In this tutorial, you will learn how to configure Site-to-Site IPSec VPN on pfSense and Libreswan. IPSec (Internet Protocol Security) is a secured network protocol commonly used on VPNs to create a secured and encrypted communication tunnel between the communicating endpoints through data packet authentication and encryption.
Both pfSense and Libreswan can be configured to establish a site to site IPSec VPN tunnel to enable remote systems to communicate securely. They can be integrated with other commercial tools like Cisco ASA/Fortinet devices to setup secured IPSec VPN tunnel between communicating sites.
Configure Site-to-Site IPSec VPN on pfSense and Libreswan
In order to demonstrate how to setup Site-to-Site IPSec VPN between pfSense and Libreswan, here is our deployment architecture.
NOTE that the IP addresses, 11.22.33.44 and 55.66.77.88 used in this guide are just BOGUS! for the purposes of demonstration. Replace them accordingly!
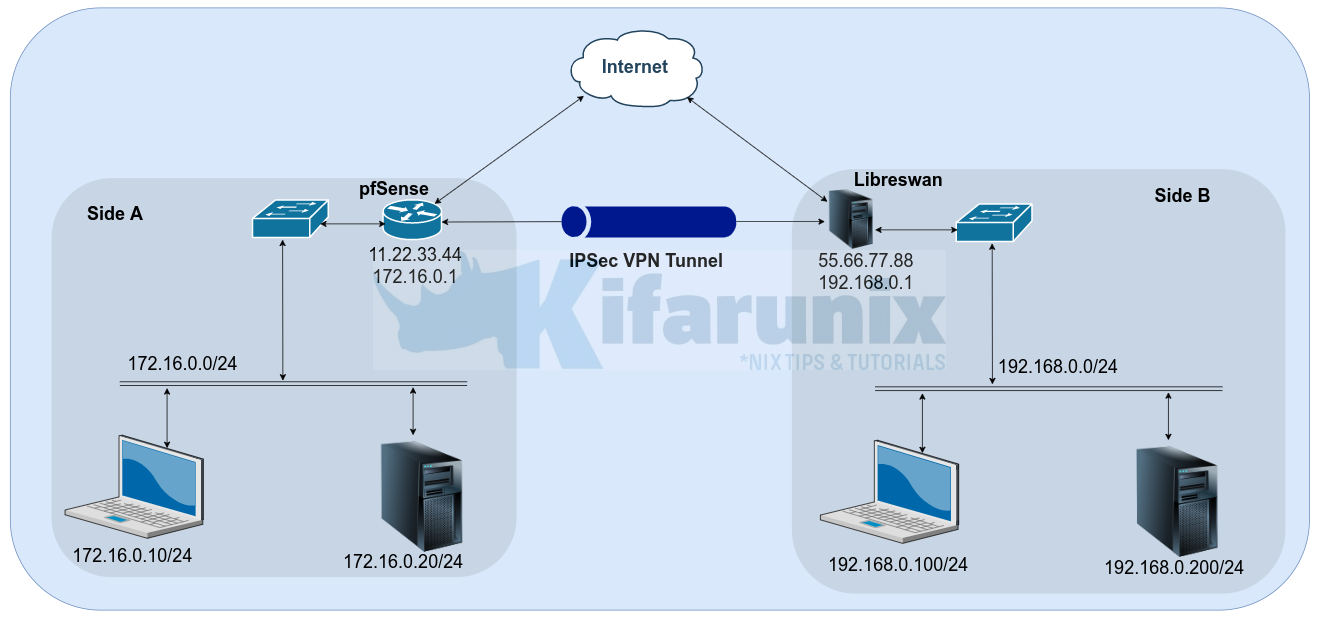
IPSec VPN configurations must match on both peers in order to the tunnel to be established successfully. In that case, below are the configuration settings were using in this particular setup;
| VPN device host information | Side A | Side B |
| VPN device version | pfSense 2.5.0 | Libreswan |
| IP address | 11.22.33.44 (bogus IP address) | 55.66.77.88 (bogus IP address) |
| IKE – Phase 1 properties | Side A | Side B |
| Authentication method | PSK (ChangeME) | PSK (ChangeME) |
| Encryption scheme | IKEv2 | IKEv2 |
| Perfect Forward Secrecy – IKE | DH Group 20 | DH Group 20 |
| Encryption algorithm – IKE | AES256 | AES256 |
| Hashing algorithm – IKE | SHA256 | SHA256 |
| IKE SA lifetime | 86400 sec | 86400 sec |
| IPSec – Phase 2 properties | Side A | Side B |
| Transform (IPSec protocol) | ESP | ESP |
| Perfect Forward Secrecy – IPSec | DH Group 20 | DH Group 20 |
| Encryption algorithm – IPSec | AES256 | AES256 |
| Hashing algorithm – IPSec | SHA256 | SHA256 |
| IPSec SA lifetime | 3600 sec | 3600 sec |
| Encryption hosts | Side A | Side B |
