In this tutorial, you will learn how to intercept malicious file upload with ModSecurity and ClamAV.
ModSecurity, currently known as libModSecurity or ModSecurity version 3 is
an open source, cross-platform web application firewall (WAF) module developed by Trustwave’s SpiderLabs. Known as the “Swiss Army Knife” of WAFs, it enables web application defenders to gain visibility into HTTP(S) traffic and provides a power rules language and API to implement advanced protections.
It has a robust event-based programming language which provides protection from a range of attacks against web applications and allows for HTTP traffic monitoring, logging and real-time analysis.
What Can ModSecurity Do?
- Intercepts, stores, and optionally validates uploaded files
- Real-time application security monitoring and access control
- Full HTTP traffic logging
- Continuous passive security assessment
- Web application hardening
- Due to its ability to parse XML and apply XPath expressions with its ability to proxy requests, it can be used as an XML web service router.
- HTTP Protocol Protection
- Real-time Blacklist Lookups
- HTTP Denial of Service Protections
- Generic Web Attack Protection
- Error Detection and Hiding
ClamAV on the other hand is an open source antivirus engine for detecting trojans, viruses, malware & other malicious threats.
Using ModSecurity and ClamAV to Intercep Malicious File Upload
ModSecurity has the ability to understand the multipart/form-data encoding which is used for file uploads. This enables ModSecurity to extract the uploaded files from the request and store on a specified file system location.
Apart from the ability to extract uploaded files, ModSecurity can as well, with integration with other tools such ClamAV, validate the uploaded files.
ClamAV provides scripts that can be used to scan the file to detect trojans, viruses, malware & other malicious threats.
Follow the links below to install ModSecurity and ClamAV;
Install and Configure ModSecurity
Install and Configure ModSecurity with Apache on Ubuntu
Configure LibModsecurity with Apache on CentOS
Install and Configure ClamAV
Install and use ClamAV on Ubuntu
You can find how to install and setup ClamAV on other Linux distros.
Note: We run our tests on an Ubuntu 20.04 system.
Create ModSecurity-ClamAV File Validation Script
To enable file upload validation using ModSecurity, you need to create a perl script that uses ClamAV command line anti-virus scanner, clamscan, to extract the full path of the file being uploaded and scan for any malicious threat.
In this tutorial, we will place our scanner script on the /etc/apache2/modsecurity.d/ directory. This is however, not a standard location and you can place it anywhere on your system.
Paste the content below to create a ClamAV scanner script, /etc/apache2/modsecurity.d/modsec_clamav.pl. You can as well choose any name for your script.
cat > /etc/apache2/modsecurity.d/modsec_clamav.pl << 'EOL'
#!/usr/bin/perl
$CLAMSCAN = "/usr/bin/clamscan";
if (@ARGV != 1) {
print "Usage: modsec_clamav.pl <filename>\n";
exit;
}
my ($FILE) = @ARGV;
$cmd = "$CLAMSCAN --stdout --disable-summary $FILE";
$input = `$cmd`;
$input =~ m/^(.+)/;
$error_message = $1;
$output = "0 Unable to parse clamscan output";
if ($error_message =~ m/: Empty file\.$/) {
$output = "1 empty file";
}
elsif ($error_message =~ m/: (.+) ERROR$/) {
$output = "0 clamscan: $1";
}
elsif ($error_message =~ m/: (.+) FOUND$/) {
$output = "0 clamscan: $1";
}
elsif ($error_message =~ m/: OK$/) {
$output = "1 clamscan: OK";
}
print "$output\n";
EOLMake the script executable;
chmod +x /etc/apache2/modsecurity.d/modsec_clamav.plCreate ModSecurity Rule to Intercept File Upload
Next, you need to create a custom ModSecurity rule to intercept file upload.
In our setup, we have specified the location of ModSecurity rules file in our Apache site configuration file as, /etc/apache2/modsecurity.d/modsec_rules.conf.
See below;
less /etc/apache2/sites-available/wordpress.conf<VirtualHost *:80>
ServerAdmin [email protected]
ServerName wp.kifarunix-demo.com
DocumentRoot /var/www/html/wp.kifarunix-demo.com
modsecurity on
modsecurity_rules_file /etc/apache2/modsecurity.d/modsec_rules.conf
<Directory /var/www/html/wp.kifarunix-demo.com>
AllowOverride All
</Directory>
ErrorLog /var/log/apache2/wp.error.log
CustomLog /var/log/apache2/wp.access.log combined
</VirtualHost>Below are the contents of the ModSecurity rules file;
less /etc/apache2/modsecurity.d/modsec_rules.confInclude "/etc/apache2/modsecurity.d/modsecurity.conf"
Include "/etc/apache2/modsecurity.d/owasp-crs/crs-setup.conf"
Include "/etc/apache2/modsecurity.d/owasp-crs/rules/*.conf"Therefore, create a custom file scannner/validation rule for ModSecurity. ModSecurity rules are defined using the SecRule directive.
