown"
elif command -v dpkg >/dev/null 2>&1; then
dpkg-query -W -f='${Version}' sudo 2>/dev/null || echo "unknown"
else
echo "unknown"
fi
register: final_detailed_sudo_version
changed_when: false
failed_when: false
when: >
(sudo_update_debian is defined and sudo_update_debian.changed) or
(sudo_update_redhat is defined and sudo_update_redhat.changed)
- name: Set final sudo version
set_fact:
final_sudo_version: >-
{{ final_detailed_sudo_version.stdout | default(initial_sudo_version) if final_detailed_sudo_version is defined else initial_sudo_version }}
update_performed: >-
{{ (sudo_update_debian is defined and sudo_update_debian.changed) or
(sudo_update_redhat is defined and sudo_update_redhat.changed) }}
- name: Check final vulnerability for CVE-2025-32462 (Debian/Ubuntu)
command: dpkg --compare-versions "{{ final_sudo_version }}" lt "{{ fixed_version_32462 }}"
register: final_32462_deb_check
changed_when: false
failed_when: false
when: >
ansible_os_family == "Debian" and
not cve_32462_not_affected and
final_sudo_version != 'unknown' and
update_performed
- name: Check final vulnerability for CVE-2025-32463 (Debian/Ubuntu)
command: dpkg --compare-versions "{{ final_sudo_version }}" lt "{{ fixed_version_32463 }}"
register: final_32463_deb_check
changed_when: false
failed_when: false
when: >
ansible_os_family == "Debian" and
not cve_32463_not_affected and
final_sudo_version != 'unknown' and
update_performed
- name: Check final vulnerability for CVE-2025-32462 (RedHat)
command: rpmdev-vercmp "{{ final_sudo_version }}" "{{ fixed_version_32462 }}"
register: final_32462_rpm_check
changed_when: false
failed_when: false
when: >
ansible_os_family == "RedHat" and
not cve_32462_not_affected and
final_sudo_version != 'unknown' and
update_performed and
rpmdev_available.rc == 0
- name: Check final vulnerability for CVE-2025-32463 (RedHat)
command: rpmdev-vercmp "{{ final_sudo_version }}" "{{ fixed_version_32463 }}"
register: final_32463_rpm_check
changed_when: false
failed_when: false
when: >
ansible_os_family == "RedHat" and
not cve_32463_not_affected and
final_sudo_version != 'unknown' and
update_performed and
rpmdev_available.rc == 0
- name: Determine final vulnerability status
set_fact:
final_vulnerable_32462: >-
{{ false if cve_32462_not_affected else
false if not initially_vulnerable_32462 else
false if not update_performed else
(final_32462_deb_check.rc == 0) if ansible_os_family == "Debian" and final_32462_deb_check is defined and 'rc' in final_32462_deb_check else
(final_32462_rpm_check.rc == 11) if ansible_os_family == "RedHat" and final_32462_rpm_check is defined and 'rc' in final_32462_rpm_check else
initially_vulnerable_32462 }}
final_vulnerable_32463: >-
{{ false if cve_32463_not_affected else
false if not initially_vulnerable_32463 else
false if not update_performed else
(final_32463_deb_check.rc == 0) if ansible_os_family == "Debian" and final_32463_deb_check is defined and 'rc' in final_32463_deb_check else
(final_32463_rpm_check.rc == 11) if ansible_os_family == "RedHat" and final_32463_rpm_check is defined and 'rc' in final_32463_rpm_check else
initially_vulnerable_32463 }}
- name: Set CVE status messages
set_fact:
cve_32462_status: >-
{{ 'Not Affected' if cve_32462_not_affected else
'Fixed' if initially_vulnerable_32462 and not final_vulnerable_32462 else
'Already Patched' if not initially_vulnerable_32462 else
'Still Vulnerable' if final_vulnerable_32462 else
'Not Vulnerable' }}
cve_32463_status: >-
{{ 'Not Affected' if cve_32463_not_affected else
'Fixed' if initially_vulnerable_32463 and not final_vulnerable_32463 else
'Already Patched' if not initially_vulnerable_32463 else
'Still Vulnerable' if final_vulnerable_32463 else
'Not Vulnerable' }}
action_taken: >-
{{ 'Sudo updated successfully' if update_performed else
'No update needed - already patched' if not initially_vulnerable_32462 and not initially_vulnerable_32463 else
'No update performed - may need manual intervention' }}
- name: Set report content for RHEL systems
set_fact:
report_lines:
- "=========================================="
- "Combined Registration & CVE Report for {{ inventory_hostname }}"
- "=========================================="
- "OS: {{ ansible_distribution }} {{ ansible_distribution_version }}"
- "RHEL Registration: {{ 'Success' if rhel_registration_success | default(false) else 'Failed/Unknown' }}"
- ""
- "Sudo Versions:"
- " Initial: {{ initial_sudo_version }}"
- " Final: {{ final_sudo_version }}"
- ""
- "CVE Status:"
- " CVE-2025-32462: {{ cve_32462_status }}"
- " CVE-2025-32463: {{ cve_32463_status }}"
- ""
- "Action Taken: {{ action_taken }}"
- ""
- "Required Fixed Versions:"
- " CVE-2025-32462: {{ fixed_version_32462 }}"
- " CVE-2025-32463: {{ fixed_version_32463 }}"
- ""
- "Initially Vulnerable:"
- " CVE-2025-32462: {{ initially_vulnerable_32462 }}"
- " CVE-2025-32463: {{ initially_vulnerable_32463 }}"
- "=========================================="
when: ansible_distribution == "RedHat"
- name: Set report content for non-RHEL systems
set_fact:
report_lines:
- "=========================================="
- "Sudo CVE Report for {{ inventory_hostname }}"
- "=========================================="
- "OS: {{ ansible_distribution }} {{ ansible_distribution_version }}"
- ""
- "Sudo Versions:"
- " Initial: {{ initial_sudo_version }}"
- " Final: {{ final_sudo_version }}"
- ""
- "CVE Status:"
- " CVE-2025-32462: {{ cve_32462_status }}"
- " CVE-2025-32463: {{ cve_32463_status }}"
- ""
- "Action Taken: {{ action_taken }}"
- ""
- "Required Fixed Versions:"
- " CVE-2025-32462: {{ fixed_version_32462 }}"
- " CVE-2025-32463: {{ fixed_version_32463 }}"
- ""
- "Initially Vulnerable:"
- " CVE-2025-32462: {{ initially_vulnerable_32462 }}"
- " CVE-2025-32463: {{ initially_vulnerable_32463 }}"
- "=========================================="
when: ansible_distribution != "RedHat"
- name: Print final report
debug:
msg: "{{ report_lines }}"
handlers:
- name: sudo_updated
debug:
msg: "Sudo package was updated on {{ inventory_hostname }}."
In high level, this playbook does the following:
- RHEL Registration:
- Cleans up old RHSM data, registers system to CDN or Satellite.
- Verifies registration success.
