In this guide, you will learn how to install and setup phpLDAPadmin on Ubuntu 20.04. phpLDAPadmin (also known as PLA) is a web-based application written in PHP for administering LDAP servers. PLA is designed to manage records in an LDAP server, including creating, modifying, deleting records.
Learn how to install and setup OpenLDAP server with SSL/TLS on Ubuntu 20.04 by following the link below;
Install and Setup OpenLDAP Server on Ubuntu 20.04
Installing phpLDAPadmin on Ubuntu 20.04
Want to use Debian 10/11 instead? Check the link below;
Install phpLDAPAdmin on Debian 10/Debian 11
Install phpLDAPadmin on Ubuntu 20.04
phpLDAPadmin is available on Ubuntu 20.04 repos;
apt show phpldapadminPackage: phpldapadmin
Version: 1.2.2-6.3
Priority: extra
Section: universe/admin
Origin: Ubuntu
Maintainer: Ubuntu Developers [email protected]
Original-Maintainer: Fabio Tranchitella [email protected]
Bugs: https://bugs.launchpad.net/ubuntu/+filebug
Installed-Size: 4,686 kB
Depends: php, php-ldap, php-xml, ucf (>= 0.28), debconf (>= 0.5) | debconf-2.0
Download-Size: 719 kB
APT-Sources: http://us.archive.ubuntu.com/ubuntu focal/universe amd64 Packages
You can simply install it by running the command below;
apt install phpldapadminNote that will install phpLDAPadmin with PHP 7.4. So expect a number of warnings on deprecation when running phpLDAPadmin.
Configuring phpLDAPadmin on Ubuntu 20.04
The default configuration file for phpLDAPadmin is /etc/phpldapadmin/config.php. This is the file that we are going to edit to make our configuration changes as per LDAP server settings.
vim /etc/phpldapadmin/config.phpThe configuration file is highly commented. We are only going to make a few changes in this demo, enough to access and run phpLDAPadmin to administer LDAP server.
Set a suitable name for your LDAP server. This is the name that will appear on phpLDAPadmin web interface.
/*********************************************
* Define your LDAP servers in this section *
*********************************************/
...
...
/* A convenient name that will appear in the tree viewer and throughout
phpLDAPadmin to identify this LDAP server to users. */
$servers->setValue('server','name','Kifarunix-demo LDAP Server');
...Define the IP address or resolvable hostname of your OpenLDAP server;
$servers->setValue('server','host','ldap.kifarunix-demo.com');Define the port on which your OpenLDAP server is listening on. In our demo, our OpenLDAP is configured with StartTLS (port 389).
/* The port your LDAP server listens on (no quotes). 389 is standard. */
$servers->setValue('server','port',389);Set the OpenLDAP base DN. In our setup, OpenLDAP base DN is set to dc=kifarunix-demo,dc=com.
/* Array of base DNs of your LDAP server. Leave this blank to have phpLDAPadmin
auto-detect it for you. */
$servers->setValue('server','base',array('dc=kifarunix-demo,dc=com'));Define your phpLDAPadmin authentication type. In this demo, we choose the default authentication type, session.
$servers->setValue('login','auth_type','session');Define the Bind DN of the administrative user to login to phpLDAPadmin;
$servers->setValue('login','bind_id','cn=admin,dc=kifarunix-demo,dc=com');You can optionally specify an attribute to use when logging in. In our case, we want to use full DN, cn=admin,dc=kifarunix-demo,dc=com, for logging in.
$servers->setValue('login','attr','dn');Configure user ID auto increment when creating users from phpLDAPadmin web interface. This ensures that you do not re-use already assigned user and group IDs. In this setup, we choose the ID from 10000.
/* The minimum number to use when searching for the next available number
(only when 'search' is used for auto_number. */
$servers->setValue('auto_number','min',array('uidNumber'=>10000,'gidNumber'=>10000));That is all the changes we could make in this guide. Go through the configuration file and choose any other option you want to configure.
Save and exit the file once done with configuration.
