In this tutorial, we are going to learn how to install and setup Squid Proxy on Debian 11/Debian 10.
Squid is a full-featured web proxy cache application which provides proxy and cache services for HTTP, FTP, SSL requests and DNS lookups. It also performs transparent caching that reduces bandwidth and improves response time by caching and reusing frequently requested web pages.
Installing Setup Squid Proxy on Debian 11/10
Run system update
To begin with, ensure that your system repos are up-to-date.
apt updateInstall Squid Proxy on Debian
Squid proxy is available on the default Debian 11/Debian 10 repositories.
apt-cache policy squidSample output on Debian 11
squid:
Installed: (none)
Candidate: 4.13-10
Version table:
4.13-10 500
500 http://deb.debian.org/debian bullseye/main amd64 PackagesTherefore, you can install it by running the command and can be installed by running the command;
apt install squid -yRunning Squid on Debian 11/Debian 10
When installed, Squid is started and enabled to run on system boot;
systemctl status squid
● squid.service - Squid Web Proxy Server
Loaded: loaded (/lib/systemd/system/squid.service; enabled; vendor preset: enabled)
Active: active (running) since Wed 2021-10-20 09:01:18 EAT; 38s ago
Docs: man:squid(8)
Process: 1718 ExecStartPre=/usr/sbin/squid --foreground -z (code=exited, status=0/SUCCESS)
Main PID: 1721 (squid)
Tasks: 4 (limit: 1133)
Memory: 15.6M
CPU: 156ms
CGroup: /system.slice/squid.service
├─1721 /usr/sbin/squid --foreground -sYC
├─1723 (squid-1) --kid squid-1 --foreground -sYC
├─1724 (logfile-daemon) /var/log/squid/access.log
└─1725 (pinger)
Oct 20 09:01:18 bullseye.kifarunix-demo.com squid[1723]: Using Least Load store dir selection
Oct 20 09:01:18 bullseye.kifarunix-demo.com squid[1723]: Set Current Directory to /var/spool/squid
Oct 20 09:01:18 bullseye.kifarunix-demo.com squid[1723]: Finished loading MIME types and icons.
Oct 20 09:01:18 bullseye.kifarunix-demo.com squid[1723]: HTCP Disabled.
Oct 20 09:01:18 bullseye.kifarunix-demo.com squid[1723]: Pinger socket opened on FD 14
Oct 20 09:01:18 bullseye.kifarunix-demo.com systemd[1]: Started Squid Web Proxy Server.
Oct 20 09:01:18 bullseye.kifarunix-demo.com squid[1723]: Squid plugin modules loaded: 0
Oct 20 09:01:18 bullseye.kifarunix-demo.com squid[1723]: Adaptation support is off.
Oct 20 09:01:18 bullseye.kifarunix-demo.com squid[1723]: Accepting HTTP Socket connections at local=[::]:3128 remote=[::] FD 12 flags=9
Oct 20 09:01:19 bullseye.kifarunix-demo.com squid[1723]: storeLateRelease: released 0 objects
To check if enabled to run on system boot;
systemctl is-enabled squidIf the output of the command is not, enabled, then enable it by running;
systemctl enable squidConfiguring Squid Proxy Server on Debian 11/Debian 10
/etc/squid/squid.conf is the default Squid Proxy configuration.
The configuration has the recommended minimum settings. However, we will modify this configuration to make a few changes.
You can also have other configurations under /etc/squid/conf.d/ directory.
Before you can proceed, create a backup of the default configuration file.
