Follow through this tutorial to learn how to install Fleet osquery manager on Oracle Linux. “Fleet is the most widely used open source osquery manager. Deploying osquery with Fleet enables programmable live queries, streaming logs, and effective management of osquery across 50,000+ servers, containers, and laptops. It’s especially useful for talking to multiple devices at the same time.“
If you are using Ubuntu, you can use the guide below;
Install Fleet Osquery Manager on Ubuntu 20.04/Ubuntu 22.04
Install Fleet Osquery Manager on Oracle Linux
Install MySQL Database
Fleet uses MySQL as its main database. Thus, to install MySQL on Oracle Linux, run the commands below;
dnf install mysql-serverOnce the installation is done, start and enable MySQL to run on system boot;
systemctl enable --now mysqldCreate Fleet Database and Database User
Run the initial MySQL security script, mysql_secure_installation, to remove anonymous database users, test tables, disable remote root login.
mysql_secure_installationBy default, root@localhost is created with an empty password. You can login by just running, mysql -u root or mysql or mysql -u root -p and press ENTER.
mysql -u root -pNext, create the Fleet database.
Note: the database database names used here are not standard. Choose any name of your preference.
create database fleetdb;Create Fleet database user with all grants on Fleet DB created above.
create user fleetadmin@localhost identified by 'StrongP@SS';grant all on fleetdb.* to fleetadmin@localhost;Reload privileges tables and exit the database;
flush privileges;
exitInstall Redis on Oracle Linux
Fleet uses Redis to ingest and queue the results of distributed queries, cache data, etc.
Install Redis on Oracle Linux by running the command below;
dnf install redisStart and enable Redis to run on system boot;
systemctl enable --now redisCheck the status;
systemctl status redis
● redis.service - Redis persistent key-value database
Loaded: loaded (/usr/lib/systemd/system/redis.service; enabled; vendor preset: disabled)
Drop-In: /etc/systemd/system/redis.service.d
└─limit.conf
Active: active (running) since Tue 2022-09-27 08:46:51 EAT; 6s ago
Main PID: 28798 (redis-server)
Status: "Ready to accept connections"
Tasks: 5 (limit: 5832)
Memory: 7.3M
CPU: 20ms
CGroup: /system.slice/redis.service
└─28798 "/usr/bin/redis-server 127.0.0.1:6379"
Sep 27 08:46:51 localhost.localdomain systemd[1]: Starting Redis persistent key-value database...
Sep 27 08:46:51 localhost.localdomain systemd[1]: Started Redis persistent key-value database.
Install Fleet Osquery Manager
The Fleet application is distributed as a single static binary. This binary serves:
- The Fleet web interface
- The Fleet application API endpoints
- The osquery TLS server API endpoints
Download the latest Fleet binary from the releases page;
curl -LO https://github.com/fleetdm/fleet/releases/download/fleet-v4.20.1/fleet_v4.20.1_linux.tar.gzcurl -LO https://github.com/fleetdm/fleet/releases/download/fleet-v4.20.1/fleetctl_v4.20.1_linux.tar.gzExtract the binaries for Linux platform:
tar xzf fleet_v4.20.1_linux.tar.gztar xzf fleetctl_v4.20.1_linux.tar.gzCopy Fleet binaries to binaries directories;
cp fleet_v4.20.1_linux/fleet /usr/local/bin/cp fleetctl_v4.20.1_linux/fleetctl /usr/local/bin/To verify the binaries are in place;
which fleet fleetctl/usr/local/bin/fleet
/usr/local/bin/fleetctlRunning Fleet Server on Oracle Linux
Initialize Fleet Database
To initialize Fleet infrastructure after installing and setting up all the requirements above, use the fleet prepare db as follows;
fleet prepare db --mysql_address=127.0.0.1:3306 --mysql_database=fleetdb --mysql_username=fleetadmin --mysql_password=StrongP@SSIf the initialization completes successfully, you should get the output,
INFO: 08:57:17 Adding software_id column to software_cve table...
INFO: 08:57:17 Done adding software_id column to software_cve table...
INFO: 08:57:17 Updating software_id column in software_cve table...
INFO: 08:57:17 Nothing to update ...