Configure Apache for phpLDAPadmin
If you need to make any changes on phpLDAPadmin Apache configuration, edit the file, /etc/apache2/conf-available/phpldapadmin.conf and make your changes. We go with the default settings in our case.
Disable Apache default site (with welcome page)
a2dissite 000-default.confOpen Apache on firewall to allow external access.
ufw allow 80/tcpRestart Apache;
systemctl restart apache2Accessing phpLDAPadmin on Browser
You can access phpLDAPadmin using the address, http://server-IP-or-Hostname/phpldapadmin.
If you get the warning, Deprecated: Array and string offset access syntax with curly braces is deprecated in /usr/share/phpldapadmin/lib/functions.php on line 1614, you can simply replace the curly braces ({}) with square brackets ([]) on the affected line, 1614.
Click login to login to you phpLDAPadmin web user interface. Since we already defined the admin Bind DN, simply enter the password and login;
Upon successful authentication, you land on phpLDAPadmin dashboard.
You can now administer your LDAP server with web interface.
Create LDAP User on phpLDAPadmin
As an example, we will learn how to create an LDAP user and its group using phpLDAPadmin.
Create user posixGroup
Click ou=group. Then click Create new entry here {option 1} or click Create a child entry {option 2}.
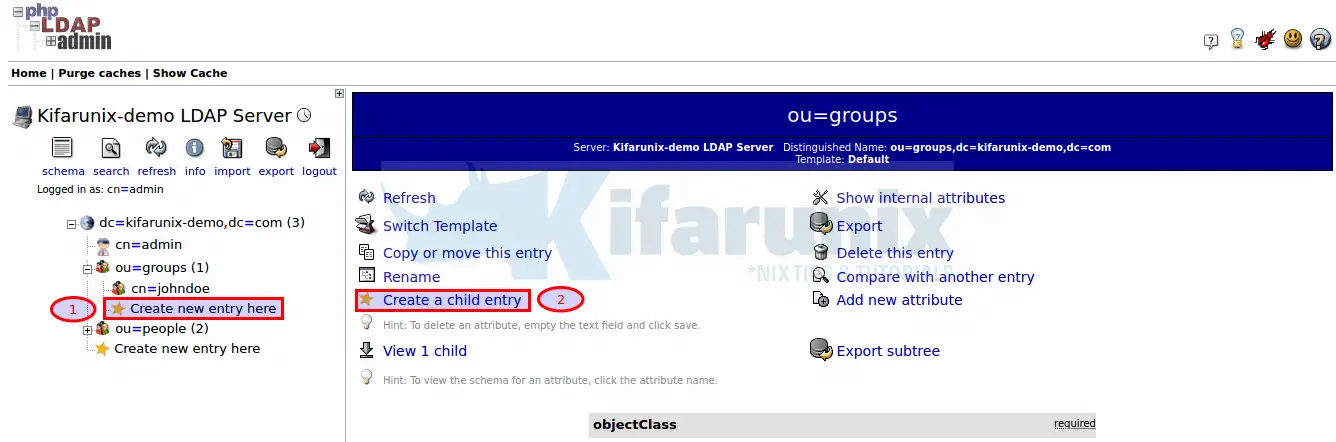
Next, click Generic: Posix Group template for creating an LDAP user group.
