In this tutorial, you will learn how to send alert when ClamAV finds infected files on Linux systems. ClamAV is an opensource antivirus engine for detecting trojans, viruses, malware & other malicious threats. It is a good idea to sent alerts whenever a malicious file is detected on the system. This enables you to take actions of analyzing the files and probably removing them from the system based on the results of the analysis.
Send Alert When ClamAV Finds Infected Files on Linux Systems
In our previous guides on ClamAV, we learnt how to perform only one time scanning of the systems using ClamAV clamscan command line tool.
We have also seen how to configure ClamAV to send scan events to ELK Stack Kibana for visualization.
In this setup, therefore, we will configure ELK stack to sent alerts using ElastAlert to analysts or system admins via the email whenever it receives events from ClamAV with evidence of infected files found on the systems rather than sending emails directly from the system where ClamAV is installed.
Send ClamAV Alerts using ElastAlert
To proceed with this kind of alerting, you need to have already setup ELK stack and already processing ClamAV events well. Check the guide below on how to configure ClamAV to send scan events to ELK Stack Kibana for visualization.
Visualize ClamAV Scan Logs on ELK Stack Kibana
Next, install ElastAlert on ELK Stack. You can check our previous guide on how to install ElastAlert.
If you are have Python 3.9, install ElastAlert2;
pip install elastalert2Configure your system to be able to send emails. You can consult our tutorials on using Postfix with Gmail SMTP.
Install and Configure Postfix Gmail SMTP relay
Assuming you already installed ElastAlert, it is then time to configure it to send ClamAV alerts whenever an infected file is found on the scan report.
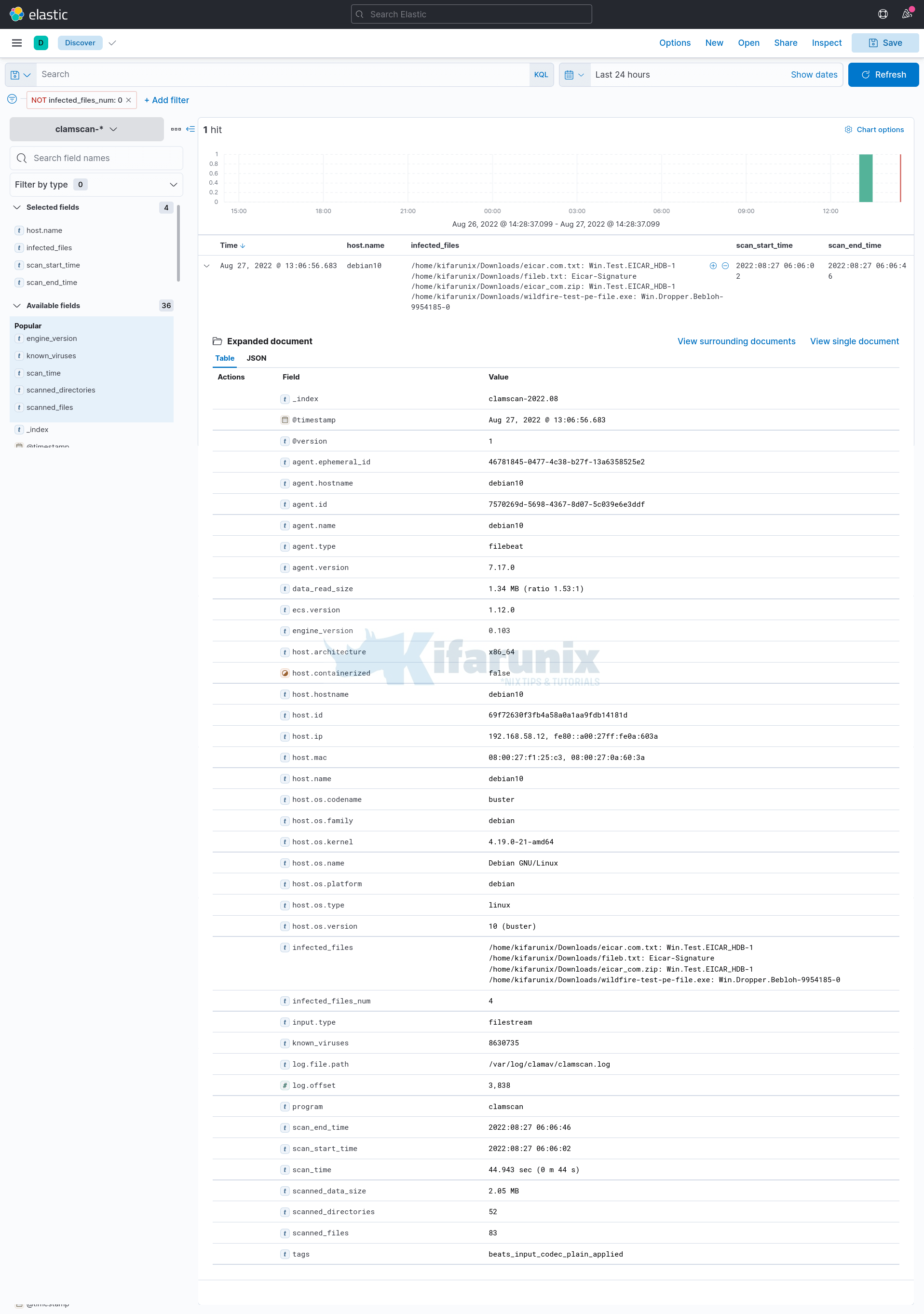
Remember in our guide on how to visualize ClamAV alerts on ELK, one could filter ClamAV events with infected files using the filter;
infected_files_num is not 0Or
infected_files: existsDetails for the infected files found event;
Based on the fields available above, we will configure ElastAlert to send an email alert when a match is found.
Make a copy of the ElastAlert configuration file and update it for ClamAV alerts. This is our sample configuration