INFO: 08:57:17 Done updating 'software_id'...
INFO: 08:57:17 Adding index to 'software_id'...
INFO: 08:57:17 Done adding index to 'software_id'...
INFO: 08:57:17 Trying to acquire lock...
INFO: 08:57:17 Lock acquired...
INFO: 08:57:17 Removing duplicates in the software_cve table
INFO: 08:57:17 Adding unique constraint on (cve, software_id) to software_cve table...
INFO: 08:57:17 Done adding unique constraint on (cve, software_id) to software_cve table...
INFO: 08:57:24 Creating table mobile_device_management_solutions...
INFO: 08:57:24 Done creating table mobile_device_management_solutions...
INFO: 08:57:24 Adding column mdm_id to table host_mdm...
INFO: 08:57:24 Done adding column mdm_id to table host_mdm...
INFO: 08:57:24 Adding index on mdm_id of table host_mdm...
INFO: 08:57:24 Done adding index on mdm_id of table host_mdm...
INFO: 08:57:24 Adding index on enrolled, installed_from_dep of table host_mdm...
INFO: 08:57:24 Done adding index on enrolled, installed_from_dep of table host_mdm...
INFO: 08:57:24 Increasing width of software.vendor...
INFO: 08:57:24 Done increasing width of software.vendor...
INFO: 08:57:24 Creating table munki_issues...
INFO: 08:57:24 Done creating table munki_issues...
INFO: 08:57:24 Creating table host_munki_issues...
INFO: 08:57:24 Done creating table host_munki_issues...
INFO: 08:57:24 Deleting dummy software_cpe entries...
INFO: 08:57:24 Done deleting dummy cpe_id entries...
INFO: 08:57:24 Removing cpe_id from software_cve...
INFO: 08:57:24 Done removing cpe_id from software_cve...
Migrations completed.
Generate SSL/TLS Certificates
Fleet server is used to run the main HTTPS server. Hence, run the command below to generate self-signed certificates.
NOTE: If you are using Self Signed Certificates as in this demo, DO NOT use wildcards lest enrollment of hosts won’t work.
openssl req -x509 -nodes -days 3650 -newkey rsa:2048 -keyout /etc/ssl/certs/fleet.key -out /etc/ssl/certs/fleet.cert -subj "/CN=*.kifarunix-demo.com/"If you can, use the commercial TLS certificates from your preferred trusted CA.
Launching Fleet Osquery Manager
Once you have initialized the database, obtained the TLS certs and get a JWT random key, you can then launch it to verify that it can run successfully using the fleet serve command as shown below.
The syntax for running fleet serve is given below;
fleet serve [flags]There are different ways in which you can specify Fleet flags;
Specifying Fleet Manager Flags on Command line
You can specify the flags on command line as shown below;
fleet serve --mysql_address=127.0.0.1:3306 \
--mysql_database=fleetdb --mysql_username=fleetadmin --mysql_password=StrongP@SS \
--server_cert=/etc/ssl/certs/fleet.cert --server_key=/etc/ssl/certs/fleet.key \
--logging_jsonIf all is well, you should see that Fleet server is now running on 0.0.0.0:8080 and hence can be accessed on https://<server-IP>:8080.
{"component":"service","err":null,"level":"info","method":"ListUsers","took":"1.943838ms","ts":"2021-03-22T17:42:25.40539689Z","user":"none"}
{"address":"0.0.0.0:8080","msg":"listening","transport":"https","ts":"2021-03-22T17:42:25.406425857Z"}Press Ctrl+c to stop Fleet server.
Specifying Fleet Manager Flags Using Environment Variables
Similarly, you can specify the Fleet flags using environment variables as shown below (update the values for the environment variables and paste the command on the terminal);
FLEET_MYSQL_ADDRESS=127.0.0.1:3306 \
FLEET_MYSQL_DATABASE=fleetdb \
FLEET_MYSQL_USERNAME=fleetadmin \
FLEET_MYSQL_PASSWORD=StrongP@SS \
FLEET_REDIS_ADDRESS=127.0.0.1:6379 \
FLEET_SERVER_CERT=/etc/ssl/certs/fleet.cert \
FLEET_SERVER_KEY=/etc/ssl/certs/fleet.key \
FLEET_LOGGING_JSON=true \
$(which fleet) serve
Similarly, press Ctrl+c to stop Fleet server.
