Docker Hardened Images (DHI), launched on May 19, 2025, are revolutionizing software supply chain security as attacks are projected to cost businesses $60 billion in 2025, with breaches like SolarWinds (impacting 18,000 customers in 2020) and MOVEit (affecting over 620 organizations in 2023) exposing ongoing vulnerabilities [Cybersecurity Ventures, ZDNET, Dark Reading]. As a DevSecOps engineer with extensive experience tackling container risks, I know the struggle of securing fast-paced pipelines. DHI’s near-zero CVEs and 95% reduced attack surface offer a robust solution. In this post, I’ll explain what DHI are, why they’re critical, and how they secure applications with practical examples.
Table of Contents
Why Docker Hardened Images Are a Game-Changer for Software Supply Chain Security
What Are Docker Hardened Images?
Docker Hardened Images (DHI) are a curated catalog of enterprise-grade container images designed to minimize security risks. Built on trusted Linux distributions like Alpine and Debian, DHI images use a distroless approach, stripping away unnecessary components to reduce the attack surface by up to 95%. They run non-root by default, receive continuous updates to eliminate Common Vulnerabilities and Exposures (CVEs), and include cryptographically signed Software Bill of Materials (SBOMs) and Vulnerability Exploitability eXchange (VEX) statements for compliance. Available via Docker Hub, DHI integrates seamlessly into your workflows.
But what exactly are SBOM and VEX?
- Software Bill of Materials (SBOM):
- A detailed inventory listing all components, libraries, and dependencies in a software application or container image.
- It provides full visibility into what’s in your software, helping you identify vulnerabilities and comply with regulations like FedRAMP or SOC 2.
- DHI’s signed SBOMs ensure every component in the image is documented and verifiable, simplifying audits.
- Vulnerability Exploitability eXchange (VEX):
- VEX is a standardized report that clarifies whether known vulnerabilities in your software’s components are actually exploitable in your specific use case.
- It reduces false positives by prioritizing real threats, saving time on unnecessary patching.
- DHI’s VEX statements confirm which CVEs are relevant, streamlining security assessments.
Sample DHI hub;
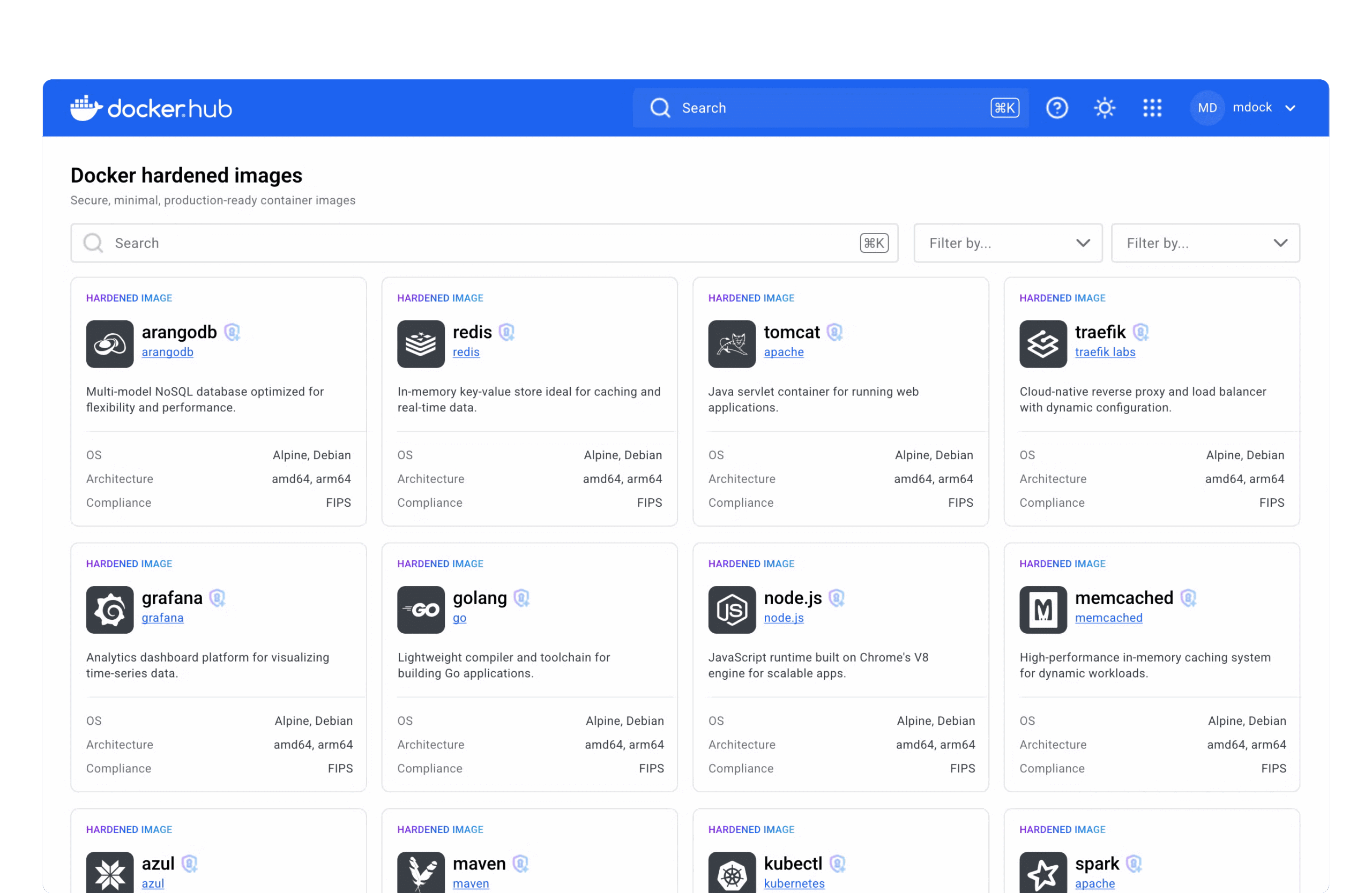
Why DHI Is a Game-Changer for Software Supply Chain Security
Containers are a prime target for attackers exploiting supply chain vulnerabilities. DHI addresses these risks with features that empower developers, platform engineers, and security teams. Here’s why they stand out:
1. Near-Zero CVEs for a Secure Foundation
