Welcome to our tutorial on how to configure Postfix to use Gmail SMTP on Ubuntu 20.04 to relay mails. Postfix is a free and open-source mail transfer agent that routes and delivers electronic mail. Postfix MTA can be configured to relay mails through an external SMTP servers such as Gmail SMTP server for a reliable mail delivery.
Configuring Postfix to Use Gmail SMTP Relay
Install Postfix on Ubuntu 20.04
You can install Postfix by installing the postfix package itself or via the mailutils package which installs along with it.
apt install postfixOr
apt install mailutilsDuring installation, you will be prompted to provide some information required to configure Postfix.
Select the Mail Server Type
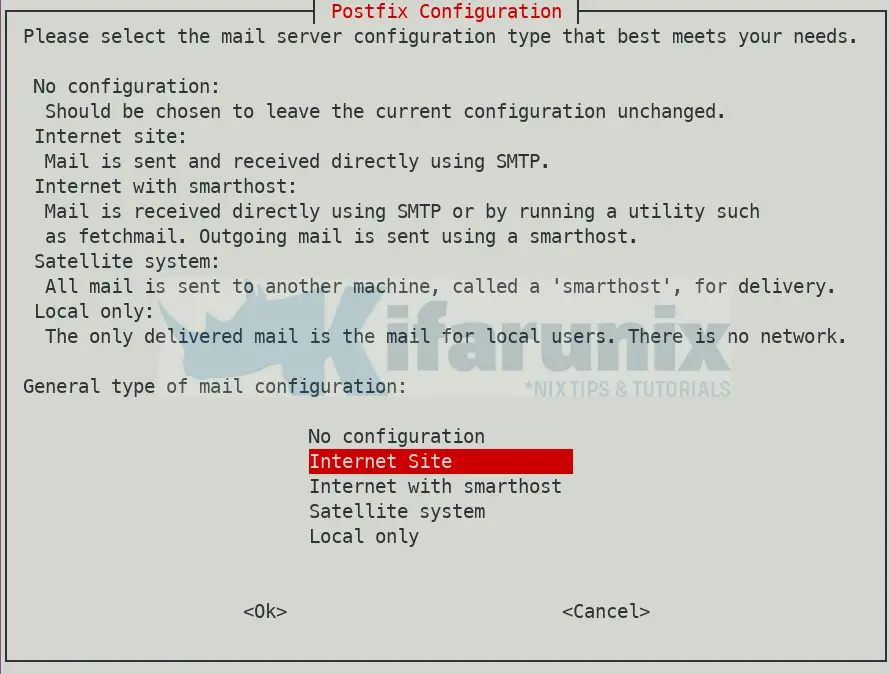
Select the mail server type configuration that best suits your environment needs. You are provided with multiple options;
No configuration: Should be chosen to leave the current configuration unchanged.Internet site: Mail is sent and received directly using SMTP.Internet with smarthost: Mail is received directly using SMTP or by running a utility such as fetchmail. Outgoing mail is sent using a smarthost.Satellite system: All mail is sent to another machine, called a ‘smarthost’, for delivery.Local only: The only delivered mail is the mail for local users. There is no network.
Select Internet Site to enable Postfix to sent and receive mails and press Enter to proceed.