- Be sure to update the variables with correct values as per your environment setup.
- Sudo CVE Audit:
- Checks if the system is affected by CVE-2025-32462 and CVE-2025-32463.
- Validates and updates the
sudopackage if vulnerable. - Generates reports for RHEL and non-RHEL systems.
- Supported OS/Version Check:
- Verifies compatibility of the OS and version.
- Final Reporting:
- Displays the status of registration and CVE vulnerability for each host.
We also have a very basic ping module to verify hosts connectivity.
cat ping.yaml- name: Check server reachability of hosts
hosts: all
gather_facts: false
tasks:
- name: Verify Hosts Connectivity
ping:
This project has been pushed to my local Git repository as well to make it easier to manage and integrate with AWX. Storing it in a Git repository allows version control, team collaboration, and seamless sync with AWX job templates, making sudo patching automation more reliable and maintainable.
Step-by-Step Sudo Patching Process with Ansible AWX
Assuming you have a tested playbooks, here’s how to execute it in AWX to patch CVE-2025-32462 and CVE-2025-32463:
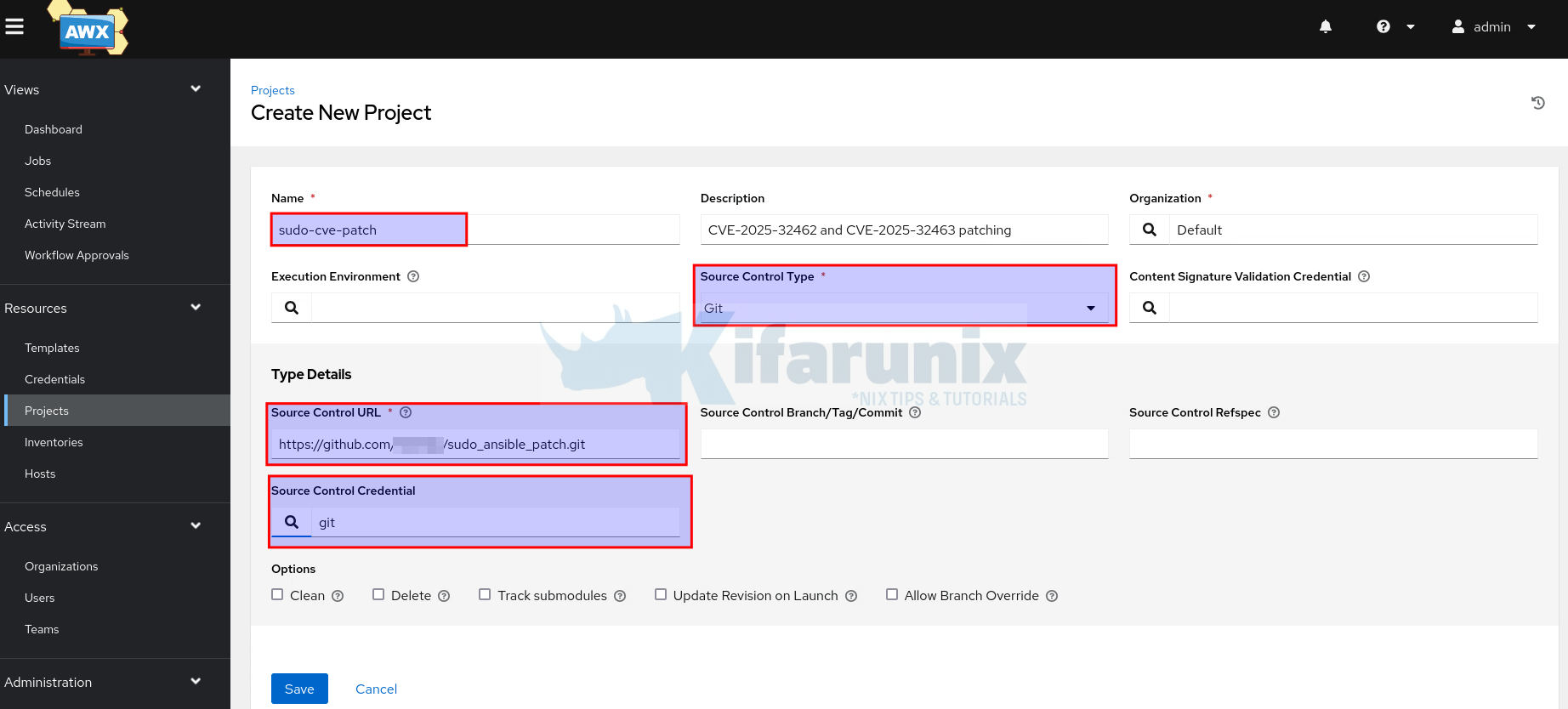
Create a Project in AWX:
- On the AWX UI, navigate to Resources > Projects > click the ADD button to add the project.
- Since I am using a Git repository to host my project playbook, I will set the:
- Source Control Type to Git
- Source Control URL: This is the HTTP address you usually use to clone the git repo e.g https://github.com/kifarunix/sudo_ansible_patch.git.
- For the Source Control Credential, search for the credentials. You need to have created them before this step.
- You can specify other options if it applies to you.
- Save the project when done configuring.
- Once you save the project, it will start to sync with the Git source and pull project files into the Ansible AWX projects directory.
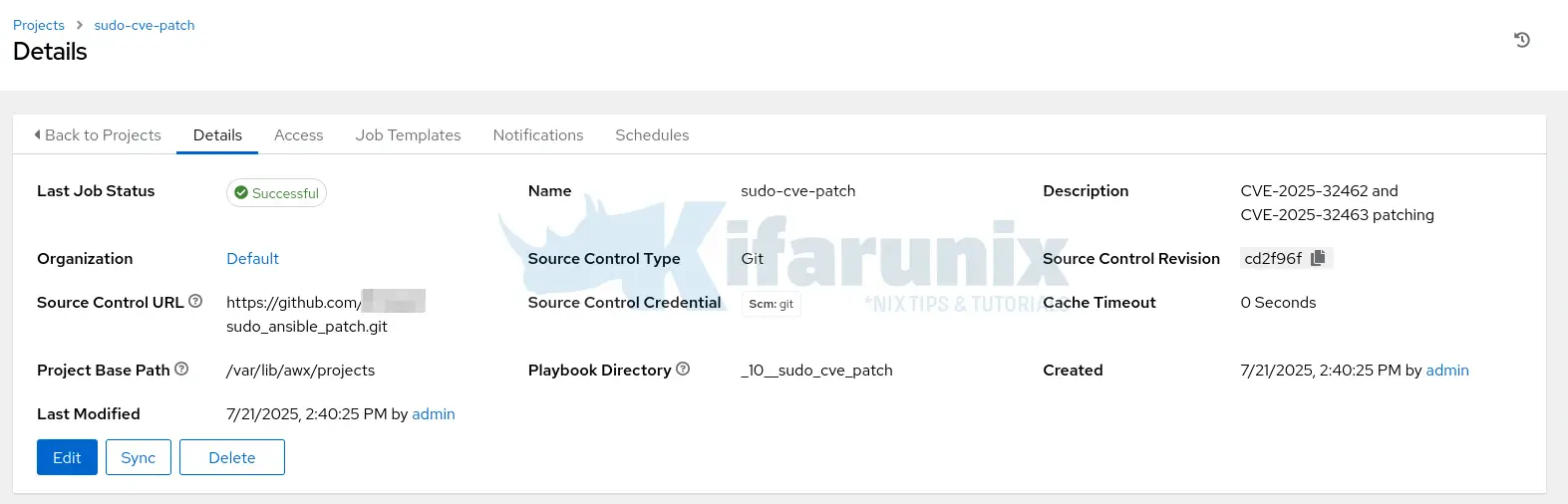
- Ensure the sync is successful. You can click the Sync button to manually sync the project.
