This guide presents a simple way of how to configure Syslog on Solaris 11.4 send logs to remote syslog server.
Table of Contents
Configuring Syslog on Solaris 11.4 for Remote Logging
Enable Syslog on Solaris 11.4
Syslog is the native log manager on Solaris 11.4. It should be enabled by default.
Before you can proceed to configure syslog on Solaris 11.4, first check if it is enabled.
svcs system-logSTATE STIME FMRI
disabled 2:07:53 svc:/system/system-log:rsyslog
online 23:08:50 svc:/system/system-log:default
As per the above output, the native syslog is enabled.
Configuring Syslog Remote Logging on Solaris 11.4
Therefore, you need to configure Syslog and define the log messages to be forwarded to the central log server. This can be done by defining the facility and priority of the logs.
The facility defines the type of program that is logging the message for example the kernel, mail system, security processes, syslog, system daemons etc. The defined facilities are auth (or security), authpriv, cron, daemon, ftp, kern, lpr, mail, mark, news, syslog, user, uucp, and local0-local7.
The priority on the other hand defines the severity level of the message. The possible priorities arranged in the decreasing order of urgency include emerg (or panic (0)), alert (1), crit (2), err (or error(3)), warning (or warn (4)), notice (5), info (6), debug (7).
Thus in this guide, we are going to send all the informational messages to the remote server. Hence, edit the syslog configuration file, /etc/syslog.conf and add the line below.
vim /etc/syslog.conf
...
# This file is processed by m4 so be careful to quote (`') names
# that match m4 reserved words. Also, within ifdef's, arguments
# containing commas must be quoted.
#
*.err;kern.notice;auth.notice /dev/sysmsg
*.err;kern.debug;daemon.notice;auth.none;mail.crit /var/adm/messages
*.alert;kern.err;daemon.err operator
*.alert root
*.emerg *
# Forward informational Messages
*.info @remotehost # Use a tab instead of spaces.
...
Ensure that you are using tabs instead of spaces;
*.info<tab>@remotehost
Save the configuration file and restart syslog.
svcadm restart system-log:default
Verify Connection to Remote Log Server
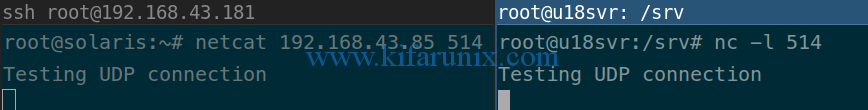
Next, verify that Solaris 11.4 server can communicate to the remote syslog server UDP port 514. This can be done using netcat command. Hence, on the remote server, run the netcat to listen on command as shown below;
nc -l 514
On Solaris 11.4, run netcat as shown below;
netcat 192.168.43.85 514
Type anything at the prompt and you should be able to see the same on remote host.
Configure Remote Log Server Logs Directory
On the remote central syslog server, configure it such that it saves the received logs to specific directory with IP/hostname as the identifier of the source of logs. See example below;
...
# provides UDP syslog reception
module(load="imudp")
input(type="imudp" port="514")
# provides TCP syslog reception
#module(load="imtcp")
#input(type="imtcp" port="514")
#Custom template to generate the log filename dynamically based on the client's IP address.
$template RemInputLogs, "/var/log/remotelogs/%FROMHOST-IP%.log"
*.* ?RemInputLogs
...
Verify Log Reception on Remote Log Server
Next, try to initiate an ssh authentication to Solaris 11.4 server. At the same time, run tcpdump command on the syslog server to verify that the logs are actually sent from Solaris 11.4 server.
tcpdump -i enp0s3 src solaris_server_IP and port 514
In the tcpdump output below, you can see two authentication messages since I tried both failed and successful authentication on Solaris 11.4 server.
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on enp0s3, link-type EN10MB (Ethernet), capture size 262144 bytes
21:17:34.926331 IP 192.168.43.181.61781 > u18svr.syslog: SYSLOG auth.error, length: 117
21:17:48.962226 IP 192.168.43.181.61781 > u18svr.syslog: SYSLOG auth.info, length: 132
At the same time, you can check the log file on the remote server as define in the configuration file above.
tail /var/log/remotelogs/192.168.43.181.log 2024-01-13T00:06:19+00:00 192.168.43.181 /usr/sbin/dhcpagent[497]: [ID 538334 daemon.info] configure_v4_timers: net0 acquired lease, expires Thu Feb 14 01:06:19 2024
2024-01-13T00:06:19+00:00 192.168.43.181 /usr/sbin/dhcpagent[497]: [ID 759141 daemon.info] configure_v4_timers: net0 begins renewal at Thu Feb 14 00:32:46 2024
2024-01-13T00:06:19+00:00 192.168.43.181 /usr/sbin/dhcpagent[497]: [ID 480545 daemon.info] configure_v4_timers: net0 begins rebinding at Thu Feb 14 00:55:16 2024
2024-01-13T00:17:35+00:00 192.168.43.181 sshd[1711]: [ID 800047 auth.error] error: PAM: Authentication failed for root from 192.168.43.149
2024-01-13T00:17:49+00:00 192.168.43.181 sshd[1711]: [ID 800047 auth.info] Accepted keyboard-interactive/pam for root from 192.168.43.149 port 40300 ssh2
Beautiful, that is how easy it is to configure Syslog to send logs to remote syslog server on Solaris 11.4.
You can also use Rsyslog instead of Syslog. Check how to Configure Rsyslog on Solaris 11.4.


Need to restart the service and how to config syslog
The guide is informational enough, Singh. where do you have a problem?