In this guide, you will learn how to scan RHEL systems for CIS benchmark compliance with Wazuh SCA. Red Hat Enterprise Linux (RHEL) systems form the backbone of countless enterprise environments, making their security posture critical for organizational protection. With cyber threats evolving rapidly, administrators need reliable methods to assess and maintain security compliance across their infrastructure. This comprehensive guide demonstrates how to leverage Wazuh Security Configuration Assessment (SCA) to scan RHEL systems against Center for Internet Security (CIS) benchmarks, providing actionable insights into your security posture.
Table of Contents
How to Scan RHEL Systems for CIS Benchmark Compliance with Wazuh SCA
What Is Wazuh SCA?
Wazuh SCA is the Security Configuration Assessment module within the open-source Wazuh platform, a unified XDR (Extended Detection and Response) solution for endpoint security, threat detection, and compliance monitoring. SCA periodically scans endpoints for misconfigurations using predefined policy files, generating alerts and reports on passed, failed, or not-applicable checks.
At its core, SCA acts like a continuous vulnerability scanner but focuses on configuration drift rather than exploits. It integrates seamlessly with Wazuh’s dashboard for visualization, allowing you to drill down into results, correlate with logs, and automate remediation via integrations like Ansible or custom scripts.
Key features include:
- Out-of-the-Box Policies: Pre-built YAML files for CIS, NIST, and more.
- Agent-Based Scanning: Lightweight agents on endpoints (like RHEL) perform scans without disrupting operations.
- Customizable Checks: Modify rules for your environment or add new ones.
- Reporting: JSON outputs for dashboards, with compliance scores and remediation guidance.
In short, Wazuh SCA turns complex compliance into a proactive, scalable process ideal for RHEL fleets spanning on-prem, cloud, and hybrid setups.
What Are CIS Benchmarks and Why Do They Matter?
The Center for Internet Security (CIS) Benchmarks are consensus-driven, prescriptive security guidelines developed by cybersecurity experts worldwide. They provide detailed, actionable recommendations to configure systems, software, and networks securely, reducing the attack surface against common threats like unauthorized access, weak encryption, and privilege escalation.
For RHEL specifically, CIS Benchmarks focus on hardening the OS by addressing vulnerabilities such as open ports, unnecessary services, and improper file permissions. They come in two levels:
- Level 1: Basic security for general environments (e.g., disabling unused accounts).
- Level 2: Advanced controls for high-security setups (e.g., full disk encryption and audit logging). AKA defense in depth.
Adopting CIS Benchmarks isn’t just best practice, it’s a strategic imperative. By scanning against CIS Benchmarks, organizations not only mitigate risks but also automate audits, saving hours of manual checks and ensuring ongoing compliance amid frequent updates.
How Wazuh SCA Utilizes CIS Benchmarks
Wazuh’s Security Configuration Assessment (SCA) module integrates CIS Benchmarks by converting their security recommendations into structured policy files that the Wazuh agent can automatically enforce and evaluate. This allows organizations to continuously monitor their RHEL systems for compliance with industry best practices.
Wazuh ships with ready-to-use policy files based on CIS Benchmarks for multiple Linux distributions, including RHEL 5, 6, 7, 8, 9, and 10. These policies are written in YAML and contain hundreds of individual rules aligned with specific CIS controls. For example, the cis_rhel8_linux.yml policy includes checks such as verifying the use of the nodev option on /tmp, or enforcing password complexity rules.
The Wazuh agent executes these policies at regular intervals (e.g., every 12 hours). Each rule defines commands or configuration checks that are run locally on the system to validate compliance. This automation ensures continuous assessment without manual intervention.
Each rule corresponds to a specific CIS recommendation and includes clear pass/fail logic. For example, to enforce CIS rule 1.1.1.2 (ensuring nodev is set on /tmp), the agent runs system commands like findmnt -l | grep /tmp to inspect mount options. The outcome is recorded for reporting.
When a rule fails, Wazuh generates a detailed alert that includes the rationale behind the control and, in many cases, specific remediation steps. For instance, if CIS rule 5.3.3.4.1 (regarding password policies) fails, the alert may suggest running the command: authselect select sssd with-faillock to fix the issue.