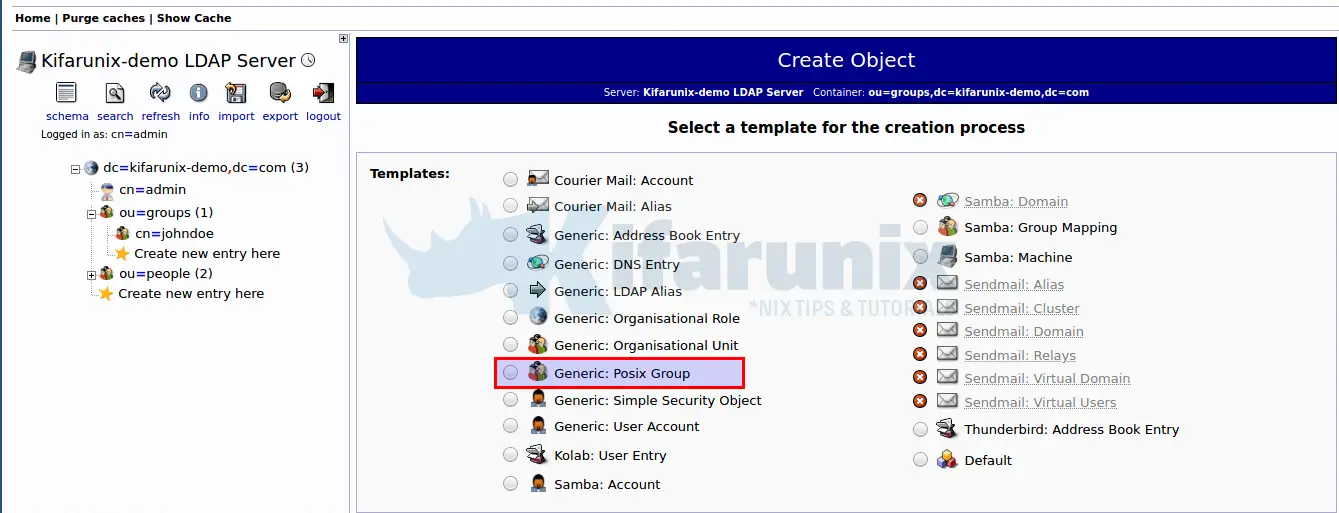
Enter name of the group, which in this case we set it to be same as the uid of the user we are going to create. If you noticed, the group is autopopulated.
If you want any other users to be part of the group, select their usernames. Click Create Object once done and commit the changes.
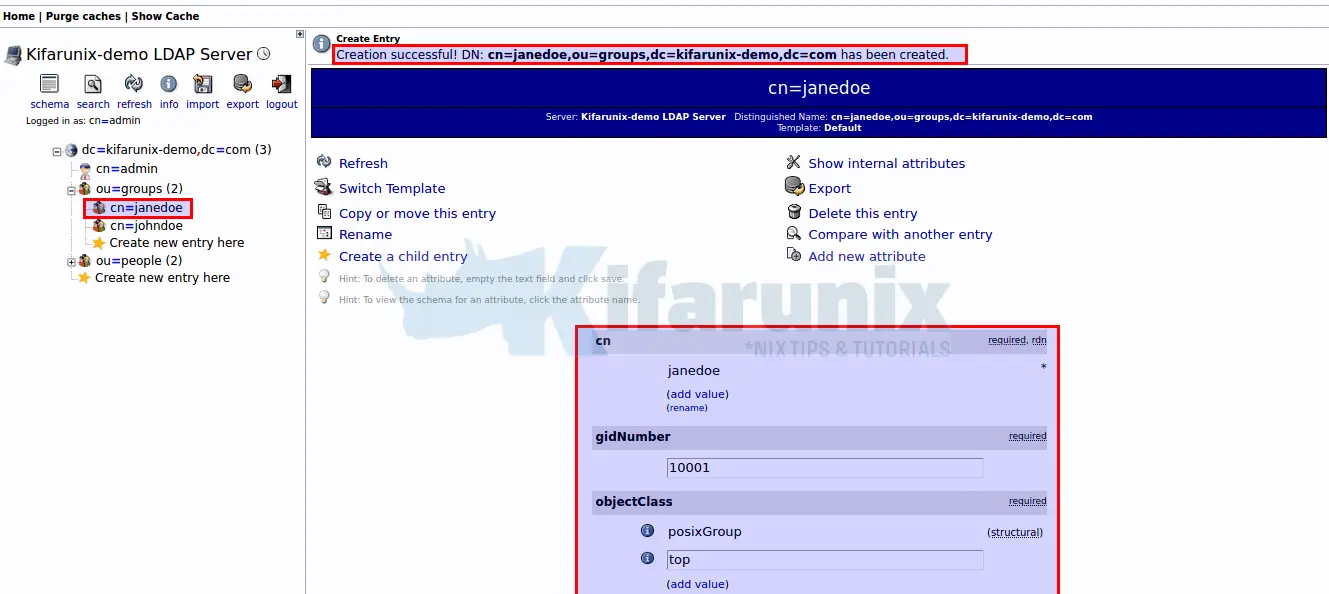
Create user posixAccount
Once you have a user group created, proceed to create the user account. Click on ou=people and similarly, you have two options, either click Create new entry here or click Create a child entry.