DHI images are engineered to have near-zero CVEs by removing unnecessary libraries, minimizing the attack surface by up to 95%. Continuous updates ensure vulnerabilities are remediated quickly.
Assuming you are deploying a Node.js application, a standard Node.js image might include outdated dependencies with CVEs. Using a DHI Node.js image, you start with a lean, secure base, freeing you to code rather than patch.
2. Non-Root by Default to Limit Risks
Running containers as root risks catastrophic breaches. DHI images are non-root by default, preventing privilege escalation.
For example, an NGINX web server, a typical image might run as root, risking compromise. A DHI NGINX image runs as a non-root user, reducing the threat.
3. Compliance-Ready with Signed Artifacts
DHI complies with Supply Chain Levels for Software Artifacts (SLSA), ensuring verifiable build provenance. Signed SBOMs and VEX statements simplify audits for standards like FedRAMP or SOC 2.
During a compliance audit, DHI’s signed SBOMs detail every component, making it easy to prove your images are secure.
4. Seamless Workflow Integration
Available on Docker Hub, DHI images fit into existing tools. Developers use simple docker pull commands, while platform engineers enforce secure policies with Docker Scout.
A DevOps team running Kubernetes can restrict pulls to DHI images, ensuring secure deployments without disrupting workflows.
5. Backed by Industry Leaders
Docker’s partnerships with Microsoft, JFrog, Gitlab, Nginx and the rest, enhance DHI with advanced scanning and compliance tools, meeting enterprise needs.
Who Benefits from Docker Hardened Images?
DHI serves the entire software development lifecycle:
- Developers: Build faster with secure images.
- Platform Engineers: Enforce security policies at scale.
- Security Engineers: Access auditable artifacts.
- CISOs: Gain visibility into container dependencies.
How to Get Started with Docker Hardened Images
Docker Hardened Images are now available on Docker Hub, offering enhanced security and reliability for production environments.
However, there is currently no public access information, so you’ll need to contact Docker directly to request access by signing up.
Once you submit your request, the Docker team will review your request and reach out.
Conclusion: The Future of Container Security
Docker Hardened Images redefine container security, offering a trusted foundation for 2025’s threat landscape. With minimal design, non-root execution, and compliance-ready artifacts, DHI empowers teams to innovate safely. As a DevSecOps engineer, I see DHI as a must-have for organizations serious about software supply chain security.
Have you tried Docker Hardened Images? Share your thoughts in the comments or on X!
More Docker Tutorials:

