In this tutorial, you will learn how to configure LDAP based HTTP basic authentication. HTTP supports various frameworks for controlling and restricting access to various web resources. One of these frameworks is HTTP Authentication frameworks. The Basic HTTP authentication scheme transmits credentials as user-id/password pairs encoded using Base64. This scheme is not considered to be a secure method of user authentication unless used in conjunction with some external secure system such as TLS (Transport Layer Security, as the user-id and password are passed over the network as cleartext.
Configuring LDAP Based HTTP Basic Authentication
In this setup, we will create a simple HTML page and enable HTTP basic authentication.
We assume you already have Basic authentication on whatever your web server is to restrict access to some resources.
However, for the sake of the demos, let us install Apache web server and configure basic authentication for a basic web page.
dnf install httpdCreate a simple html web page;
cat > /var/www/html/index.html << 'EOL'
<!DOCTYPE html>
<html>
<body>
<h1><center>Enabling OpenLDAP Based HTTP</center></h1>
<h1><center>Basic Authentication</center></h1>
</body>
</html>
EOLWe will configure HTTP basic authentication for this page;
cat > /etc/httpd/conf.d/basic-auth.conf << 'EOL'
<Directory /var/www/html>
AuthType Basic
AuthName "HTTP Basic Authentication"
AuthUserFile /etc/httpd/conf/.htpasswd
require valid-user
</Directory>
EOLCheck Apache configuration syntax and reload Apache service;
httpd -tIf the output is, Syntax OK, then restart Apache;
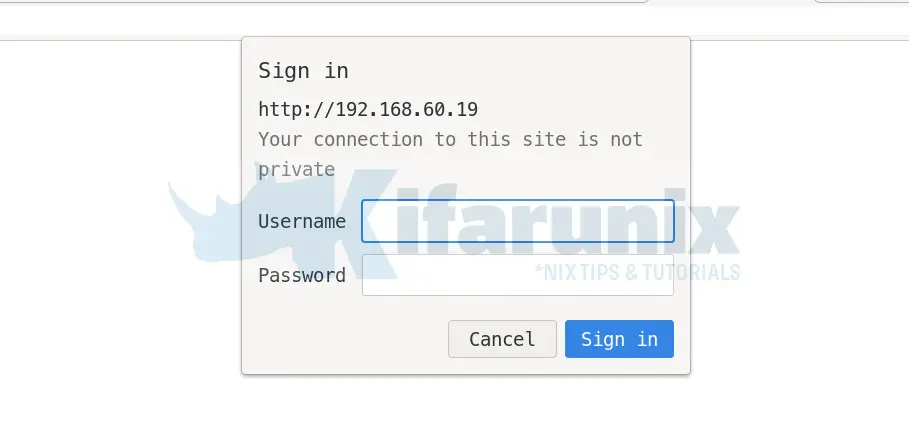
systemctl restart httpd If you try to access the page, you will be prompted to authenticate;
The usual way to authenticate is via a user/password file, as specified by the line, AuthUserFile, in the configuration above.
So for example, you can create the credentials file and add a user/password using the htpasswd utility. htpasswd utility is provided by the httpd-tools package;
htpasswd -c /etc/httpd/conf/.htpasswd kifarunixThe above command creates the password file and adds a user called kifarunix. Upon pressing ENTER, you are prompted to enter your password. The Base64 encoded password is added to the file. This is how the file looks like;
cat /etc/httpd/conf/.htpasswdkifarunix:$apr1$8HNgjKFG$MQ6UgholhZtTaJeiXH/dg1So with that, you can now authenticate to your web resource with username/password.
Integrate HTTP Basic Authentication with OpenLDAP
What if instead of using the usual username/password authentication file, you want to enable OpenLDAP based basic authentication?
Install and setup OpenLDAP server
Of course you need to have an OpenLDAP directory setup and running. You can check the link below to setup OpenLDAP.
Install and Setup OpenLDAP on Rocky Linux 8
Install and Enable Required HTTP modules
With Apache web server, there are three types of modules that are required for authentication and authorization process.