Select the Generic: User Account template for creating user object.
Generate user password hash;
slappasswdNew password: password
Re-enter new password: password
{SSHA}vrJOf+/AFD9pdGKo/azGavDfbZ8OGJX1If you need to verify if the password matches the pasted hash, click check password.
When you set the password, select ssha and paste the hash above as the password.
Fill in the user details appropriately as shown in the screenshot below;
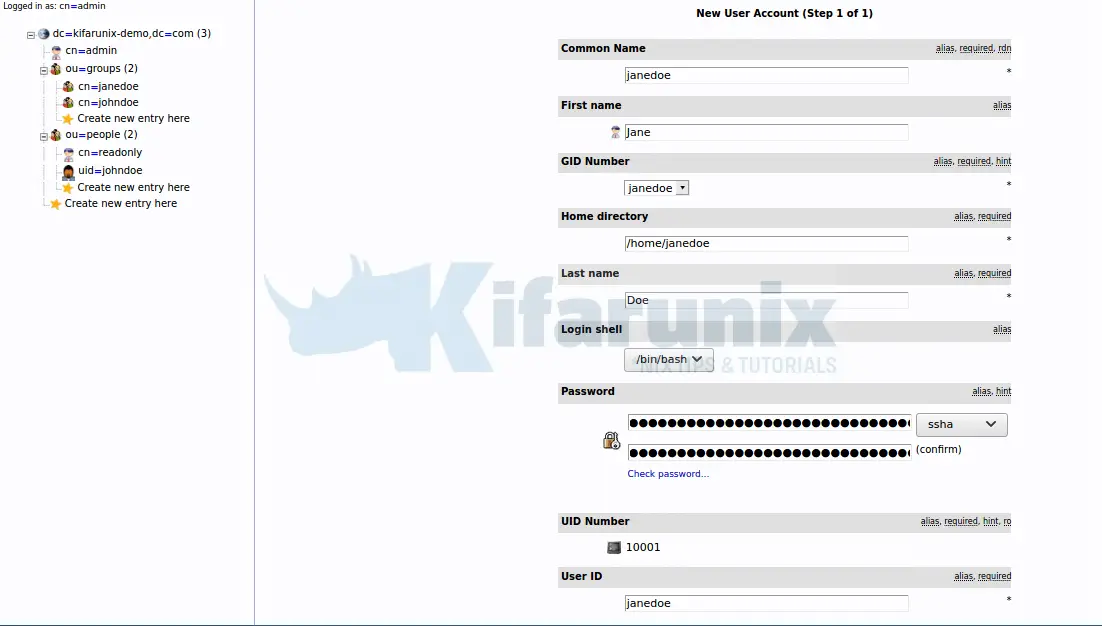
Once done, click Create Object once done and commit the changes.