cp /etc/squid/squid.conf{,.old}By default, the Squid configuration file looks like as shown below (with comment lines removed);
grep -vE "^#|^$" /etc/squid/squid.conf
acl localnet src 0.0.0.1-0.255.255.255 # RFC 1122 "this" network (LAN)
acl localnet src 10.0.0.0/8 # RFC 1918 local private network (LAN)
acl localnet src 100.64.0.0/10 # RFC 6598 shared address space (CGN)
acl localnet src 169.254.0.0/16 # RFC 3927 link-local (directly plugged) machines
acl localnet src 172.16.0.0/12 # RFC 1918 local private network (LAN)
acl localnet src 192.168.0.0/16 # RFC 1918 local private network (LAN)
acl localnet src fc00::/7 # RFC 4193 local private network range
acl localnet src fe80::/10 # RFC 4291 link-local (directly plugged) machines
acl SSL_ports port 443
acl Safe_ports port 80 # http
acl Safe_ports port 21 # ftp
acl Safe_ports port 443 # https
acl Safe_ports port 70 # gopher
acl Safe_ports port 210 # wais
acl Safe_ports port 1025-65535 # unregistered ports
acl Safe_ports port 280 # http-mgmt
acl Safe_ports port 488 # gss-http
acl Safe_ports port 591 # filemaker
acl Safe_ports port 777 # multiling http
acl CONNECT method CONNECT
http_access deny !Safe_ports
http_access deny CONNECT !SSL_ports
http_access allow localhost manager
http_access deny manager
include /etc/squid/conf.d/*
http_access allow localhost
http_access deny all
http_port 3128
coredump_dir /var/spool/squid
refresh_pattern ^ftp: 1440 20% 10080
refresh_pattern ^gopher: 1440 0% 1440
refresh_pattern -i (/cgi-bin/|\?) 0 0% 0
refresh_pattern . 0 20% 4320
Configure Squid Access Control Policies
If you already noticed, the above configuration file has ACLs for specific networks and safe ports. You can modify them to include your safe ports as well as the your local networks whose Squid should proxy for.
When defining an ACL, each and every one of them must begin with an acl name and acl type followed by either type-specific arguments or a quoted filename that they are read from;
acl aclname acltype argument ...acl aclname acltype "file" ...When using “file“, the file should contain one item per line.
vim /etc/squid/squid.confIn this tutorial, we will create an ACL for our LAN network, 192.168.58.0/24.
We append this line just above the SSL ports ACL.
Replace the name of the ACL and the source network appropriately.
...
acl localnet src fe80::/10 # RFC 4291 link-local (directly plugged) machines
acl kifarunix-demo-net src 192.168.58.0/24 # My LAN network ACL
acl SSL_ports port 443
...Read more about ACL configuration directives on Squid Wiki page.
You can comment out (adding # at the beginning of the lines) the default ACLs.
#acl localnet src 0.0.0.1-0.255.255.255 # RFC 1122 "this" network (LAN)
#acl localnet src 10.0.0.0/8 # RFC 1918 local private network (LAN)
#acl localnet src 100.64.0.0/10 # RFC 6598 shared address space (CGN)
#acl localnet src 169.254.0.0/16 # RFC 3927 link-local (directly plugged) machines
#acl localnet src 172.16.0.0/12 # RFC 1918 local private network (LAN)
#acl localnet src 192.168.0.0/16 # RFC 1918 local private network (LAN)
#acl localnet src fc00::/7 # RFC 4193 local private network range
#acl localnet src fe80::/10 # RFC 4291 link-local (directly plugged) machines
acl kifarunix-demo-net src 192.168.58.0/24 # My LAN network ACL
...
Allow or Deny Access Based on defined ACL
Once you have the ACL in place, you can then use the http_access directive to define the ACL allowed or denied to use the proxy to access external network.
Therefore, to allow our network, defined by our ACL, kifarunix-demo-net, external access, add the line below;
...
#http_access allow localnet
http_access allow localhost
http_access allow kifarunix-demo-net # Allow kifarunix-demo-net
# And finally deny all other access to this proxy
http_access deny allThe last entry should always be http_access deny all.
Deny Access to Specific Websites
Access to specific websites can be restricted using Squid Proxy. For example to block access to youtube, facebook, netflix;
- you would have to create a file that defines the domains of these websites as shown below. Exit the squid.conf and create the file.
vim /etc/squid/denied-sites.squid.youtube.com
.facebook.com
.netflix.comNext, create an ACL for the restricted sites above in the squid configuration file and set the deny rule for the defined ACL.
acl deniedsites dstdomain "/etc/squid/denied-sites.squid"- or you would list the domain names, space separated on the ACL statement.
acl deniedsites dstdomain youtube.com facebook.com netflix.comUpdate squid configuration file.