To configure LDAP based HTTP authentication, you need to enable mod_authnz_ldap module, which can authenticate users through an ldap directory. The module is provided by the mod_ldap package on CentOS/RHEL based systems and ships with Apache package on Debian based systems.
Install LDAP module on RHEL based distros;
dnf install mod_ldapWhen, installed, it is enabled automatcally.
This module can be enabled on an Apache server on Debian based systes like Ubuntu by running the command below;
a2enmod authnz_ldapTo verify that the module is enabled, run either of the commands below depending on your system distro.
httpd -M | grep ldapapachectl -M | grep ldapBoth commands output should be similar to;
authnz_ldap_module (shared)
ldap_module (shared)In my OpenLDAP server, i have a group of web developers called webdev. Querying groups on my OpenLDAP server just to show you about this.
ldapsearch -H ldapi:/// -Y EXTERNAL -LLL -Q -b "dc=ldapmaster,dc=kifarunix-demo,dc=com" uid=* memberOfSample group;
dn: uid=devadmin,ou=people,dc=ldapmaster,dc=kifarunix-demo,dc=com
memberOf: cn=webdev,ou=groups,dc=ldapmaster,dc=kifarunix-demo,dc=comFrom the above, a user whose uid is devadmin is a member of the webdev group.
You can learn more on setting OpenLDAP member groups by following the link below;
How to Create OpenLDAP Member Groups
So, we need to update the web server basic authentication with this information.
In the above user/password file based configuration;
<Directory /var/www/html>
AuthType Basic
AuthName "HTTP Basic Authentication"
AuthUserFile /etc/httpd/conf/.htpasswd
require valid-user
</Directory>We will replace it such that it looks like;
<Directory /var/www/html>
AuthType Basic
AuthName "LDAP Based HTTP Basic Authentication"
AuthBasicProvider ldap
AuthLDAPURL ldap://ldap.kifarunix-demo.com/dc=ldapmaster,dc=kifarunix-demo,dc=com?uid
AuthLDAPBindDN cn=readonly,ou=system,dc=ldapmaster,dc=kifarunix-demo,dc=com
AuthLDAPBindPassword bindDNpass
Require ldap-group cn=webdev,ou=groups,dc=ldapmaster,dc=kifarunix-demo,dc=com
</Directory>
AuthLDAPURL: Specifies the LDAP server, the base DN, the attribute to use in the search, as well as the extra search filter to use.- AuthLDAPBindDN: An optional DN to bind with during the search phase.
- if your DN has spaces, enclose it in single quotes eg
'cn=read only,ou=sys tem,dc=ldapmaster,dc=kifarunix-demo,dc=com'.
- if your DN has spaces, enclose it in single quotes eg
- AuthLDAPBindPassword: An optional password to bind with during the search phase
Require: Specifies a resource that a user is allowed to access. mod_authnz_ldap extends the authorization types withldap-user,ldap-dn,ldap-group,ldap-attributeandldap-filter.
If your LDAP server is configured with TLS/SSL, then use this configuration instead;
LDAPTrustedGlobalCert CA_BASE64 /etc/ssl/certs/ldap.pem
<Directory /var/www/html>
AuthType Basic
AuthName "LDAP Based HTTP Basic Authentication"
AuthBasicProvider ldap
AuthLDAPURL ldap://ldap.kifarunix-demo.com/dc=ldapmaster,dc=kifarunix-demo,dc=com?uid
AuthLDAPBindDN cn=readonly,ou=system,dc=ldapmaster,dc=kifarunix-demo,dc=com
AuthLDAPBindPassword bindDNpass
Require ldap-group cn=webdev,ou=groups,dc=ldapmaster,dc=kifarunix-demo,dc=com
</Directory>
In my setup, my LDAP server setup with SSL/TLS, hence, download the certificate with the command below;
openssl s_client -connect ldap.kifarunix-demo.com:389 -starttls ldap -showcerts < /dev/null | openssl x509 -text | sed -ne '/-BEGIN CERTIFICATE-/,/-END CERTIFICATE-/p'Copy the certificate between -----BEGIN CERTIFICATE----- and -----END CERTIFICATE-----, and put it in a file specified by the line LDAPTrustedGlobalCert above, /etc/ssl/certs/ldap.pem.