Wazuh maps CIS rules to broader compliance standards, such as NIST 800-53 (e.g., CM-6), helping organizations demonstrate how specific technical configurations meet regulatory or audit requirements. This is especially valuable for enterprises in regulated industries.
Wazuh maintains and updates its policy files in line with changes to the CIS Benchmarks. For example, support for CIS Benchmark version 2.0.0 for RHEL 9 has been incorporated, and community contributions have helped develop beta policies for RHEL 10 as of September 2025.
Key Security Areas Covered by CIS Benchmarks
The CIS Benchmarks are structured into logical categories to cover all critical aspects of system security. Below is a breakdown of the key areas commonly addressed in Linux distributions like RHEL, CentOS, and Rocky Linux:
- 1 Initial Setup
- 1.1 Filesystem
- 1.2 Package Management
- 1.3 Mandatory Access Control
- 1.4 Configure Bootloader
- 1.5 Configure Additional Process Hardening
- 1.6 Configure system wide crypto policy
- 1.7 Configure Command Line Warning Banners
- 1.8 Configure GNOME Display Manager
- 2 Services
- 2.1 Configure Server Services
- 2.2 Configure Client Services
- 2.3 Configure Time Synchronization
- 2.4 Job Schedulers
- 3 Network
- 3.1 Configure Network Devices
- 3.2 Configure Network Kernel Modules
- 3.3 Configure Network Kernel Parameters
- 4 Host Based Firewall
- 4.1 Configure a firewall utility
- 4.2 Configure FirewallD
- 4.3 Configure NFTables
- 5 Access Control
- 5.1 Configure SSH Server
- 5.2 Configure privilege escalation
- 5.3 Pluggable Authentication Modules
- 5.4 User Accounts and Environment
- 6 Logging and Auditing
- 6.1 Configure Integrity Checking
- 6.2 System Logging
- 6.3 System Auditing
- 7 System Maintenance
- 7.1 System File Permissions
- 7.2 Local User and Group Settings
You can download the CIS benchmarks PDF for your preview.
Step-by-Step Guide: Scanning RHEL Systems for CIS Compliance
Step 1: Set Up Wazuh Server and Install Agents
Before scanning your RHEL systems for CIS compliance, you must have a working Wazuh setup:
- A Wazuh server (manager) must be installed and running.
- The Wazuh agent must be installed and actively communicating with the server on each RHEL system you want to scan.
This guide assumes you’ve already completed the Wazuh server and agent installation.
If not, use the links below to get started:
Once your environment is ready, continue to the next step to configure and run the CIS benchmark scan.
Step 2: Configure SCA for CIS Benchmarks
Wazuh’s Security Configuration Assessment (SCA) module is enabled by default on both the manager and agents. However, you should still verify that it is properly configured.
On the Wazuh Manager, confirm that the following block exists in the /var/ossec/etc/ossec.conf file:
<sca>
<enabled>yes</enabled>
...
</sca>This ensures the manager is ready to manage SCA policies and receive scan results from agents.
On the Agent, verify or configure the SCA section as follows:
vim /var/ossec/etc/ossec.conf<sca>
<enabled>yes</enabled>
<scan_on_start>yes</scan_on_start>
<interval>12h</interval>
<skip_nfs>yes</skip_nfs>
</sca>Where:
enabled: Enables the SCA module on the agent.scan_on_start: Runs a scan when the agent starts.interval: Sets the frequency of SCA scans (e.g., every 12 hours).skip_nfs: Prevents scanning of NFS-mounted file systems to reduce unnecessary load.
This configuration allows the agent to perform scheduled compliance checks based on defined policies, such as CIS benchmarks.
Step 3: Configure CIS Policy Files
During installation, Wazuh agents automatically include Security Configuration Assessment (SCA) policy files tailored to their operating system. These policies define the specific CIS benchmark checks to be performed on the system.