Create Linux Host Machine Credentials in AWX
Next, you need to create credentials that Ansible AWX will use to connect to your Linux servers and execute playbooks.
- In the AWX web UI, go to Resources > Credentials > Add.
- Fill out the credential details:
- Name: Choose a descriptive name (e.g.,
Linux SSH Credential) - Description: (Optional) Add a note like “Used for sudo patching playbooks”
- Organization: Select your organization (use default if unsure)
- Credential Type: Select Machine (for SSH connections to Linux hosts)
- Name: Choose a descriptive name (e.g.,
- Provide the SSH login details:
- Username: Use a Linux user account that has SSH access and sudo privileges (e.g.,
ansible,ec2-user, orroot) - Password or SSH Private Key: Choose your authentication method:
- If using a password, enter it in the Password field.
- If using an SSH key, paste the private key into the “SSH Private Key” field.
- Privilege Escalation: If the user is not root but needs to run
sudo, check “Enable Privilege Escalation” and specifysudoas the method.
- Username: Use a Linux user account that has SSH access and sudo privileges (e.g.,
- Click Save to store the credentials.

Create Sudo Patching Hosts Inventory
Now that you have the project created, proceed to create your hosts inventory. On the AWX UI:
- Navigate to Resources > Inventories > ADD > Add Inventory.
- Enter the name of the inventory.
- Description (optional).
- Organization (you can leave the default value).
- Instance Groups if you have any groups created already
- Labels that optionally describe the inventory, such as ‘dev’ or ‘test’. Labels can be used to group and filter inventories and completed jobs.
- If there is any custom variables that you want to apply to your hosts, define them.
- Click Save when done.
When you click Save inventory Details wizard opens up. From here:
- You can now add the hosts manually to the inventory (Hosts > Add) or
- choose the source of the inventory, for example, if you already have an inventory in your project folder with hosts defined, you can go to Sources > Add.
- Set the name of the hosts source.
- Define the description and Execution environment (We use default values)
- Source: Sourced from a Project
- Under Source Type, click the search Icon on the project
- select the respective inventory file.
- Update other settings if applicable.
- Click Save and then hit Sync to sync the inventory and get the hosts populated.
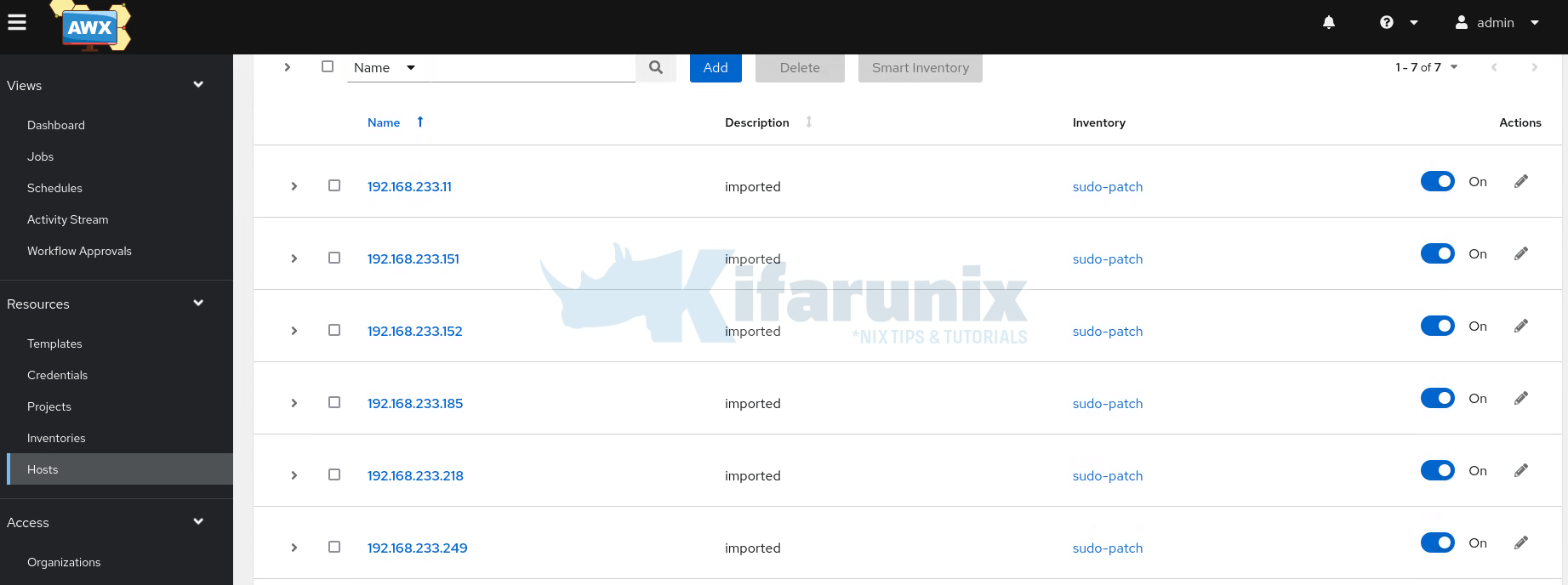
You inventory hosts will now appear under Resources > Hosts.
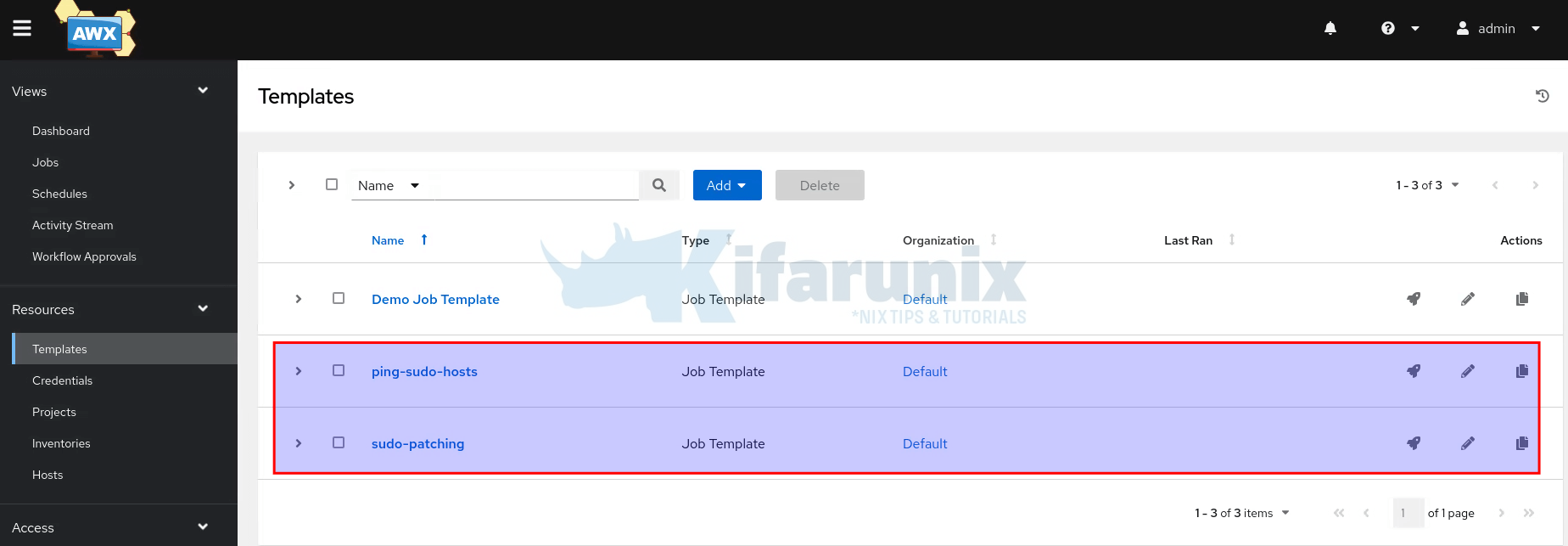
Create Sudo Patching Templates on Ansible AWX
Next, create job templates in AWX. A job template defines how a specific playbook should run by associating it with:
- The playbook to execute
- A host inventory
- Machine credentials (SSH for Linux)
- Optional variables (extra vars or prompts)
- The project source (e.g., your Git repository)
Since we have two playbooks, we’ll create a job template for each one.
To create a job template:
- Go to Resources > Templates > Add > Add job template.
- Enter a name of the template.
- Leave Job Type as Run.
- Select the inventory, project, and the first playbook (e.g., subscription-registration.yaml for setting up RHEL hosts repositories).
- Choose the appropriate credentials for connecting to the hosts.
- If the playbook requires variables, define them under variables.
- Leave other settings as default unless needed.
- Save the job template.
If you want, you can also set the number of forks or job slicing.
- Forks: Forks are the number of tasks that Ansible will run in parallel across hosts. For example, if you have 20 hosts and set forks to 5, Ansible will run tasks on 5 hosts at a time, and once those 5 finish, it will move on to the next 5, until all hosts are processed.
- Job Slicing: Job slicing is a method of breaking a task into smaller batches to control how many hosts are worked on at a time. For example, if you have 50 hosts and set
serial: 10, Ansible will process 10 hosts at a time, and only after those are completed will it move to the next 10, allowing better resource management and reducing system load.
Repeat the same steps for your second playbook.
We have also added our ping job template;
Create Sudo Patching Workflow Templates [for Multiple Playbooks]
If you want, you can launch individual job templates to perform specific patching tasks on hosts. However, if you need to automate the entire patching process across multiple systems or handle complex scenarios, you can use a workflow.
A workflow is a collection of job templates linked together in a sequence, allowing you to automate multi-step processes. For example, you can have one job to check the current patch level, another to apply patches, and a third to verify the patching status. By using a workflow, you ensure these steps are executed in the right order, with conditional logic to handle failures and retries.
In our case, we have just a single playbook, hence, the use of workflows do not apply here. The ping playbook is just an adhoc playbook for host reachability verification.
You can see example use of Workflow in the guide below;
Automate Windows Server Patching with Ansible AWX: Step-by-Step
Run Sudo Patch Job
Before launching the Sudo Patch Job, it’s important to ensure that your servers are reachable. We will first run a simple Ping Job Template to verify the connectivity.
Hence, from the templates section, select the ping job template (if you have one) and click launch.
Sample results:
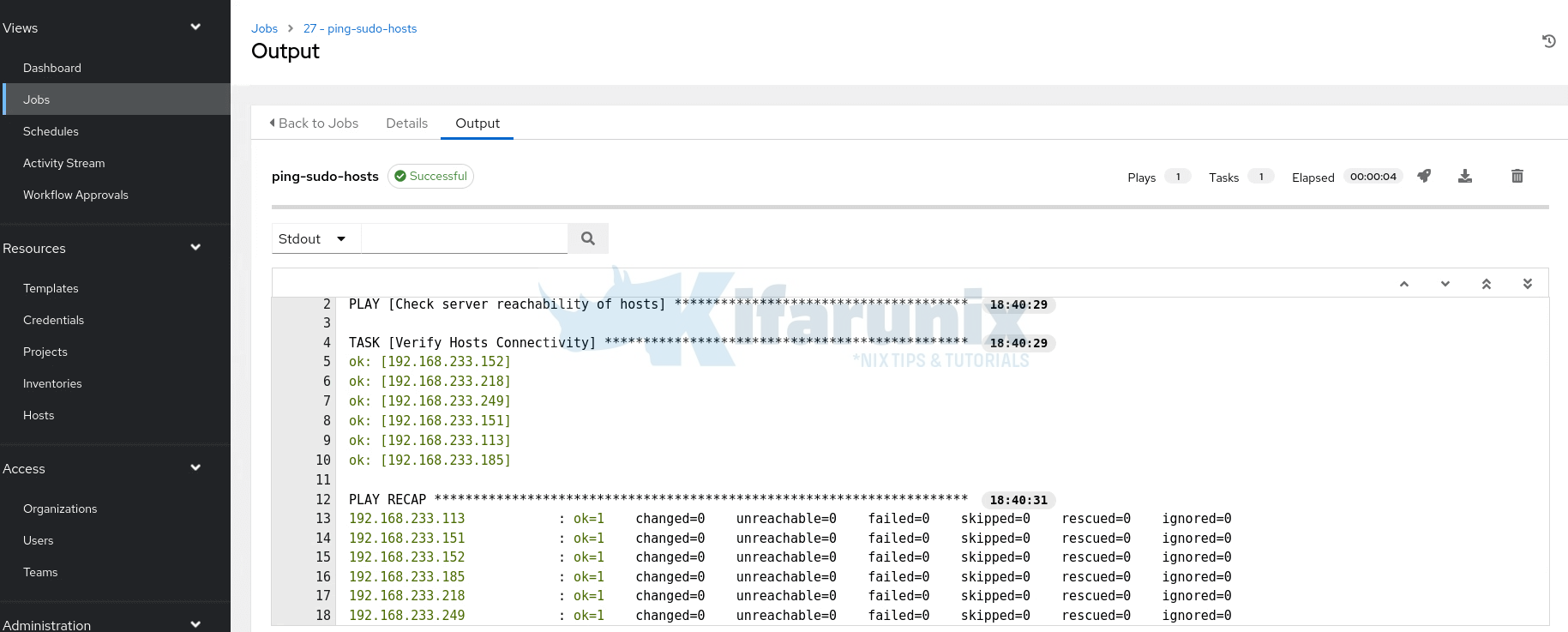
All our inventory hosts are reachable.
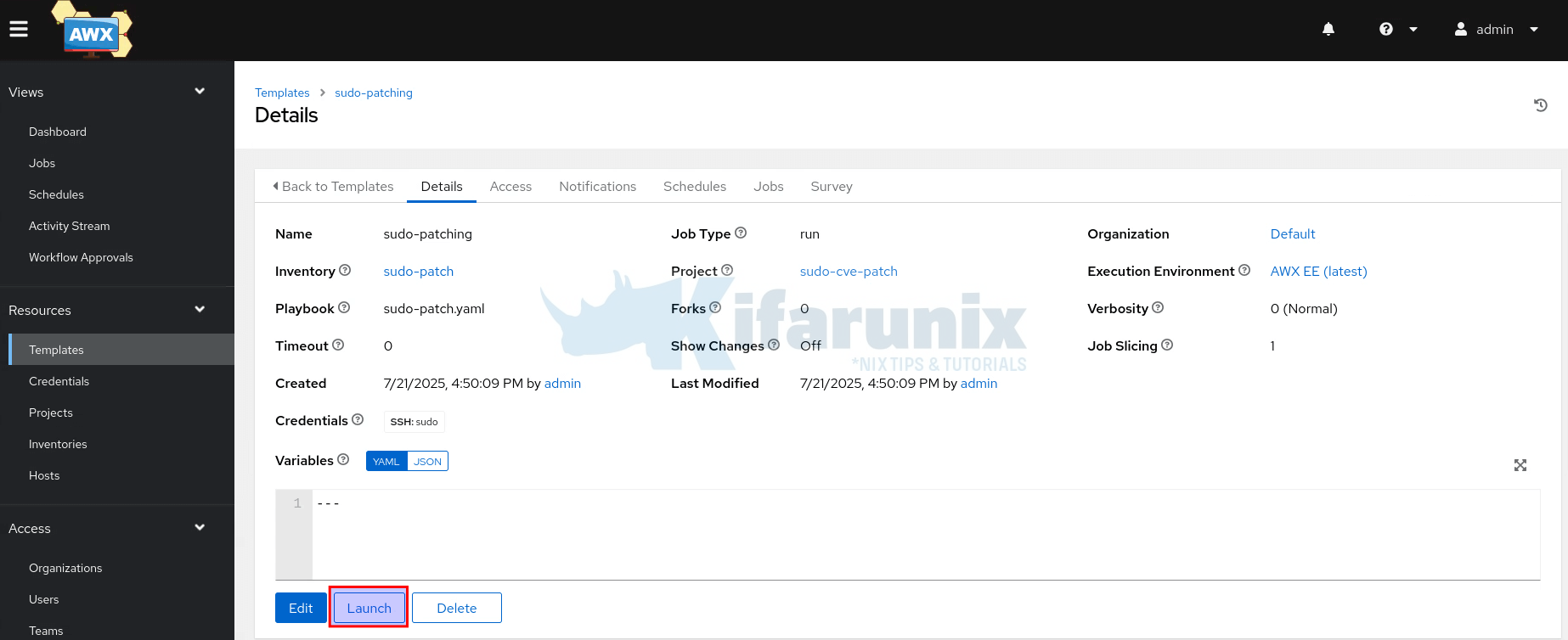
Next, launch the sudo patch job template from AWX’s web interface. Similarly, click on the job template name and Launch.
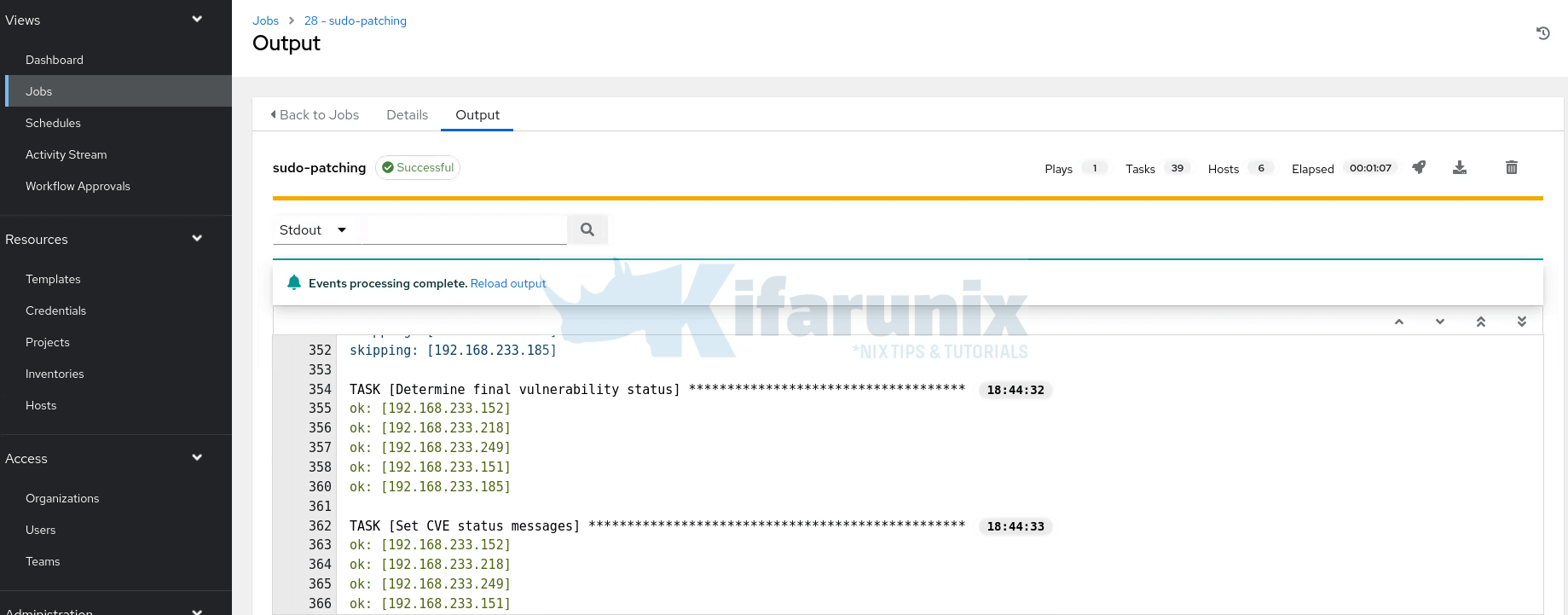
Monitor the job output in real-time to confirm successful package updates.
