Follow through this tutorial to learn how to install Consul server on Ubuntu 22.04/Ubuntu 20.04. According to the documentation, “HashiCorp Consul is a service networking solution that enables teams to manage secure network connectivity between services and across on-prem and multi-cloud environments and runtimes. Consul offers service discovery, service mesh, traffic management, and automated updates to network infrastructure device. You can use these features individually or together in a single Consul deployment“.
Installing Consul Server on Ubuntu
You can:
Note that it is recommended to run production Consul in a cluster of either three or five nodes. This is to ensure that Consul’s state is preserved if a single server fails. In this tutorial, however, we will just run Consul on a single node (bootstrap_expect=1) for demonstration purposes!
How to install Consul server on Ubuntu using Precompiled binary
To install Consul server on Ubuntu using Precompiled binary, you can either;
- Install Consul from APT repositories or
- Download the current release version of Consul binary.
Install Consul from APT repositories
To install Consul from APT repositories, proceed as follows;
apt install gnupg2wget -qO- https://apt.releases.hashicorp.com/gpg | gpg --dearmor > \
/etc/apt/trusted.gpg.d/consul.gpgecho "deb https://apt.releases.hashicorp.com $(lsb_release -cs) main" > \
/etc/apt/sources.list.d/consul.listapt updateapt install consulDownload and Install Consul Binary
Navigate to the downloads page and grab Consul binary for your specific system architecture.
As of this writing, Consul v1.13.2 is the current stable release. You can just grab the download link and pull it as follows;
wget https://releases.hashicorp.com/consul/1.13.2/consul_1.13.2_linux_amd64.zipExtract the binary to /usr/local/bin directory;
unzip consul_1.13.2_linux_amd64.zip -d /usr/local/bin/Build Consul from Source
If you want, you can build Consul from the source.
Download and install Go.
wget https://go.dev/dl/go1.19.1.linux-amd64.tar.gztar xzf go1.19.1.linux-amd64.tar.gz -C /optUpdate the PATH with path to Go binary;
sed -i.bak 's|"$|:/opt/go/bin/"|' /etc/environmentsource /etc/environmentNext, clone the Consul repository from GitHub:
apt install git makegit clone https://github.com/hashicorp/consul.gitCompile Consul;
cd consulmake devOnce compilation is done, copy the binary to /usr/local/bin/;
cp ./bin/consul /usr/local/bin/Verify Consul Installation
You can run the consul command without any options to confirm and verify its installation.
consul
Usage: consul [--version] [--help] []
Available commands are:
acl Interact with Consul's ACLs
agent Runs a Consul agent
catalog Interact with the catalog
config Interact with Consul's Centralized Configurations
connect Interact with Consul Connect
debug Records a debugging archive for operators
event Fire a new event
exec Executes a command on Consul nodes
force-leave Forces a member of the cluster to enter the "left" state
info Provides debugging information for operators.
intention Interact with Connect service intentions
join Tell Consul agent to join cluster
keygen Generates a new encryption key
keyring Manages gossip layer encryption keys
kv Interact with the key-value store
leave Gracefully leaves the Consul cluster and shuts down
lock Execute a command holding a lock
login Login to Consul using an auth method
logout Destroy a Consul token created with login
maint Controls node or service maintenance mode
members Lists the members of a Consul cluster
monitor Stream logs from a Consul agent
operator Provides cluster-level tools for Consul operators
peering Create and manage peering connections between Consul clusters
reload Triggers the agent to reload configuration files
rtt Estimates network round trip time between nodes
services Interact with services
snapshot Saves, restores and inspects snapshots of Consul server state
tls Builtin helpers for creating CAs and certificates
validate Validate config files/directories
version Prints the Consul version
watch Watch for changes in Consul
Configuring Consul Agent on Ubuntu
As already mentioned, we are running a single node Consul server in this setup (Option; bootstrap_expect=1).
Consul agent can run either in server or client mode. We will run Consul agent as a server in this setup.
Thus, before you can start Consul agent server, there are a few things that you need to do.
- Create Consul service account (ONLY if you didn’t install Consul using APT);
useradd -r -M -s /bin/false consul- Create Consul data directory. If you installed using APT,
/opt/consuldirectory is created by default. You can choose to use a different directory though.
[ -d /opt/consul ] || mkdir /opt/consul- Create Consul configurations directory. Similarly, this directory is created if you installed Consul using APT;
[ -d /etc/consul.d ] || mkdir /etc/consul.dAny custom configuration options need to be placed in consul.hcl file, under the configuration directory created above.
