In this guide, we are going to learn how to configure HAProxy load balancer with SSL on Ubuntu 18.04/Debian 10/9. HAProxy is the de-factor opensource solution providing very fast and reliable high availability, load balancing and proxying for TCP and HTTP-based applications. As such, HAProxy is suited for very high traffic web sites.
Configure HAProxy Load Balancer with SSL on Ubuntu 18.04/Debian 10/9
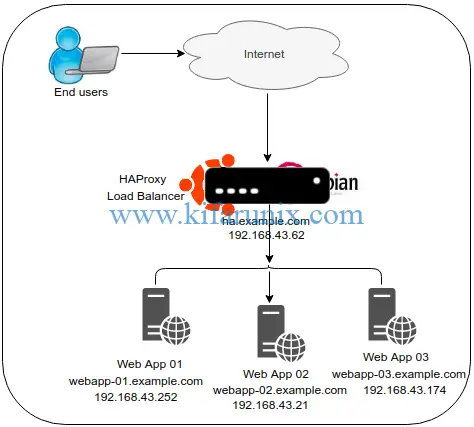
In this guide, we are going to demonstrate how HAProxy performs load balancing using three web servers serving simple html pages. Our architecture looks like in the diagram below;
Install HAProxy on Ubuntu 18.04/Debian 10/Debian 9
Run system update.
apt update
apt upgradeOnce the update is done, proceed to install HAProxy on your Ubuntu/Debian systems.
Create HAProxy Repository
There are different HAProxy packages for each system. Hence, you need to create dedicated repository for each system.
Before you can create the repos, install the APT signing Key.
apt install curl -y
curl https://haproxy.debian.net/bernat.debian.org.gpg | apt-key add -Next, create HAProxy repositories. On Debian 10 Buster/Debian 9 Stretch, run the command below to create the repo.
echo "deb http://haproxy.debian.net $(lsb_release -cs)-backports-2.0 main" | tee /etc/apt/sources.list.d/haproxy.listOn Ubuntu 18.04, you need to add the vbernat haproxy PPA repos as shown below;
apt install software-properties-common
add-apt-repository ppa:vbernat/haproxy-2.0Once the repos are created on each system, perform system update and install HAProxy.
apt update
apt install haproxy=2.0.\*To check the version of installed HAProxy, run the command below;
haproxy -vHA-Proxy version 2.0.1-1~bpo9+1 2019/06/27 - https://haproxy.org/Configure HAProxy Load Balancer on Ubuntu 18.04/Debian 10/9
Configuration of HAProxy is all about where it is listening for connection requests and where to forward such requests to. It is therefore made up of frontend system and one or more back-end systems. The front-end system defines the IP address and port on which the proxy listens as well as the back-end systems to use for a particular proxy.
The main configuration file for HAProxy is /etc/haproxy/haproxy.cfg.
The HAProxy configuration file is made up of four sections;
global
The global section defines process-wide security and performance tunings that affect HAProxy at a low level.defaults
The global section defines the configuration settings that are applied to all of thefrontendandbackendsections. You can define multiple default sections but the sub-sequent defaults sections override that came before it.frontend
When HAProxy is placed as a reverse proxy, thefrontendsection defines the IP addresses and ports that clients can connect to.backend
The backend section defines the group of servers that will be load balanced and assigned to handle requests.
The frontend and backend sections can be combined using the listen section. It can also be used to server HAProxy statistics page.
To read more on the explanation of HAProxy configuration sections, check here.
Before we can begin any configuration, let us create a backup of the configuration file.
cp /etc/haproxy/haproxy.cfg{,.bak}The default HAProxy configuration contain the default configuration settings for the global and default section.
global
log /dev/log local0
log /dev/log local1 notice
chroot /var/lib/haproxy
stats socket /run/haproxy/admin.sock mode 660 level admin expose-fd listeners
stats timeout 30s
user haproxy
group haproxy
daemon
# Default SSL material locations
ca-base /etc/ssl/certs
crt-base /etc/ssl/private
# Default ciphers to use on SSL-enabled listening sockets.
# For more information, see ciphers(1SSL). This list is from:
# https://hynek.me/articles/hardening-your-web-servers-ssl-ciphers/
# An alternative list with additional directives can be obtained from
# https://mozilla.github.io/server-side-tls/ssl-config-generator/?server=haproxy
ssl-default-bind-ciphers ECDH+AESGCM:DH+AESGCM:ECDH+AES256:DH+AES256:ECDH+AES128:DH+AES:RSA+AESGCM:RSA+AES:!aNULL:!MD5:!DSS
ssl-default-bind-options no-sslv3
## Add the line below
tune.ssl.default-dh-param 2048
defaults
log global
mode http
option httplog
option dontlognull
timeout connect 5000
timeout client 50000
timeout client 50000
timeout server 50000
errorfile 400 /etc/haproxy/errors/400.http
errorfile 403 /etc/haproxy/errors/403.http
errorfile 408 /etc/haproxy/errors/408.http
errorfile 500 /etc/haproxy/errors/500.http
errorfile 502 /etc/haproxy/errors/502.http
errorfile 503 /etc/haproxy/errors/503.http
errorfile 504 /etc/haproxy/errors/504.httpWe are going to leave this settings just the way they are and add the our configurations for the frontend and backend sections. However, you can add the line tune.ssl.default-dh-param 2048 to the global section which sets the maximum size of the Diffie-Hellman parameters used for generating the ephemeral/temporary Diffie-Hellman key in case of DHE key exchange.