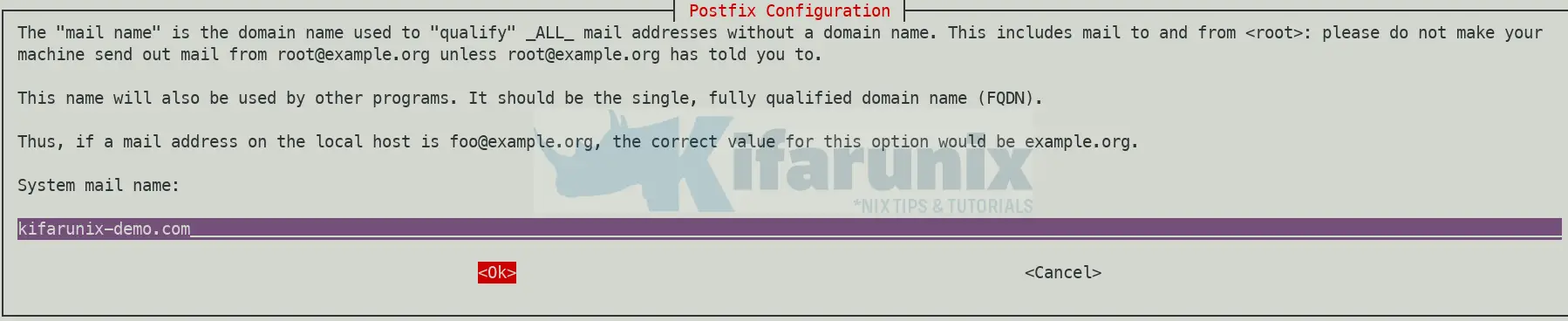
Set System Mail Name
The mail name is the domain name used to “qualify” _ALL_ mail addresses without a domain name, for example, kifarunix-demo.com, in our case.
You can always reset these settings by re-configuring postfix after the installation by executing the command below.
dpkg-reconfigure postfixConfiguring Postfix to Use Gmail SMTP
Postfix is now set up with a default configuration. To make further configuration changes, edit the main Postfix configuration file, /etc/postfix/main.cf and make any necessary changes as needed.
You can view Postfix configuration values using the postconf command;
postconfSet the Postfix Relay server
Postfix can be configured to deliver mails indirectly via a relay host. A relay host can be defined on a Postfix configuration file using the relayhost parameter.
By default, the value of the relayhost parameter is empty. This configures Postfix is to try to deliver mail directly to the Internet, which is usually not desirable.
According to Postfix configuration, different values can be set for the relayhost parameter;
- On an intranet, you can specify your organizational domain name. If your internal DNS uses no MX records, specify the name of the intranet gateway host instead.
- In the case of SMTP or LMTP delivery, specify one or more destinations in the form of a domain name, hostname, hostname:port, [hostname]:port, [hostaddress] or [hostaddress]:port, separated by comma or whitespace. The form [hostname] turns off MX lookups.
In our case, we are setting Postfix relay to Gmail SMTP servers. Hence, open the Postfix main configuration file;
vim /etc/postfix/main.cfFind the line, relayhost =, and set its value to Gmail SMTP domain name as shown below;
...
mydestination = $myhostname, kifarunix-demo.com, ubuntu20, localhost.localdomain, localhost
relayhost = [smtp.gmail.com]:587
mynetworks = 127.0.0.0/8 [::ffff:127.0.0.0]/104 [::1]/128
...Configure Postfix SASL Authentication
According to Postfix:
- SMTP servers need to decide whether an SMTP client is authorized to send mail to remote destinations, or only to destinations that the server itself is responsible for.
- Usually, SMTP servers accept mail to remote destinations when the client’s IP address is in the “same network” as the server’s IP address.
- SMTP clients outside the SMTP server’s network need a different way to get “same network” privileges. To address this need, Postfix supports SASL authentication. With this, a remote SMTP client can authenticate to the Postfix SMTP server, and the Postfix SMTP client can authenticate to a remote SMTP server.
- Once a client is authenticated, a server can give it “same network” privileges.
To enable SASL server authentication, you need to;
- Enable SMTP client-side authentication by setting the value of
smtp_sasl_auth_enabletoyes.smtp_sasl_auth_enable = yes - Configure the Postfix SMTP client to send username and password information to the mail gateway server. This can be done by defining the path to
sasl_passwdas using thesmtp_sasl_password_mapsparameter.smtp_sasl_password_maps = hash:/etc/postfix/sasl_passwd - Enforce STARTTLS encryption for outgoing SMTP to ensure that connection to the remote smtp server will be encrypted using the
smtp_tls_security_levelparameter.smtp_tls_security_level = encrypt - Define the Postfix SMTP client SASL security options. This be zero or more of the following options;
- noplaintext: Disallow methods that use plaintext passwords.