...
#acl localnet src fe80::/10 # RFC 4291 link-local (directly plugged) machines
acl kifarunix-demo-net src 192.168.58.0/24 # My LAN network ACL
acl deniedsites dstdomain "/etc/squid/denied-sites.squid" ## Sites to Block access to ###
...
http_access allow localhost
http_access deny deniedsites # Deny access to facebook, youtube, netflix
http_access allow kifarunix-demo-net # Allow kifarunix-demo-net
# And finally deny all other access to this proxy
http_access deny all
...
Block Sites based on Specific Keywords
You can also restrict access to a website by the use of a keyword. Create a file with specific keywords as shown below;
vim /etc/squid/banned-keywords.squidporn
ads
movie
gambleMake the necessary changes on squid configuration file by adding the ACL for above keywords;
acl keyword-ban url_regex -i "/etc/squid/keyword-ban.squid"
...
acl kifarunix-demo-net src 192.168.58.0/24 # My LAN network ACL
acl deniedsites dstdomain "/etc/squid/denied-sites.squid" ## Sites to Block access to ###
acl keyword-ban url_regex -i "/etc/squid/keyword-ban.squid" ## Banned Keywords
...
http_access allow localhost
http_access deny deniedsites # Deny access to facebook, youtube, netflix
http_access deny keyword-ban # Deny access based on keywords
http_access allow kifarunix-demo-net # Allow kifarunix-demo-net
http_access deny all
...
NOTE: http_access entries are processed from top to bottom and depending on which occurs first, access is allowed or denied.
Masking Outgoing Traffic
As much as you use proxy server to anonymize your IP addresses by presenting the IP address of the proxy to other web servers, proxy servers may expose your IP addresses on the outgoing HTTP requests. You can however disable this by including the following directives at the end of your squid configuration file.
Disable Via headers in requests and replies using the directive, via off.
via offConfigure Squid not to append your client’s IP address in the HTTP requests it forwards;
forwarded_for offRemove Squid proxy headers to avoid revealing identity of Squid proxy server.
request_header_access From deny all
request_header_access Server deny all
request_header_access WWW-Authenticate deny all
request_header_access Link deny all
request_header_access Cache-Control deny all
request_header_access Proxy-Connection deny all
request_header_access X-Cache deny all
request_header_access X-Cache-Lookup deny all
request_header_access Via deny all
request_header_access X-Forwarded-For deny all
request_header_access Pragma deny all
request_header_access Keep-Alive deny all
Change Squid Default Port
Squid proxy listens on TCP port 3128 by default.
To change this port, open the /etc/squid/squid.conf configuration file and replace the value of the http_port with your desired port number.
For example, to change the default port to 8888, as long as no other application is listening on the same port;
...
# Squid normally listens to port 3128
# http_port 3128 << Comment the line by adding #
http_port 8888
...You can also set it to listen on a specific IP (Replace the IP address accordingly)
http_port 192.168.58.26:3128Save and exit the configuration file once you are done with the configuration.