| Remote Networks | 172.16.0.0/24 | 192.168.0.0/24 |
| Hosts | 172.16.0.20 | 192.168.0.200 |
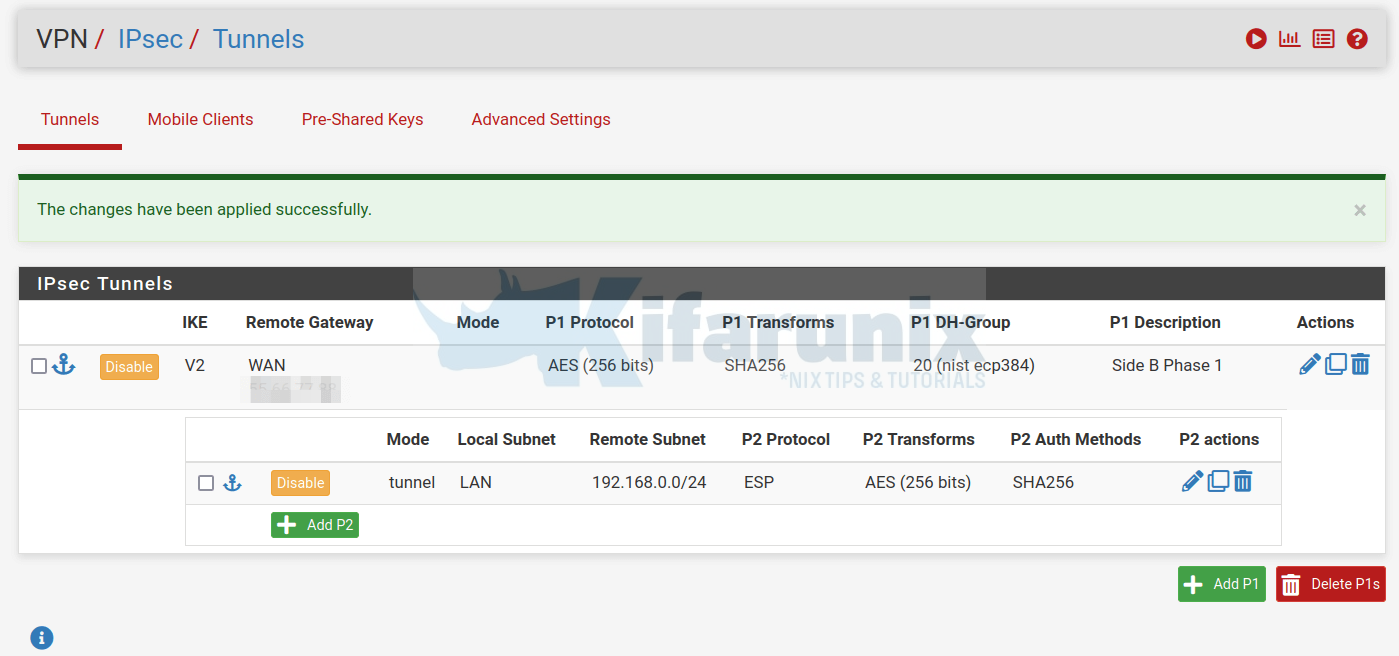
Configure IPSec VPN on pfSense on Side A
You can start by configuring the IPSec VPN settings on pfSense on side A.
We extensively explained how to configure IPSec VPN on pfSense in our previous guide. You can check the link below on how to go about this configuration;
Configuring IPSec on pfSense on Side A
This is how our configurations are like;
Configure Libreswa IPSec VPN
On the remote end, we are using a Rocky Linux server which acts as a Linux router for the Side B LAN.
Thus, to setup Libreswan for IPSec VPN on Rocky Linux;
- Run system update;
dnf update- Install Libreswan on Rocky Linux
dnf install libreswan- Initialize IPSec NSS database;
ipsec initnss- Start IPSec;
systemctl enable --now ipsec- Open Libreswan ipsec service Firewall
systemctl disable --now firewallddnf install iptables-servicesfor ISAKMP (handling of security associations)
iptables -A INPUT -p udp --dport 500 --j ACCEPTfor NAT-T (handling of IPsec between natted devices)
iptables -A INPUT -p udp --dport 4500 --j ACCEPTfor ESP payload (the encrypted data packets)
iptables -A INPUT -p esp -j ACCEPT- Enable IP masquerading on firewalld.
ipset create ipsecvpn hash:net
ipset add ipsecvpn 192.168.0.0/24
ipset add ipsecvpn 172.16.0/24iptables -t nat -A POSTROUTING -j MASQUERADE -m set ! --match-set ipsecvpn dstiptables-save > /etc/sysconfig/iptablessystemctl restart iptables- Disable redirects for XFRM/IPsec;
cp /etc/sysctl.d/50-libreswan.conf{,.old}
cat > /etc/sysctl.d/50-libreswan.conf << 'EOL'
net.ipv6.conf.default.accept_redirects = 0
net.ipv6.conf.all.accept_redirects = 0
net.ipv4.conf.default.send_redirects = 0
net.ipv4.conf.default.accept_redirects = 0
net.ipv4.conf.all.send_redirects = 0
net.ipv4.conf.all.accept_redirects = 0
net.ipv4.conf.all.rp_filter = 0
EOL
sysctl --system- Create Libreswan IPSec VPN Configuration. The configurations here must match exactly as what is configured on the remote peer!