Setting the Fleet Manager Flags in a Configuration file
You can create a YAML configuration file where you can define the flags and their options. For example, let us create a configuration file, e.g /etc/fleet/fleet.yml.
mkdir /etc/fleetThe, create a YAML configuration file under the directory above.
You can simply execute the command below and be sure to replace your settings appropriately.
cat > /etc/fleet/fleet.yml << 'EOL'
mysql:
address: 127.0.0.1:3306
database: fleetdb
username: fleetadmin
password: StrongP@SS
redis:
address: 127.0.0.1:6379
server:
cert: /etc/ssl/certs/fleet.cert
key: /etc/ssl/certs/fleet.key
logging:
json: true
# auth:
# jwt_key: 0iXLJRKhB77puDm13G6ehgkClK0kff6N
EOL
Next, launch the Fleet manager by running the command below;
fleet serve -c /etc/fleet/fleet.ymlSimilarly, press Ctrl+c to stop Fleet server.
Create Fleet Systemd Service Unit on Oracle Linux
Once you have verified that Fleet is running fine, create a systemd service file, /etc/systemd/system/fleet.service. You can use any method shown above to specify the flags for ExecStart option while creating the systemd service unit file.
Example of Fleet systemd service unit file with Flags specified in ‘cli’ like format.
cat > /etc/systemd/system/fleet.service << 'EOL'
[Unit]
Description=Fleet Osquery Fleet Manager
After=network.target
[Service]
LimitNOFILE=8192
ExecStart=/usr/local/bin/fleet serve \
--mysql_address=127.0.0.1:3306 \
--mysql_database=fleetdb \
--mysql_username=fleetadmin \
--mysql_password=StrongP@SS \
--redis_address=127.0.0.1:6379 \
--server_cert=/etc/ssl/certs/fleet.cert \
--server_key=/etc/ssl/certs/fleet.key \
--logging_json
ExecStop=/bin/kill -15 $(ps aux | grep "fleet serve" | grep -v grep | awk '{print$2}')
[Install]
WantedBy=multi-user.target
EOL
The method I preferred myself is to use the configuration file instead. The below service file uses the configuration file with Fleet flags defined as shown above.
cat > /etc/systemd/system/fleet.service << 'EOL'
[Unit]
Description=Fleet Osquery Fleet Manager
After=network.target
[Service]
LimitNOFILE=8192
ExecStart=/usr/local/bin/fleet serve -c /etc/fleet/fleet.yml
ExecStop=/bin/kill -15 $(ps aux | grep "fleet serve" | grep -v grep | awk '{print$2}')
[Install]
WantedBy=multi-user.target
EOL
Reload systemd configurations.
systemctl daemon-reloadStart and enable Fleet service.
systemctl enable --now fleetCheck the status;
systemctl status fleet
● fleet.service - Fleet Osquery Fleet Manager
Loaded: loaded (/etc/systemd/system/fleet.service; enabled; vendor preset: disabled)
Active: active (running) since Tue 2022-09-27 09:01:35 EAT; 5s ago
Main PID: 29045 (fleet)
Tasks: 6 (limit: 5832)
Memory: 25.8M
CPU: 95ms
CGroup: /system.slice/fleet.service
└─29045 /usr/local/bin/fleet serve -c /etc/fleet/fleet.yml
Sep 27 09:01:35 localhost.localdomain systemd[1]: Started Fleet Osquery Fleet Manager.
Sep 27 09:01:35 localhost.localdomain fleet[29045]: Using config file: /etc/fleet/fleet.yml
Sep 27 09:01:35 localhost.localdomain fleet[29045]: {"component":"redis","level":"info","mode":"standalone","ts":"2022-09-27T06:01:35.540613952Z"}
Sep 27 09:01:35 localhost.localdomain fleet[29045]: {"level":"info","msg":"metrics endpoint disabled (http basic auth credentials not set)","ts":"2022-09-27T06:01:35.58738>
Sep 27 09:01:35 localhost.localdomain fleet[29045]: {"component":"crons","cron":"vulnerabilities","level":"info","periodicity":"1h0m0s","ts":"2022-09-27T06:01:35.587659388>
Sep 27 09:01:35 localhost.localdomain fleet[29045]: {"address":"0.0.0.0:8080","msg":"listening","transport":"https","ts":"2022-09-27T06:01:35.588482596Z"}
Access Fleet Web Interface
Fleet can be accessed on the browser using the URL https://<server-IP_OR_hostname>:8080.