The syntax of a rule is;
SecRule VARIABLES "OPERATOR" "TRANSFORMATIONS,ACTIONS"In this setup, we name our custom rules file as /etc/apache2/modsecurity.d/modsec_clamav.conf.
Below is the rule configuration;
cat /etc/apache2/modsecurity.d/modsec_clamav.confSecRule FILES_TMPNAMES "@inspectFile /etc/apache2/modsecurity.d/modsec_clamav.pl" \
"id:'400001', \
phase:2, \
t:none, \
deny, \
log, \
msg:'Infected File upload detected', \
tag:'MALICIOUS_SOFTWARE/VIRUS'"Next, include the rule in the rules file.
echo 'Include "/etc/apache2/modsecurity.d/modsec_clamav.conf"' >> /etc/apache2/modsecurity.d/modsec_rules.confYour rules file now looks like;
less /etc/apache2/modsecurity.d/modsec_rules.confInclude "/etc/apache2/modsecurity.d/modsecurity.conf"
Include "/etc/apache2/modsecurity.d/owasp-crs/crs-setup.conf"
Include "/etc/apache2/modsecurity.d/owasp-crs/rules/*.conf"
Include "/etc/apache2/modsecurity.d/modsec_clamav.conf"Check Apache configuration syntax;
apachectl configtestIf you get Syntax OK, then proceed to restart/reload Apache;
systemctl restart apache2Testing the Interception of Malicious File Upload with ModSecurity and ClamAV
If you have test environment, you can download test malicious files from Eicar and try to upload to your site.
While you upload, be sure to tail both Apache error log and ModSecurity audit log files.
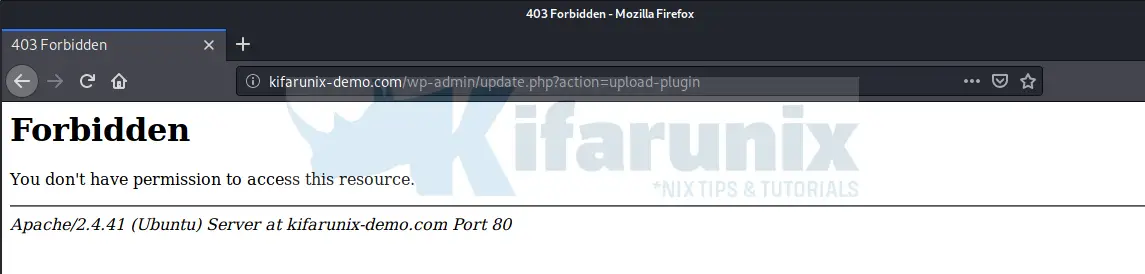
For example, in the screenshot below, I tried to upload the eicar_com.zip on my WordPress and this is the result;
And the ModSecurity audit logs;
tail -f /var/log/modsec_audit.log---i6mkrLhp---H--
ModSecurity: Access denied with code 403 (phase 2). Matched "Operator `InspectFile' with parameter `/etc/apache2/modsecurity.d/modsec_clamav.pl' against variable `FILES_TMPNAMES:' (Value: `' ) [file "/etc/apache2/modsecurity.d/modsec_clamav.conf"] [line "1"] [id "400001"] [rev ""] [msg "Infected File upload detected"] [data ""] [severity "0"] [ver ""] [maturity "0"] [accuracy "0"] [tag "MALICIOUS_SOFTWARE/VIRUS"] [hostname "wp.kifarunix-demo.com"] [uri "/wp-admin/update.php"] [unique_id "161558337389.815242"] [ref "v1369,0"]
---i6mkrLhp---I--
---i6mkrLhp---J--
---i6mkrLhp---Z--And that is it!
Useful Links
ModSecurity v2 Reference Manual
Other Related Tutorials
Restrict Access to WordPress Login Page to Specific IPs with libModSecurity
Create Kibana Visualization Dashboards for ModSecurity Logs


Thank you for the article, I find it very interesant. I wonder, if its works for incercept any file type, for example: Allow only files with extention “.pdf” and deny others.
I tried with match files and don’t work, because I use proxypass to the backend, there is, run an app type, that load the files throught a type of Iframe.
How will I do it?