Create a backup of the default IPSec configuration file;
mv /etc/ipsec.conf{,.old}Run the command below to paste our sample configurations into the /etc/ipsec.conf file;
cat > /etc/ipsec.conf << 'EOL'
config setup
logfile=/var/log/pluto.log
conn libreswan-pfsense
type=tunnel
authby=secret
left=55.66.77.88
leftid=55.66.77.88
leftsubnet=192.168.0.0/24
right=11.22.33.44
rightid=11.22.33.44
rightsubnet=172.16.0.0/24
ike=aes256-sha256-ecp384
esp=aes256-sha256-ecp384
pfs=yes
keyingtries=5
ikev2=insist
ikelifetime=24h
salifetime=1h
dpddelay=30
dpdtimeout=120
dpdaction=restart
auto=start
include /etc/crypto-policies/back-ends/libreswan.config
EOL
- Install pfSense-Libreswan IPSec secrets. This is the PresShared Key (PSK);
echo '55.66.77.88 : PSK "ChangeME"
11.22.33.44 : PSK "ChangeME"' > /etc/ipsec.secrets- Next, verify the Libreswan IPSec configuration syntax;
ipsec verifySample output;
Verifying installed system and configuration files
Version check and ipsec on-path [OK]
Libreswan 4.4 (netkey) on 4.18.0-348.20.1.el8_5.x86_64
Checking for IPsec support in kernel [OK]
NETKEY: Testing XFRM related proc values
ICMP default/send_redirects [OK]
ICMP default/accept_redirects [OK]
XFRM larval drop [OK]
Pluto ipsec.conf syntax [OK]
Checking rp_filter [OK]
Checking that pluto is running [OK]
Pluto listening for IKE on udp 500 [OK]
Pluto listening for IKE/NAT-T on udp 4500 [OK]
Pluto ipsec.secret syntax [OK]
Checking 'ip' command [OK]
Checking 'iptables' command [OK]
Checking 'prelink' command does not interfere with FIPS [OK]
Checking for obsolete ipsec.conf options [OK]
Restart IPSec service;
systemctl restart ipsecCheck status;
systemctl status ipsec● ipsec.service - Internet Key Exchange (IKE) Protocol Daemon for IPsec
Loaded: loaded (/usr/lib/systemd/system/ipsec.service; enabled; vendor preset: disabled)
Active: active (running) since Sat 2022-04-16 00:45:15 EAT; 3min 3s ago
Docs: man:ipsec(8)
man:pluto(8)
man:ipsec.conf(5)
Process: 6181 ExecStopPost=/usr/sbin/ipsec --stopnflog (code=exited, status=0/SUCCESS)
Process: 6177 ExecStopPost=/bin/bash -c if test "$EXIT_STATUS" != "12"; then /sbin/ip xfrm policy flush; /sbin/ip xfrm state flush; fi (code=exited, status=0/SUCCESS)
Process: 6174 ExecStop=/usr/libexec/ipsec/whack --shutdown (code=exited, status=0/SUCCESS)
Process: 6435 ExecStartPre=/usr/sbin/ipsec --checknflog (code=exited, status=0/SUCCESS)
Process: 6433 ExecStartPre=/usr/sbin/ipsec --checknss (code=exited, status=0/SUCCESS)
Process: 6190 ExecStartPre=/usr/libexec/ipsec/_stackmanager start (code=exited, status=0/SUCCESS)
Process: 6188 ExecStartPre=/usr/libexec/ipsec/addconn --config /etc/ipsec.conf --checkconfig (code=exited, status=0/SUCCESS)
Main PID: 6447 (pluto)
Status: "Startup completed."
Tasks: 4 (limit: 17837)
Memory: 3.8M
CGroup: /system.slice/ipsec.service
└─6447 /usr/libexec/ipsec/pluto --leak-detective --config /etc/ipsec.conf --nofork
Apr 16 00:45:15 vpn.kifarunix-demo.com systemd[1]: Starting Internet Key Exchange (IKE) Protocol Daemon for IPsec...
Apr 16 00:45:15 vpn.kifarunix-demo.com ipsec[6435]: nflog ipsec capture disabled
Apr 16 00:45:15 vpn.kifarunix-demo.com systemd[1]: Started Internet Key Exchange (IKE) Protocol Daemon for IPsec.