Wazuh provides the following preloaded CIS benchmark policies for Red Hat Enterprise Linux (RHEL):
- cis_rhel5_linux – CIS Benchmark for RHEL 5
- cis_rhel6_linux – CIS Benchmark for RHEL 6
- cis_rhel7_linux – CIS Benchmark for RHEL 7
- cis_rhel8_linux – CIS Benchmark for RHEL 8
- cis_rhel9_linux – CIS Benchmark for RHEL 9
- cis_rhel10_linux – CIS Benchmark for RHEL 10
These policy files are located at:
/var/ossec/ruleset/scaBy default, only the policy matching the current operating system version is available and active on the node.
To confirm that the policy is active on your system, you can run:
ls -1 /var/ossec/ruleset/scaYou should see something like, (if your node is rhel 8):
cis_rhel8_linux.ymlIf you want to use a custom policy file stored outside the default directory, you must explicitly add it to the Wazuh agent configuration. To do this, update the <sca> section in the agent’s ossec.conf:
<sca>
<policies>
<policy>/path/to/custom_policy_file.yml</policy>
</policies>
</sca>This overrides the default behavior and instructs the agent to scan using your custom policy file. Refer to creating custom SCA policies for more information.
If you make any changes, be sure to restart the agent.
sudo systemctl restart wazuh-agentStep 4: Configure Scan Scheduling
Customize scan scheduling based on your operational requirements. Consider factors such as system performance impact, compliance reporting needs, and change frequency when determining optimal scan intervals.
For environments requiring frequent compliance verification, consider more frequent scanning:
<sca>
<interval>6h</interval>
...
</sca>For systems with infrequent changes, less frequent scanning may be appropriate:
<sca>
<interval>24h</interval>
</sca>Step 5: Run and Monitor Scans
The Wazuh agent will automatically perform SCA scans periodically, as per the defined interval or on agent start.
You can also trigger a manual scan on the agent from the Wazuh manager CLI:
/var/ossec/bin/agent_control -R <agent_id>Or force a scan via the Wazuh API (The default Wazuh server API credential is wazuh:wazuh):
Obtain the authentication TOKEN
TOKEN=$(curl -u <WAZUH_API_USER>:<WAZUH_API_PASSWORD> -sk -X POST "https://<MANAGER_IP>:55000/security/user/authenticate?raw=true")Get the agent ID:
/var/ossec/bin/agent_control -lRestart the agent:
curl -X PUT -sk "https://<MANAGER_IP>:55000/agents/<AGENT_ID>/restart?pretty=true" -H "Authorization: Bearer $TOKEN"Step 6: Understanding SCA Results and Reports
Wazuh SCA generates comprehensive reports that provide detailed insights into system compliance status, failed checks, and remediation guidance. Understanding these reports enables effective security posture management.
The Wazuh web interface presents SCA results through an intuitive dashboard that highlights key compliance metrics:
- Overall Compliance Score: Percentage-based compliance rating showing the proportion of passed checks versus total applicable checks.
- Policy Breakdown: Detailed breakdown showing compliance status for individual CIS benchmark sections, enabling focused remediation efforts.
- Trend Analysis: Historical compliance data showing improvement or degradation over time, helping track remediation progress.
- Risk Prioritization: Failed checks organized by severity level, allowing administrators to focus on the most critical security gaps first.
So, once the scan completes, you can head over to Wazuh dashboard and navigate to Endpoint Security > Configuration Assessment module to view the scan summaries.