If firewall is running, open this port to allow external access;
firewall-cmd --add-port=8080/tcp --permanent
firewall-cmd --reloadThen access Fleet Web interface from browser. and proceed to finalize the setup of Fleet Osquery manager on Oracle Linux;
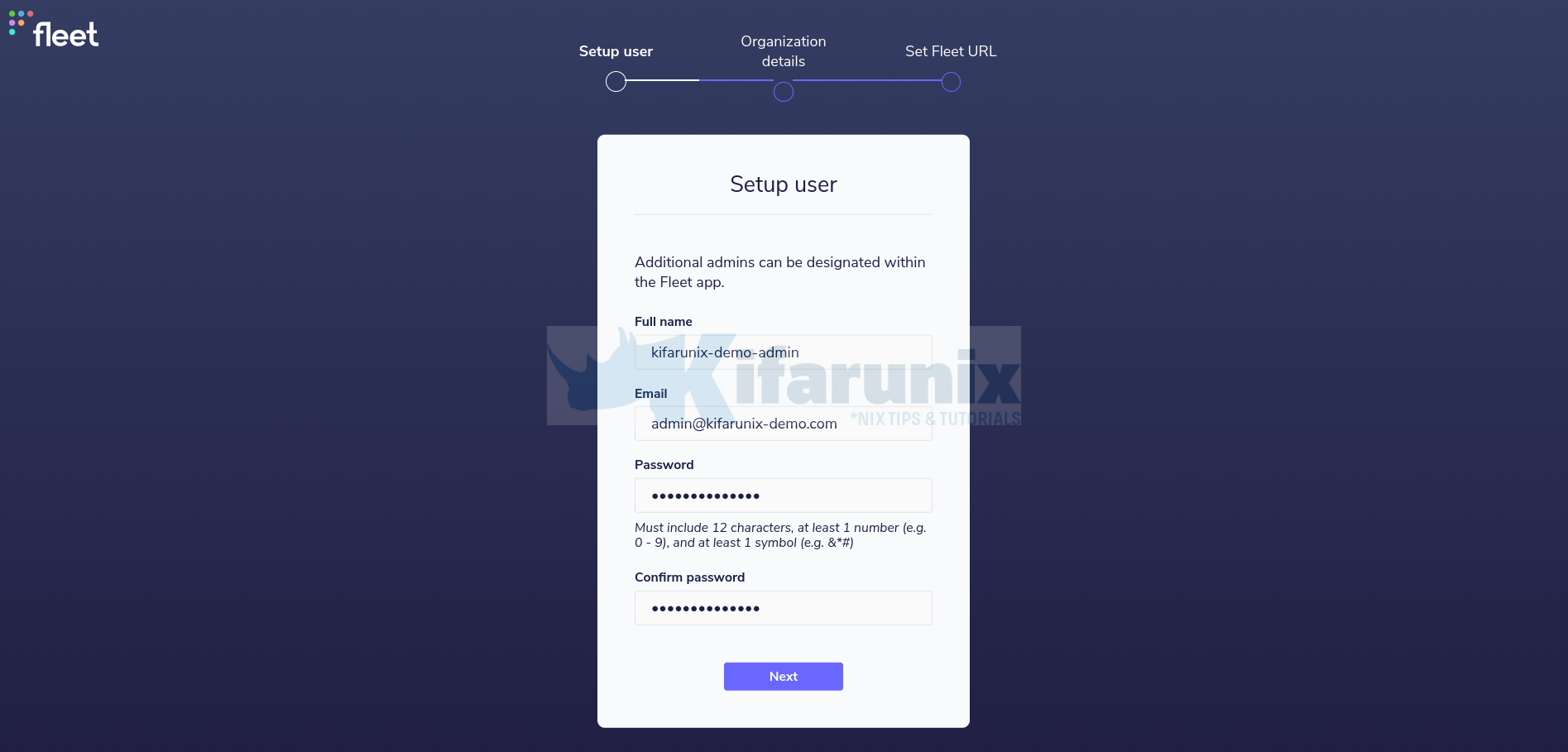
Create the admin user;