Or use the command;
ipsec statusSample output (pay attention to the line Total IPsec connections:);
000 using kernel interface: xfrm
000
000 interface lo UDP [::1]:500
000 interface lo UDP 127.0.0.1:4500
000 interface lo UDP 127.0.0.1:500
000 interface enp0s3 UDP 55.66.77.88:4500
000 interface enp0s3 UDP 55.66.77.88:500
000 interface enp0s8 UDP 192.168.0.1:4500
000 interface enp0s8 UDP 192.168.0.1:500
000
000 fips mode=disabled;
000 SElinux=enabled
000 seccomp=disabled
000
000 config setup options:
000
000 configdir=/etc, configfile=/etc/ipsec.conf, secrets=/etc/ipsec.secrets, ipsecdir=/etc/ipsec.d
000 nssdir=/etc/ipsec.d, dumpdir=/run/pluto, statsbin=unset
000 dnssec-rootkey-file=/var/lib/unbound/root.key, dnssec-trusted=<unset>
000 sbindir=/usr/sbin, libexecdir=/usr/libexec/ipsec
000 pluto_version=4.4, pluto_vendorid=OE-Libreswan-4.4, audit-log=yes
000 nhelpers=-1, uniqueids=yes, dnssec-enable=yes, logappend=yes, logip=yes, shuntlifetime=900s, xfrmlifetime=30s
000 ddos-cookies-threshold=25000, ddos-max-halfopen=50000, ddos-mode=auto, ikev1-policy=accept
000 ikebuf=0, msg_errqueue=yes, crl-strict=no, crlcheckinterval=0, listen=<any>, nflog-all=0
000 ocsp-enable=no, ocsp-strict=no, ocsp-timeout=2, ocsp-uri=<unset>
000 ocsp-trust-name=<unset>
000 ocsp-cache-size=1000, ocsp-cache-min-age=3600, ocsp-cache-max-age=86400, ocsp-method=get
000 global-redirect=no, global-redirect-to=<unset>
000 secctx-attr-type=32001
000 debug:
000
000 nat-traversal=yes, keep-alive=20, nat-ikeport=4500
000 virtual-private (%priv):
000
000 Kernel algorithms supported:
000
000 algorithm ESP encrypt: name=3DES_CBC, keysizemin=192, keysizemax=192
000 algorithm ESP encrypt: name=AES_CBC, keysizemin=128, keysizemax=256
000 algorithm ESP encrypt: name=AES_CCM_12, keysizemin=128, keysizemax=256
000 algorithm ESP encrypt: name=AES_CCM_16, keysizemin=128, keysizemax=256
000 algorithm ESP encrypt: name=AES_CCM_8, keysizemin=128, keysizemax=256
000 algorithm ESP encrypt: name=AES_CTR, keysizemin=128, keysizemax=256
000 algorithm ESP encrypt: name=AES_GCM_12, keysizemin=128, keysizemax=256
000 algorithm ESP encrypt: name=AES_GCM_16, keysizemin=128, keysizemax=256
000 algorithm ESP encrypt: name=AES_GCM_8, keysizemin=128, keysizemax=256
000 algorithm ESP encrypt: name=CAMELLIA_CBC, keysizemin=128, keysizemax=256
000 algorithm ESP encrypt: name=CHACHA20_POLY1305, keysizemin=256, keysizemax=256
000 algorithm ESP encrypt: name=NULL, keysizemin=0, keysizemax=0
000 algorithm ESP encrypt: name=NULL_AUTH_AES_GMAC, keysizemin=128, keysizemax=256
000 algorithm AH/ESP auth: name=AES_CMAC_96, key-length=128
000 algorithm AH/ESP auth: name=AES_XCBC_96, key-length=128