- noactive: Disallow methods subject to active (non-dictionary) attack.
- nodictionary: Disallow methods subject to passive (dictionary) attack.
- noanonymous: Disallow methods that allow anonymous authentication.
- mutual_auth: Only allow methods that provide mutual authentication.
smtp_sasl_security_options = noanonymous
These configs can be updated on Postfix configuration file (See the highlighted lines);
...
relayhost = [smtp.gmail.com]:587
...
#
...
smtp_tls_CApath=/etc/ssl/certs
#smtp_tls_security_level=may
smtp_tls_security_level=encrypt
smtp_tls_session_cache_database = btree:${data_directory}/smtp_scache
...
recipient_delimiter = +
inet_interfaces = all
inet_protocols = all
smtp_sasl_auth_enable = yes
smtp_sasl_password_maps = hash:/etc/postfix/sasl_passwd
smtp_sasl_security_options = noanonymous
Save and exit the configurtion file.
Set the SMTP SASL Credentials
As per our configurations above, the SASL credentials database file is set to /etc/postfix/sasl_passwd.
You should define the SMTP credentials in the format;
# destination credentials
[smtp.domain.name] username:passwordAs shown below;
vim /etc/postfix/sasl_passwd[smtp.gmail.com]:587 [email protected]:passwordReplace the userid@gmail and password with your Gmail account credentials.
Note:
- If you specify the “
[” and “]” in therelayhostdestination, you must as well use the same format in thesmtp_sasl_password_mapsfile. - If you specify a non-default TCP Port (such as “
:submission” or “:587“) in therelayhostdestination, you must as well use the same form in thesmtp_sasl_password_mapsfile.
Secure the SASL Password File
The credentials are set in plaintext. To protect access to the file by other users, make the file read+write only for root.
chown root:root /etc/postfix/sasl_passwd
chmod 600 /etc/postfix/sasl_passwdCreate SASL Password DB file
Postfix requires that the sasl_passwd file to be a database such that it can be read faster. Use postmap command to convert the file into a database, sasl_passwd.db.
postmap /etc/postfix/sasl_passwdThis will assign the same ownership and permissions to the database file as set for the sasl_passwd file above.
ls -l /etc/postfix/sasl_passwd*-rw------- 1 root root 53 Jun 1 13:57 /etc/postfix/sasl_passwd
-rw------- 1 root root 12288 Jun 1 14:06 /etc/postfix/sasl_passwd.dbCheck Postfix Configuration
Run the postfix check command to check the Postfix configuration for any error. Any error should printed on the output.
postfix checkYou can ignore the warning, postfix/postfix-script: warning: symlink leaves directory: /etc/postfix/./makedefs.out.
Restart Postfix
systemctl restart postfixTo check the status;
systemctl status postfix● postfix.service - Postfix Mail Transport Agent
Loaded: loaded (/lib/systemd/system/postfix.service; enabled; vendor preset: enabled)
Active: active (exited) since Mon 2020-06-01 14:11:55 UTC; 5s ago
Process: 7507 ExecStart=/bin/true (code=exited, status=0/SUCCESS)
Main PID: 7507 (code=exited, status=0/SUCCESS)
Jun 01 14:11:55 ubuntu20 systemd[1]: Starting Postfix Mail Transport Agent...
Jun 01 14:11:55 ubuntu20 systemd[1]: Finished Postfix Mail Transport Agent.
