Welcome to our guide on how to install and configure Maltrail on Ubuntu 18.04. Maltrail is a malicious traffic detection system. It utilizes the blacklists containing malicious or suspicious trails that are available in public domain. It can also utilize custom lists created by the users themselves as well as reports from various AntiVirus solutions. The trail in question includes domains names, IP addresses, URLs, HTTP User Agent header values associated with Malicious traffic. Apart from using the lists on public domains, Maltrail can also heuristically analyze the traffic to detect unknown or new threats.
Maltrail is made up of three components; The Sensor which monitors traffic for threats, the Server which provides logging for the event details of the detected malicious traffic, and the Client which provides visualization and reporting of the event details. In this guide, we are going to setup standalone deployment architecture where all components are running on the same server.
Install and Configure Maltrail on Ubuntu 18.04
Install Maltrail on Ubuntu 18.04, you need to clone the git repository to your system. However, before you can proceed, upgrade your system packages and install the following Maltrail dependencies.
Update and upgrade your system
apt update apt upgrade
Install the required dependencies
Maltrail requires the python pcap packages. Hence, to install pcap and other necessary dependencies, run the command below;
apt install python-setuptools python-pcapy
Clone the Maltrail Github repository
Run the command below to clone Maltrail Github repository into your server
git clone https://github.com/stamparm/maltrail.git
Start Maltrail Sensor
To run Maltrail Sensor, navigate to the Maltrail clone directory and execute the command below to run the Maltrail sensor in background.
cd maltrail/ python sensor.py &
When run, the script downloads and updates the Maltrail lists related to Malicious traffic and launch the Maltrail Sensor service.
Maltrail (sensor) #v0.12.16 [i] using configuration file '/home/amos/maltrail/maltrail.conf' [i] using '/var/log/maltrail' for log storage [?] at least 384MB of free memory required [i] using '/root/.maltrail/trails.csv' for trail storage ... [i] update finished [i] trails stored to '/root/.maltrail/trails.csv' [i] updating ipcat database... [?] in case of any problems with packet capture on virtual interface 'any', please put all monitoring interfaces to promiscuous mode manually (e.g. 'sudo ifconfig eth0 promisc') [i] opening interface 'any' [i] setting capture filter 'udp or icmp or (tcp and (tcp[tcpflags] == tcp-syn or port 80 or port 1080 or port 3128 or port 8000 or port 8080 or port 8118))' [?] please install 'schedtool' for better CPU scheduling (e.g. 'sudo apt-get install schedtool') [o] running...
Note that the Sensor is using any interface for monitoring. To set this to a specific interace, edit the maltrail.conf configuration file under /home/username/maltrail/maltrail.conf under the Sensor section.
# Interface used for monitoring (e.g. eth0, eth1) #MONITOR_INTERFACE any MONITOR_INTERFACE enp0s8
Start Maltrail Server
To start Maltrail server, run the command below under the maltrail directory.
python server.py &
Maltrail (server) #v0.12.16 [i] using configuration file '/home/amos/maltrail/maltrail.conf' [i] starting HTTP server at 'http://0.0.0.0:8338/' [o] running...
As you can see, the server is now listening on all interfaces on the server on TCP port 8338. If you need to change this, stop the server and edit the configuration file $HOME/maltrail/maltrail.conf.
pkill -f server.py
Edit the maltrail.conf to set the interface to a specific IP.
vim maltrail.conf
# [Server] # Listen address of (reporting) HTTP server #HTTP_ADDRESS 0.0.0.0 HTTP_ADDRESS 192.168.43.203
Run the server again.
python server.py &
... [i] using configuration file '/home/amos/maltrail/maltrail.conf' [i] starting HTTP server at 'http://192.168.43.203:8338/' [o] running...
To login to the Web User interface, navigate to the address above, http://192.168.43.203:8338/. You will be redirected to Maltrail login interface. The default login credentials are: admin:changeme!.
To change the admin password, you need to generate a sha256 password by running the comand below;
echo -n 'password' | sha256sum | cut -d " " -f 1
5e884898da28047151d0e56f8dc6292773603d0d6aabbdd62a11ef721d1542d8
Where password is your password string. Next, copy the code and paste it on the maltrail.conf, server section, USERS sub-section. For example, if you were changing for the admin user,
USERS
admin:5e884898da28047151d0e56f8dc6292773603d0d6aabbdd62a11ef721d1542d8:0: # password
# admin:9ab3cd9d67bf49d01f6a2e33d0bd9bc804ddbe6ce1ff5d219c42624851db5dbc:0: # changeme!
# local:9ab3cd9d67bf49d01f6a2e33d0bd9bc804ddbe6ce1ff5d219c42624851db5dbc:1000:192.168.0.0/16 # changeme!
Restart the Maltrail server for the changes to take effect.