000 algorithm AH/ESP auth: name=HMAC_MD5_96, key-length=128
000 algorithm AH/ESP auth: name=HMAC_SHA1_96, key-length=160
000 algorithm AH/ESP auth: name=HMAC_SHA2_256_128, key-length=256
000 algorithm AH/ESP auth: name=HMAC_SHA2_256_TRUNCBUG, key-length=256
000 algorithm AH/ESP auth: name=HMAC_SHA2_384_192, key-length=384
000 algorithm AH/ESP auth: name=HMAC_SHA2_512_256, key-length=512
000 algorithm AH/ESP auth: name=NONE, key-length=0
000
000 IKE algorithms supported:
000
000 algorithm IKE encrypt: v1id=5, v1name=OAKLEY_3DES_CBC, v2id=3, v2name=3DES, blocksize=8, keydeflen=192
000 algorithm IKE encrypt: v1id=8, v1name=OAKLEY_CAMELLIA_CBC, v2id=23, v2name=CAMELLIA_CBC, blocksize=16, keydeflen=128
000 algorithm IKE encrypt: v1id=-1, v1name=n/a, v2id=20, v2name=AES_GCM_C, blocksize=16, keydeflen=128
000 algorithm IKE encrypt: v1id=-1, v1name=n/a, v2id=19, v2name=AES_GCM_B, blocksize=16, keydeflen=128
000 algorithm IKE encrypt: v1id=-1, v1name=n/a, v2id=18, v2name=AES_GCM_A, blocksize=16, keydeflen=128
000 algorithm IKE encrypt: v1id=13, v1name=OAKLEY_AES_CTR, v2id=13, v2name=AES_CTR, blocksize=16, keydeflen=128
000 algorithm IKE encrypt: v1id=7, v1name=OAKLEY_AES_CBC, v2id=12, v2name=AES_CBC, blocksize=16, keydeflen=128
000 algorithm IKE encrypt: v1id=-1, v1name=n/a, v2id=28, v2name=CHACHA20_POLY1305, blocksize=16, keydeflen=256
000 algorithm IKE PRF: name=HMAC_MD5, hashlen=16
000 algorithm IKE PRF: name=HMAC_SHA1, hashlen=20
000 algorithm IKE PRF: name=HMAC_SHA2_256, hashlen=32
000 algorithm IKE PRF: name=HMAC_SHA2_384, hashlen=48
000 algorithm IKE PRF: name=HMAC_SHA2_512, hashlen=64
000 algorithm IKE PRF: name=AES_XCBC, hashlen=16
000 algorithm IKE DH Key Exchange: name=MODP1024, bits=1024
000 algorithm IKE DH Key Exchange: name=MODP1536, bits=1536
000 algorithm IKE DH Key Exchange: name=MODP2048, bits=2048
000 algorithm IKE DH Key Exchange: name=MODP3072, bits=3072
000 algorithm IKE DH Key Exchange: name=MODP4096, bits=4096
000 algorithm IKE DH Key Exchange: name=MODP6144, bits=6144
000 algorithm IKE DH Key Exchange: name=MODP8192, bits=8192
000 algorithm IKE DH Key Exchange: name=DH19, bits=512
000 algorithm IKE DH Key Exchange: name=DH20, bits=768
000 algorithm IKE DH Key Exchange: name=DH21, bits=1056
000 algorithm IKE DH Key Exchange: name=DH31, bits=256
000
000 stats db_ops: {curr_cnt, total_cnt, maxsz} :context={0,0,0} trans={0,0,0} attrs={0,0,0}
000
000 Connection list:
000
000 "libreswan-pfsense": 192.168.0.0/24===55.66.77.88<55.66.77.88>...11.22.33.44<11.22.33.44>===172.16.0.0/24; erouted; eroute owner: #2
000 "libreswan-pfsense": oriented; my_ip=unset; their_ip=unset; my_updown=ipsec _updown;
000 "libreswan-pfsense": xauth us:none, xauth them:none, my_username=[any]; their_username=[any]