Send a Test Mail to Verify Postfix Gmail SMTP Relay
Once you are done with the configuration, you can try to send a test mail to verify that Gmail SMTP relay works fine. You can use mail client or any other for this purpose.
echo "Test Postfix Gmail SMTP Relay" | mail -s "Postfix Gmail SMTP Relay" [email protected]You can tail the logs to check the delivery status;
tail /var/log/mail.logIf you get the error;
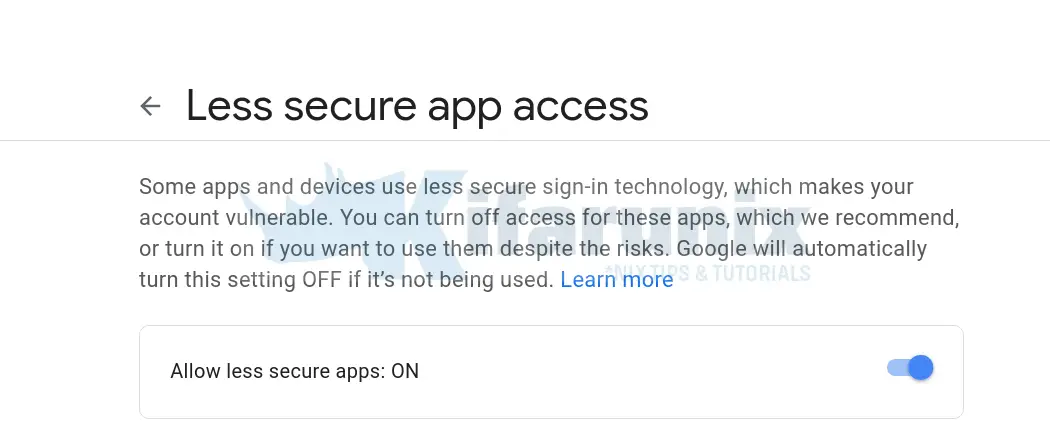
...status=deferred (SASL authentication failed; server smtp.gmail.com[74.125.133.108] said: 535-5.7.8 Username and Password not accepted.You need to login to the account you used for the SASL authentication and enable Less secure app access.
NOTE that the use of less secure app access has been deprecated. See how you can use App password as an alternative in the guide below;
Configure Postfix to Use Gmail App Passwords
After that, retry to sent the test mail and check the logs and hurray, our test mail is delivered, status=sent.
...
Jun 1 14:22:42 ubuntu20 postfix/smtp[7650]: 6892D40186: to=[email protected], relay=smtp.gmail.com[173.194.76.109]:587, delay=4.8, delays=0.35/0.03/3.6/0.8, dsn=2.0.0, status=sent (250 2.0.0 OK 1591021361 k12sm19227410wrn.42 - gsmtp)
...If you get the error, Network is unreachable ;
postfix/smtp[10417]: connect to smtp.gmail.com[2a00:1450:4013:c07::6c]:587: Network is unreachableThe change the following line int he main.cf;
inet_protocols = allto
inet_protocols = ipv4And restart Postfix service.
That marks the end of our guide on how to install and configure Postfix to use Gmail SMTP relay host on Ubuntu 20.04. Enjoy.
Read more about Postfix Configuration on;
Related Tutorials
Configure Nagios Email Notification Using Gmail
Configure Sendmail to Use Gmail Relay on Ubuntu 18.04/Debian 10/9


Great, great, great. Thank you very much !
Also, this worked on Debian 10 too.
On raspberry OS, it worked too, but only after installing libsasl2-modules and reboot.
Great, thanks for the feedback
On Ubuntu 20.04 — I was getting ‘534-5.7.9 Please log in with your web browser and then try again’ in your log’ error and also needed to bypass captcha. Used the following link:
https://accounts.google.com/DisplayUnlockCaptcha
Received ‘534-5.7.9 Please log in with your web browser and then try again’ in my log on Ubuntu 20.04. I needed to bypass the catpcha. Went to following Google link:
https://accounts.google.com/DisplayUnlockCaptcha
I got “SMTP Error: 454 4.7.0 Too many login attempts, please try again later”. What I need to do?
Hi, did you try suggestions here?