This articles describes how to configure OpenLDAP client on Debian 9 Stretch. You can check our previous article on how to install and configure OpenLDAP Server on Debian 9 Stretch.
Install and Configure OpenLDAP Client on Debian 9 Stretch
Install the required packages.
apt -y install libnss-ldap libpam-ldap ldap-utils
Configure OpenLDAP client on Debian 9 Stretch
During the installation process, you will receive different configuration prompts.
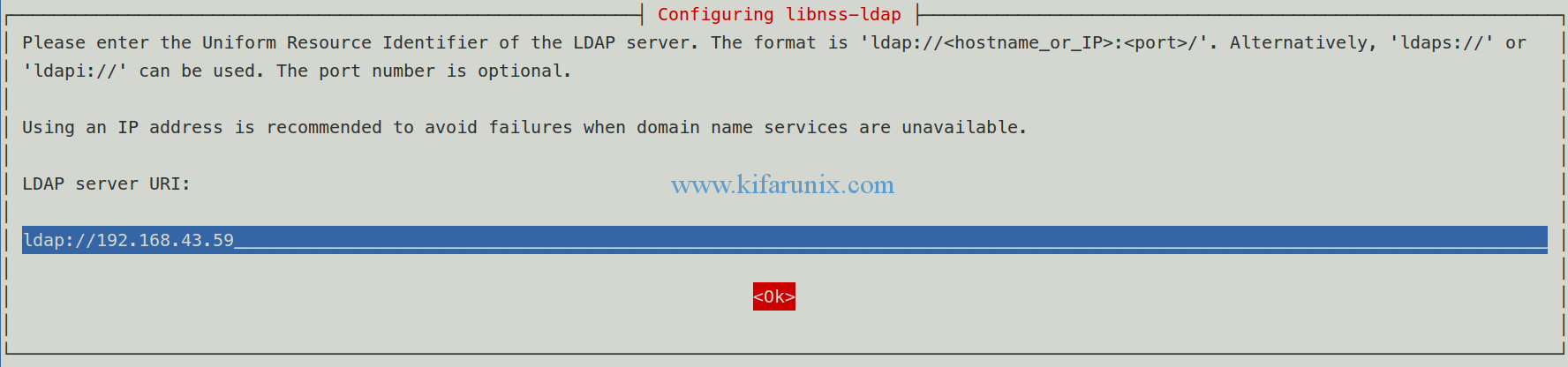
Define LDAP server’s URI.
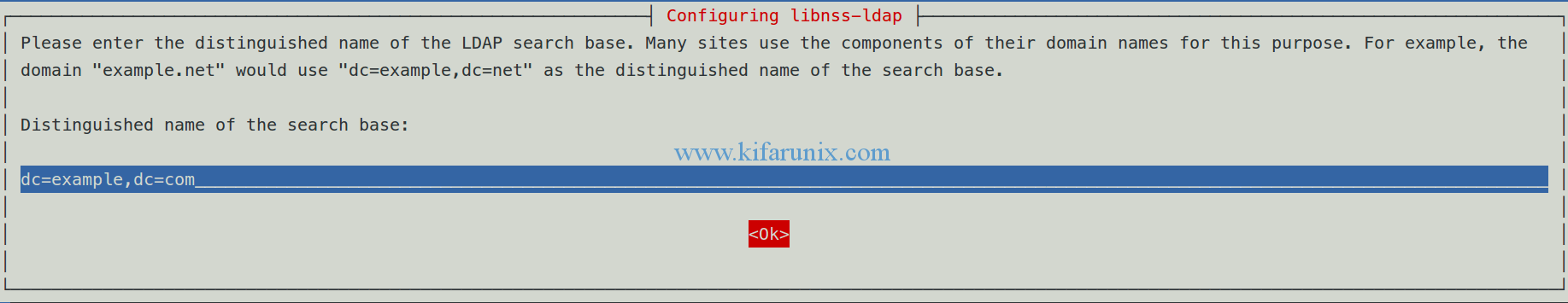
Set the distinguished name of the LDAP search base.