000 "libreswan-pfsense": our auth:secret, their auth:secret
000 "libreswan-pfsense": modecfg info: us:none, them:none, modecfg policy:push, dns:unset, domains:unset, cat:unset;
000 "libreswan-pfsense": sec_label:unset;
000 "libreswan-pfsense": ike_life: 86400s; ipsec_life: 3600s; replay_window: 32; rekey_margin: 540s; rekey_fuzz: 100%; keyingtries: 5;
000 "libreswan-pfsense": retransmit-interval: 500ms; retransmit-timeout: 60s; iketcp:no; iketcp-port:4500;
000 "libreswan-pfsense": initial-contact:no; cisco-unity:no; fake-strongswan:no; send-vendorid:no; send-no-esp-tfc:no;
000 "libreswan-pfsense": policy: IKEv2+PSK+ENCRYPT+TUNNEL+PFS+UP+IKE_FRAG_ALLOW+ESN_NO;
000 "libreswan-pfsense": v2-auth-hash-policy: none;
000 "libreswan-pfsense": conn_prio: 24,24; interface: enp0s3; metric: 0; mtu: unset; sa_prio:auto; sa_tfc:none;
000 "libreswan-pfsense": nflog-group: unset; mark: unset; vti-iface:unset; vti-routing:no; vti-shared:no; nic-offload:auto;
000 "libreswan-pfsense": our idtype: ID_IPV4_ADDR; our id=55.66.77.88; their idtype: ID_IPV4_ADDR; their id=11.22.33.44
000 "libreswan-pfsense": dpd: action:restart; delay:30; timeout:120; nat-t: encaps:auto; nat_keepalive:yes; ikev1_natt:both
000 "libreswan-pfsense": newest ISAKMP SA: #1; newest IPsec SA: #2; conn serial: $1;
000 "libreswan-pfsense": IKE algorithms: AES_CBC_256-HMAC_SHA2_256-DH20
000 "libreswan-pfsense": IKEv2 algorithm newest: AES_CBC_256-HMAC_SHA2_256-DH20
000 "libreswan-pfsense": ESP algorithms: AES_CBC_256-HMAC_SHA2_256_128-DH20
000 "libreswan-pfsense": ESP algorithm newest: AES_CBC_256-HMAC_SHA2_256_128; pfsgroup=<Phase1>
000
000 Total IPsec connections: loaded 1, active 1
000
000 State Information: DDoS cookies not required, Accepting new IKE connections
000 IKE SAs: total(1), half-open(0), open(0), authenticated(1), anonymous(0)
000 IPsec SAs: total(1), authenticated(1), anonymous(0)
000
000 #1: "libreswan-pfsense":500 STATE_V2_ESTABLISHED_IKE_SA (established IKE SA); EVENT_SA_REKEY in 85347s; newest ISAKMP; idle;
000 #2: "libreswan-pfsense":500 STATE_V2_ESTABLISHED_CHILD_SA (IPsec SA established); EVENT_SA_REKEY in 2788s; newest IPSEC; eroute owner; isakmp#1; idle;
000 #2: "libreswan-pfsense" [email protected] [email protected] [email protected] [email protected] Traffic: ESPin=0B ESPout=0B! ESPmax=0B
000
000 Bare Shunt list:
000
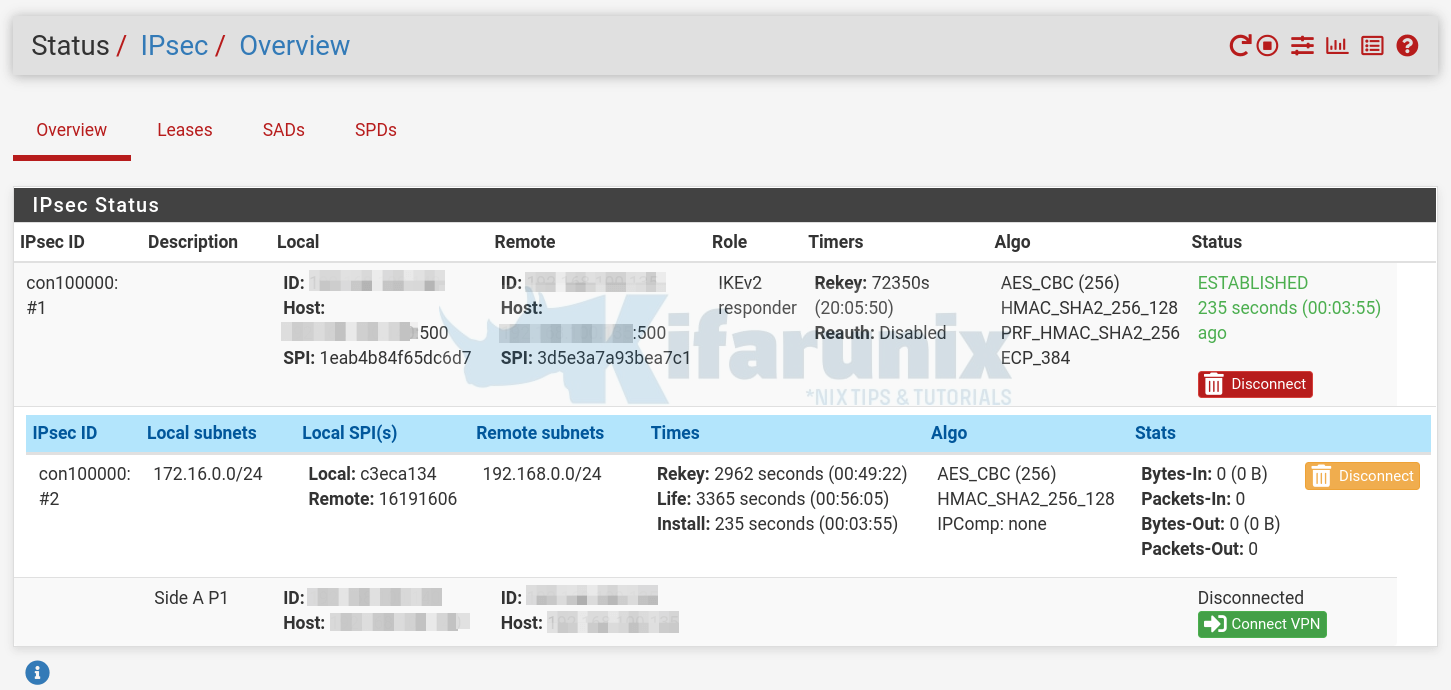
Check Status on pfSense As well;
Test the connection between Local LANs
The tunnel is now established and you need to find out what the two remote LANS can communicate.
Considering that you have correct firewall rules in place, everything should work just fine now.