Configure HAProxy with SSL on Ubuntu 18.04/Debian 10/9
As stated above, frontend section defines the IP address on which to listen for connection requests.
Since we are configuring HAProxy with SSL, you need to generate the SSL/TLS certificates. This guide uses self-signed certificates. You can get your own from a trusted CA.
Generating Self-Signed SSL Certificates for HAProxy
Begin with generating private key.
openssl genrsa -out /etc/ssl/private/haproxy.key 2048Next, generate the Certificate signing request (CSR).
openssl req -new -key /etc/ssl/private/haproxy.key -out /etc/ssl/certs/haproxy.csrCreate the Self Signed Certificate (CRT)
openssl x509 -req -days 365 -in /etc/ssl/certs/haproxy.csr -signkey /etc/ssl/private/haproxy.key -out /etc/ssl/certs/haproxy.crtCreate SSL pem file by containing both the key and the certificate.
cat /etc/ssl/private/haproxy.key /etc/ssl/certs/haproxy.crt >> /etc/ssl/certs/haproxy.pemDefine HAProxy Frontend Configuration Settings
Open the HAProxy configuration file and configure the frontend settings as shown below;
vim /etc/haproxy/haproxy.cfgThis is our frontend configuration basic settings.
frontend lb_01
bind 192.168.43.62:443 ssl crt /etc/ssl/certs/haproxy.pem
default_backend webapp_backends- bind setting assigns a listener to a given IP address and port. ssl crt instructs HAProxy to use SSL.
default_backendgives the name of abackendto send traffic to.
Define HAProxy Backend Configuration Settings
In its basic configuration, out backend settings are defined below;
backend webapp_backends
balance roundrobin
server webapp_01.example.com 192.168.43.252:80 check
server webapp_02.example.com 192.168.43.174:80 check
server webapp_03.example.com 192.168.43.21:80 check- balance setting defines the load balancer scheduling algorithm.
- roundrobin selects the servers in turns.
- Other common algorithms is leastconn which enabled the load balancer to forward request to servers with least connections.
- server setting specify the servers available in the back end.
- check option enables health checks on the server such that if one of them is down, requests are directed to the available backend servers.
Enable HAProxy Statistics via Web
listen stats
bind 192.168.43.62:443 ssl crt /etc/ssl/certs/haproxy.pem
stats enable # enable statistics reports
stats hide-version # Hide the version of HAProxy
stats refresh 30s # HAProxy refresh time
stats show-node # Shows the hostname of the node
stats auth admin:P@ssword # Authentication for Stats page
stats uri /lb_stats # Statistics URLVerify HAProxy Configuration
Once the configuration is done, you can run the command below to check the HAProxy configuration for any error.
haproxy -c -f /etc/haproxy/haproxy.cfgConfiguration file is validRunning HAProxy
When installed, HAProxy is set to run by default. To restart and enable HAProxy to run on system boot;
systemctl restart haproxy
systemctl enable haproxyTo check the status;
systemctl status haproxy
● haproxy.service - HAProxy Load Balancer
Loaded: loaded (/lib/systemd/system/haproxy.service; enabled; vendor preset: enabled)
Active: active (running) since Fri 2019-07-12 23:22:58 EAT; 5s ago
Docs: man:haproxy(1)
file:/usr/share/doc/haproxy/configuration.txt.gz
Process: 10686 ExecStartPre=/usr/sbin/haproxy -f $CONFIG -c -q $EXTRAOPTS (code=exited, status=0/SUCCESS)
Main PID: 10687 (haproxy)
Tasks: 2 (limit: 2340)
CGroup: /system.slice/haproxy.service
├─10687 /usr/sbin/haproxy -Ws -f /etc/haproxy/haproxy.cfg -p /run/haproxy.pid -S /run/haproxy-master.sock
└─10688 /usr/sbin/haproxy -Ws -f /etc/haproxy/haproxy.cfg -p /run/haproxy.pid -S /run/haproxy-master.sockIf UFW is running, Open port 443,
ufw allow 443Verify HAProxy Load Balancing
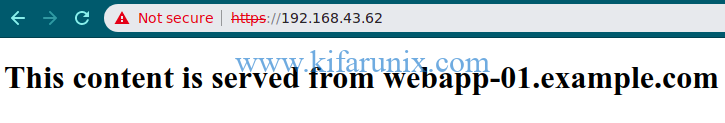
Now that the configuration is done, you can access your HAProxy from web to see if it performs any round-robin load balancing using the address, https://<haproxy-IP>.
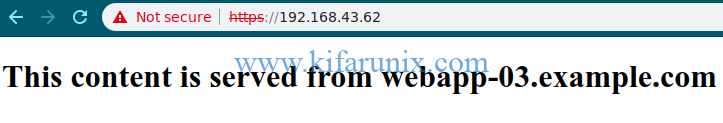
The first page the loads shows content server from webapp_01. For this demo, we have three test html pages. When refreshed, content from other servers is shown.
Well, as you can realize, the pages are served in order, one after the other. That is it on our basic tutorial on how to configure HAProxy Load Balancer with Self-Signed certificate on Ubuntu 18.04/Debian 10/Debian 9.
You can read more about HAProxy and configuration options in the documentation page below;
Related Tutorials
Install and Setup HAProxy on Ubuntu 20.04
Setup HAProxy Load Balancer on Fedora 30/Fedora 29
How to Install and Configure Pound as Apache HTTP Load balancer on Ubuntu 16.04