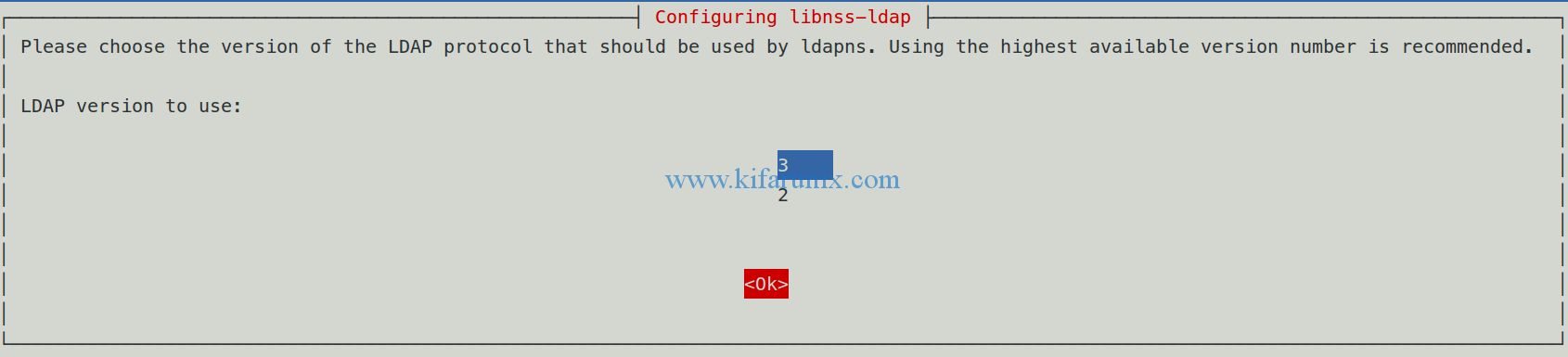
Specify LDAP protocol version.
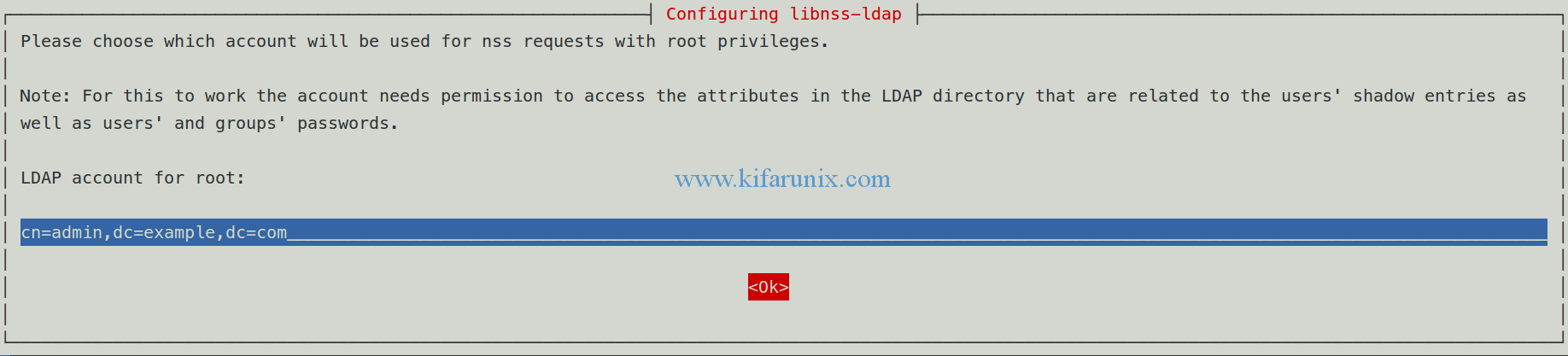
Set the LDAP administrator suffix.