Testing Maltrail
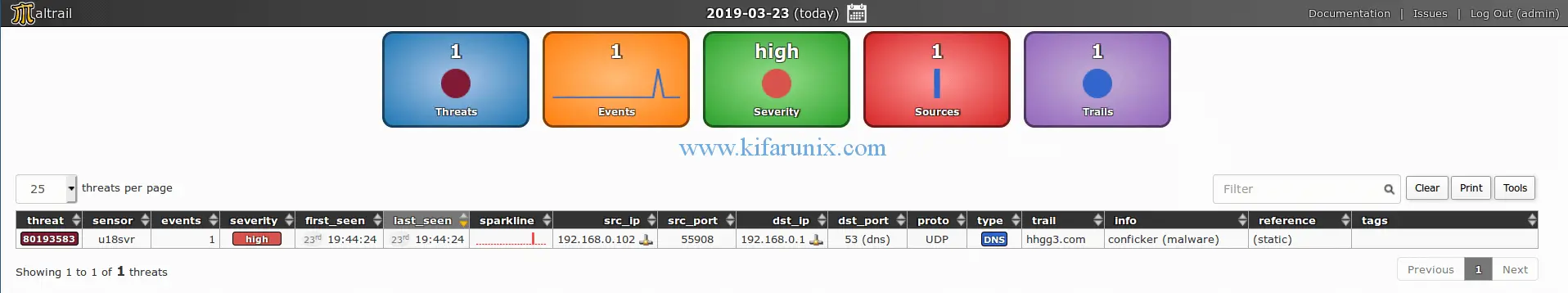
Well, to test how Maltrail detection works, am gonna try to establish a connection to a domain associated with malware as shown below;
ping hhgg3.com -c 10
PING pkcdn2.pk051.com (173.248.252.3) 56(84) bytes of data. 64 bytes from 173-248-252-003.static.imsbiz.com (173.248.252.3): icmp_seq=1 ttl=63 time=714 ms 64 bytes from 173-248-252-003.static.imsbiz.com (173.248.252.3): icmp_seq=2 ttl=63 time=531 ms 64 bytes from 173-248-252-003.static.imsbiz.com (173.248.252.3): icmp_seq=4 ttl=63 time=567 ms 64 bytes from 173-248-252-003.static.imsbiz.com (173.248.252.3): icmp_seq=5 ttl=63 time=589 ms 64 bytes from 173-248-252-003.static.imsbiz.com (173.248.252.3): icmp_seq=6 ttl=63 time=817 ms 64 bytes from 173-248-252-003.static.imsbiz.com (173.248.252.3): icmp_seq=7 ttl=63 time=636 ms 64 bytes from 173-248-252-003.static.imsbiz.com (173.248.252.3): icmp_seq=8 ttl=63 time=491 ms 64 bytes from 173-248-252-003.static.imsbiz.com (173.248.252.3): icmp_seq=9 ttl=63 time=503 ms 64 bytes from 173-248-252-003.static.imsbiz.com (173.248.252.3): icmp_seq=10 ttl=63 time=704 ms ...
Next, go back to the browser and check the statistics.
That is all on how to install and configure Maltrail on Ubuntu 18.04. Maltrail is an awesome tool. Feel free to explore it further. You can check their documentation by following the reference link below
Reference:
Maltrail: Malicious traffic detection system
You can also check our previous articles by following the links below;
- How to Install and Configure Nessus Scanner on Ubuntu 18.04/CentOS 7
- How to Install and Use WPScan WordPress Vulnerability Scanner Ubuntu 18.04
- How to Install and Use Nikto Web Scanner on Ubuntu 18.04
- How to Install and Use ClamAV Antivirus on Ubuntu 18.04
- How to Perform System Security Auditing with Lynis on Ubuntu 18.04
- How to Install RKHunter (RootKit Hunter) On Ubuntu 18.04
- How to Install Sophos AntiVirus on Ubuntu 18.04