For example, to define the custom options;
vim /etc/consul.d/consul.hclbind_addr = "192.168.56.124"
data_dir = "/opt/consul"
bootstrap_expect=1Always confirm the validity of the Consul configuration file;
sudo consul validate /etc/consul.d/You should get such an output if all is good.
Configuration is valid!- Set Proper ownership for the Consul data and configuration directories
chown -R consul: /opt/consul /etc/consul.dRunning Consul Agent Server
“Consul uses documented reasonable defaults so only non-default values must be set in the configuration file”.
You can use the command below to start the Consul agent and runs until an interrupt is received. The agent represents a single node in a cluster.
consul agent [options]These are the available [options] you can use;
HTTP API Options
-datacenter=
Datacenter of the agent.
Command Options
-advertise=
Sets the advertise address to use.
-advertise-wan=
Sets address to advertise on WAN instead of -advertise address.
-allow-write-http-from=
Only allow write endpoint calls from given network. CIDR format,
can be specified multiple times.
-alt-domain=
Alternate domain to use for DNS interface.
-auto-reload-config
Watches config files for changes and auto reloads the files when
modified.
-bind=
Sets the bind address for cluster communication.
-bootstrap
Sets server to bootstrap mode.
-bootstrap-expect=
Sets server to expect bootstrap mode.
-check_output_max_size=
Sets the maximum output size for checks on this agent
-client=
Sets the address to bind for client access. This includes RPC, DNS,
HTTP, HTTPS and gRPC (if configured).
-config-dir=
Path to a directory to read configuration files from. This
will read every file ending in '.json' as configuration in this
directory in alphabetical order. Can be specified multiple times.
-config-file=
Path to a file in JSON or HCL format with a matching file
extension. Can be specified multiple times.
-config-format=
Config files are in this format irrespective of their extension.
Must be 'hcl' or 'json'
-data-dir=
Path to a data directory to store agent state.
-default-query-time=
the amount of time a blocking query will wait before Consul will
force a response. This value can be overridden by the 'wait' query
parameter.
-dev
Starts the agent in development mode.
-disable-host-node-id
Setting this to true will prevent Consul from using information
from the host to generate a node ID, and will cause Consul to
generate a random node ID instead.
-disable-keyring-file
Disables the backing up of the keyring to a file.
-dns-port=
DNS port to use.
-domain=
Domain to use for DNS interface.
-enable-local-script-checks
Enables health check scripts from configuration file.
-enable-script-checks
Enables health check scripts.
-encrypt=
Provides the gossip encryption key.
-grpc-port=
Sets the gRPC API port to listen on.
-grpc-tls-port=
Sets the gRPC-TLS API port to listen on.
-hcl=
hcl config fragment. Can be specified multiple times.
-http-port=
Sets the HTTP API port to listen on.
-https-port=
Sets the HTTPS API port to listen on.
-join=
Address of an agent to join at start time. Can be specified
multiple times.
-join-wan=
Address of an agent to join -wan at start time. Can be specified
multiple times.
-log-file=
Path to the file the logs get written to
-log-json
Output logs in JSON format.
-log-level=
Log level of the agent.
-log-rotate-bytes=
Maximum number of bytes that should be written to a log file
-log-rotate-duration=
Time after which log rotation needs to be performed
-log-rotate-max-files=
Maximum number of log file archives to keep
-max-query-time=
the maximum amount of time a blocking query can wait before Consul
will force a response. Consul applies jitter to the wait time. The
jittered time will be capped to MaxQueryTime.
-node=
Name of this node. Must be unique in the cluster.
-node-id=
A unique ID for this node across space and time. Defaults to a
randomly-generated ID that persists in the data-dir.
-node-meta=
An arbitrary metadata key/value pair for this node, of the format
`key:value`. Can be specified multiple times.
-non-voting-server
(Enterprise-only) DEPRECATED: -read-replica should be used instead
-pid-file=
Path to file to store agent PID.
-primary-gateway=
Address of a mesh gateway in the primary datacenter to use to
bootstrap WAN federation at start time with retries enabled. Can be
specified multiple times.
-protocol=
Sets the protocol version. Defaults to latest.
-raft-protocol=
Sets the Raft protocol version. Defaults to latest.
-read-replica
(Enterprise-only) This flag is used to make the server not
participate in the Raft quorum, and have it only receive the data
replication stream. This can be used to add read scalability to
a cluster in cases where a high volume of reads to servers are
needed.
-recursor=
Address of an upstream DNS server. Can be specified multiple times.
-rejoin
Ignores a previous leave and attempts to rejoin the cluster.
-retry-interval=
Time to wait between join attempts.