cp /opt/elastalert/{config,-clamav}.yamlIf you installed via PIP, you can download example configuration file and rules from Github repository.
vim /opt/elastalert/config-clamav.yamlrules_folder: example_rules
run_every:
minutes: 5
buffer_time:
minutes: 15
es_host: 192.168.58.22
es_port: 9200
writeback_index: elastalert_status
writeback_alias: elastalert_alerts
alert_time_limit:
days: 2
rules_folderis where ElastAlert will load rule configuration files from, which in our case is/opt/elastalert/example_rules.run_everyis how often ElastAlert will query Elasticsearch index for the events specified in the alert.buffer_timeis the size of the query window, stretching backwards from the time each query is run.es_hostis the address of an Elasticsearch cluster where ElastAlert will store data about its state, queries run, alerts, and errors. Each rule may also use a different Elasticsearch host to query against.es_portis the port corresponding toes_host.writeback_indexis the name of the index in which ElastAlert will store data. We will create this index later.alert_time_limitis the retry window for failed alerts.
ClamAV ElastAlert Rules file;
vim /opt/elastalert/example_rules/clamav-alert.yamlname: ClamAV Infected Files Report
type: frequency
num_events: 1
timeframe:
minutes: 1
filter:
- query:
query_string:
query: "infected_files: * AND NOT infected_files_num: 0"
index: "clamscan-*"
realert:
minutes: 5
query_key:
- host.name
include:
- host.name
- infected_files
- scan_start_time
- scan_end_time
- scan_time
- known_viruses
- engine_version
- scanned_directories
- scanned_files
- scanned_data_size
include_match_in_root: true
alert_subject_args:
- host.name
alert_subject: "ClamAV Scan Report for {}"
alert_text_args:
- host.name
- infected_files
- scan_start_time
- scan_end_time
- scan_time
- known_viruses
- engine_version
- scanned_directories
- scanned_files
- scanned_data_size
alert_text: |-
Kindly find the ClamAV Scan report for {}
Details of the event:
- Infected Files: {}
- Scan Start Time: {}
- Scan End Time: {}
- Scan Time: {}
- Known Viruses: {}
- Scanner Engine Version: {}
- Scanned Directories: {}
- Scanned Files: {}
- Scanned Data Size: {}
alert:
- email:
from_addr: "[email protected]"
email: "[email protected]"
alert_text_type: alert_text_only
Consult ElastAlert documentation for more information on the configuration options used.