Sample output preview:
Complete output report (downloaded):
SSH password:
PLAY [RHEL Registration and Sudo CVE audit for CVE-2025-32462 and CVE-2025-32463] ***
TASK [Gathering Facts] *********************************************************
ok: [192.168.233.152]
ok: [192.168.233.218]
ok: [192.168.233.151]
ok: [192.168.233.249]
ok: [192.168.233.113]
ok: [192.168.233.185]
TASK [Set activation key based on OS major version (RHEL only)] ****************
skipping: [192.168.233.152]
ok: [192.168.233.218]
ok: [192.168.233.249]
ok: [192.168.233.151]
skipping: [192.168.233.113]
skipping: [192.168.233.185]
TASK [Full RHSM cleanup (unregister, remove, clean) - RHEL only] ***************
skipping: [192.168.233.152]
skipping: [192.168.233.113]
skipping: [192.168.233.185]
changed: [192.168.233.151]
changed: [192.168.233.218]
changed: [192.168.233.249]
TASK [Clean old RHSM certificates and facts - RHEL only] ***********************
skipping: [192.168.233.152] => (item=/etc/pki/consumer)
skipping: [192.168.233.152] => (item=/etc/pki/entitlement)
skipping: [192.168.233.152] => (item=/etc/rhsm/facts)
skipping: [192.168.233.152]
skipping: [192.168.233.185] => (item=/etc/pki/consumer)
skipping: [192.168.233.113] => (item=/etc/pki/consumer)
skipping: [192.168.233.113] => (item=/etc/pki/entitlement)
skipping: [192.168.233.113] => (item=/etc/rhsm/facts)
skipping: [192.168.233.113]
skipping: [192.168.233.185] => (item=/etc/pki/entitlement)
skipping: [192.168.233.185] => (item=/etc/rhsm/facts)
skipping: [192.168.233.185]
changed: [192.168.233.218] => (item=/etc/pki/consumer)
changed: [192.168.233.151] => (item=/etc/pki/consumer)
changed: [192.168.233.249] => (item=/etc/pki/consumer)
changed: [192.168.233.218] => (item=/etc/pki/entitlement)
changed: [192.168.233.151] => (item=/etc/pki/entitlement)
changed: [192.168.233.249] => (item=/etc/pki/entitlement)
changed: [192.168.233.218] => (item=/etc/rhsm/facts)
changed: [192.168.233.151] => (item=/etc/rhsm/facts)
changed: [192.168.233.249] => (item=/etc/rhsm/facts)
TASK [Uninstall Katello CA consumer RPM - RHEL only] ***************************
skipping: [192.168.233.152]
skipping: [192.168.233.185]
skipping: [192.168.233.113]
ok: [192.168.233.218]
ok: [192.168.233.151]
changed: [192.168.233.249]
TASK [Install Katello CA consumer RPM - RHEL only] *****************************
skipping: [192.168.233.152]
skipping: [192.168.233.218]
skipping: [192.168.233.249]
skipping: [192.168.233.151]
skipping: [192.168.233.113]
skipping: [192.168.233.185]
TASK [Configure no_proxy and register to Satellite - RHEL only] ****************
skipping: [192.168.233.152]
skipping: [192.168.233.218]
skipping: [192.168.233.249]
skipping: [192.168.233.151]
skipping: [192.168.233.113]
skipping: [192.168.233.185]
TASK [Register to Red Hat CDN - RHEL only] *************************************
skipping: [192.168.233.152]
skipping: [192.168.233.113]
skipping: [192.168.233.185]
changed: [192.168.233.151]
changed: [192.168.233.249]
changed: [192.168.233.218]
TASK [Refresh subscription - RHEL only] ****************************************
skipping: [192.168.233.152]
skipping: [192.168.233.113]
skipping: [192.168.233.185]
changed: [192.168.233.151]
changed: [192.168.233.249]
changed: [192.168.233.218]
TASK [Verify RHEL registration status] *****************************************
skipping: [192.168.233.152]
skipping: [192.168.233.113]
skipping: [192.168.233.185]
ok: [192.168.233.218]
ok: [192.168.233.249]
ok: [192.168.233.151]
TASK [Set registration success status] *****************************************
skipping: [192.168.233.152]
ok: [192.168.233.218]
ok: [192.168.233.151]
ok: [192.168.233.249]
skipping: [192.168.233.113]
skipping: [192.168.233.185]
TASK [Display RHEL registration status] ****************************************
skipping: [192.168.233.152]
ok: [192.168.233.218] => {
"msg": [
"RHEL Registration Status for 192.168.233.218",
[
"+-------------------------------------------+",
" System Status Details",
"+-------------------------------------------+",
"Overall Status: Disabled",
"Content Access Mode is set to Simple Content Access. This host has access to content, regardless of subscription status.",
"",
"System Purpose Status: Disabled"
]
]
}
ok: [192.168.233.151] => {
"msg": [
"RHEL Registration Status for 192.168.233.151",
[
"+-------------------------------------------+",
" System Status Details",
"+-------------------------------------------+",
"Overall Status: Disabled",
"Content Access Mode is set to Simple Content Access. This host has access to content, regardless of subscription status.",
"",
"System Purpose Status: Disabled"
]
]
}
ok: [192.168.233.249] => {
"msg": [
"RHEL Registration Status for 192.168.233.249",
[
"+-------------------------------------------+",
" System Status Details",
"+-------------------------------------------+",
"Overall Status: Disabled",
"Content Access Mode is set to Simple Content Access. This host has access to content, regardless of subscription status.",
"",
"System Purpose Status: Disabled"
]
]
}
skipping: [192.168.233.113]
skipping: [192.168.233.185]
TASK [Validate supported OS] ***************************************************
skipping: [192.168.233.152]
skipping: [192.168.233.218]
skipping: [192.168.233.249]
skipping: [192.168.233.151]
skipping: [192.168.233.113]
skipping: [192.168.233.185]
TASK [Set OS release version short] ********************************************
ok: [192.168.233.152]
ok: [192.168.233.218]
ok: [192.168.233.151]
ok: [192.168.233.249]
ok: [192.168.233.113]
ok: [192.168.233.185]
TASK [Skip unsupported OS versions] ********************************************
skipping: [192.168.233.152]
skipping: [192.168.233.218]
skipping: [192.168.233.249]
skipping: [192.168.233.151]
skipping: [192.168.233.113]
skipping: [192.168.233.185]
TASK [Validate fixed_versions entry] *******************************************
skipping: [192.168.233.152]
skipping: [192.168.233.218]
skipping: [192.168.233.249]
skipping: [192.168.233.151]
skipping: [192.168.233.113]
skipping: [192.168.233.185]