Our final squid.conf file now looks like;
cat /etc/squid/squid.conf
#acl localnet src 0.0.0.1-0.255.255.255 # RFC 1122 "this" network (LAN)
#acl localnet src 10.0.0.0/8 # RFC 1918 local private network (LAN)
#acl localnet src 100.64.0.0/10 # RFC 6598 shared address space (CGN)
#acl localnet src 169.254.0.0/16 # RFC 3927 link-local (directly plugged) machines
#acl localnet src 172.16.0.0/12 # RFC 1918 local private network (LAN)
#acl localnet src 192.168.0.0/16 # RFC 1918 local private network (LAN)
#acl localnet src fc00::/7 # RFC 4193 local private network range
#acl localnet src fe80::/10 # RFC 4291 link-local (directly plugged) machines
acl kifarunix-demo-net src 192.168.58.0/24 # My LAN network ACL
acl deniedsites dstdomain "/etc/squid/denied-sites.squid" ## Sites to Block access to ###
acl keyword-ban url_regex -i "/etc/squid/keyword-ban.squid" ## Banned Keywords
acl SSL_ports port 443
acl Safe_ports port 80 # http
acl Safe_ports port 21 # ftp
acl Safe_ports port 443 # https
acl Safe_ports port 70 # gopher
acl Safe_ports port 210 # wais
acl Safe_ports port 1025-65535 # unregistered ports
acl Safe_ports port 280 # http-mgmt
acl Safe_ports port 488 # gss-http
acl Safe_ports port 591 # filemaker
acl Safe_ports port 777 # multiling http
acl CONNECT method CONNECT
http_access deny !Safe_ports
http_access deny CONNECT !SSL_ports
http_access allow localhost manager
http_access deny manager
include /etc/squid/conf.d/*
http_access allow localhost
http_access deny deniedsites # Deny access to facebook, youtube, netflix
http_access deny keyword-ban # Deny access based on keywords
http_access allow kifarunix-demo-net # Allow kifarunix-demo-net
http_access deny all
#http_port 3128
http_port 192.168.58.26:3128
coredump_dir /var/spool/squid
refresh_pattern ^ftp: 1440 20% 10080
refresh_pattern ^gopher: 1440 0% 1440
refresh_pattern -i (/cgi-bin/|\?) 0 0% 0
refresh_pattern . 0 20% 4320
via off
forwarded_for off
request_header_access From deny all
request_header_access Server deny all
request_header_access WWW-Authenticate deny all
request_header_access Link deny all
request_header_access Cache-Control deny all
request_header_access Proxy-Connection deny all
request_header_access X-Cache deny all
request_header_access X-Cache-Lookup deny all
request_header_access Via deny all
request_header_access X-Forwarded-For deny all
request_header_access Pragma deny all
request_header_access Keep-Alive deny all
Check Squid Configuration File for Errors
squid -k parseIf there is any syntax error, the erroneous lines will be displayed. Be sure to run this command every time you modify your configuration.
Sample config check output;
2021/10/20 09:40:17| Startup: Initializing Authentication Schemes ...
2021/10/20 09:40:17| Startup: Initialized Authentication Scheme 'basic'
2021/10/20 09:40:17| Startup: Initialized Authentication Scheme 'digest'
2021/10/20 09:40:17| Startup: Initialized Authentication Scheme 'negotiate'
2021/10/20 09:40:17| Startup: Initialized Authentication Scheme 'ntlm'
2021/10/20 09:40:17| Startup: Initialized Authentication.
2021/10/20 09:40:17| Processing Configuration File: /etc/squid/squid.conf (depth 0)
2021/10/20 09:40:17| Processing: acl kifarunix-demo-net src 192.168.58.0/24 # My LAN network ACL
2021/10/20 09:40:17| Processing: acl deniedsites dstdomain "/etc/squid/denied-sites.squid" ## Sites to Block access to ###
2021/10/20 09:40:17| Processing: acl keyword-ban url_regex -i "/etc/squid/keyword-ban.squid" ## Banned Keywords
2021/10/20 09:40:17| Processing: acl SSL_ports port 443
2021/10/20 09:40:17| Processing: acl Safe_ports port 80 # http
2021/10/20 09:40:17| Processing: acl Safe_ports port 21 # ftp
2021/10/20 09:40:17| Processing: acl Safe_ports port 443 # https
2021/10/20 09:40:17| Processing: acl Safe_ports port 70 # gopher
2021/10/20 09:40:17| Processing: acl Safe_ports port 210 # wais
2021/10/20 09:40:17| Processing: acl Safe_ports port 1025-65535 # unregistered ports
2021/10/20 09:40:17| Processing: acl Safe_ports port 280 # http-mgmt
2021/10/20 09:40:17| Processing: acl Safe_ports port 488 # gss-http