-retry-interval-wan=
Time to wait between join -wan attempts.
-retry-join=
Address of an agent to join at start time with retries enabled. Can
be specified multiple times.
-retry-join-wan=
Address of an agent to join -wan at start time with retries
enabled. Can be specified multiple times.
-retry-max=
Maximum number of join attempts. Defaults to 0, which will retry
indefinitely.
-retry-max-wan=
Maximum number of join -wan attempts. Defaults to 0, which will
retry indefinitely.
-segment=
(Enterprise-only) Sets the network segment to join.
-serf-lan-allowed-cidrs=
Networks (eg: 192.168.1.0/24) allowed for Serf LAN. Can be
specified multiple times.
-serf-lan-bind=
Address to bind Serf LAN listeners to.
-serf-lan-port=
Sets the Serf LAN port to listen on.
-serf-wan-allowed-cidrs=
Networks (eg: 192.168.1.0/24) allowed for Serf WAN (other
datacenters). Can be specified multiple times.
-serf-wan-bind=
Address to bind Serf WAN listeners to.
-serf-wan-port=
Sets the Serf WAN port to listen on.
-server
Switches agent to server mode.
-server-port=
Sets the server port to listen on.
-syslog
Enables logging to syslog.
-ui
Enables the built-in static web UI server.
-ui-content-path=
Sets the external UI path to a string. Defaults to: /ui/
-ui-dir=
Path to directory containing the web UI resources.
To Start Consul agent server in development mode, with default configs;
consul agent -devPress Ctrl+c to stop.
To run Consul agent as a server;
sudo -u consul consul agent -bind=192.168.56.124 -bootstrap-expect=1 -data-dir=/opt/consul -serverSample output;
==> Starting Consul agent...
Version: '1.14.0-dev'
Revision: 'a74d826b0'
Build Date: '2022-09-30 19:17:16 +0000 UTC'
Node ID: 'a191f825-3766-1ea1-d5a6-e5d2612756e4'
Node name: 'jellyfish'
Datacenter: 'dc1' (Segment: '')
Server: true (Bootstrap: true)
Client Addr: [127.0.0.1] (HTTP: 8500, HTTPS: -1, gRPC: -1, gRPC-TLS: -1, DNS: 8600)
Cluster Addr: 192.168.56.124 (LAN: 8301, WAN: 8302)
Gossip Encryption: false
Auto-Encrypt-TLS: false
HTTPS TLS: Verify Incoming: false, Verify Outgoing: false, Min Version: TLSv1_2
gRPC TLS: Verify Incoming: false, Min Version: TLSv1_2
Internal RPC TLS: Verify Incoming: false, Verify Outgoing: false (Verify Hostname: false), Min Version: TLSv1_2
==> Log data will now stream in as it occurs:
2022-10-01T07:02:52.526Z [WARN] agent: BootstrapExpect is set to 1; this is the same as Bootstrap mode.
2022-10-01T07:02:52.526Z [WARN] agent: bootstrap = true: do not enable unless necessary
2022-10-01T07:02:52.534Z [WARN] agent.auto_config: BootstrapExpect is set to 1; this is the same as Bootstrap mode.
2022-10-01T07:02:52.534Z [WARN] agent.auto_config: bootstrap = true: do not enable unless necessary
2022-10-01T07:02:52.541Z [INFO] agent.server.raft: initial configuration: index=1 servers="[{Suffrage:Voter ID:a191f825-3766-1ea1-d5a6-e5d2612756e4 Address:192.168.56.124:8300}]"
2022-10-01T07:02:52.541Z [INFO] agent.server.raft: entering follower state: follower="Node at 192.168.56.124:8300 [Follower]" leader-address= leader-id=
2022-10-01T07:02:52.541Z [INFO] agent.server.serf.wan: serf: EventMemberJoin: jellyfish.dc1 192.168.56.124
2022-10-01T07:02:52.541Z [WARN] agent.server.serf.wan: serf: Failed to re-join any previously known node
2022-10-01T07:02:52.541Z [INFO] agent.server.serf.lan: serf: EventMemberJoin: jellyfish 192.168.56.124
2022-10-01T07:02:52.542Z [INFO] agent.router: Initializing LAN area manager
2022-10-01T07:02:52.542Z [WARN] agent.server.serf.lan: serf: Failed to re-join any previously known node
2022-10-01T07:02:52.542Z [INFO] agent.server.autopilot: reconciliation now disabled
2022-10-01T07:02:52.542Z [INFO] agent.server: Handled event for server in area: event=member-join server=jellyfish.dc1 area=wan
2022-10-01T07:02:52.542Z [INFO] agent.server: Adding LAN server: server="jellyfish (Addr: tcp/192.168.56.124:8300) (DC: dc1)"
2022-10-01T07:02:52.542Z [WARN] agent: [core]grpc: addrConn.createTransport failed to connect to {dc1-192.168.56.124:8300 jellyfish 0 }. Err: connection error: desc = "transport: Error while dialing dial tcp 192.168.56.124:0->192.168.56.124:8300: operation was canceled". Reconnecting...