TASK [Check if sudo is installed] **********************************************
ok: [192.168.233.152]
ok: [192.168.233.218]
ok: [192.168.233.113]
ok: [192.168.233.249]
ok: [192.168.233.151]
ok: [192.168.233.185]
TASK [Fail if sudo is not installed] *******************************************
skipping: [192.168.233.152]
skipping: [192.168.233.218]
skipping: [192.168.233.249]
skipping: [192.168.233.151]
skipping: [192.168.233.113]
skipping: [192.168.233.185]
TASK [Gather package facts] ****************************************************
ok: [192.168.233.218]
ok: [192.168.233.152]
ok: [192.168.233.151]
ok: [192.168.233.113]
ok: [192.168.233.249]
ok: [192.168.233.185]
TASK [Get detailed sudo version info] ******************************************
ok: [192.168.233.218]
ok: [192.168.233.152]
ok: [192.168.233.249]
ok: [192.168.233.151]
ok: [192.168.233.113]
ok: [192.168.233.185]
TASK [Set initial sudo version] ************************************************
ok: [192.168.233.152]
ok: [192.168.233.218]
ok: [192.168.233.249]
ok: [192.168.233.151]
ok: [192.168.233.113]
ok: [192.168.233.185]
TASK [Set CVE affected status] *************************************************
ok: [192.168.233.152]
ok: [192.168.233.218]
ok: [192.168.233.249]
ok: [192.168.233.151]
ok: [192.168.233.113]
ok: [192.168.233.185]
TASK [Check initial vulnerability for CVE-2025-32462 (Debian/Ubuntu)] **********
skipping: [192.168.233.218]
skipping: [192.168.233.249]
skipping: [192.168.233.151]
ok: [192.168.233.152]
ok: [192.168.233.113]
ok: [192.168.233.185]
TASK [Check initial vulnerability for CVE-2025-32463 (Debian/Ubuntu)] **********
skipping: [192.168.233.152]
skipping: [192.168.233.218]
skipping: [192.168.233.249]
skipping: [192.168.233.151]
skipping: [192.168.233.113]
ok: [192.168.233.185]
TASK [Check if rpmdev-vercmp is available (RedHat)] ****************************
skipping: [192.168.233.152]
skipping: [192.168.233.113]
skipping: [192.168.233.185]
ok: [192.168.233.218]
ok: [192.168.233.249]
ok: [192.168.233.151]
TASK [Check initial vulnerability for CVE-2025-32462 (RedHat)] *****************
skipping: [192.168.233.152]
skipping: [192.168.233.218]
skipping: [192.168.233.249]
skipping: [192.168.233.151]
skipping: [192.168.233.113]
skipping: [192.168.233.185]
TASK [Check initial vulnerability for CVE-2025-32463 (RedHat)] *****************
skipping: [192.168.233.152]
skipping: [192.168.233.218]
skipping: [192.168.233.249]
skipping: [192.168.233.151]
skipping: [192.168.233.113]
skipping: [192.168.233.185]
TASK [Determine initial vulnerability status] **********************************
ok: [192.168.233.152]
ok: [192.168.233.218]
ok: [192.168.233.249]
ok: [192.168.233.151]
ok: [192.168.233.113]
ok: [192.168.233.185]
TASK [Update sudo package (Debian/Ubuntu)] *************************************
skipping: [192.168.233.218]
skipping: [192.168.233.249]
skipping: [192.168.233.151]
changed: [192.168.233.152]
changed: [192.168.233.113]
changed: [192.168.233.185]
TASK [Update sudo package (RedHat) - Only if registration successful] **********
skipping: [192.168.233.152]
skipping: [192.168.233.218]
skipping: [192.168.233.249]
skipping: [192.168.233.151]
skipping: [192.168.233.113]
skipping: [192.168.233.185]
TASK [Gather package facts after update] ***************************************
skipping: [192.168.233.218]
skipping: [192.168.233.249]
skipping: [192.168.233.151]
ok: [192.168.233.152]
ok: [192.168.233.113]
ok: [192.168.233.185]
TASK [Get final sudo version after update] *************************************
skipping: [192.168.233.218]
skipping: [192.168.233.249]
skipping: [192.168.233.151]
ok: [192.168.233.152]
ok: [192.168.233.113]
ok: [192.168.233.185]
TASK [Set final sudo version] **************************************************
ok: [192.168.233.152]
ok: [192.168.233.218]
ok: [192.168.233.249]
ok: [192.168.233.151]
ok: [192.168.233.113]
ok: [192.168.233.185]
TASK [Check final vulnerability for CVE-2025-32462 (Debian/Ubuntu)] ************
skipping: [192.168.233.218]
skipping: [192.168.233.249]
skipping: [192.168.233.151]
ok: [192.168.233.152]
ok: [192.168.233.113]
ok: [192.168.233.185]
TASK [Check final vulnerability for CVE-2025-32463 (Debian/Ubuntu)] ************
skipping: [192.168.233.152]
skipping: [192.168.233.218]
skipping: [192.168.233.249]
skipping: [192.168.233.151]
skipping: [192.168.233.113]
ok: [192.168.233.185]
TASK [Check final vulnerability for CVE-2025-32462 (RedHat)] *******************
skipping: [192.168.233.152]
skipping: [192.168.233.218]
skipping: [192.168.233.249]
skipping: [192.168.233.151]
skipping: [192.168.233.113]
skipping: [192.168.233.185]
TASK [Check final vulnerability for CVE-2025-32463 (RedHat)] *******************
skipping: [192.168.233.152]
skipping: [192.168.233.218]
skipping: [192.168.233.249]
skipping: [192.168.233.151]
skipping: [192.168.233.113]
skipping: [192.168.233.185]
TASK [Determine final vulnerability status] ************************************
ok: [192.168.233.152]
ok: [192.168.233.218]
ok: [192.168.233.249]
ok: [192.168.233.151]
ok: [192.168.233.113]
ok: [192.168.233.185]
TASK [Set CVE status messages] *************************************************
ok: [192.168.233.152]
ok: [192.168.233.218]
ok: [192.168.233.249]
ok: [192.168.233.151]
ok: [192.168.233.113]
ok: [192.168.233.185]
TASK [Set report content for RHEL systems] *************************************
skipping: [192.168.233.152]
ok: [192.168.233.218]
ok: [192.168.233.249]
ok: [192.168.233.151]
skipping: [192.168.233.113]
skipping: [192.168.233.185]
TASK [Set report content for non-RHEL systems] *********************************
ok: [192.168.233.152]
skipping: [192.168.233.218]
skipping: [192.168.233.249]
skipping: [192.168.233.151]
ok: [192.168.233.113]
ok: [192.168.233.185]
TASK [Print final report] ******************************************************
ok: [192.168.233.152] => {
"msg": [
"==========================================",
"Sudo CVE Report for 192.168.233.152",
"==========================================",
"OS: Debian 12.4",
"",
"Sudo Versions:",
" Initial: 1.9.13p3-1+deb12u1",