2021/10/20 09:40:17| Processing: acl Safe_ports port 591 # filemaker
2021/10/20 09:40:17| Processing: acl Safe_ports port 777 # multiling http
2021/10/20 09:40:17| Processing: acl CONNECT method CONNECT
2021/10/20 09:40:17| Processing: http_access deny !Safe_ports
2021/10/20 09:40:17| Processing: http_access deny CONNECT !SSL_ports
2021/10/20 09:40:17| Processing: http_access allow localhost manager
2021/10/20 09:40:17| Processing: http_access deny manager
2021/10/20 09:40:17| Processing: include /etc/squid/conf.d/*
2021/10/20 09:40:17| Processing Configuration File: /etc/squid/conf.d/debian.conf (depth 1)
2021/10/20 09:40:17| Processing: logfile_rotate 0
2021/10/20 09:40:17| Processing: http_access allow localhost
2021/10/20 09:40:17| Processing: http_access deny deniedsites # Deny access to facebook, youtube, netflix
2021/10/20 09:40:17| Processing: http_access deny keyword-ban # Deny access based on keywords
2021/10/20 09:40:17| Processing: http_access allow kifarunix-demo-net # Allow kifarunix-demo-net
2021/10/20 09:40:17| Processing: http_access deny all
2021/10/20 09:40:17| Processing: http_port 192.168.58.26:3128
2021/10/20 09:40:17| Processing: coredump_dir /var/spool/squid
2021/10/20 09:40:17| Processing: refresh_pattern ^ftp: 1440 20% 10080
2021/10/20 09:40:17| Processing: refresh_pattern ^gopher: 1440 0% 1440
2021/10/20 09:40:17| Processing: refresh_pattern -i (/cgi-bin/|\?) 0 0% 0
2021/10/20 09:40:17| Processing: refresh_pattern . 0 20% 4320
2021/10/20 09:40:17| Processing: via off
2021/10/20 09:40:17| Processing: forwarded_for off
2021/10/20 09:40:17| Processing: request_header_access From deny all
2021/10/20 09:40:17| Processing: request_header_access Server deny all
2021/10/20 09:40:17| Processing: request_header_access WWW-Authenticate deny all
2021/10/20 09:40:17| Processing: request_header_access Link deny all
2021/10/20 09:40:17| Processing: request_header_access Cache-Control deny all
2021/10/20 09:40:17| Processing: request_header_access Proxy-Connection deny all
2021/10/20 09:40:17| Processing: request_header_access X-Cache deny all
2021/10/20 09:40:17| Processing: request_header_access X-Cache-Lookup deny all
2021/10/20 09:40:17| Processing: request_header_access Via deny all
2021/10/20 09:40:17| Processing: request_header_access X-Forwarded-For deny all
2021/10/20 09:40:17| Processing: request_header_access Pragma deny all
2021/10/20 09:40:17| Processing: request_header_access Keep-Alive deny all
2021/10/20 09:40:17| WARNING: HTTP requires the use of Via
2021/10/20 09:40:17| Initializing https:// proxy context
Restart Squid
Once you are done with the configuration, save the file and restart squid.
You can reload Squid configuration without actually restarting it using the command;
squid -k reconfigureIf you want to restart the service, then;
systemctl restart squidCheck that Squid is listening on defined port. In this case, we didn’t change the default.
ss -altnp | grep 3128LISTEN 0 256 192.168.58.26:3128 0.0.0.0:* users:(("squid",pid=1948,fd=12))Allow Squid Port on Firewall
If UFW is running, allow open squid proxy port;
ufw allow 3128/tcpConfigure Clients to Connect Through Proxy server
To configure end points to connect to internet via Squid proxy server, you can either set system wide proxy configurations, configure client to use the Squid proxy as the gateway or set the proxy settings on the browser.
System Wide proxy configuration on Debian 11/Debian 10
To set system wide proxy configurations, create a configuration file under /etc/profile.d with environment variables defining squid proxy server details as follows;
vim /etc/profile.d/squid.shReplace the IP address of the Squid server accordingly.
PROXY_URL="192.168.58.26:3128"
HTTP_PROXY=$PROXY_URL
HTTPS_PROXY=$PROXY_URL
FTP_PROXY=$PROXY_URL
http_proxy=$PROXY_URL
https_proxy=$PROXY_URL
ftp_proxy=$PROXY_URL
export HTTP_PROXY HTTPS_PROXY FTP_PROXY http_proxy https_proxy ftp_proxy
After that, source the new configuration file.
source /etc/profile.d/squid.shTo test this, try to download anything from the clients terminal while tailing access logs on squid proxy server.