See more Examples.
If you are using CentOS/RHEL based distro, you need to update SELinux, if not already done, to allow httpd to connect to network, ldap, authlogin nsswitch ldap, and enable nis, respectively.
setsebool -P httpd_can_network_connect 1setsebool -P httpd_can_network_connect 1setsebool -P httpd_can_connect_ldap 1setsebool -P authlogin_nsswitch_use_ldap 1setsebool -P nis_enabled 1Check Apache syntax for errors and restart it;
CentOS
httpd -tUbuntu/Debian
apachectl -tRestart Apache
CentOS
systemctl restart httpdUbuntu/Debian
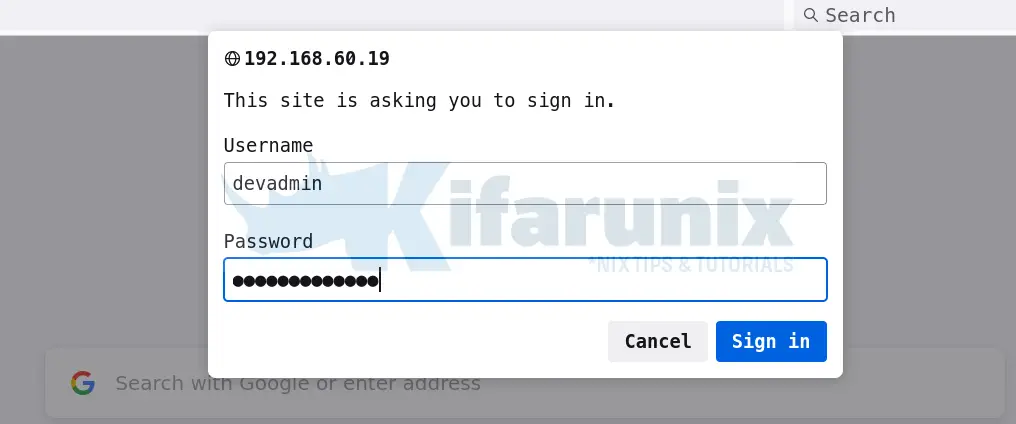
systemctl restart apache2Authenticating with LDAP credentials
You can now access your web page. When prompted for credentials, provide LDAP credentials.
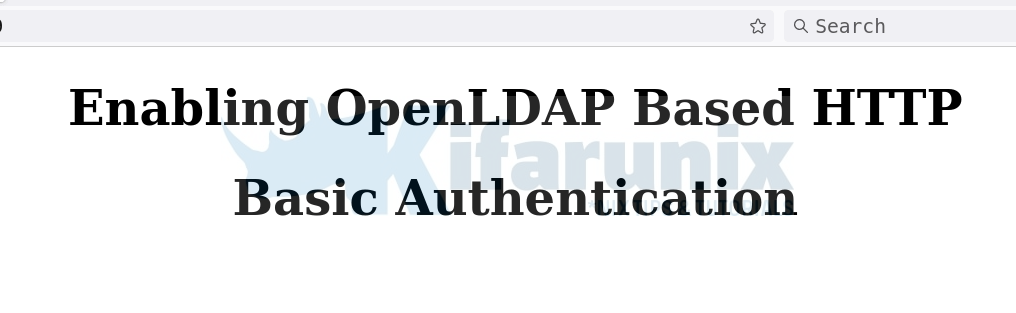
Upon successful login, you land on your page, which in my setup looks like below;
Also, the access logs shows this activity;
192.168.60.3 - devadmin [31/Jul/2021:01:18:54 +0300] "GET / HTTP/1.1" 200 150 "-" "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:89.0) Gecko/20100101 Firefox/89.0"
192.168.60.3 - devadmin [31/Jul/2021:01:18:55 +0300] "GET /favicon.ico HTTP/1.1" 404 196 "http://192.168.60.19/" "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:89.0) Gecko/20100101 Firefox/89.0"And there you go. You have successfully integrated web HTTP basic authentication with OpenLDAP.
Other Tutorials
Configure Squid Proxy OpenLDAP Authentication on pfSense