2022-10-01T07:02:52.543Z [INFO] agent: Started DNS server: address=127.0.0.1:8600 network=udp
2022-10-01T07:02:52.543Z [INFO] agent: Started DNS server: address=127.0.0.1:8600 network=tcp
2022-10-01T07:02:52.544Z [INFO] agent: Starting server: address=127.0.0.1:8500 network=tcp protocol=http
2022-10-01T07:02:52.544Z [INFO] agent: started state syncer
2022-10-01T07:02:52.544Z [INFO] agent: Consul agent running!
2022-10-01T07:02:57.806Z [WARN] agent.server.raft: heartbeat timeout reached, starting election: last-leader-addr= last-leader-id=
2022-10-01T07:02:57.806Z [INFO] agent.server.raft: entering candidate state: node="Node at 192.168.56.124:8300 [Candidate]" term=3
2022-10-01T07:02:57.826Z [INFO] agent.server.raft: election won: tally=1
2022-10-01T07:02:57.826Z [INFO] agent.server.raft: entering leader state: leader="Node at 192.168.56.124:8300 [Leader]"
2022-10-01T07:02:57.827Z [INFO] agent.server: cluster leadership acquired
2022-10-01T07:02:57.828Z [INFO] agent.server: New leader elected: payload=jellyfish
2022-10-01T07:02:57.846Z [INFO] agent.server.autopilot: reconciliation now enabled
2022-10-01T07:02:57.846Z [INFO] agent.leader: started routine: routine="federation state anti-entropy"
2022-10-01T07:02:57.846Z [INFO] agent.leader: started routine: routine="federation state pruning"
2022-10-01T07:02:58.059Z [INFO] agent: Synced node info
You can use these options in a configuration file;
sudo -u consul vim /etc/consul.d/consul.hclbind_addr = "192.168.56.124"
bootstrap_expect=1
data_dir = "/opt/consul"
server = trueAnd just use the command;
sudo -u consul consul agent -config-dir=/etc/consul.dRunning Consul Agent server with Consul UI Enabled;
Consul features a web-based user interface, allowing you to get an overview of all services, nodes, intentions and more using a graphical user interface, rather than the CLI or API.
If you are running Consul in a cluster, you can enable UI on a single node.
To enable Consul UI, you can pass the options on the command line or use the configuration file;
To pass the options, -ui on the command line;
sudo -u consul consul agent -bind=192.168.56.124 -bootstrap-expect=1 -data-dir=/opt/consul -server -ui
==> Starting Consul agent...
Version: '1.14.0-dev'
Revision: 'a74d826b0'
Build Date: '2022-09-30 19:17:16 +0000 UTC'
Node ID: 'a191f825-3766-1ea1-d5a6-e5d2612756e4'
Node name: 'jellyfish'
Datacenter: 'dc1' (Segment: '')
Server: true (Bootstrap: true)
Client Addr: [127.0.0.1] (HTTP: 8500, HTTPS: -1, gRPC: -1, gRPC-TLS: -1, DNS: 8600)
Cluster Addr: 192.168.56.124 (LAN: 8301, WAN: 8302)
Gossip Encryption: false
Auto-Encrypt-TLS: false
HTTPS TLS: Verify Incoming: false, Verify Outgoing: false, Min Version: TLSv1_2
gRPC TLS: Verify Incoming: false, Min Version: TLSv1_2
Internal RPC TLS: Verify Incoming: false, Verify Outgoing: false (Verify Hostname: false), Min Version: TLSv1_2
==> Log data will now stream in as it occurs:
2022-10-01T07:08:34.316Z [WARN] agent: BootstrapExpect is set to 1; this is the same as Bootstrap mode.
2022-10-01T07:08:34.316Z [WARN] agent: bootstrap = true: do not enable unless necessary
2022-10-01T07:08:34.322Z [WARN] agent.auto_config: BootstrapExpect is set to 1; this is the same as Bootstrap mode.