On the client’s terminal, run;
wget google.com
--2021-10-20 02:46:02-- http://google.com/
Connecting to 192.168.58.26:3128... connected.
Proxy request sent, awaiting response... 301 Moved Permanently
Location: http://www.google.com/ [following]
--2021-10-20 02:46:02-- http://www.google.com/
Reusing existing connection to 192.168.58.26:3128.
Proxy request sent, awaiting response... 200 OK
Length: unspecified [text/html]
Saving to: ‘index.html’
index.html [ <=> ] 14.54K --.-KB/s in 0s
2021-10-20 02:46:03 (29.4 MB/s) - ‘index.html’ saved [14894]
On the Squid proxy server;
tail -f /var/log/squid/access.log1634712362.509 467 192.168.58.1 TCP_MISS/301 656 GET http://google.com/ - HIER_DIRECT/216.58.223.110 text/html
1634712363.038 526 192.168.58.1 TCP_MISS/200 15816 GET http://www.google.com/ - HIER_DIRECT/216.58.223.68 text/htmlConfigure Proxy settings on Firefox browser.
On your Firefox, configure it to connect external network via your Squid server. Preferences > General > Network Settings > Manual Proxy Configuration. Check Use this proxy server for all protocols.
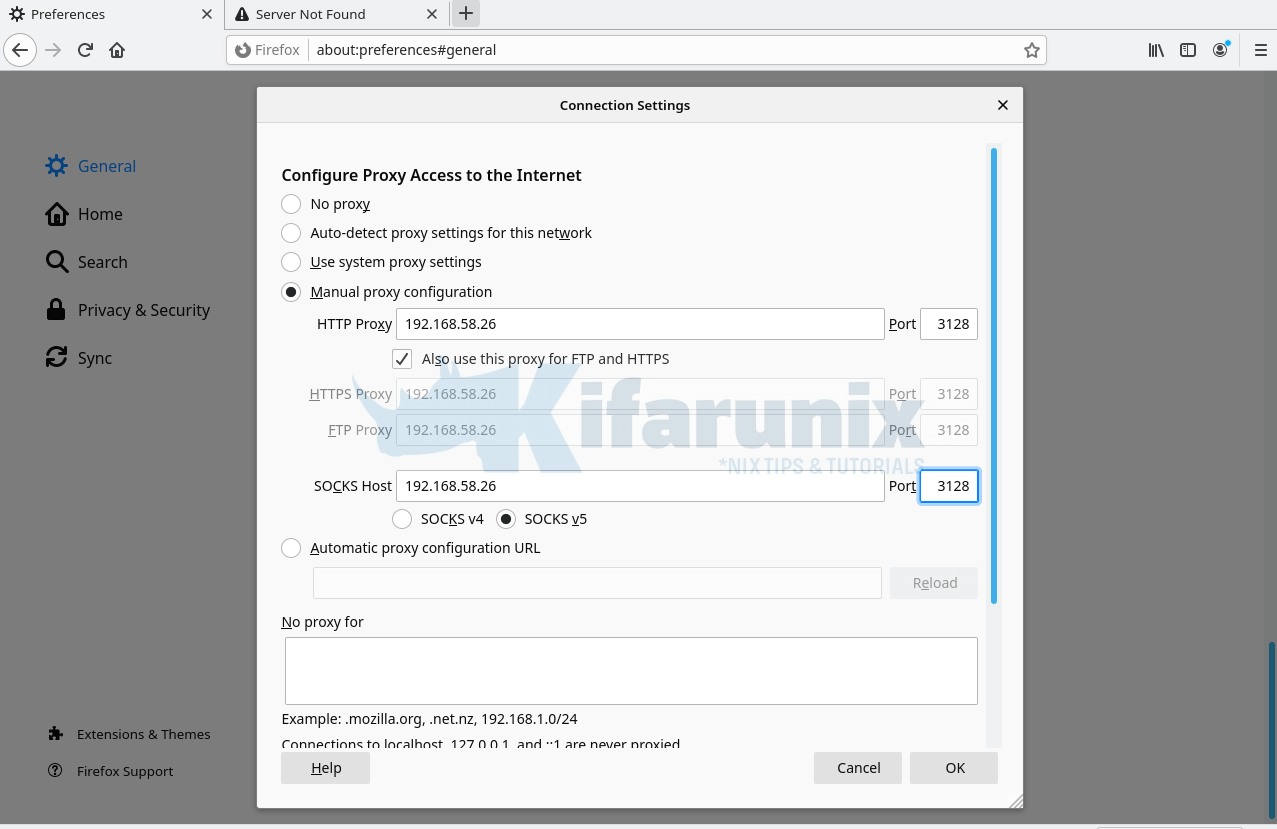
Try to access blocked sites on your browser;
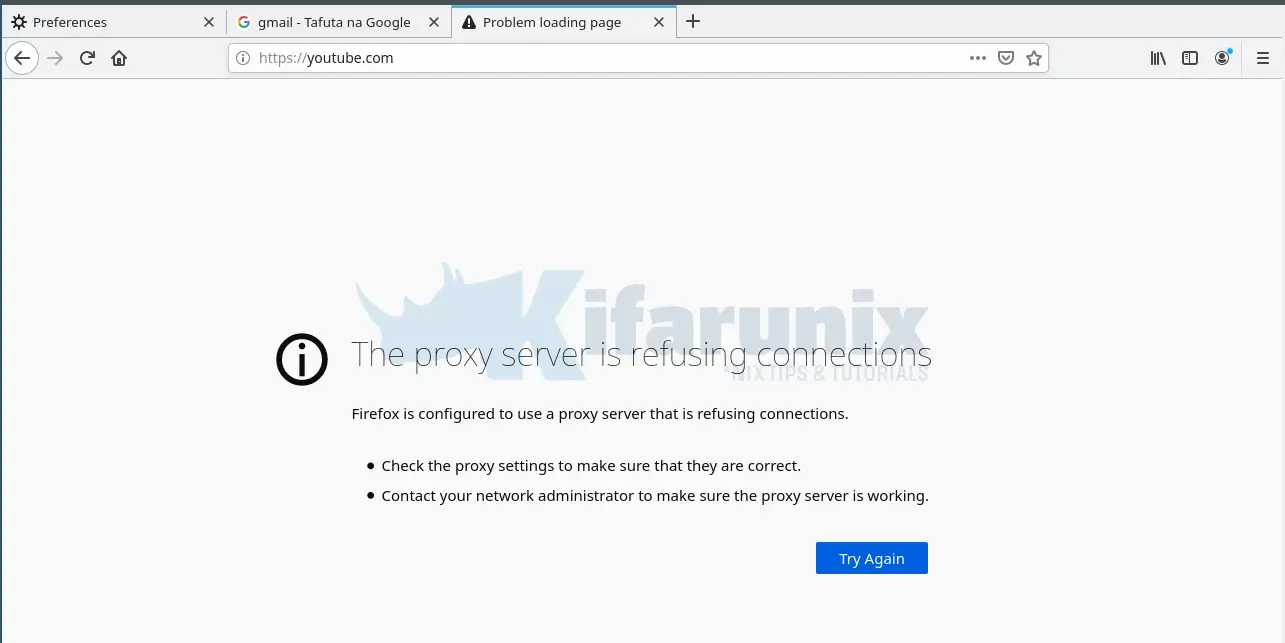
Check the logs on the Squid server.
tail -f /var/log/squid/access.log1634717782.953 0 192.168.58.12 TCP_DENIED/403 4007 CONNECT youtube.com:443 - HIER_NONE/- text/htmlAnd that how to basically configure squid proxy to block or deny access to external resources.
Related Tutorials
Other Tutorials
How to Set System Wide Proxy in Ubuntu 18.04
Monitor Squid logs with Grafana and Graylog