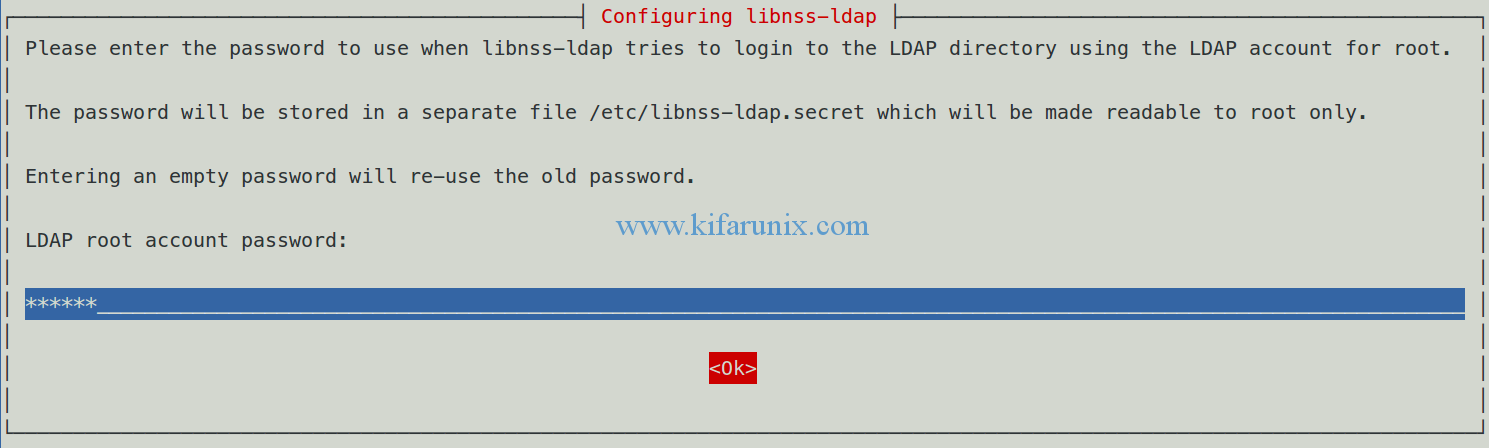
Enter the LDAP admin account password for libnss-ldap LDAP authentication.
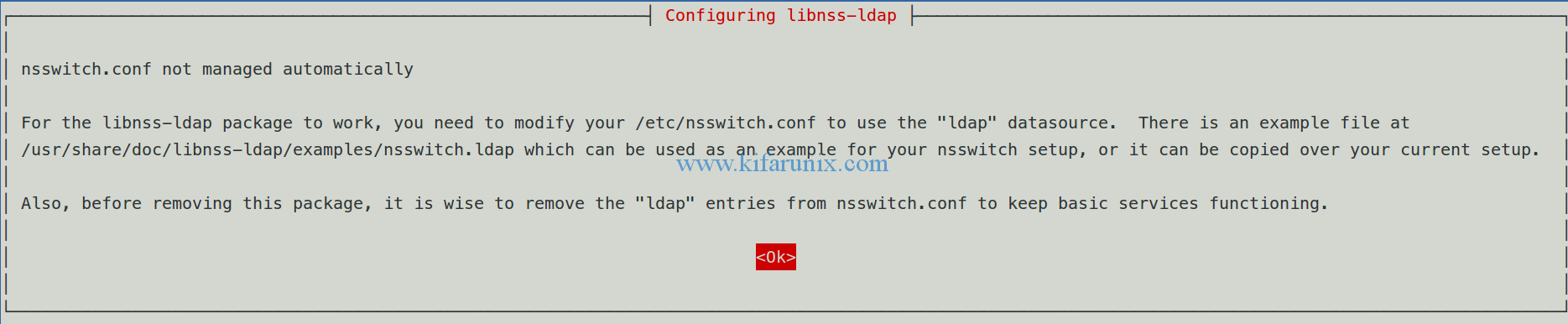
On nsswitch configuration, select Ok and press Enter to proceed. We will configure nsswitch later.
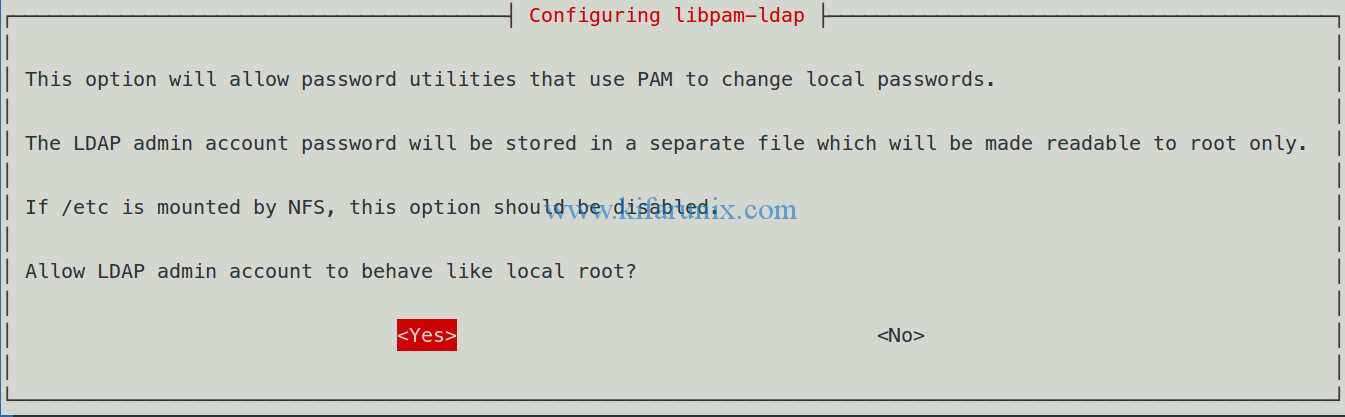
Allow LDAP admin account to assume local root behavior. This allows using the usual passwd command for changing passwords stored in the LDAP database.