On Side A, let check connectivity to from the system 172.16.0.20 to Side B local system, 192.168.0.200.
ip a
1: lo: mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: enp0s3: mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 08:00:27:80:75:65 brd ff:ff:ff:ff:ff:ff
inet 172.16.0.20/24 brd 172.16.0.255 scope global enp0s3
valid_lft forever preferred_lft forever
inet6 fe80::a00:27ff:fe80:7565/64 scope link
valid_lft forever preferred_lft forever
ip rdefault via 172.16.0.1 dev enp0s3 onlink
172.16.0.0/24 dev enp0s3 proto kernel scope link src 172.16.0.20Check connectivity to remote system;
ping -c 4 192.16.0.200PING 192.16.0.200 (192.16.0.200) 56(84) bytes of data.
64 bytes from 192.16.0.200: icmp_seq=1 ttl=48 time=251 ms
64 bytes from 192.16.0.200: icmp_seq=2 ttl=48 time=274 ms
64 bytes from 192.16.0.200: icmp_seq=3 ttl=48 time=296 ms
64 bytes from 192.16.0.200: icmp_seq=4 ttl=48 time=196 ms
--- 192.16.0.200 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3006ms
rtt min/avg/max/mdev = 195.909/254.192/296.481/37.353 ms
Check connection to SSH;
telnet 192.168.0.200 22Trying 192.168.0.200...
Connected to 192.168.0.200.
Escape character is '^]'.
SSH-2.0-OpenSSH_8.4p1 Debian-5
^]
telnet> quit
Connection closed.
On Side B, let check connectivity to from the system 192.168.0.200 to Side A local system, 172.16.0.20.
ip a
1: lo: mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: enp0s3: mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 08:00:27:88:1b:ae brd ff:ff:ff:ff:ff:ff
inet 192.168.0.200/24 brd 192.168.0.255 scope global enp0s3
valid_lft forever preferred_lft forever
inet6 fe80::a00:27ff:fe88:1bae/64 scope link
valid_lft forever preferred_lft forever
ip rdefault via 192.168.0.1 dev enp0s3 onlink
192.168.0.0/24 dev enp0s3 proto kernel scope link src 192.168.0.200Check connectivity to remote system;
ping -c 4 172.16.0.20PING 172.16.0.20 (172.16.0.20) 56(84) bytes of data.
64 bytes from 172.16.0.20: icmp_seq=1 ttl=62 time=0.685 ms