Save and exit your rule.
Run rule test to confirm if all good.
elastalert-test-rule --config /opt/elastalert/config-clamav.yaml /opt/elastalert/example_rules/clamav-alert.yamlINFO:elastalert:Note: In debug mode, alerts will be logged to console but NOT actually sent.
To send them but remain verbose, use --verbose instead.
Got 421 hits from the last 0 day
Available terms in first hit:
@version
data_read_size
log.file.path
log.offset
scanned_directories
program
tags
known_viruses
scanned_files
engine_version
scanned_data_size
scan_start_time
host.ip
host.name
host.architecture
host.os.type
host.os.name
host.os.platform
host.os.kernel
host.os.codename
host.os.version
host.os.family
host.id
host.containerized
host.hostname
host.mac
infected_files
ecs.version
input.type
scan_end_time
@timestamp
infected_files_num
scan_time
agent.type
agent.name
agent.id
agent.version
agent.hostname
agent.ephemeral_id
INFO:elastalert:Note: In debug mode, alerts will be logged to console but NOT actually sent.
To send them but remain verbose, use --verbose instead.
INFO:elastalert:1 rules loaded
INFO:apscheduler.scheduler:Adding job tentatively -- it will be properly scheduled when the scheduler starts
INFO:elastalert:Queried rule ClamAV Infected Files Report from 2022-08-28 08:56 EAT to 2022-08-28 08:57 EAT: 1 / 1 hits
INFO:elastalert:Alert for ClamAV Infected Files Report at 2022-08-28T05:56:55.056Z:
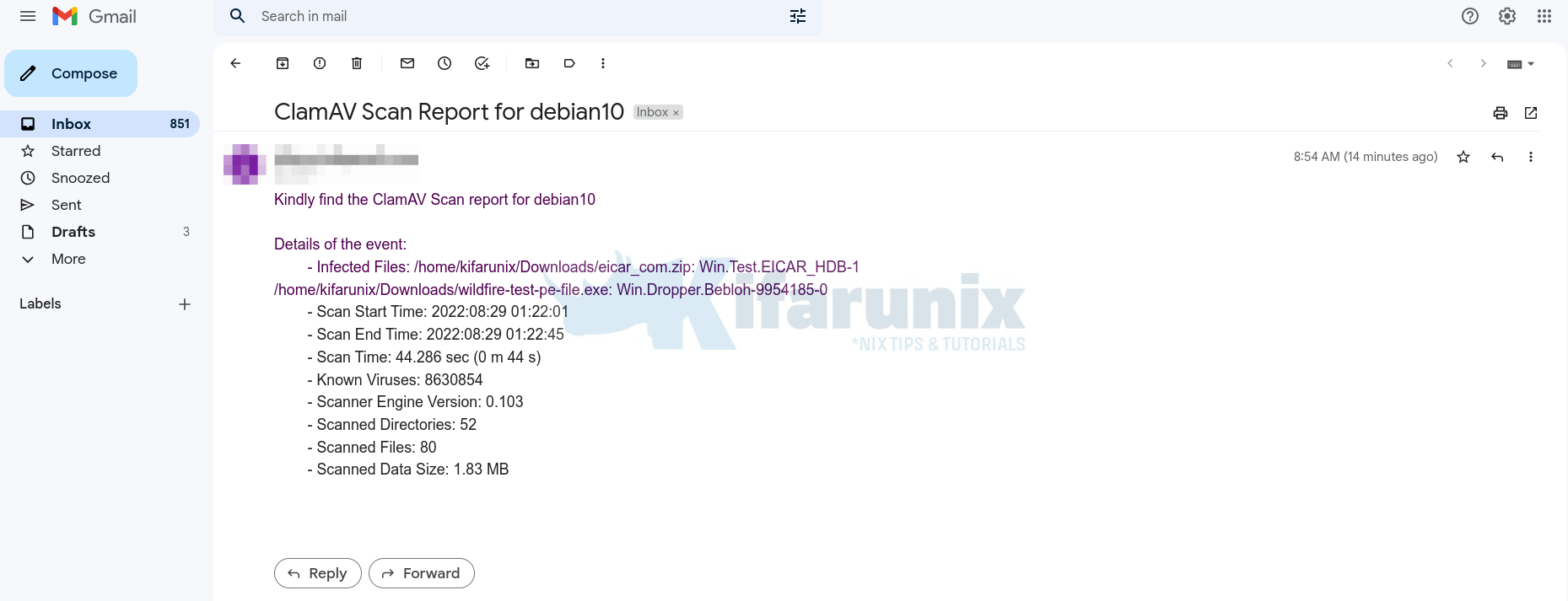
INFO:elastalert:Kindly find the ClamAV Scan report for debian10
Details of the event:
- Infected Files: /home/kifarunix/Downloads/eicar_com.zip: Win.Test.EICAR_HDB-1
/home/kifarunix/Downloads/wildfire-test-pe-file.exe: Win.Dropper.Bebloh-9954185-0
- Scan Start Time: 2022:08:29 01:56:01
- Scan End Time: 2022:08:29 01:56:45
- Scan Time: 43.965 sec (0 m 43 s)
- Known Viruses: 8630854
- Scanner Engine Version: 0.103.6
- Scanned Directories: 52
- Scanned Files: 80
- Scanned Data Size: 1.83 MB
Would have written the following documents to writeback index (default is elastalert_status):
silence - {'exponent': 0, 'rule_name': 'ClamAV Infected Files Report.debian10', '@timestamp': datetime.datetime(2022, 8, 29, 5, 57, 1, 990643, tzinfo=tzutc()), 'until': datetime.datetime(2022, 8, 29, 6, 2, 1, 990633, tzinfo=tzutc())}