Here is a sample dashboard for our RHEL 9 agent:
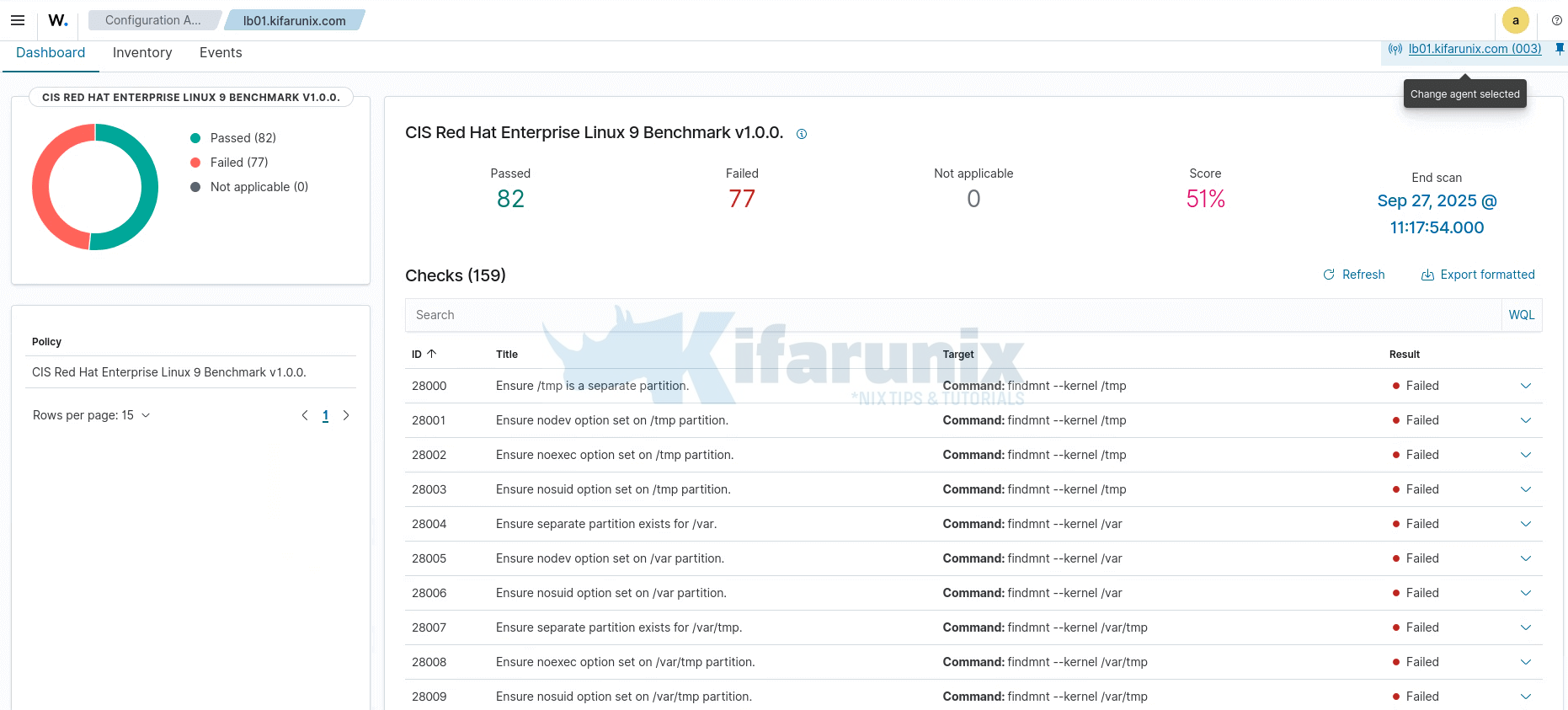
Each SCA check provides specific information about configuration assessment results:
- Pass Status: Indicates the system configuration meets CIS benchmark recommendations for the specific security control.
- Fail Status: Shows configuration deviations from CIS recommendations, including specific details about current configuration and expected settings.
- Not Applicable: Identifies checks that don’t apply to the specific system configuration or installed software components.
- Error Status: Indicates checks that couldn’t be completed due to permission issues, missing files, or other technical problems.