64 bytes from 172.16.0.20: icmp_seq=2 ttl=62 time=1.12 ms
64 bytes from 172.16.0.20: icmp_seq=3 ttl=62 time=1.12 ms
64 bytes from 172.16.0.20: icmp_seq=4 ttl=62 time=1.31 ms
--- 172.16.0.20 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3015ms
rtt min/avg/max/mdev = 0.685/1.058/1.314/0.230 ms
Check connection to SSH;
telnet 172.16.0.20 22Trying 172.16.0.20...
Connected to 172.16.0.20.
Escape character is '^]'.
SSH-2.0-OpenSSH_8.4p1 Debian-5
^]
telnet> quit
Connection closed.
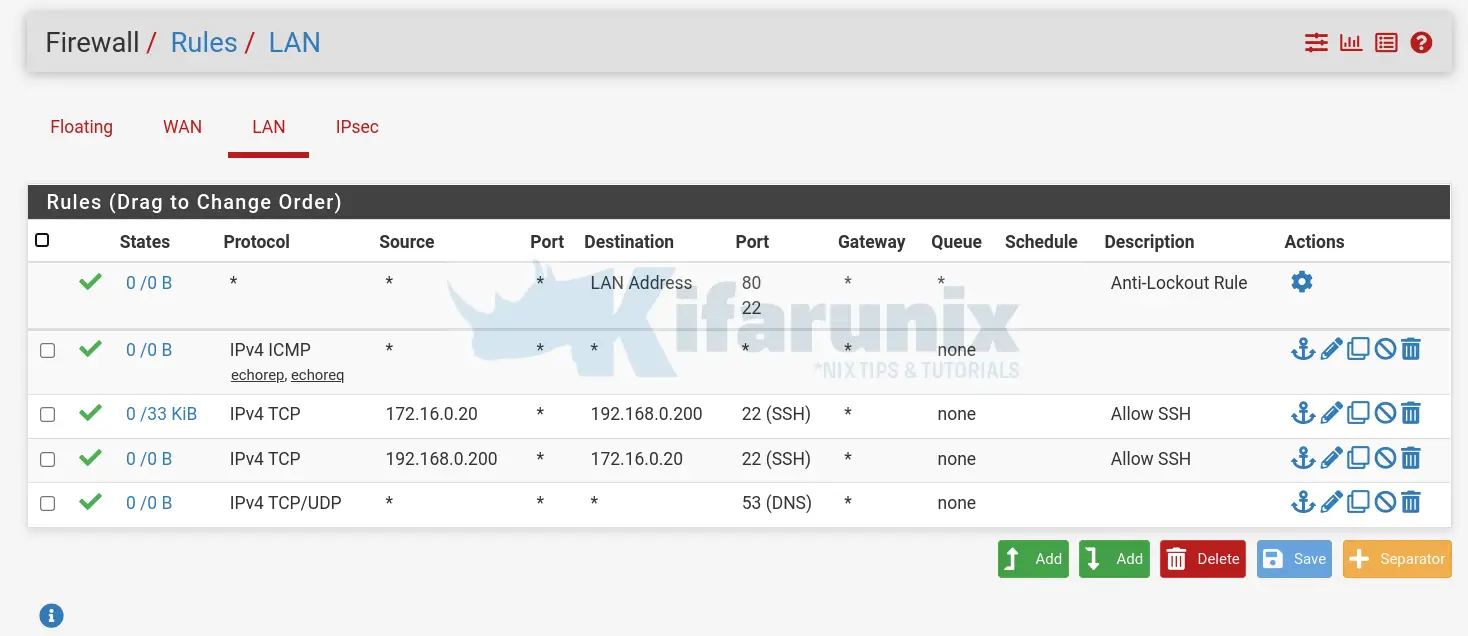
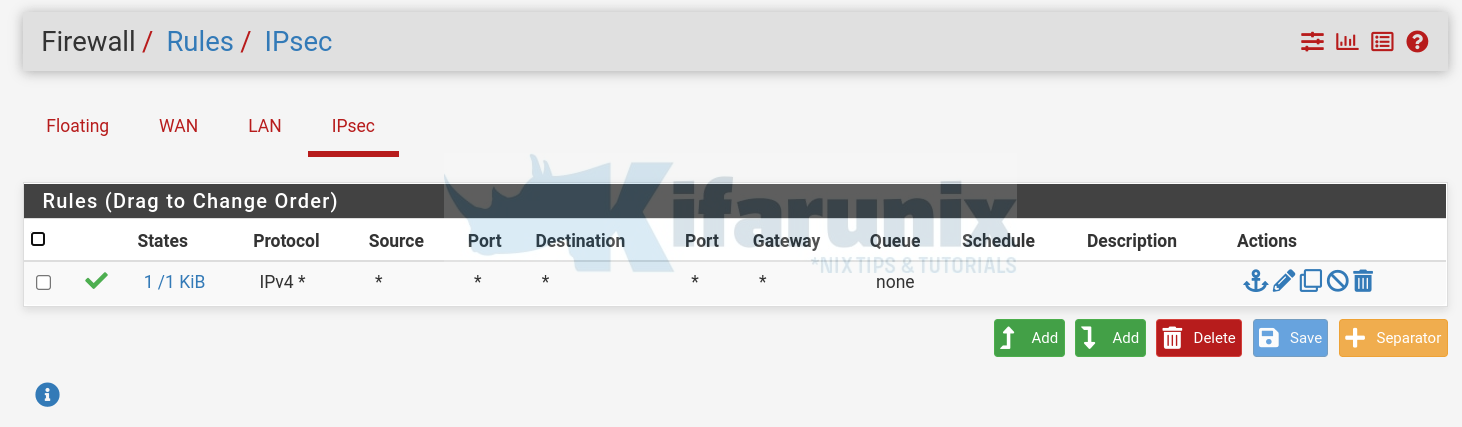
So what Firewall rules we have in place?
on Side A, pfSense Firewall rules;
On Libreswan CentOS Linux Router firewall rules;
iptables -L -nvChain INPUT (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
273 39388 ACCEPT esp -- * * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT udp -- * * 0.0.0.0/0 0.0.0.0/0 udp dpt:4500
101 10908 ACCEPT udp -- * * 0.0.0.0/0 0.0.0.0/0 udp dpt:500
1 84 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
246 16940 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:22
119 18126 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
280 20726 ACCEPT all -- enp0s3 enp0s8 0.0.0.0/0 0.0.0.0/0
211 23856 ACCEPT all -- enp0s8 enp0s3 0.0.0.0/0 0.0.0.0/0
0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain OUTPUT (policy ACCEPT 746 packets, 101K bytes)
pkts bytes target prot opt in out source destination
iptables -t nat -L -nvChain PREROUTING (policy ACCEPT 18 packets, 1319 bytes)
pkts bytes target prot opt in out source destination
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain POSTROUTING (policy ACCEPT 10 packets, 672 bytes)
pkts bytes target prot opt in out source destination
31 2265 MASQUERADE all -- * * 0.0.0.0/0 0.0.0.0/0 ! match-set ipsecvpn dst
Chain OUTPUT (policy ACCEPT 30 packets, 2172 bytes)
pkts bytes target prot opt in out source destination
And that is it on how to setup Site-to-Site IPSec VPN between pfSense and Libreswan.