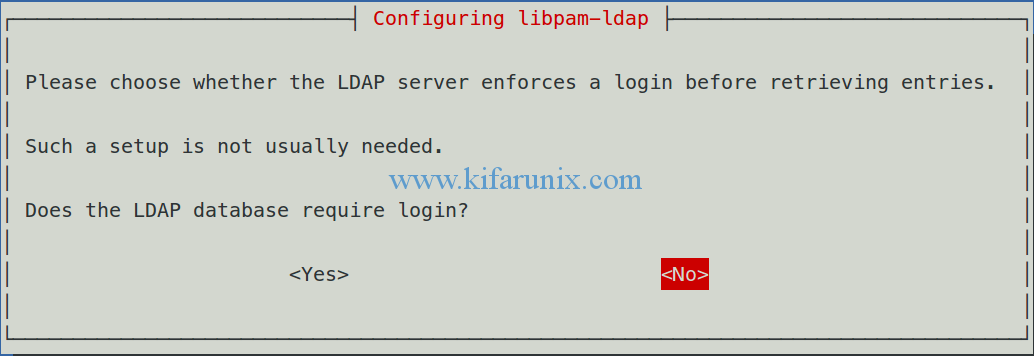
Disable LDAP database login requirement.
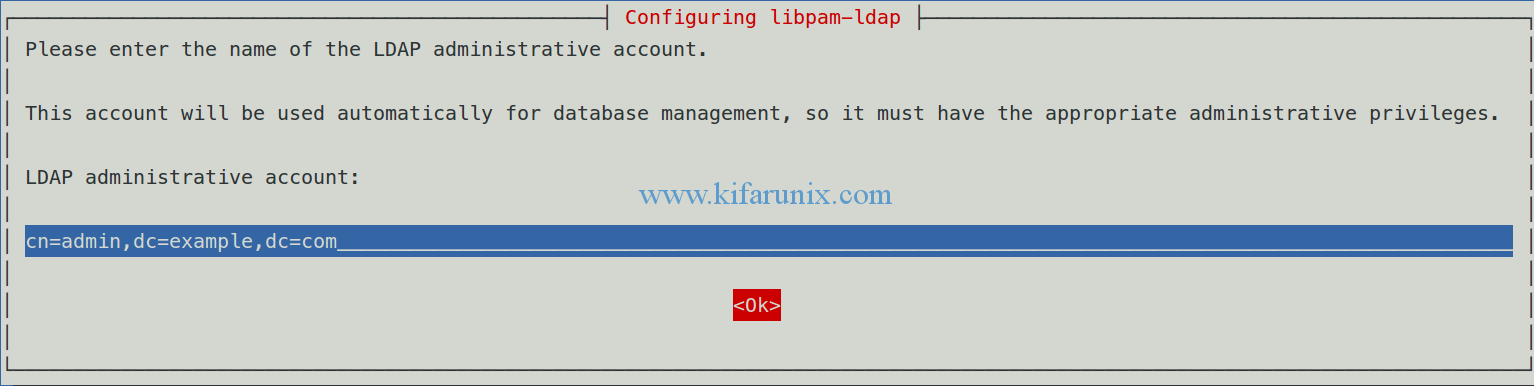
Enter LDAP administrator account suffix.