2022-10-01T07:08:34.322Z [WARN] agent.auto_config: bootstrap = true: do not enable unless necessary
2022-10-01T07:08:34.330Z [INFO] agent.server.raft: initial configuration: index=1 servers="[{Suffrage:Voter ID:a191f825-3766-1ea1-d5a6-e5d2612756e4 Address:192.168.56.124:8300}]"
2022-10-01T07:08:34.330Z [INFO] agent.server.raft: entering follower state: follower="Node at 192.168.56.124:8300 [Follower]" leader-address= leader-id=
2022-10-01T07:08:34.331Z [INFO] agent.server.serf.wan: serf: EventMemberJoin: jellyfish.dc1 192.168.56.124
2022-10-01T07:08:34.331Z [WARN] agent.server.serf.wan: serf: Failed to re-join any previously known node
2022-10-01T07:08:34.332Z [INFO] agent.server.serf.lan: serf: EventMemberJoin: jellyfish 192.168.56.124
2022-10-01T07:08:34.332Z [INFO] agent.router: Initializing LAN area manager
2022-10-01T07:08:34.332Z [INFO] agent.server.autopilot: reconciliation now disabled
2022-10-01T07:08:34.332Z [WARN] agent.server.serf.lan: serf: Failed to re-join any previously known node
2022-10-01T07:08:34.332Z [INFO] agent.server: Adding LAN server: server="jellyfish (Addr: tcp/192.168.56.124:8300) (DC: dc1)"
2022-10-01T07:08:34.333Z [INFO] agent.server: Handled event for server in area: event=member-join server=jellyfish.dc1 area=wan
2022-10-01T07:08:34.333Z [WARN] agent: [core]grpc: addrConn.createTransport failed to connect to {dc1-192.168.56.124:8300 jellyfish 0 }. Err: connection error: desc = "transport: Error while dialing dial tcp 192.168.56.124:0->192.168.56.124:8300: operation was canceled". Reconnecting...
2022-10-01T07:08:34.334Z [INFO] agent: Started DNS server: address=127.0.0.1:8600 network=udp
2022-10-01T07:08:34.334Z [INFO] agent: Started DNS server: address=127.0.0.1:8600 network=tcp
2022-10-01T07:08:34.334Z [INFO] agent: Starting server: address=127.0.0.1:8500 network=tcp protocol=http
2022-10-01T07:08:34.335Z [INFO] agent: started state syncer
2022-10-01T07:08:34.335Z [INFO] agent: Consul agent running!
This will start HTTP server on Port 8500, bind to loopback interface;
2022-10-01T06:41:00.847Z [INFO] agent: Starting server: address=127.0.0.1:8500 network=tcp protocol=httpTo bind the HTTP server to a non-loopback interface, define the address using -client option.
sudo -u consul consul agent -bind=192.168.56.124 -bootstrap-expect=1 -client=192.168.56.124 -data-dir=/opt/consul -server -uiTo enable these options in a configuration file;
vim /etc/consul.d/consul.hcl...
data_dir = "/opt/consul"
client_addr = "192.168.56.124"
ui_config{
enabled = true
}
server = true
bind_addr = "192.168.56.124"
bootstrap_expect=1
...Then, you can just start Consult agent server;
sudo -u consul consul agent -config-dir=/etc/consul.dNote that you can control all these command line options in the configuration file.
Here is a sample config with all options commented out;
cat /etc/consul.d/consul.hcl
# Full configuration options can be found at https://www.consul.io/docs/agent/config
# datacenter
# This flag controls the datacenter in which the agent is running. If not provided,
# it defaults to "dc1". Consul has first-class support for multiple datacenters, but
# it relies on proper configuration. Nodes in the same datacenter should be on a
# single LAN.
#datacenter = "my-dc-1"
# data_dir
# This flag provides a data directory for the agent to store state. This is required
# for all agents. The directory should be durable across reboots. This is especially
# critical for agents that are running in server mode as they must be able to persist
# cluster state. Additionally, the directory must support the use of filesystem
# locking, meaning some types of mounted folders (e.g. VirtualBox shared folders) may
# not be suitable.
data_dir = "/opt/consul"
# client_addr
# The address to which Consul will bind client interfaces, including the HTTP and DNS
# servers. By default, this is "127.0.0.1", allowing only loopback connections. In
# Consul 1.0 and later this can be set to a space-separated list of addresses to bind
# to, or a go-sockaddr template that can potentially resolve to multiple addresses.
#client_addr = "0.0.0.0"