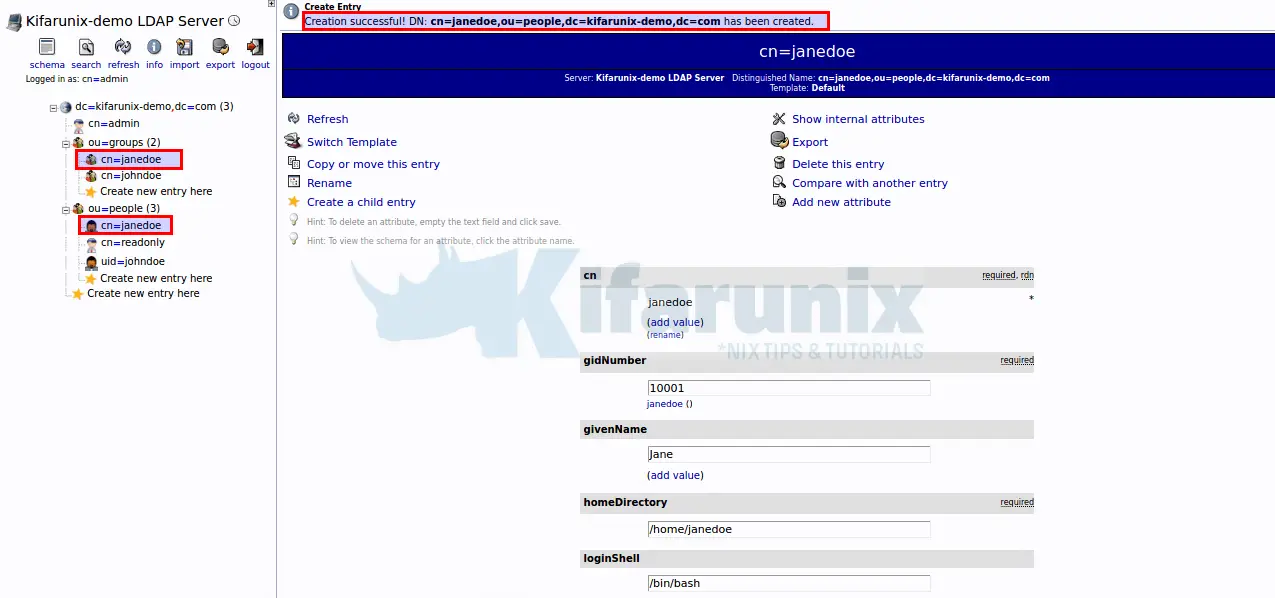
Note, to be able to have bash among the shell options, edit the posixAccount creation template and add bash option by running the command;
sed -i '/<value id="\/bin\/tsh">\/bin\/tsh<\/value>/a \\t<value id="/bin/bash">\/bin\/bash<\/value>' /etc/phpldapadmin/templates/creation/posixAccount.xmlIf you have the user information in an LDIF file, you can import this file by clicking import at the top menu bar on the left pane.
To confirm the user creation on OpenLDAP server backend;
ldapsearch -H ldapi:/// -Y EXTERNAL -b "dc=kifarunix-demo,dc=com" "(&(objectclass=posixAccount)(uid=janedoe))" -LLL -Qdn: cn=janedoe,ou=people,dc=kifarunix-demo,dc=com
cn: janedoe
givenName: Jane
gidNumber: 10001
homeDirectory: /home/janedoe
sn: Doe
loginShell: /bin/bash
objectClass: inetOrgPerson
objectClass: posixAccount
objectClass: top
uidNumber: 10001
uid: janedoe
userPassword:: e1NTSEF9Y1VNNWx1UWM0Sjl5WlhnZWJZTHkwMjRhTmszdlVkUE4=
ldapsearch -H ldapi:/// -Y EXTERNAL -b "dc=kifarunix-demo,dc=com" "(&(objectclass=posixGroup)(cn=janedoe))" -LLL -Qdn: cn=janedoe,ou=groups,dc=kifarunix-demo,dc=com
gidNumber: 10001
cn: janedoe
objectClass: posixGroup
objectClass: topYou can explore the functionality of this tool further.
Related Tutorials
Install phpLDAPadmin on CentOS 8
Configure SSSD for LDAP Authentication on Ubuntu 20.04


I followed these steps exactly, and I get 2 errors :
Unable to connect to LDAP server Kifarunix-demo LDAP Server
Error: Can’t contact LDAP server (-1) for user
error Failed to Authenticate to server
Invalid Username or Password.
Despite typing the exact same password I’ve typed during your openLDAP installation guide on Ubuntu 20.04 (https://kifarunix.com/install-and-setup-openldap-server-on-ubuntu-20-04/#comment-30697)