elastalert_status - {'rule_name': 'ClamAV Infected Files Report', 'endtime': datetime.datetime(2022, 8, 29, 5, 57, 1, 146070, tzinfo=tzutc()), 'starttime': datetime.datetime(2022, 8, 29, 5, 56, 0, 546070, tzinfo=tzutc()), 'matches': 1, 'hits': 1, '@timestamp': datetime.datetime(2022, 8, 29, 5, 57, 1, 991196, tzinfo=tzutc()), 'time_taken': 0.008098840713500977}
Running ElastAlert
Once you have confirmed that your query is working fine, it is time to run ElastAlert.
ElastAlert can be run as a daemon via supervisord or via Python.
You can as well run it on standard output using the elastalert binary, /usr/local/bin/elastalert.
For example, you run ElastAlert against all rules defined in the rules directory;
/usr/local/bin/elastalert --verbose --config /opt/elastalert/config.yamlTo specify a specific configuration and rules file, for example;
/usr/local/bin/elastalert --verbose --config /opt/elastalert/config-clamav.yaml --rule /opt/elastalert/example_rules/clamav-alert.yamlSample output;
INFO:elastalert:1 rules loaded
INFO:elastalert:Starting up
INFO:elastalert:Disabled rules are: []
INFO:elastalert:Sleeping for 299.999937 seconds
INFO:elastalert:Queried rule ClamAV Infected Files Report from 2022-08-28 08:21 EAT to 2022-08-28 08:36 EAT: 1 / 1 hits
INFO:elastalert:Queried rule ClamAV Infected Files Report from 2022-08-28 08:36 EAT to 2022-08-28 08:51 EAT: 0 / 0 hits
INFO:elastalert:Queried rule ClamAV Infected Files Report from 2022-08-28 08:51 EAT to 2022-08-28 08:54 EAT: 0 / 0 hits
INFO:elastalert:Sent email to ['[email protected]']
INFO:elastalert:Ran ClamAV Infected Files Report from 2022-08-28 08:21 EAT to 2022-08-28 08:54 EAT: 0 query hits (0 already seen), 1 matches, 1 alerts sent
INFO:elastalert:ClamAV Infected Files Report range 1959
As you can see, an alert has been sent out.
Sample receipt;
Run ElastAlert as a systemd service
In our previous guide, you can check how to configure ElastAlert for specific alerting to run as a system service.
Run ElastAlert as systemd service
And that concludes our guide on how to alert when ClamAV finds infected files on Linux Systems.