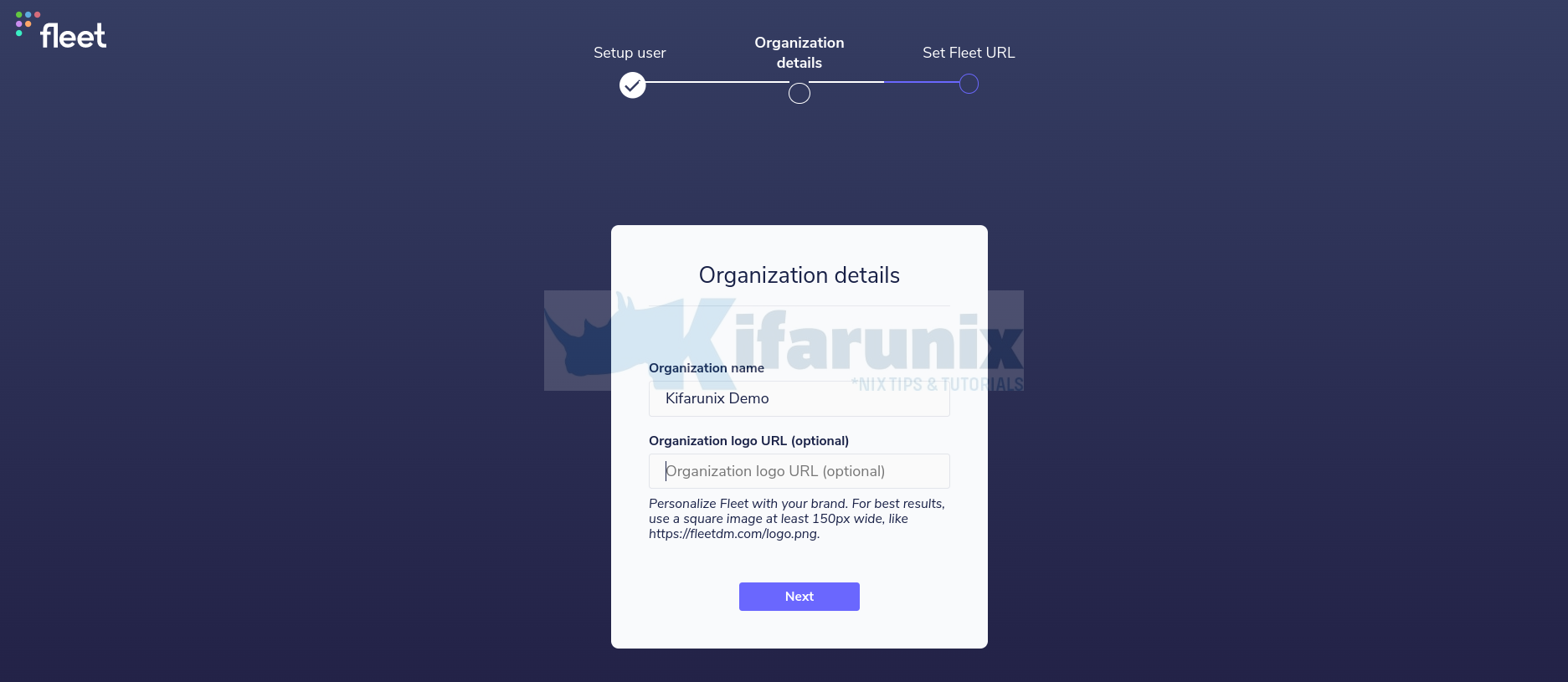
Enter your organization details, Name and url to logo.
Set the Fleet server URL.
Go the next page and confirm the details and proceed to Fleet web interface.
And that marks the end of our tutorial on installation of Fleet Osquery Manager on Oracle Linux.
Other Tutorials
Integrate Osquery Manager with ELK Stack