You can click any result to expand it and display additional information:
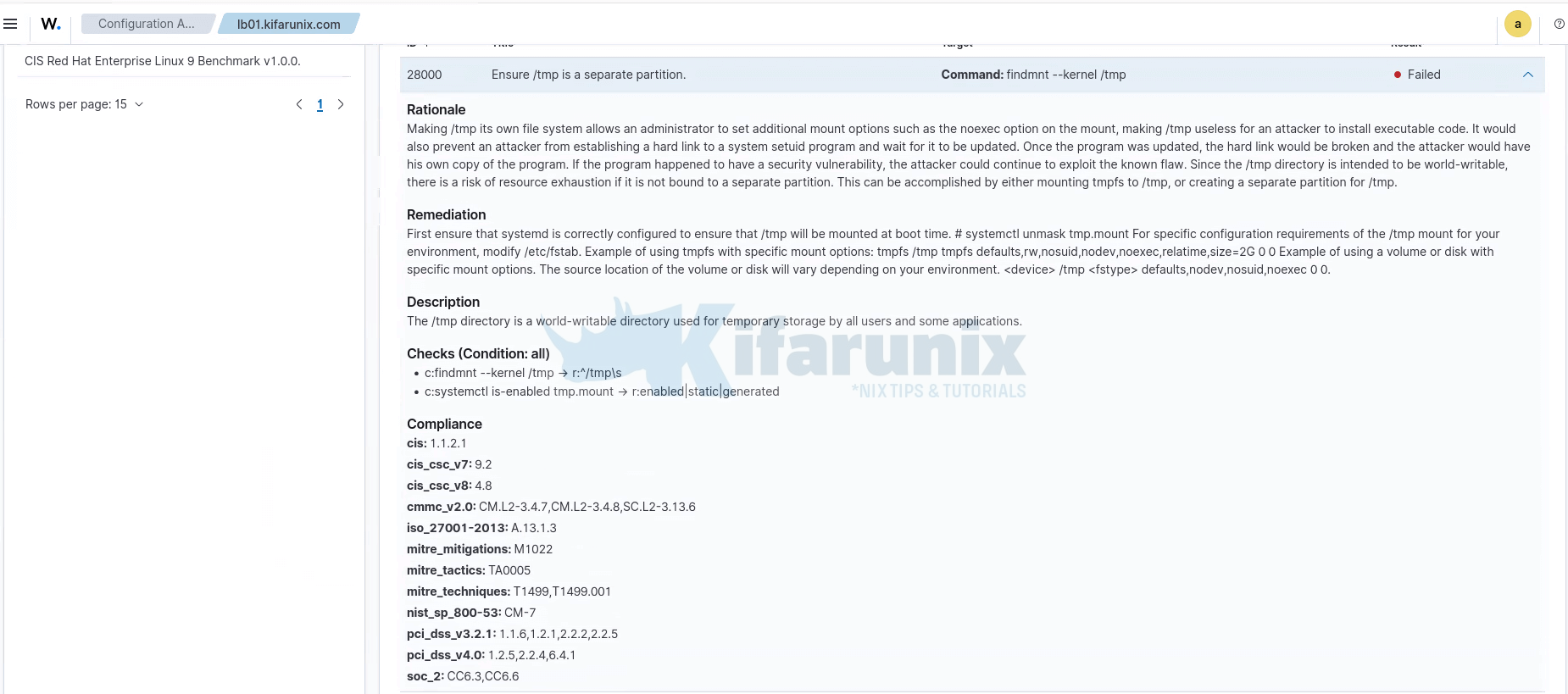
As you can see from the details above, SCA reports include detailed information such as:
- Description – A brief explanation of the system component or behavior under review.
- Rationale – Why the control is important from a security perspective.
- Remediation – Clear steps on how to fix a failed check and bring the system into compliance.
- Checks Performed – The specific logic and conditions used by Wazuh to evaluate compliance.
- Compliance Mappings – References to broader frameworks like CIS, NIST, ISO 27001, PCI-DSS, and MITRE.
Further reading:
Security Configuration Assessment
Conclusion
Hardening RHEL systems according to CIS Benchmarks is an essential step in reducing security risks and ensuring compliance. By leveraging Wazuh Security Configuration Assessment (SCA), organizations can automate the detection of misconfigurations, generate compliance reports, and streamline audits.
If you’re running RHEL in production, enabling Wazuh SCA for CIS compliance should be a top priority for your security operations team. It not only helps you meet industry standards but also ensures your systems remain resilient against evolving threats. Remember that security is an ongoing process rather than a one-time implementation. Continuous monitoring, regular review of scan results, and proactive remediation of identified issues ensure that your RHEL systems maintain strong security posture against evolving threats and changing compliance requirements.