" Final: 1.9.13p3-1+deb12u2",
"",
"CVE Status:",
" CVE-2025-32462: Fixed",
" CVE-2025-32463: Not Affected",
"",
"Action Taken: Sudo updated successfully",
"",
"Required Fixed Versions:",
" CVE-2025-32462: 1.9.13p3-1+deb12u2",
" CVE-2025-32463: not affected",
"",
"Initially Vulnerable:",
" CVE-2025-32462: True",
" CVE-2025-32463: False",
"=========================================="
]
}
ok: [192.168.233.218] => {
"msg": [
"==========================================",
"Combined Registration & CVE Report for 192.168.233.218",
"==========================================",
"OS: RedHat 7.9",
"RHEL Registration: Success",
"",
"Sudo Versions:",
" Initial: 1.8.23-10",
" Final: 1.8.23-10",
"",
"CVE Status:",
" CVE-2025-32462: Already Patched",
" CVE-2025-32463: Not Affected",
"",
"Action Taken: No update needed - already patched",
"",
"Required Fixed Versions:",
" CVE-2025-32462: 1.8.23-10",
" CVE-2025-32463: not affected",
"",
"Initially Vulnerable:",
" CVE-2025-32462: False",
" CVE-2025-32463: False",
"=========================================="
]
}
ok: [192.168.233.249] => {
"msg": [
"==========================================",
"Combined Registration & CVE Report for 192.168.233.249",
"==========================================",
"OS: RedHat 8.10",
"RHEL Registration: Success",
"",
"Sudo Versions:",
" Initial: 1.9.5p2-1",
" Final: 1.9.5p2-1",
"",
"CVE Status:",
" CVE-2025-32462: Already Patched",
" CVE-2025-32463: Not Affected",
"",
"Action Taken: No update needed - already patched",
"",
"Required Fixed Versions:",
" CVE-2025-32462: 1.9.5p2-1",
" CVE-2025-32463: not affected",
"",
"Initially Vulnerable:",
" CVE-2025-32462: False",
" CVE-2025-32463: False",
"=========================================="
]
}
ok: [192.168.233.151] => {
"msg": [
"==========================================",
"Combined Registration & CVE Report for 192.168.233.151",
"==========================================",
"OS: RedHat 9.4",
"RHEL Registration: Success",
"",
"Sudo Versions:",
" Initial: 1.9.5p2-10",
" Final: 1.9.5p2-10",
"",
"CVE Status:",
" CVE-2025-32462: Already Patched",
" CVE-2025-32463: Not Affected",
"",
"Action Taken: No update needed - already patched",
"",
"Required Fixed Versions:",
" CVE-2025-32462: 1.9.5p2-10",
" CVE-2025-32463: not affected",
"",
"Initially Vulnerable:",
" CVE-2025-32462: False",
" CVE-2025-32463: False",
"=========================================="
]
}
ok: [192.168.233.113] => {
"msg": [
"==========================================",
"Sudo CVE Report for 192.168.233.113",
"==========================================",
"OS: Ubuntu 22.04",
"",
"Sudo Versions:",
" Initial: 1.9.9-1ubuntu2.4",
" Final: 1.9.9-1ubuntu2.5",
"",
"CVE Status:",
" CVE-2025-32462: Fixed",
" CVE-2025-32463: Not Affected",
"",
"Action Taken: Sudo updated successfully",
"",
"Required Fixed Versions:",
" CVE-2025-32462: 1.9.9-1ubuntu2.5",
" CVE-2025-32463: not affected",
"",
"Initially Vulnerable:",
" CVE-2025-32462: True",
" CVE-2025-32463: False",
"=========================================="
]
}
ok: [192.168.233.185] => {
"msg": [
"==========================================",
"Sudo CVE Report for 192.168.233.185",
"==========================================",
"OS: Ubuntu 24.04",
"",
"Sudo Versions:",
" Initial: 1.9.15p5-3ubuntu5",
" Final: 1.9.15p5-3ubuntu5.24.04.1",
"",
"CVE Status:",
" CVE-2025-32462: Fixed",
" CVE-2025-32463: Fixed",
"",
"Action Taken: Sudo updated successfully",
"",
"Required Fixed Versions:",
" CVE-2025-32462: 1.9.15p5-3ubuntu5.24.04.1",
" CVE-2025-32463: 1.9.15p5-3ubuntu5.24.04.1",
"",
"Initially Vulnerable:",
" CVE-2025-32462: True",
" CVE-2025-32463: True",
"=========================================="
]
}
PLAY RECAP *********************************************************************
192.168.233.113 : ok=18 changed=1 unreachable=0 failed=0 skipped=24 rescued=0 ignored=0
192.168.233.151 : ok=23 changed=4 unreachable=0 failed=0 skipped=19 rescued=0 ignored=0
192.168.233.152 : ok=18 changed=1 unreachable=0 failed=0 skipped=24 rescued=0 ignored=0
192.168.233.185 : ok=20 changed=1 unreachable=0 failed=0 skipped=22 rescued=0 ignored=0
192.168.233.218 : ok=23 changed=4 unreachable=0 failed=0 skipped=19 rescued=0 ignored=0
192.168.233.249 : ok=23 changed=5 unreachable=0 failed=0 skipped=19 rescued=0 ignored=0
See sample Ubuntu 24.04 final sudo patch report.
ok: [192.168.233.185] => {
"msg": [
"==========================================",
"Sudo CVE Report for 192.168.233.185",
"==========================================",
"OS: Ubuntu 24.04",
"",
"Sudo Versions:",
" Initial: 1.9.15p5-3ubuntu5",
" Final: 1.9.15p5-3ubuntu5.24.04.1",
"",
"CVE Status:",
" CVE-2025-32462: Fixed",
" CVE-2025-32463: Fixed",
"",
"Action Taken: Sudo updated successfully",
"",
"Required Fixed Versions:",
" CVE-2025-32462: 1.9.15p5-3ubuntu5.24.04.1",
" CVE-2025-32463: 1.9.15p5-3ubuntu5.24.04.1",
"",
"Initially Vulnerable:",
" CVE-2025-32462: True",
" CVE-2025-32463: True",
"=========================================="
]
That confirms that sudo has been successfully patched for both CVEs.
How to
Verify the Sudo Patch Activity
After the patch job completes, verify the sudo version on the target hosts by running:
sudo --versionOr;
rpm -qa sudoOr
dpkg -l sudoThe output should match the fixed version you applied during the patch process. Ensure the version is updated correctly on all target hosts.
Additionally, the Security team should perform a scan on the servers to check for any residual vulnerabilities related to the Sudo CVEs. This ensures that all security issues are properly addressed and mitigated.
That marks the end of our simple guide on how to patch sudo CVEs 2025-32462 & 2025-32463 using Ansible AWX
Conclusion
Patching CVE-2025-32462 and CVE-2025-32463 with Ansible AWX ensures a fast, reliable, and secure update process across your Linux infrastructure. By automating patching, you not only reduce risks and save time but also improve operational efficiency and maintain continuous compliance. To bolster your security posture, integrate AWX into your broader patch management workflow.