# ui
# Enables the built-in web UI server and the required HTTP routes. This eliminates
# the need to maintain the Consul web UI files separately from the binary.
# Version 1.10 deprecated ui=true in favor of ui_config.enabled=true
#ui_config{
# enabled = true
#}
# server
# This flag is used to control if an agent is in server or client mode. When provided,
# an agent will act as a Consul server. Each Consul cluster must have at least one
# server and ideally no more than 5 per datacenter. All servers participate in the Raft
# consensus algorithm to ensure that transactions occur in a consistent, linearizable
# manner. Transactions modify cluster state, which is maintained on all server nodes to
# ensure availability in the case of node failure. Server nodes also participate in a
# WAN gossip pool with server nodes in other datacenters. Servers act as gateways to
# other datacenters and forward traffic as appropriate.
#server = true
# Bind addr
# You may use IPv4 or IPv6 but if you have multiple interfaces you must be explicit.
#bind_addr = "[::]" # Listen on all IPv6
#bind_addr = "0.0.0.0" # Listen on all IPv4
#
# Advertise addr - if you want to point clients to a different address than bind or LB.
#advertise_addr = "127.0.0.1"
# Enterprise License
# As of 1.10, Enterprise requires a license_path and does not have a short trial.
#license_path = "/etc/consul.d/consul.hclic"
# bootstrap_expect
# This flag provides the number of expected servers in the datacenter. Either this value
# should not be provided or the value must agree with other servers in the cluster. When
# provided, Consul waits until the specified number of servers are available and then
# bootstraps the cluster. This allows an initial leader to be elected automatically.
# This cannot be used in conjunction with the legacy -bootstrap flag. This flag requires
# -server mode.
#bootstrap_expect=3
# encrypt
# Specifies the secret key to use for encryption of Consul network traffic. This key must
# be 32-bytes that are Base64-encoded. The easiest way to create an encryption key is to
# use consul keygen. All nodes within a cluster must share the same encryption key to
# communicate. The provided key is automatically persisted to the data directory and loaded
# automatically whenever the agent is restarted. This means that to encrypt Consul's gossip
# protocol, this option only needs to be provided once on each agent's initial startup
# sequence. If it is provided after Consul has been initialized with an encryption key,
# then the provided key is ignored and a warning will be displayed.
#encrypt = "..."
# retry_join
# Similar to -join but allows retrying a join until it is successful. Once it joins
# successfully to a member in a list of members it will never attempt to join again.
# Agents will then solely maintain their membership via gossip. This is useful for
# cases where you know the address will eventually be available. This option can be
# specified multiple times to specify multiple agents to join. The value can contain
# IPv4, IPv6, or DNS addresses. In Consul 1.1.0 and later this can be set to a go-sockaddr
# template. If Consul is running on the non-default Serf LAN port, this must be specified
# as well. IPv6 must use the "bracketed" syntax. If multiple values are given, they are
# tried and retried in the order listed until the first succeeds. Here are some examples:
#retry_join = ["consul.domain.internal"]
#retry_join = ["10.0.4.67"]
#retry_join = ["[::1]:8301"]
#retry_join = ["consul.domain.internal", "10.0.4.67"]
# Cloud Auto-join examples:
# More details - https://www.consul.io/docs/agent/cloud-auto-join
#retry_join = ["provider=aws tag_key=... tag_value=..."]
#retry_join = ["provider=azure tag_name=... tag_value=... tenant_id=... client_id=... subscription_id=... secret_access_key=..."]
#retry_join = ["provider=gce project_name=... tag_value=..."]
You can now access Consul Web UI via http://server-IP:8500.
Running Consul Agent Server as systemd Service
For easy manageability, you can create a systemd service unit file for Consul by running the command below;
Ensure the path to the consul binary is correct, /usr/local/bin/consul in our setup.
cat > /etc/systemd/system/consul.service << 'EOL'
[Unit]
Description="HashiCorp Consul"
Requires=network-online.target
After=network-online.target
ConditionFileNotEmpty=/etc/consul.d/consul.hcl
[Service]
EnvironmentFile=-/etc/consul.d/consul.env
User=consul
Group=consul
ExecStart=/usr/local/bin/consul agent -config-dir=/etc/consul.d/
ExecReload=/bin/kill --signal HUP $MAINPID
KillMode=process
KillSignal=SIGTERM
Restart=on-failure
LimitNOFILE=65536
[Install]
WantedBy=multi-user.target
EOL
Note that the service above uses the Consul options in a configuration file, /etc/consul.d/consul.hcl.