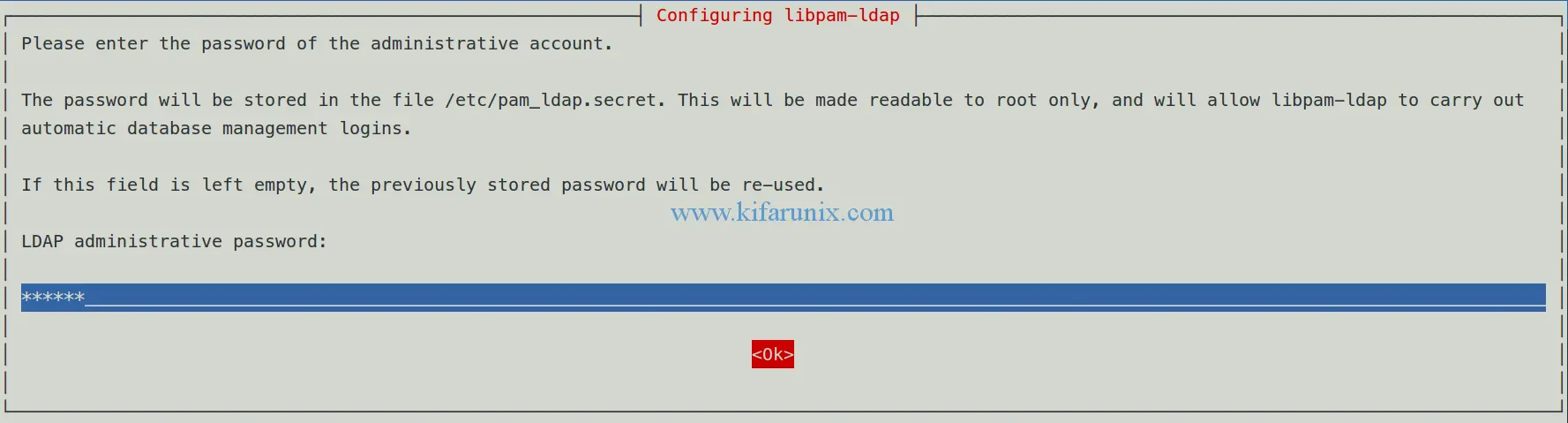
Set the LDAP administrator account password. Press Enter to complete installation and configuration.
Modify nsswitch.conf to use ldap datasource such that it looks like;.
vim /etc/nsswitch.conf
... passwd: compat ldap group: compat ldap shadow: compat ldap gshadow: files ...
Edit the /etc/pam.d/common-password and remove the use_authtok on the highlighted line below. use_authtok causes the PAM module to use the earlier provided password when changing the password..
vim /etc/pam.d/common-password
... # here are the per-package modules (the "Primary" block) password [success=2 default=ignore] pam_unix.so obscure sha512 password [success=1 user_unknown=ignore default=die] pam_ldap.so try_first_pass # here's the fallback if no module succeeds password requisite pam_deny.so # prime the stack with a positive return value if there isn't one already; ...
To enable automatic user home directory creation at first login, add the line session optional pam_mkhomedir.so skel=/etc/skel umask=077 to the /etc/pam.d/common-session between the pam_ldap.so and pam_systemd.so.
vim /etc/pam.d/common-session
# and here are more per-package modules (the "Additional" block) session required pam_unix.so session optional pam_ldap.so session optional pam_mkhomedir.so skel=/etc/skel umask=077 session optional pam_systemd.so # end of pam-auth-update config
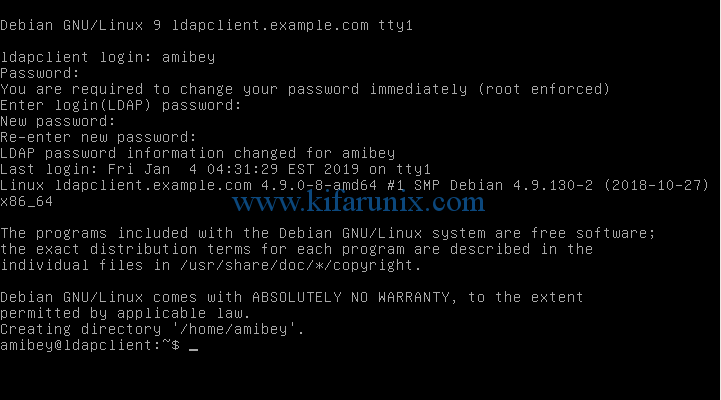
Reboot the LDAP client for the changes to take effect. After reboot, try logging in as an LDAP user. See screenshot below.
You have successfully authenticated to Debian 9 Strecth as an LDAP user.
That is all it takes configure OpenLDAP client on Debian 9 Stretch. In our next article, we will discuss how to configure LDAP client to use SSSD for LDAP authentication on Debian 9 stretch.


Hi there,
thank you for your post.
Do you know how to allow user to run `sudo` command without configure sssd?
thank you!
You can add the user sudo group, or to sudoers file.
You can as well configure LDAP to provide sudo, see the link;
How to Configure SUDO via OpenLDAP Server