Start and enable Consul service to run on system boot;
systemctl enable --now consulCheck the status;
systemctl status consul● consul.service - "HashiCorp Consul"
Loaded: loaded (/etc/systemd/system/consul.service; enabled; vendor preset: enabled)
Active: active (running) since Sat 2022-10-01 07:20:45 UTC; 2s ago
Main PID: 66160 (consul)
Tasks: 9 (limit: 2241)
Memory: 23.4M
CPU: 111ms
CGroup: /system.slice/consul.service
└─66160 /usr/local/bin/consul agent -config-dir=/etc/consul.d/
Oct 01 07:20:46 jellyfish consul[66160]: 2022-10-01T07:20:46.054Z [WARN] agent.server.serf.lan: serf: Failed to re-join any previously known node
Oct 01 07:20:46 jellyfish consul[66160]: 2022-10-01T07:20:46.054Z [WARN] agent.server.serf.wan: serf: Failed to re-join any previously known node
Oct 01 07:20:46 jellyfish consul[66160]: 2022-10-01T07:20:46.054Z [INFO] agent.server: Handled event for server in area: event=member-join server=jellyfish.dc1 area=wan
Oct 01 07:20:46 jellyfish consul[66160]: 2022-10-01T07:20:46.054Z [WARN] agent: [core]grpc: addrConn.createTransport failed to connect to {dc1-192.168.56.124:8300 jellyfi>
Oct 01 07:20:46 jellyfish consul[66160]: 2022-10-01T07:20:46.054Z [INFO] agent.server: Adding LAN server: server="jellyfish (Addr: tcp/192.168.56.124:8300) (DC: dc1)"
Oct 01 07:20:46 jellyfish consul[66160]: 2022-10-01T07:20:46.056Z [INFO] agent: Started DNS server: address=192.168.56.124:8600 network=udp
Oct 01 07:20:46 jellyfish consul[66160]: 2022-10-01T07:20:46.056Z [INFO] agent: Started DNS server: address=192.168.56.124:8600 network=tcp
Oct 01 07:20:46 jellyfish consul[66160]: 2022-10-01T07:20:46.056Z [INFO] agent: Starting server: address=192.168.56.124:8500 network=tcp protocol=http
Oct 01 07:20:46 jellyfish consul[66160]: 2022-10-01T07:20:46.056Z [INFO] agent: started state syncer
Oct 01 07:20:46 jellyfish consul[66160]: 2022-10-01T07:20:46.056Z [INFO] agent: Consul agent running!
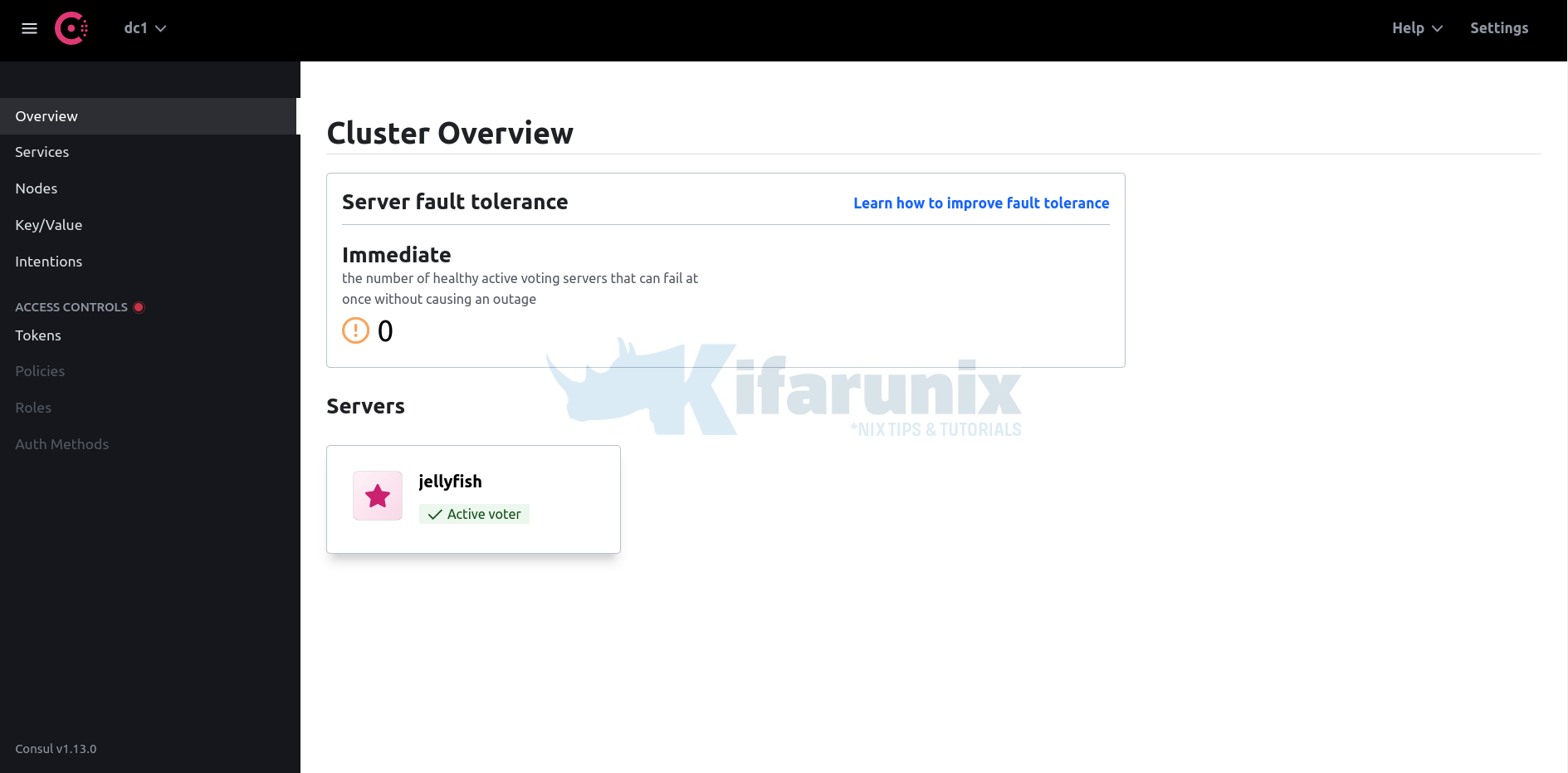
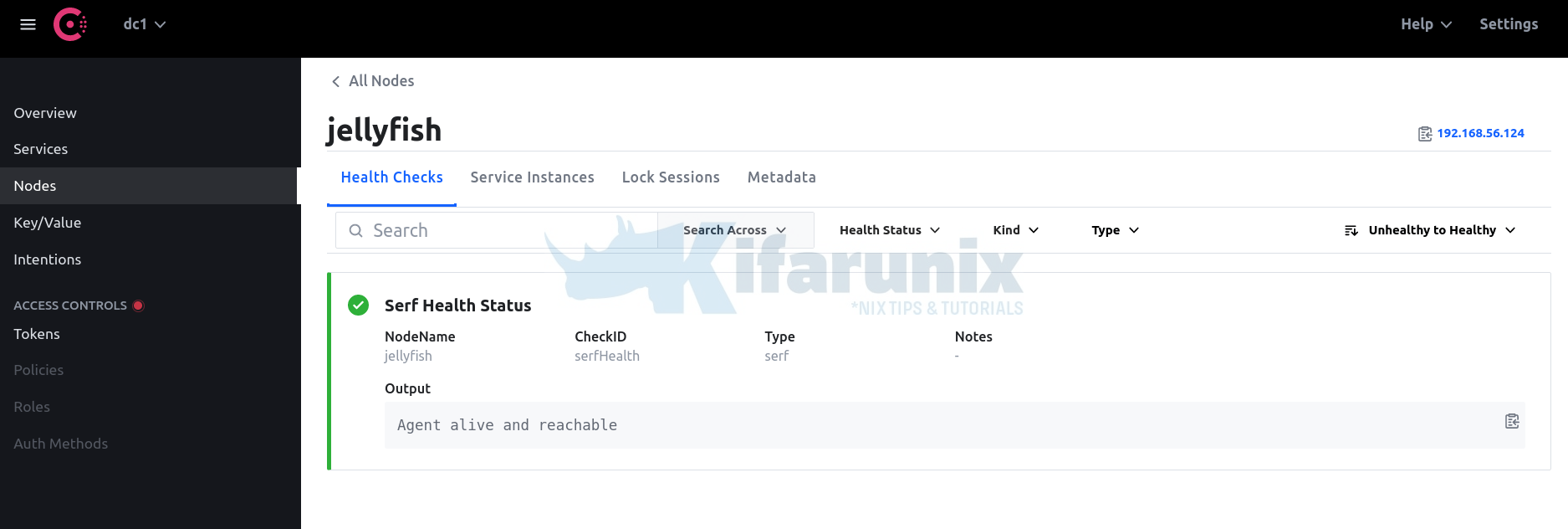
Accessing Consul Agent Server Web UI
If you enabled Consul UI, you can access via the addresses that you defined on the configuration. Eg http://server-IP-or-resolvable-domain:8500.
Cluster Overview;
Nodes Overview
You can continue to explore Consul UI.
Further Reading
Other Tutorials
Install and Deploy Kubernetes Cluster on Ubuntu 20.04
Analyze PCAP Files using Malcolm Network Traffic Analysis tool